Trusted measurement method, device and system, electronic equipment and storage medium
A credible and credible technology, applied in computer security devices, electrical digital data processing, instruments, etc., can solve problems such as insufficient security of systems and data, and achieve the effect of ensuring system and data security and ensuring effectiveness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
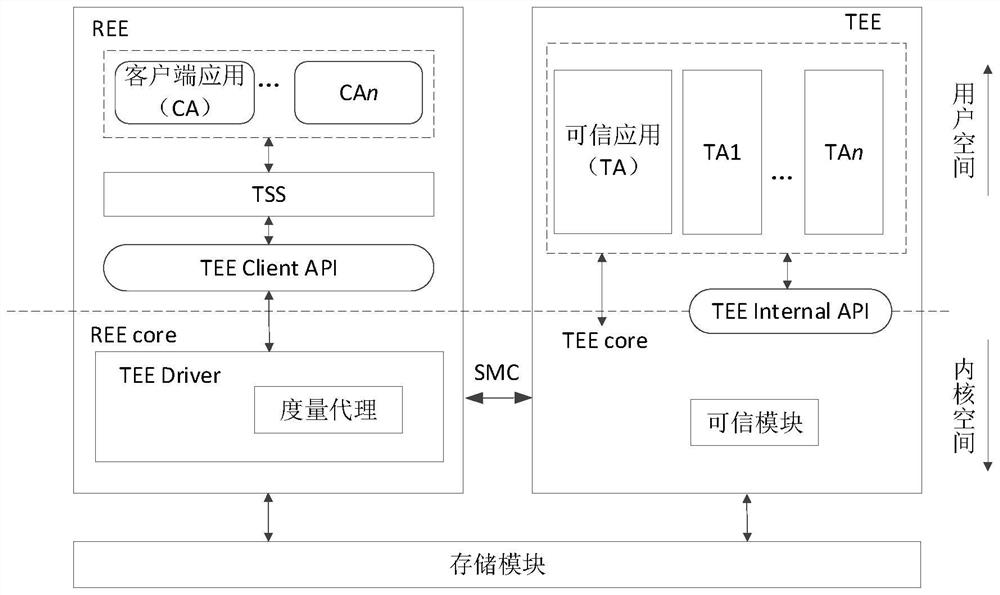
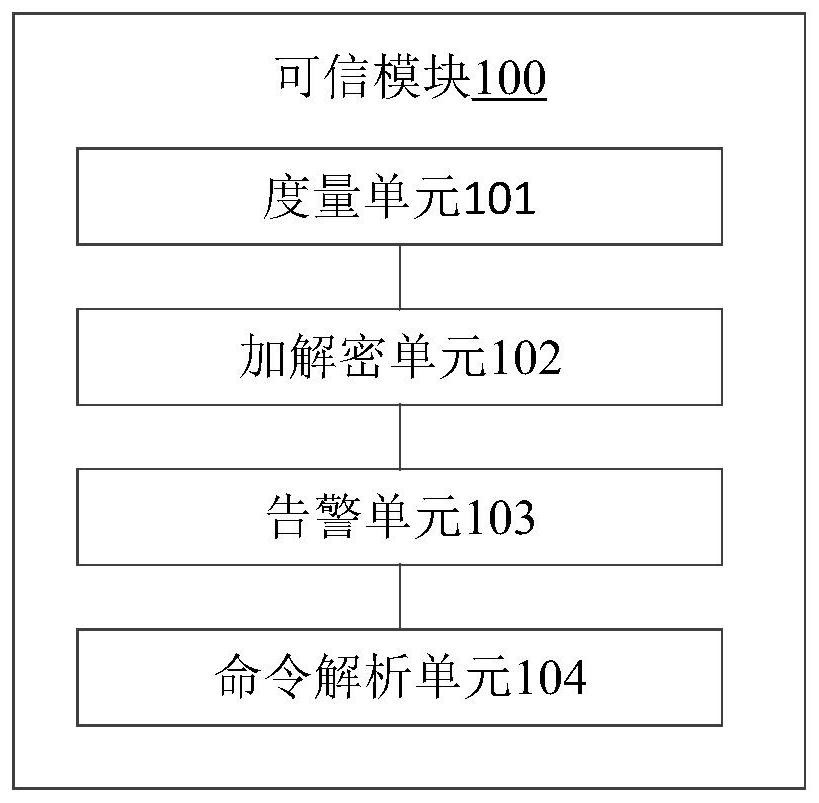
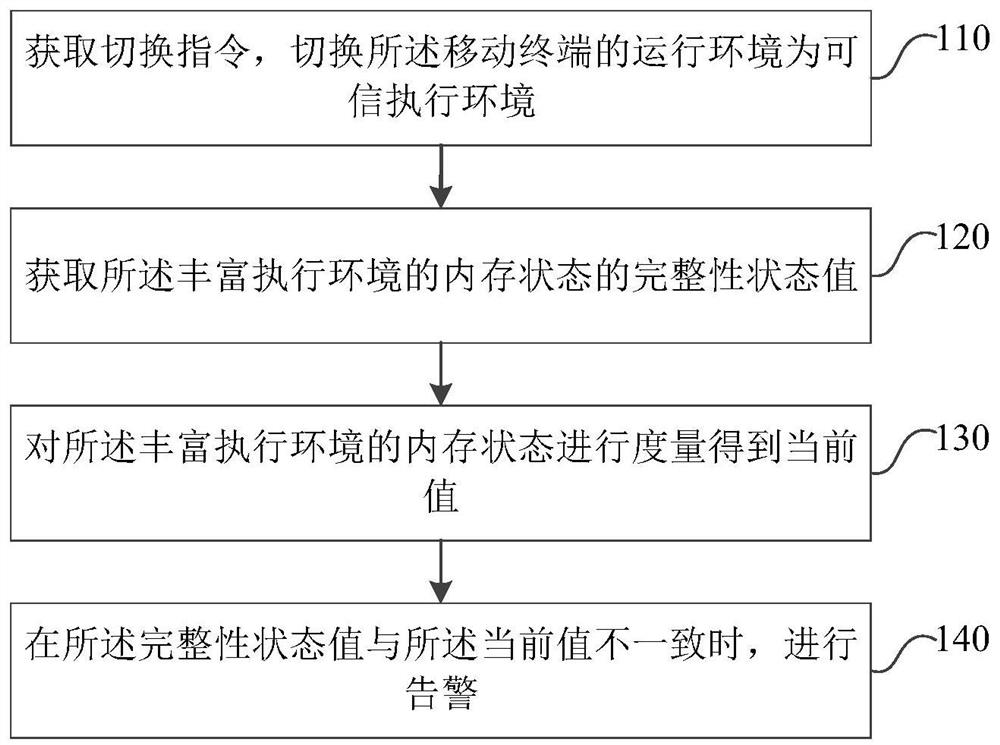
[0019] As mobile terminals become more intelligent and their applications more abundant, more and more sensitive information involving business secrets or personal privacy is facing serious security threats. Various applications are constantly emerging on mobile terminals. If developers do not implement security reinforcement protection when developing these applications, hackers may take advantage of the inherent security holes in these applications to obtain the root authority of the mobile terminal operating system and easily intercept users' sensitive data. data. So far, how to ensure the security of the mobile terminal has become more and more important.
[0020] In order to provide a safe operating environment for mobile terminals, ARM has introduced TrustZone technology from the ARMv6 architecture. TrustZone technology divides the working state of the central processing unit into normal state and safe state. The environment running in the secure state is a trusted exe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com