A method, system and storage medium for identifying malware mining
A malicious software and identification method technology, applied in the field of network security, can solve the problems that deformation and packing methods are difficult to extract effective features, dynamic analysis methods are not very applicable, and computer resources are wasted, etc., so as to achieve consumption of less resources, Low false positive rate, highly targeted effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
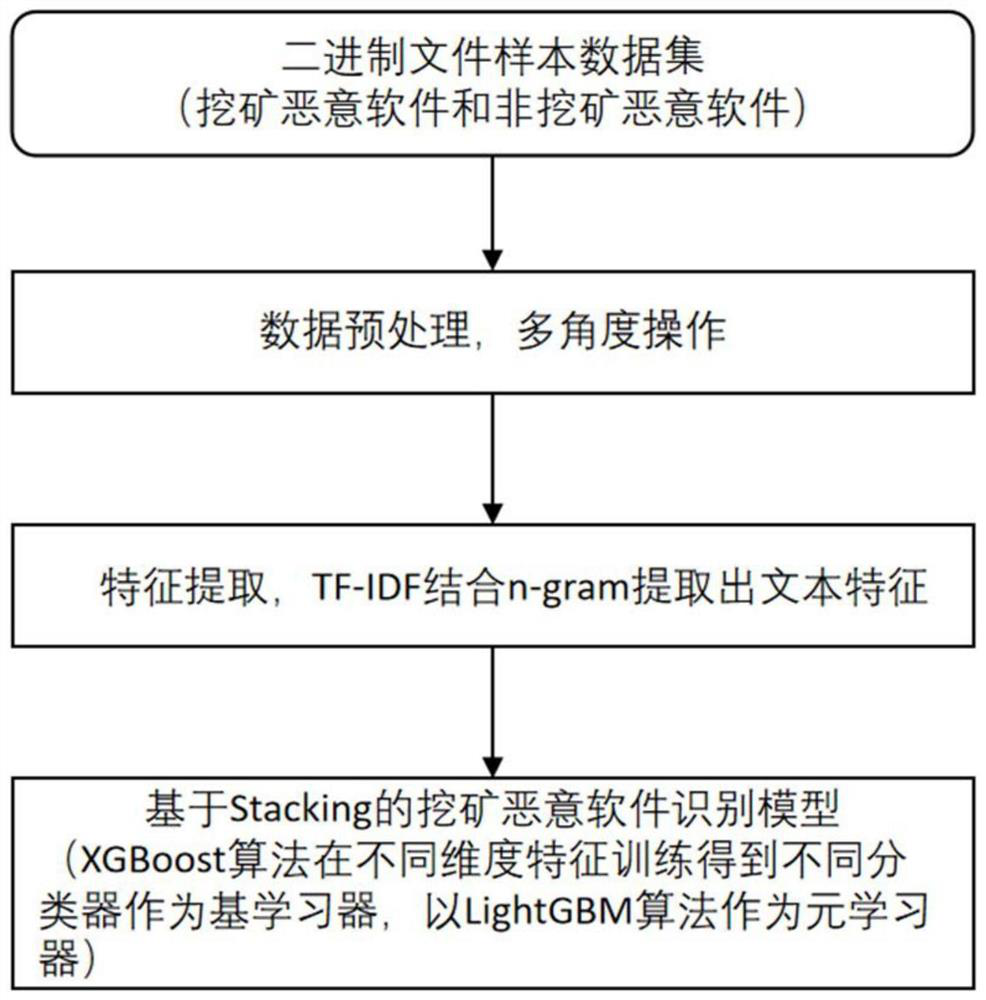
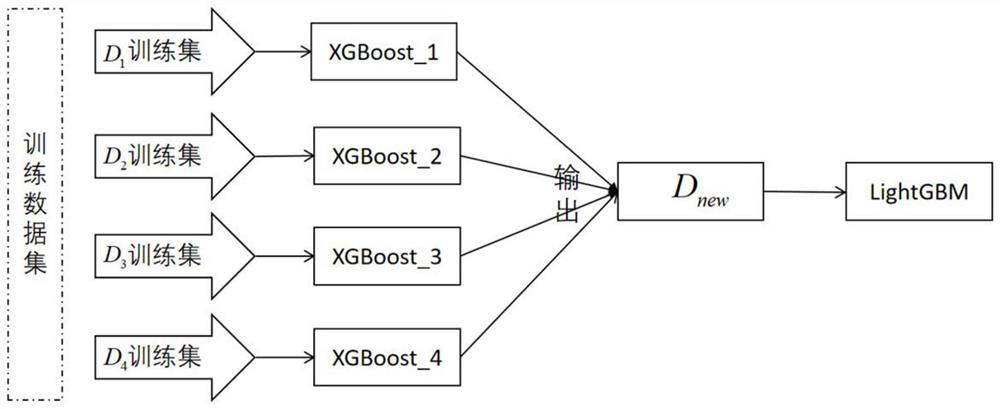
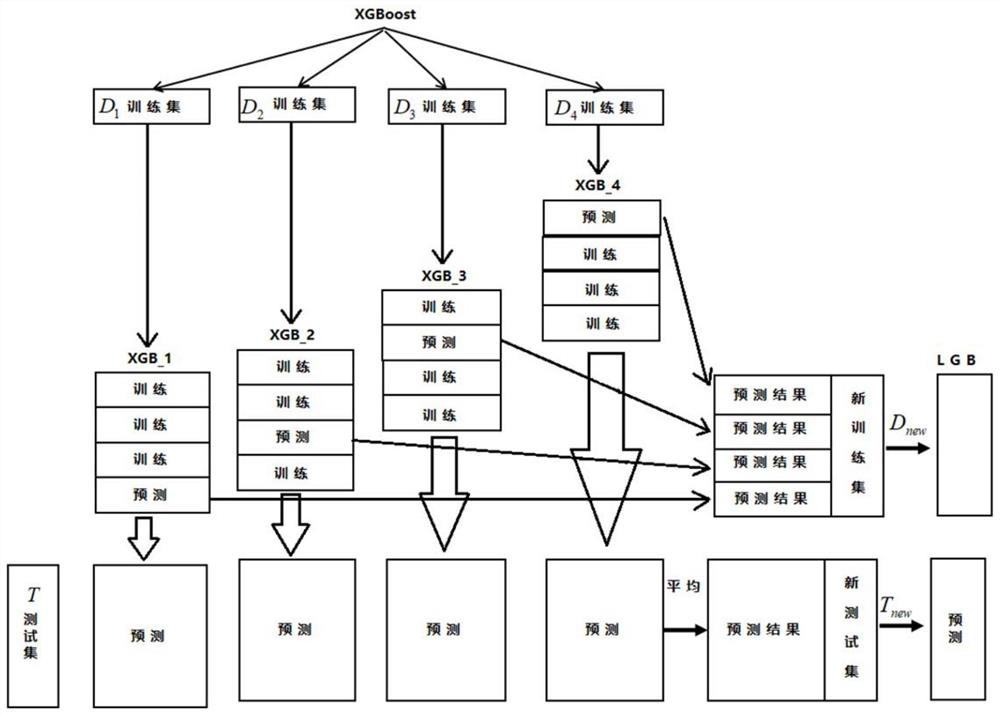
[0057] This embodiment provides a method for identifying mining malware. First, based on the binary file sample, through multi-dimensional analysis, it is preprocessed using a static analysis method, and vectorized to extract the multi-dimensional features of effective mining malware. , and then build a multi-model integrated mining malware recognition model.
[0058] Such as figure 1 As shown, the method of this embodiment specifically includes the following steps:
[0059] S1. Data preprocessing, performing multi-dimensional data operations on the original binary sample data set composed of mining malware and non-mining malware, to obtain corresponding characteristic data of different dimensions;
[0060] More specifically, in step S1, the multi-dimensional data operation includes:
[0061] For the binary file sample, read the file in the form of binary bytecode, and then decode it into a string, and filter out the string with a length within a certain interval;
[0062] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com