Container safety detection method based on machine learning
A machine learning and security detection technology, applied in the field of container technology, can solve problems such as man-in-the-middle attacks, achieve low false positive rate, high intrusion detection rate, and solve the problem of man-in-the-middle attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The present invention will be further described below in conjunction with the accompanying drawings.
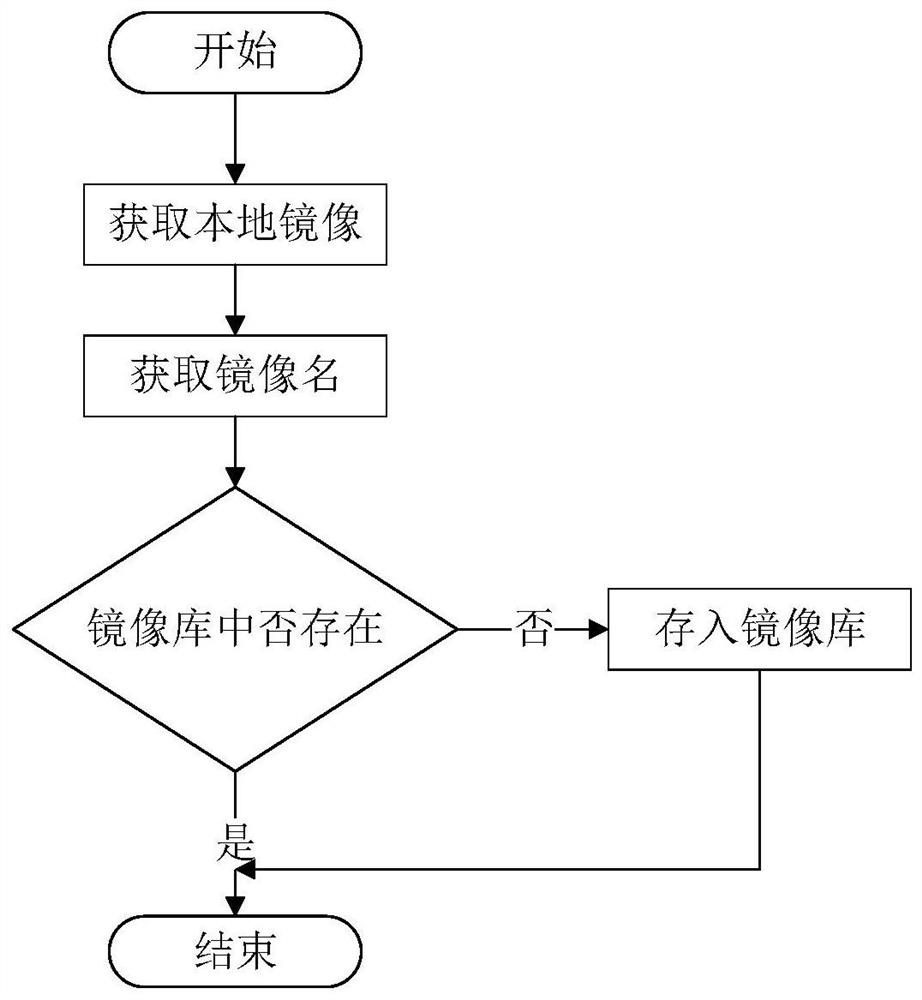
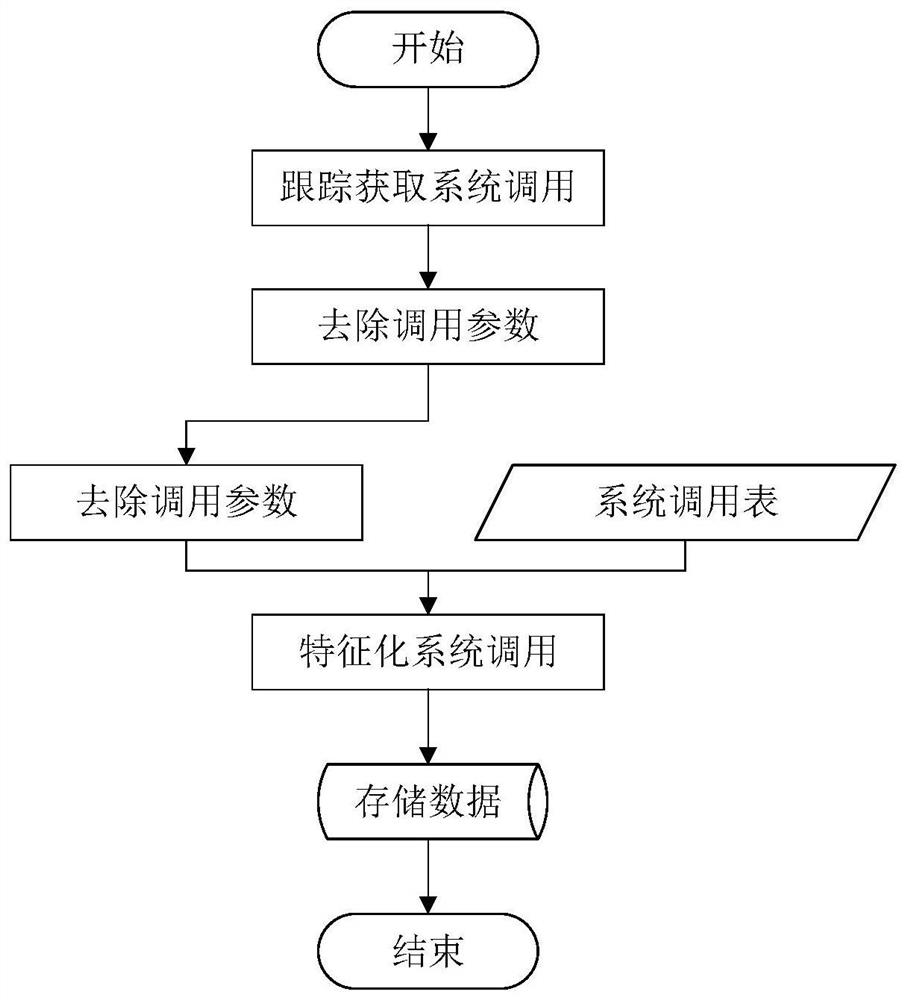
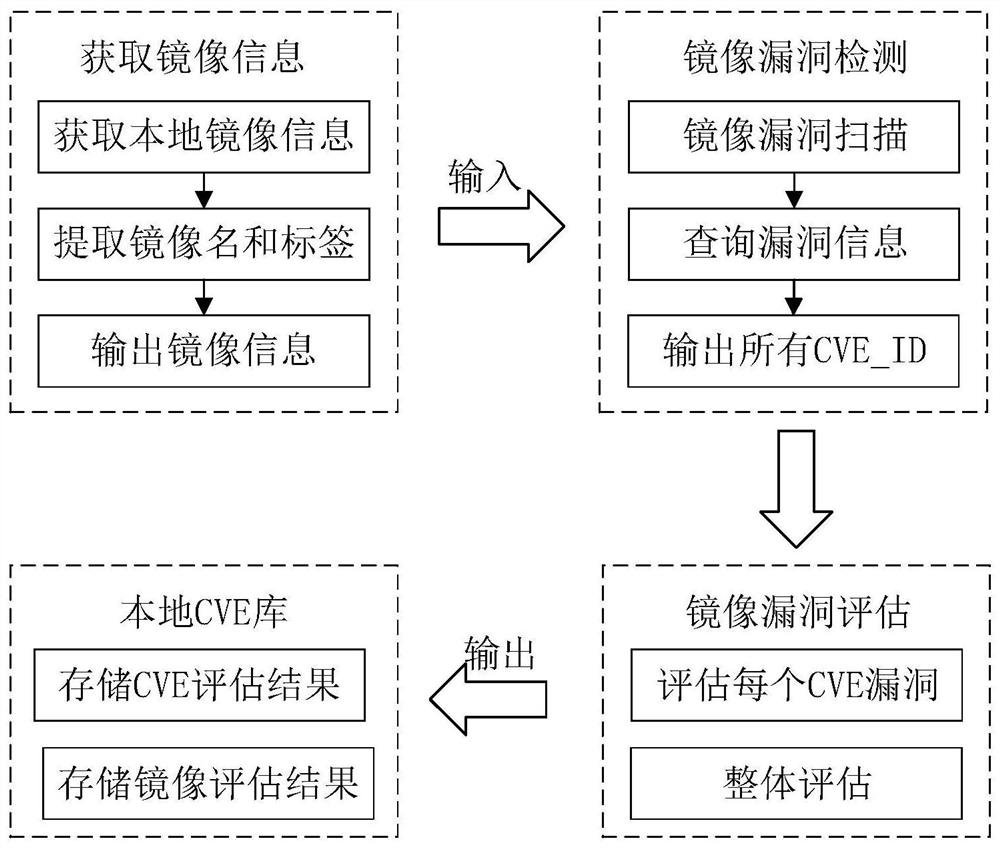
[0030] Such as Figure 1~5Shown is a container security detection method based on machine learning. First, when the user pulls the image from the Docker warehouse to the local, the method uses the image vulnerability scanning tool to scan the vulnerability information in the image pulled by the user. By comparing the general vulnerability information The library obtains the detailed information of the vulnerability, and then obtains the vulnerability risk score through the vulnerability assessment system, and finally collects all the vulnerability scores and information in the image, and evaluates the overall security of the image. If the image evaluation result is insecure, remind or delete the mirror, otherwise, the user can download the mirror normally and allow the mirror to be used. After the user creates a container through the mirror image, the method enters th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com