Server malicious program detection method based on code characteristics and flow behaviors
A malicious program and detection method technology, applied in the field of malicious program detection, can solve problems such as incomplete coverage of regular expressions, false negatives and false positives, and undetectable server backdoor programs, achieving the effect of improving detection efficiency and accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
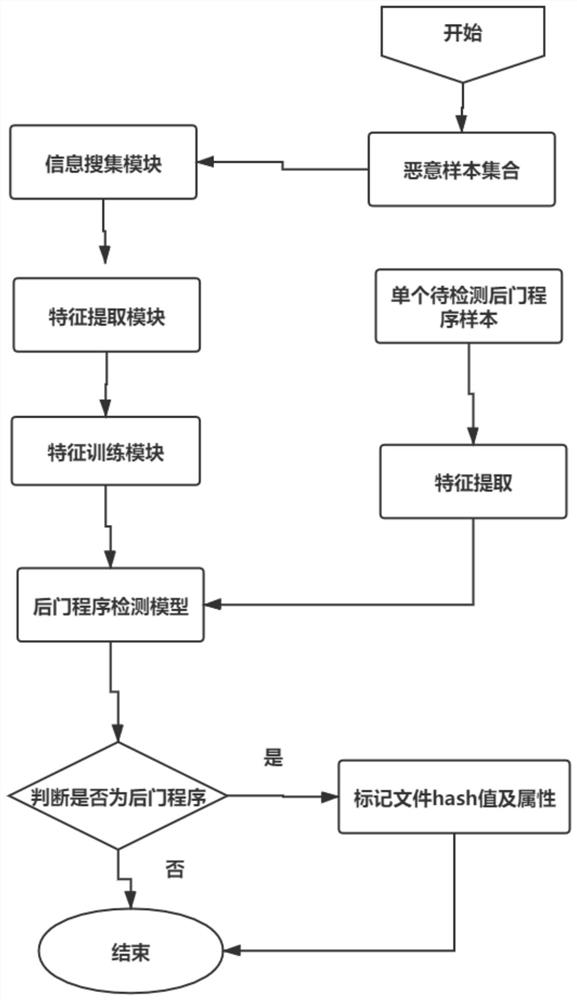
[0043] Such as figure 1 As shown, a server-side malicious program detection method based on code features and traffic behavior, this method combines code features and malicious traffic behavior, first extracts code features and traffic behavior, and then uses relief algorithm to optimize the features, Combine into a new feature set, and finally use the decision tree method to learn and train to establish a server-side backdoor program detection model, detect the server-side backdoor program and output the results. Technical solutions include the following:
[0044] 1. Information collection: Collect all backdoor program samples shared by open source communities at home and abroad, extract function features and hash values, and establish a malicious program sample library.
[0045] 2. Feature extraction: build the simulation environment required for backdoor program file communication, use the simulated client to communicate with the backdoor program, use wireshark to capture ...
Embodiment 2
[0052] Such as figure 1 As shown, a server-side malicious program detection method based on code characteristics and traffic behavior, including:
[0053] 1. Collect server-side backdoor program samples;
[0054] Server backdoor program sample collection: Under normal circumstances, there are relatively few server backdoor program samples. You can collect server backdoor programs and match static rules by sorting out malicious sample libraries uploaded by communities such as github.
[0055] 2. Extract code features: extract the code features of backdoor program samples obtained from public platforms.
[0056] Code features: Mainly refers to the longest string length, file overlap index, file compression ratio, non-alphanumeric character proportion, high-risk function (command execution, operation file read and write, encryption and decryption related functions) proportion as input features, Form the sample set S1.
[0057] 3. Extract traffic behavior: Simulate the operatin...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap