Data access permission updating method and device, equipment and readable storage medium
A data access and update method technology, applied in the storage field, can solve the problems of heavy data access authority update burden, complicated authority update process and high cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
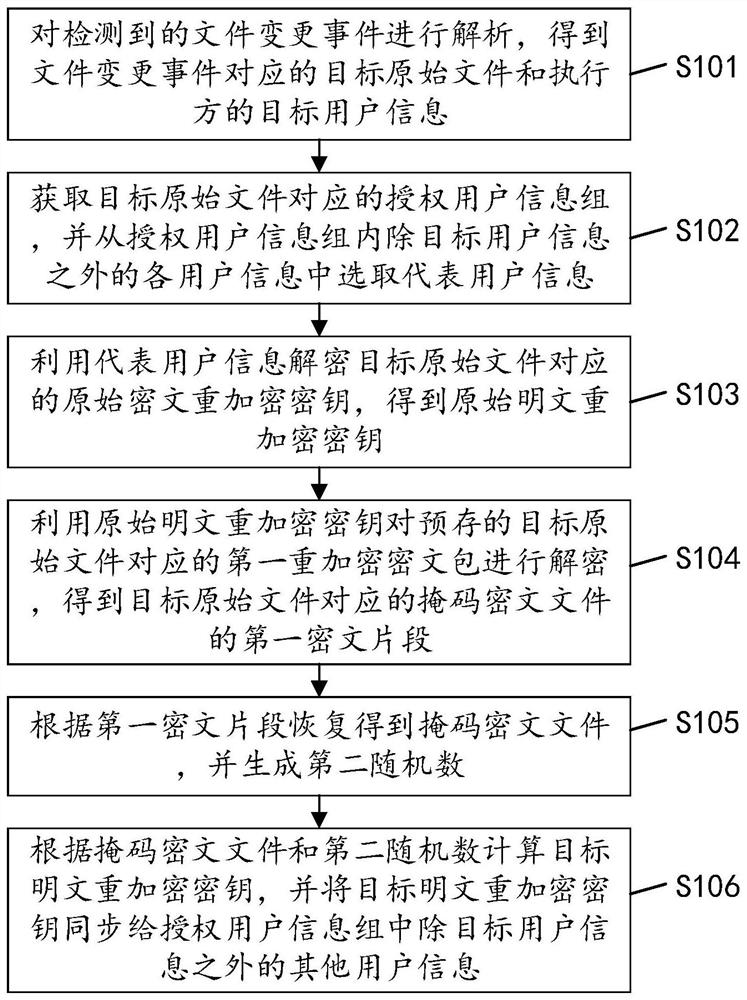
[0054] see figure 1 , figure 1 It is an implementation flowchart of a method for updating data access rights in an embodiment of the present invention, and the method may include the following steps:
[0055] S101: Analyze the detected file change event to obtain the target original file corresponding to the file change event and the target user information of the executor.
[0056] After receiving the files uploaded by each client, the cloud server detects whether there is a file change event, such as whether there is an action to modify or delete the stored file, and if so, obtains the file change event, which includes the changed The target original file and the target user information of the executor who executes the file change. The detected file change event is analyzed to obtain the target original file corresponding to the file change event and the target user information of the executor.
[0057] S102: Obtain an authorized user information group corresponding to th...
Embodiment 2
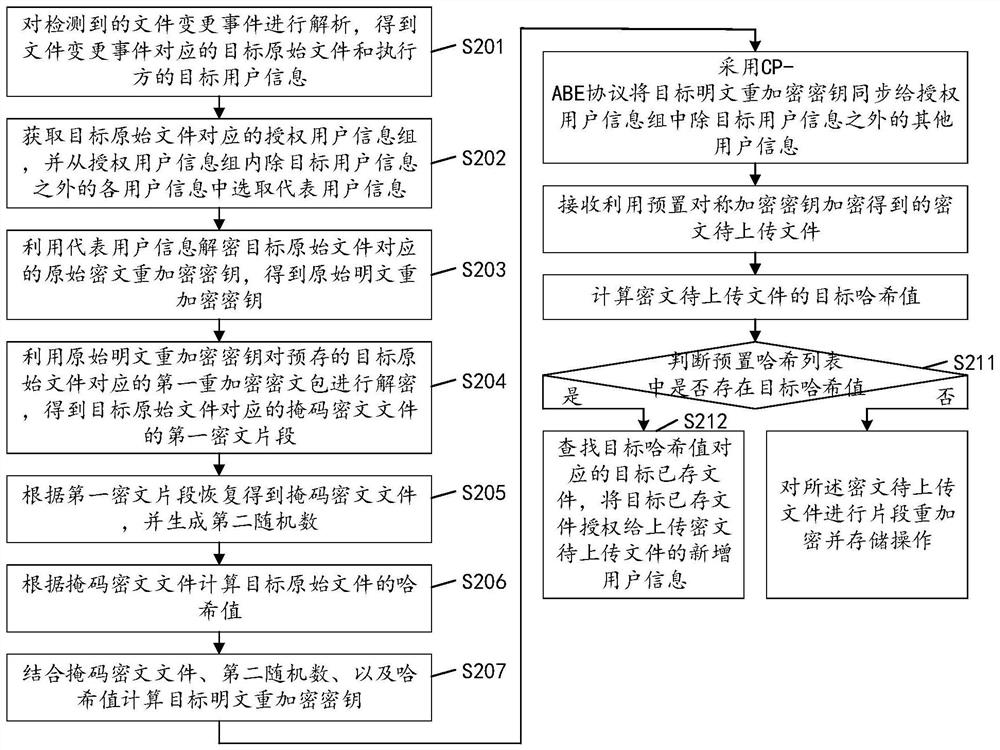
[0073] see figure 2 , figure 2 It is another implementation flowchart of the method for updating data access rights in the embodiment of the present invention, and the method may include the following steps:
[0074] S201: Analyze the detected file change event to obtain the target original file corresponding to the file change event and the target user information of the executor.
