Method and system for mobile device security authentication based on bilinear pairing
A mobile device and security authentication technology, applied in the field of information security, can solve the problems of being vulnerable to attacks and low security performance, and achieve the effects of security assurance, avoiding counterfeit attacks and ensuring security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
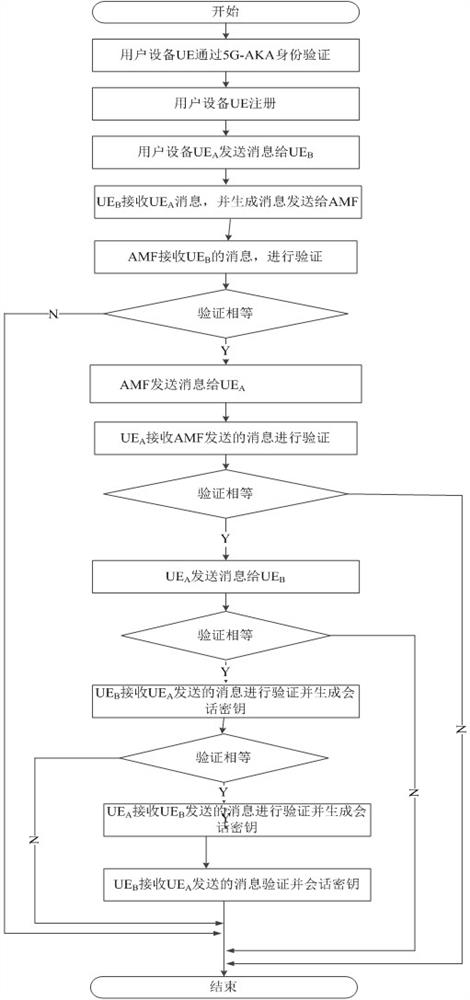
[0060] figure 2 It is a schematic diagram of the authentication process in Embodiment 1 of the present invention, such as figure 2 As shown, the security authentication process between mobile devices disclosed in this embodiment is as follows:
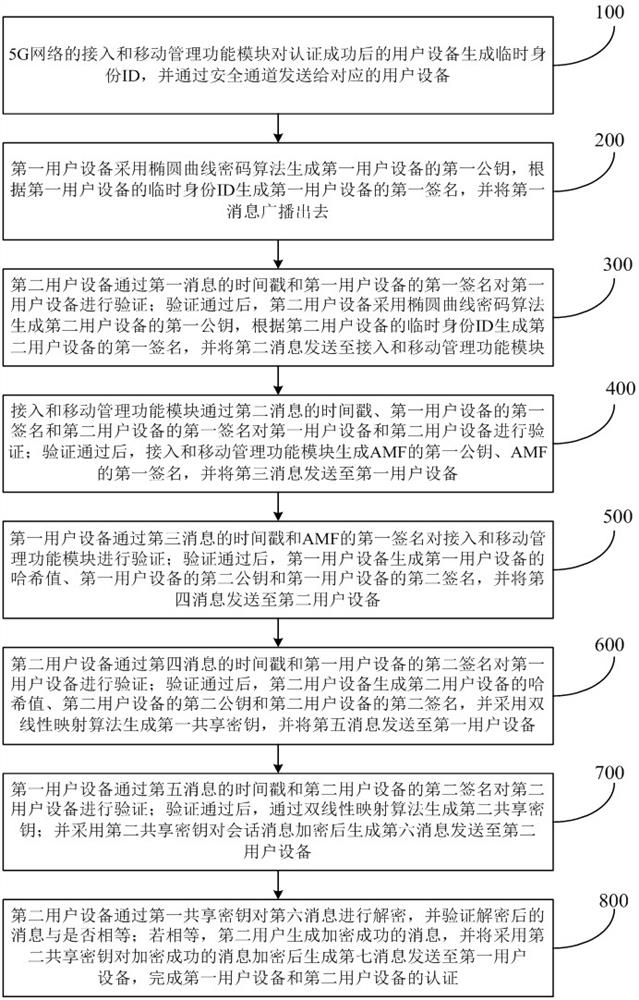
[0061] Step 100: The access and mobility management function module of the 5G network generates a temporary ID for the successfully authenticated user equipment, and sends it to the corresponding user equipment through a secure channel.
