Cooperative identity verification method for large-scale wireless sensor network
An identity verification method and wireless sensor technology are applied in the field of Internet of Things security to achieve the effect of reducing storage space requirements, less memory consumption, and meeting the needs of collaborative verification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The specific implementation manner of the present invention will be described in detail below in combination with the technical scheme and accompanying drawings.
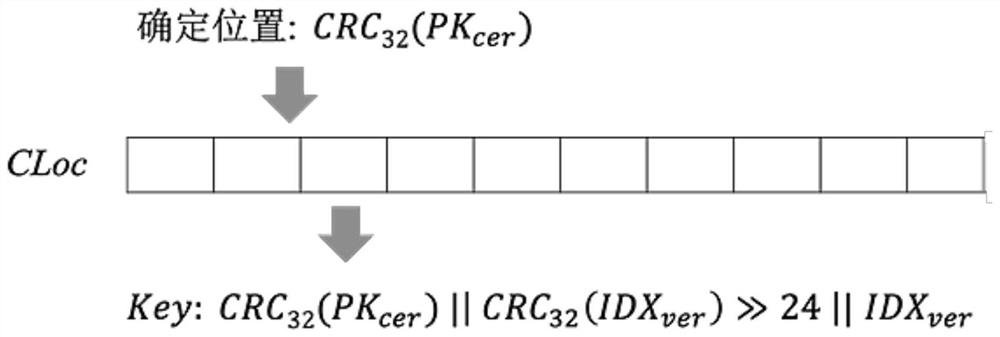
[0029] The structure of the locator CLoc based on the cuckoo hash designed by the present invention is as follows figure 1 As shown, similar to the basic cuckoo hash, CLoc first constructs a hash table for storing key values. Second, two hash functions h are required 1 (·), h 2 (·) is used to determine the two possible positions of the inserted value.
[0030] The insertion operation of the CLoc locator is as follows:
[0031] (1) Perform CRC-32 function calculation on the public key value attached to the verified certificate: CRC 32 (PK cer ).
[0032] (2) Calculate the Key:CRC to be stored in the locator 32 (PK cer )||CRC 32 (IDX ver )>>24||IDX ver .
[0033] (3) Input the obtained 32-bit check code into a hash function to obtain the first possible storage position of the K...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com