Flow security analysis modeling method and system
A technology of safety analysis and modeling method, applied in the field of flow safety analysis modeling method and system, can solve problems such as hidden safety hazards of production equipment, and achieve the effect of improving impedance capability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
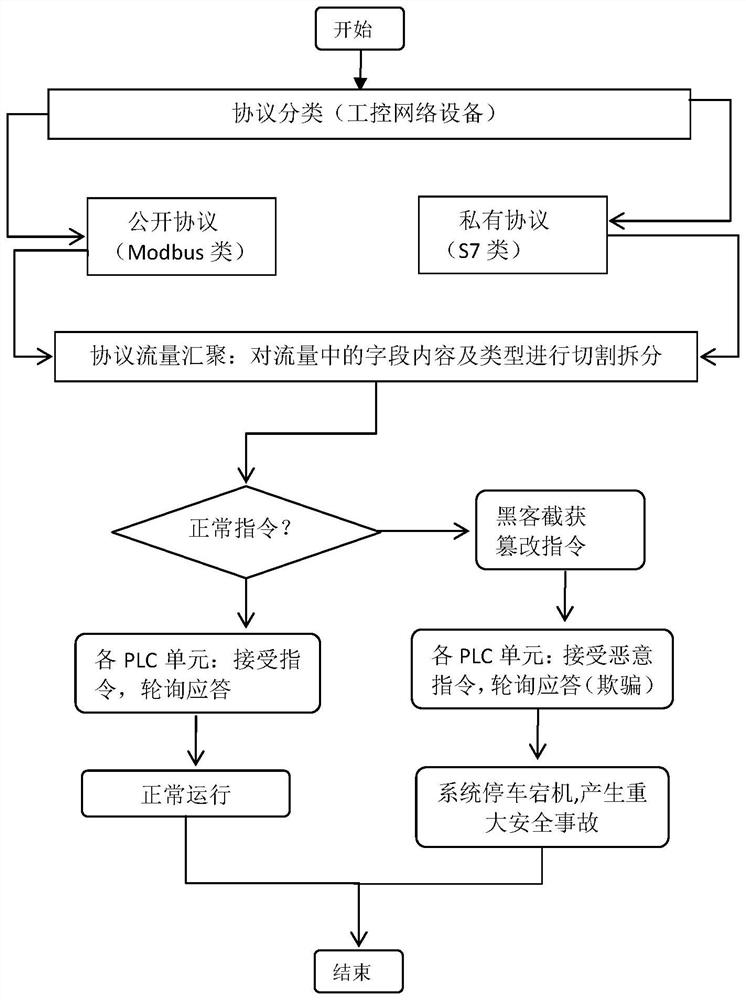
[0047] Embodiment 1 of the present invention proposes a flow security analysis and modeling method. The present invention adopts N-Tier layering. During the network flow transmission process using the industrial control protocol, the network flow is realized based on the network flow mirroring bypass system. No intrusive mirroring.
[0048] Such as figure 1 A flowchart of a traffic security analysis and modeling method in Embodiment 1 of the present invention is given;
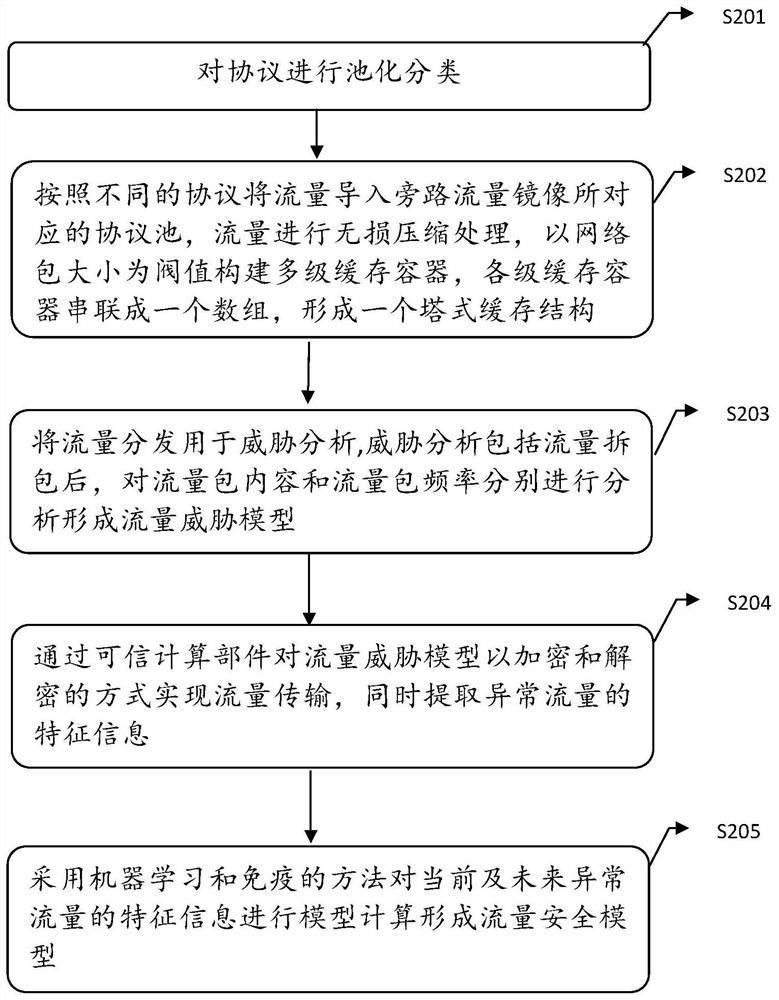
[0049] In step S101, the protocols are pooled and classified into shared protocol pools and private protocol pools.