[0062] Step 200: The first user equipment generates the first public key of the first user equipment using the elliptic curve cryptographic algorithm, generates the first signature of the first user equipment according to the temporary identity ID of the first user equipment, and sends the first message Broadcast out. in, is the temporary identity ID of the first user equipment, is the first signature of the first user equipment, is the first public key of the first user equipment, is the...
Embodiment 2
[0071] Compared with Embodiment 1, this embodiment discloses specific methods of each public key, signature and authentication. image 3 It is a schematic diagram of the authentication process in Embodiment 2 of the present invention, such as image 3 As shown, the security authentication process between mobile devices disclosed in this embodiment is as follows:
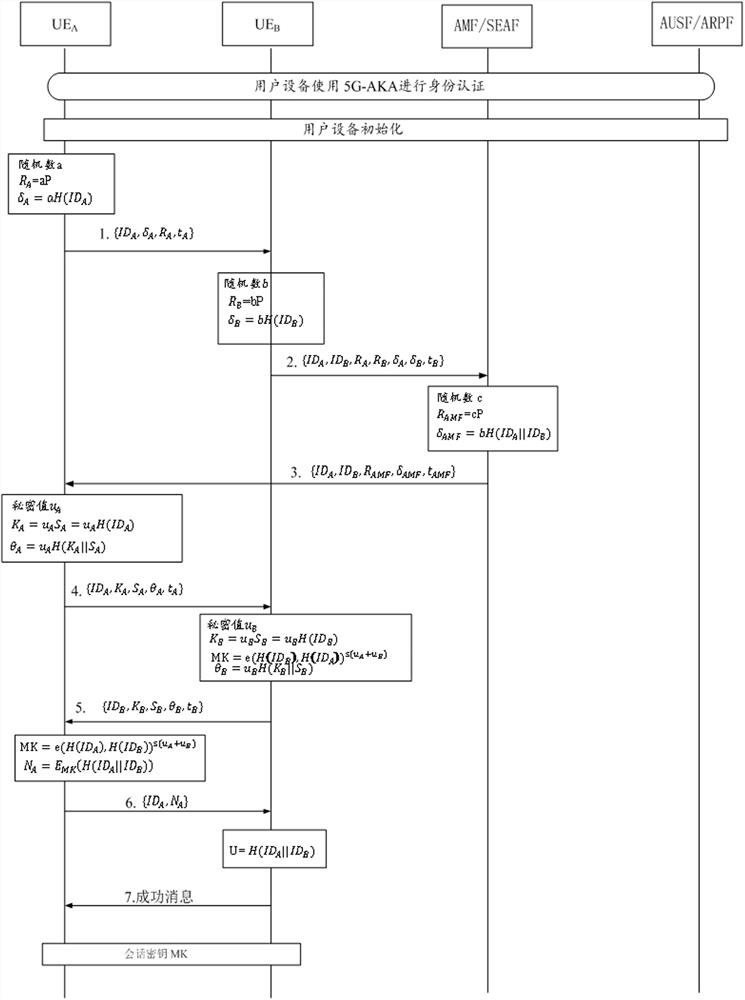
[0072] Step 1: The user equipment UE is initialized, and then the user equipment UE is authenticated through the protocol 5G-AKA protocol and the 5G network, and a secure channel is established after the authentication is successful. At this time, the AMF module generates the temporary identity ID of the user equipment UE, calculates S=H(ID), M=sS, and then sends M and ID to the user equipment UE through a secure channel.
[0073] Step 2: User Equipment First choose a random number a and calculate the public key =aP, for user equipment temporary status Perform signature calculation to get signature , then ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com