Method and device for screening financial business operation logs
A business operation and business technology, applied in the field of financial technology, can solve problems such as failure to meet the verification requirements of mass business risk control compliance, effectiveness cannot be guaranteed, business model and rules are out of touch, and achieve reduction of verification and inspection time, and solution Timeliness issues, the effect of meeting performance requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
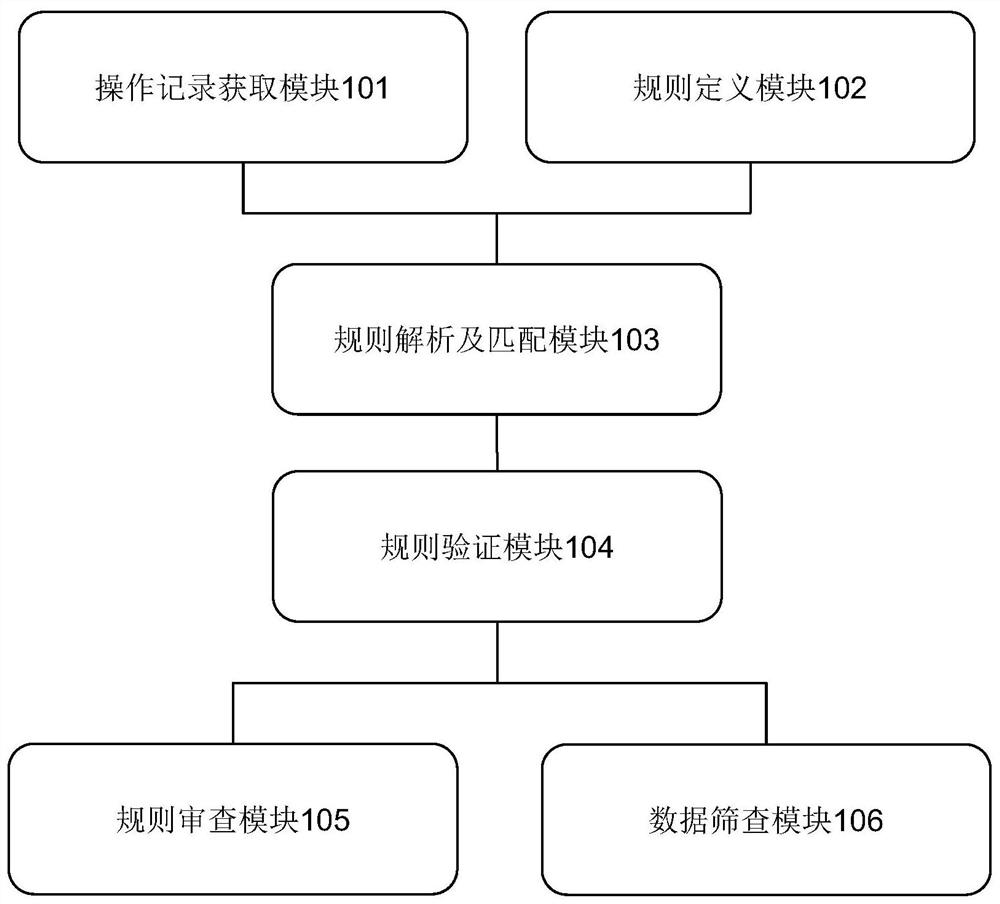
Image
Examples
Embodiment Construction
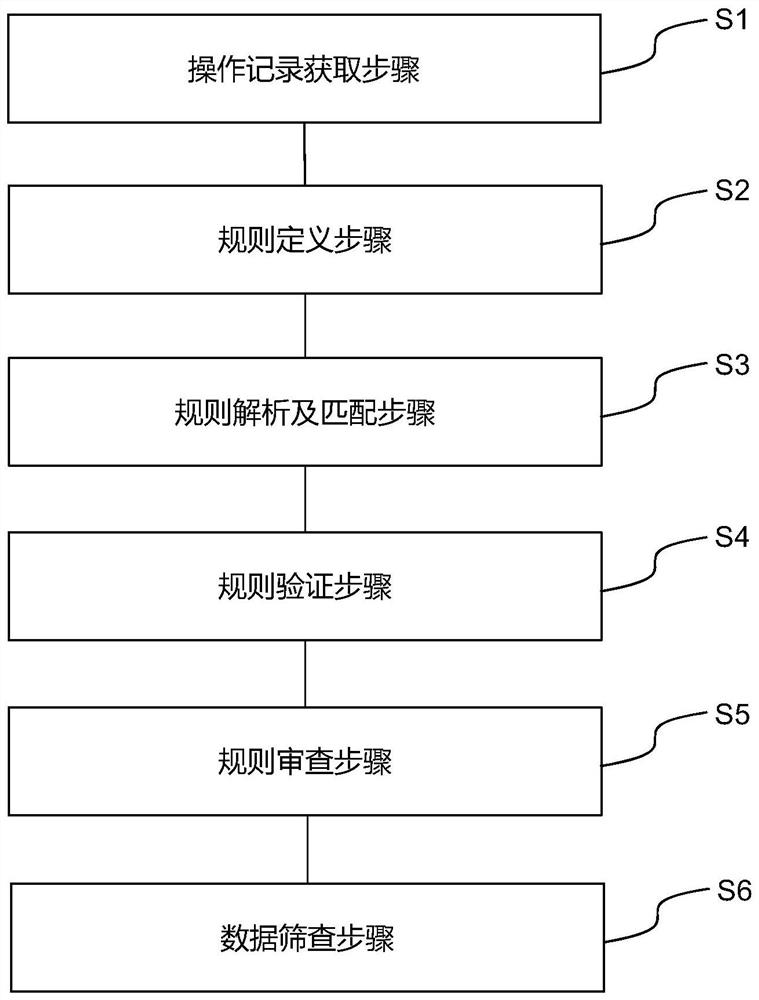
[0029] figure 1 Disclosed is a flow chart of a method for screening financial business operation logs according to an embodiment of the present invention. refer to figure 1 As shown, the screening method of the financial business operation log includes the following steps:
[0030] S1. The step of obtaining operation records. Obtain operation records from operation logs from multiple data sources, process and convert the operation records to obtain operation sequence files. Since the bank has many branches and business outlets, each branch and business outlet has a local operation log to record relevant local operation data. In the operation record obtaining step, respective operation records are obtained from the servers of each branch office and business network. In the internal compliance review, the sequence of operations is an important verification link, and the sequence of operations is mainly judged by recording the occurrence time of the operations. In order to a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com