[0050] In step S102, according to different protocols, the traffic is imported into the protocol pool corresponding to the bypass traffic mirror, and the traffic is subjected to lossless compression processing, and a multi-level cache container is constructed with the network packet size as the threshold, and the cache containers of all levels are connected in series to form an array. Form a ...
Embodiment 2
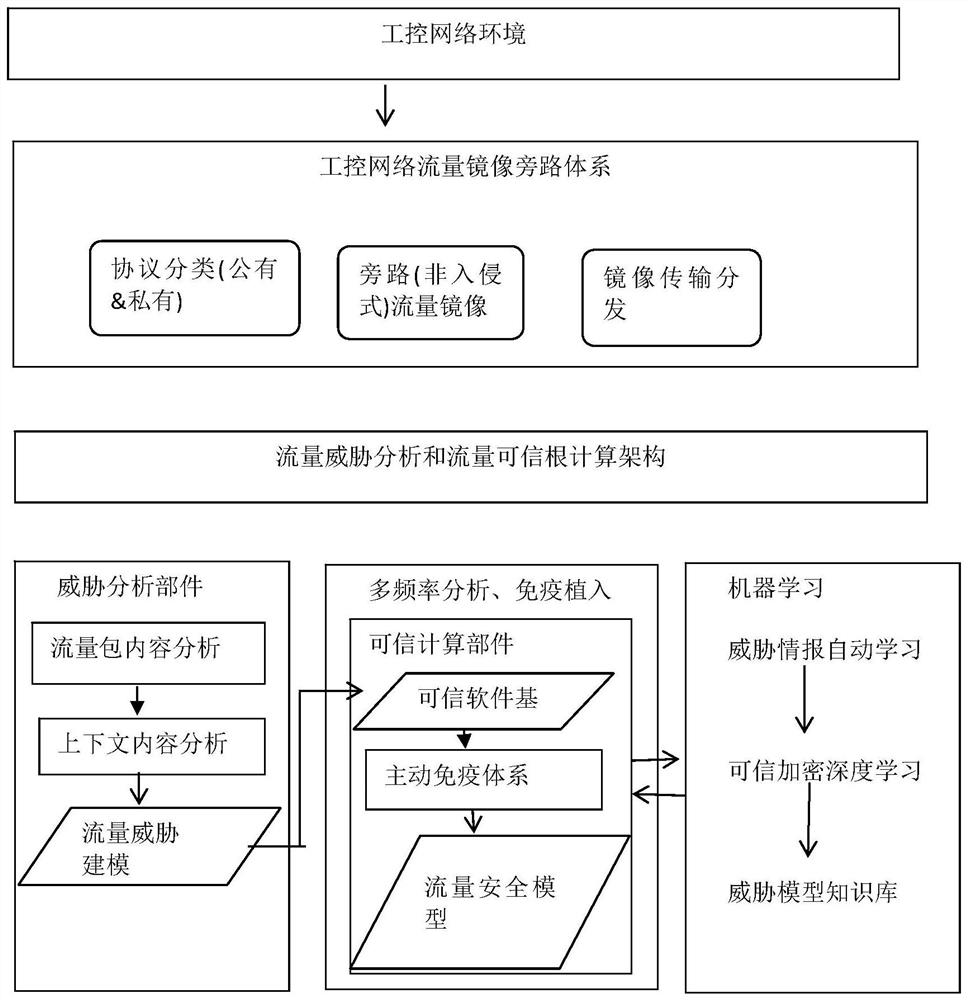
[0068] Based on the traffic security analysis and modeling method proposed in Embodiment 1 of the present invention, Embodiment 2 of the present invention proposes a traffic security analysis and modeling system. Such as image 3 A schematic diagram of a traffic security analysis and modeling system in Embodiment 2 of the present invention is given. The system includes an industrial control network bypass module, a threat analysis module and a trusted root computing module;
[0069] The industrial control network bypass module is used to import traffic into the protocol pool corresponding to the bypass traffic mirror according to different protocols, compress the traffic in the protocol pool and put it into the cache; distribute the traffic for threat analysis;
[0070] The threat analysis module is used to analyze the content of the traffic packet and the frequency of the traffic packet to form a traffic threat model after the traffic is unpacked;
[0071] The root of trust...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com