Data sharing and privacy protection method based on block chain
A data sharing and privacy protection technology, applied in the field of information security, can solve problems such as storage capacity limitations, achieve the effect of lowering the threshold of use, enriching data types and application types, and optimizing consensus algorithms
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
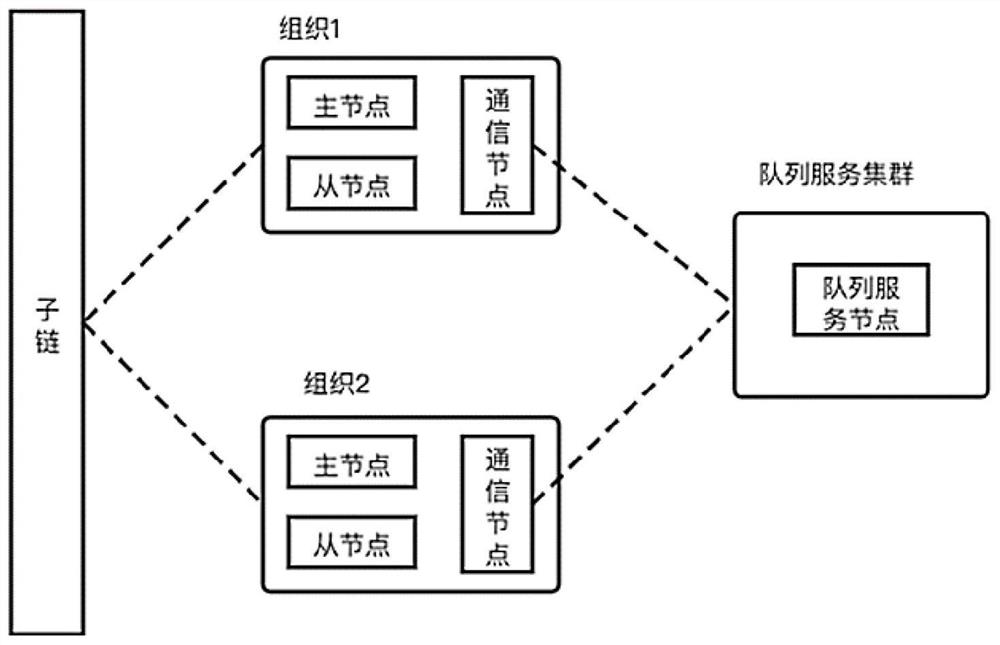
[0020] Such as figure 1 As shown, this embodiment relates to a blockchain node organization structure, wherein: node organization as a participant basic unit includes: 1 communication node and 4 consensus nodes, of which there is only 1 at the same time Consensus nodes are elected to generate the master node.
[0021] The election specifically refers to: in each node organization, after each master node stops serving or participates in n times of consensus service expiration, the node organization will re-elect the master node. Wherein, n can be preset depending on the number of nodes in the node organization. If the master node service expires, the master node will actively initiate a vote; if the master node service stops unexpectedly, the ordering node will initiate a vote to other nodes in the node organization. At the same time, each node has its own address (private key), and members in the node organization will jointly maintain an ordered list of all node addresses i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com