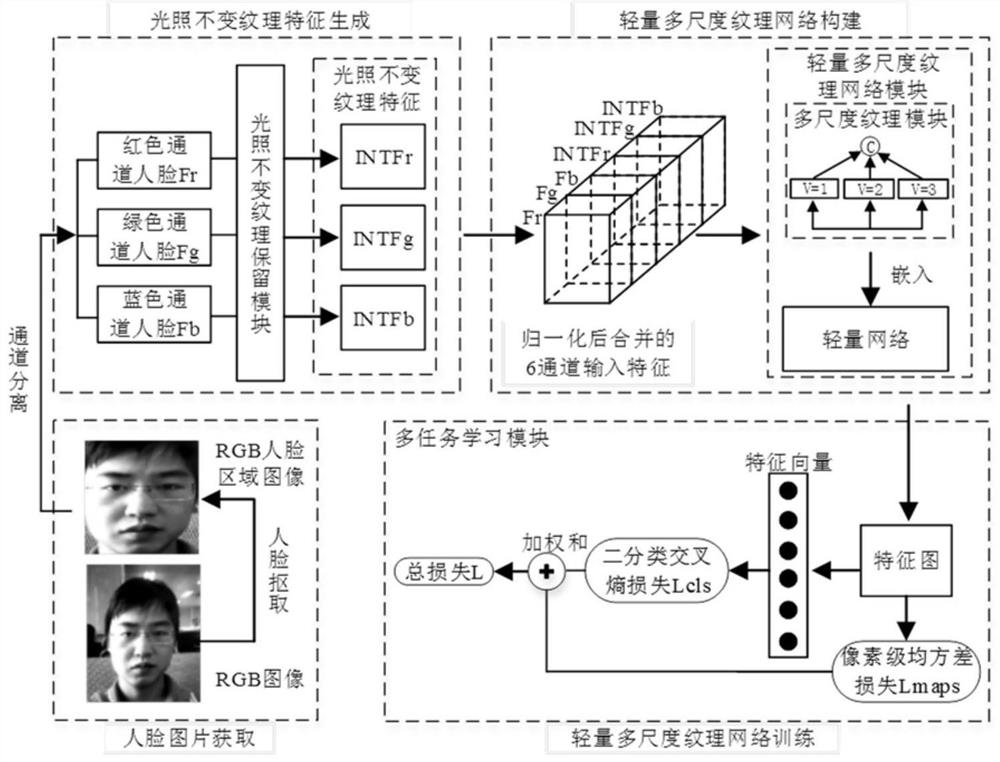
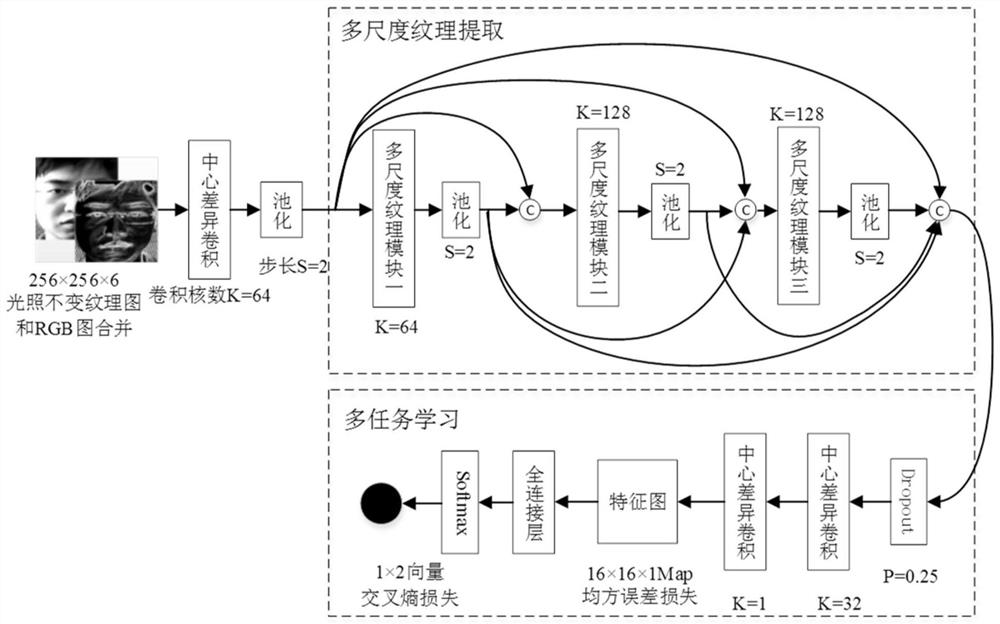
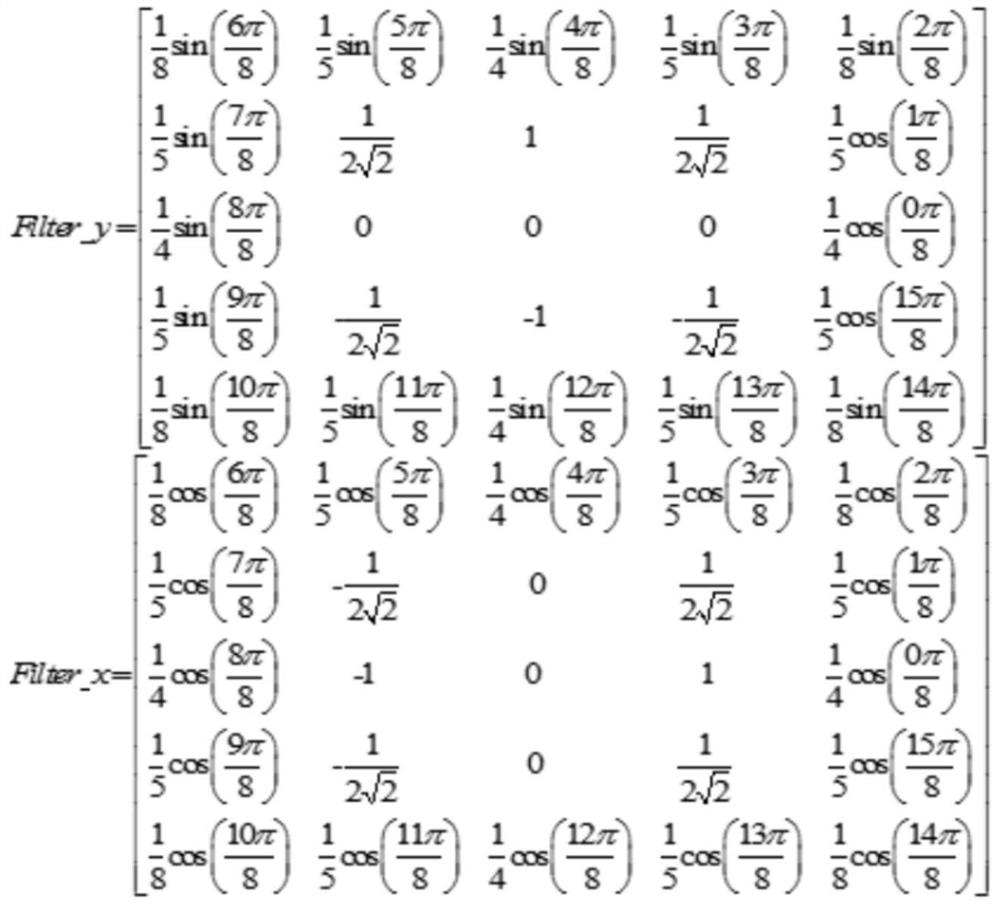
Face spoofing detection method and system based on multi-scale illumination invariance textural features
A texture feature and deception detection technology, applied in the field of face deception detection, can solve the problems of generalization performance and computational complexity limitations, algorithm generalization performance degradation, threats to the application of face recognition systems, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0083] The present embodiment adopts the data sets of CASIA-MFSD face deception database, MSU_MFSD database and Replay-Attack database to carry out training and detection;
[0084] Among them, the CASIA-MFSD face spoofing database is divided into a training set taken by 20 people and a test set taken by 30 people, and fake faces are made by recapturing real faces. The database uses three types of cameras to collect videos with different imaging qualities, and the resolutions are 640×480 pixels, 480×640 pixels, and 1920×1080 pixels. Attack methods include: bending photo attack, cutting photo attack, and video replay attack; a total of 50 people and 600 videos were involved.
[0085] The Replay-Attack database consists of real and attack videos of 50 people. The shooting equipment is a MacBook camera with a resolution of 320×240 pixels. The 1200 videos captured are divided into two lighting conditions: (1) uniform background, fluorescent lighting; (2) background Uneven, poor li...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com