Web vulnerability static detection method and system based on taint analysis and medium
A taint analysis and static detection technology, applied in the field of network security, can solve the problems of unsupported inter-process analysis, large manual experience, and low detection accuracy, so as to improve detection accuracy, improve detection ability, and reduce false alarm rate Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
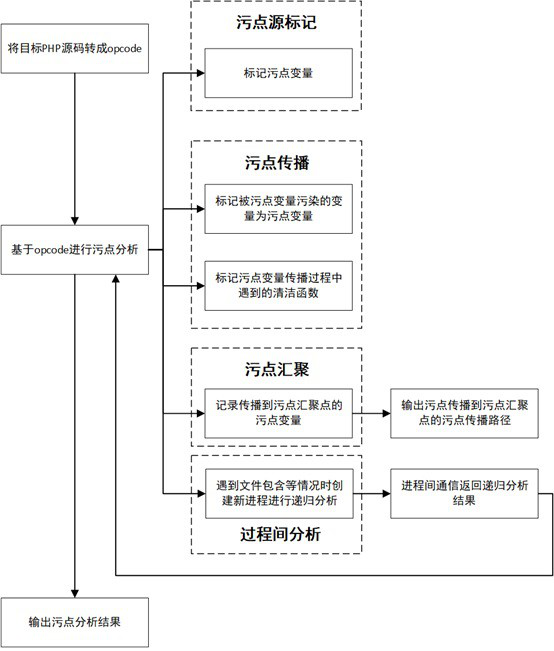
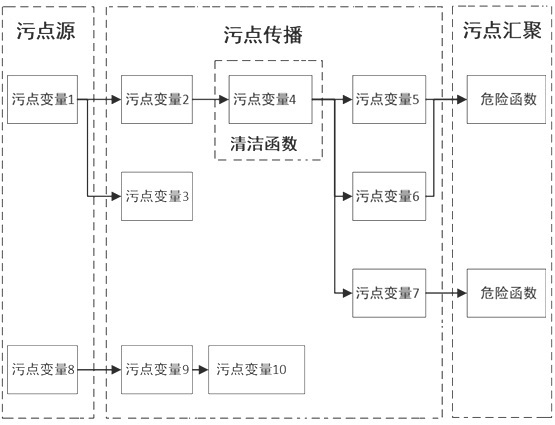
[0051] The following takes the code fragment vul.php containing the command injection vulnerability as an example to illustrate the process of using the static detection method for web vulnerabilities based on taint analysis of the present invention to detect vulnerabilities. For the process diagram, see Figure 4 .
[0052] #vul.php
[0053] php
[0054] include "test.php";
[0055] $dir=$_GET["dir"];
[0056] $dir=str_replace("whoami", "", "$dir");
[0057] system1("ls -al". $dir);
[0058] >
[0059] #test.php
[0060] php
[0061] function system1($command1, $command2){
[0062] $command=$command1.$command2;
[0063] return system($command);
[0064]}
[0065] 1) As shown in Table 1, convert the target php source code vul.php into opcode.
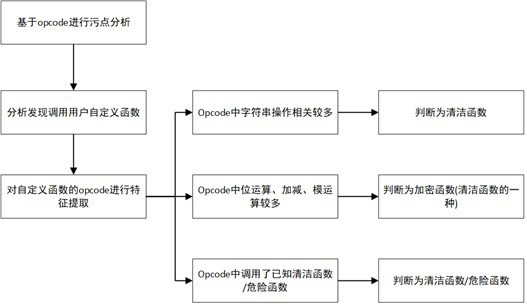
[0066] 2) Stain analysis based on opcode
[0067] As shown in Table 1, the instruction INCLUDE_OR_EVAL is encountered, and the value of its operand op2 is INCLUDE, indicating that this is a file inclusion, so the taint a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com