[0075] S202: Obtain an authorized user information group corresponding to the target original file, and select representative user information from all user information in the authorized user information group except the target user information.
[0076] S203: Use the original ciphertext re-encryption key corresponding to the target original file to decrypt the representative user information to obtain the original plaintext re-encryption key.
[0077] S204: Use the original plaintext re-encryption key to decrypt the pre-stored first re-encrypted ciphertext packet corresponding to the target o...
Embodiment 3
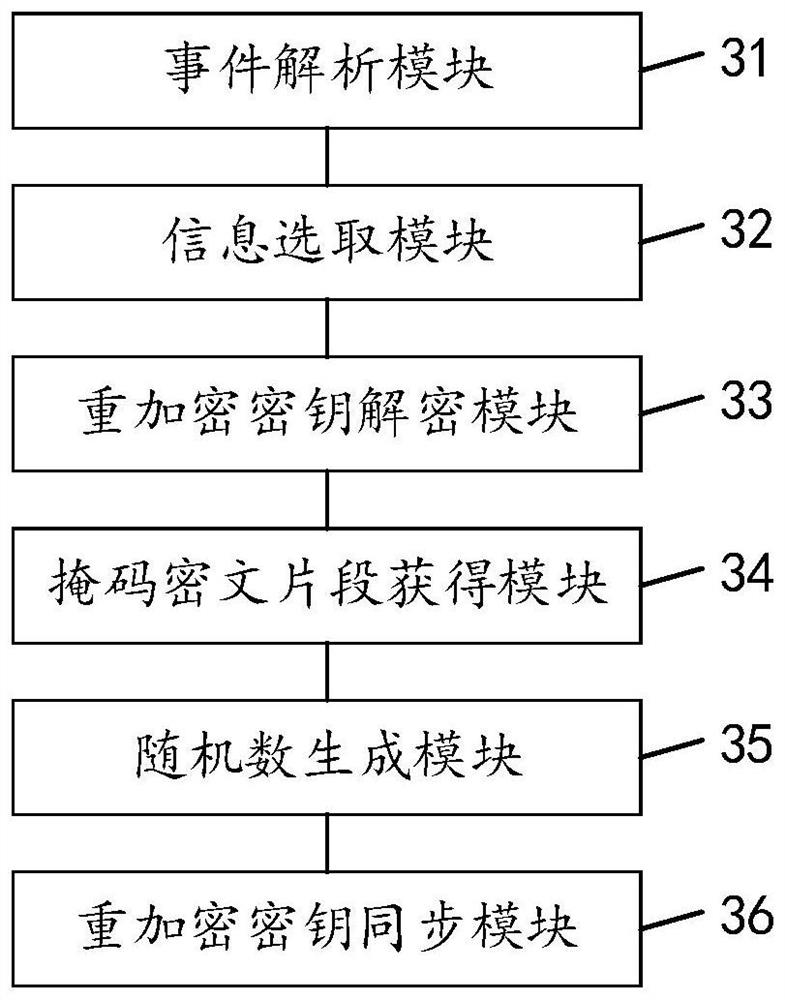
[0144] Corresponding to the above method embodiment, the present invention also provides a device for updating data access rights. The device for updating data access rights described below and the method for updating data access rights described above can be referred to in correspondence.
[0145] see image 3 , image 3 It is a structural block diagram of an apparatus for updating data access rights in an embodiment of the present invention, and the apparatus may include:
[0146] The event analysis module 31 is used to analyze the detected file change event, and obtain the target original file corresponding to the file change event and the target user information of the executor;
[0147] The information selection module 32 is used to obtain the authorized user information group corresponding to the target original file, and select representative user information from each user information in the authorized user information group except the target user information;
[014...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com