Ddos attack defense method and device based on browser fingerprint recognition
A browser fingerprint and browser technology, applied in the field of network security, can solve problems such as poor, inability to distinguish attack traffic, and other users affecting defense effects, achieve fine-grained control, reduce network bandwidth and computer resource consumption, and network adaptation. strong effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
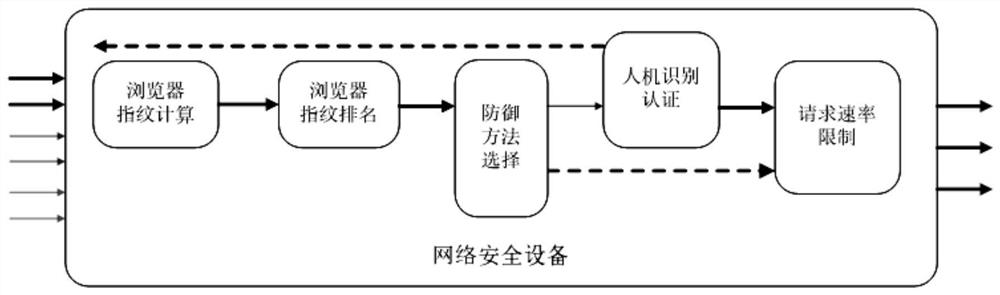
[0050] see figure 1 and figure 2 , providing a DDoS attack defense method based on browser fingerprint identification, comprising the following steps:
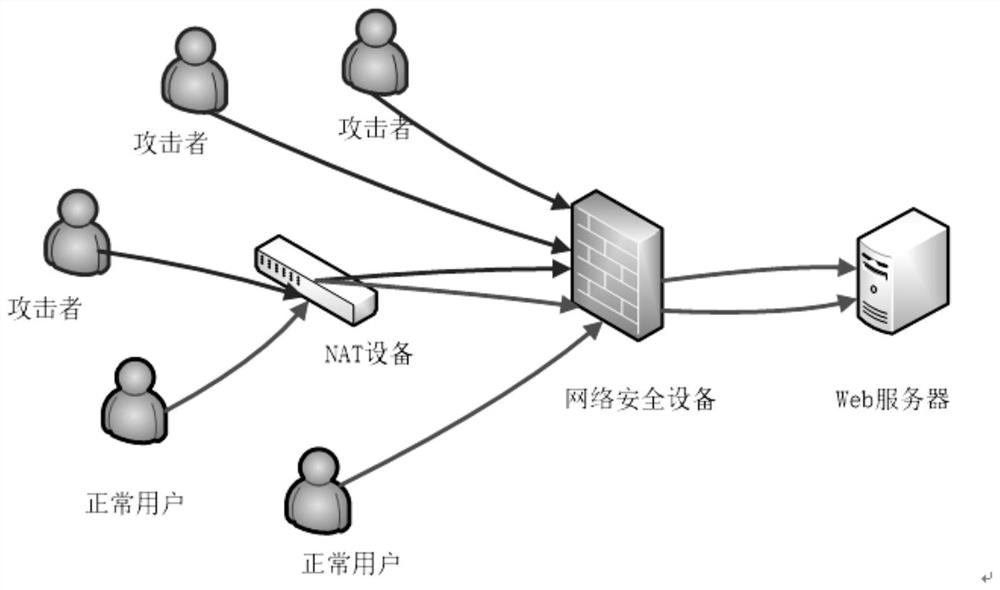
[0051] The network security device is set up on the front end of the Web server, and the HTTP request sent to the Web server is filtered by the network security device;
[0052] When the network security device receives the HTTP request, it extracts the fingerprint of the browser sending the HTTP request according to the preset statistical period, and obtains the browser fingerprint ID;
[0053] When each statistical period ends, the HTTP request feature calculation is performed to obtain a feature score, and the feature score is sorted from high to low to obtain the top N browser fingerprint IDs;
[0054] Captcha authentication and request rate limiting are performed on the top N browser fingerprint IDs in each statistical period.
[0055] In this embodiment, the browser fingerprint ID includes the source IP, the content ...
Embodiment 2
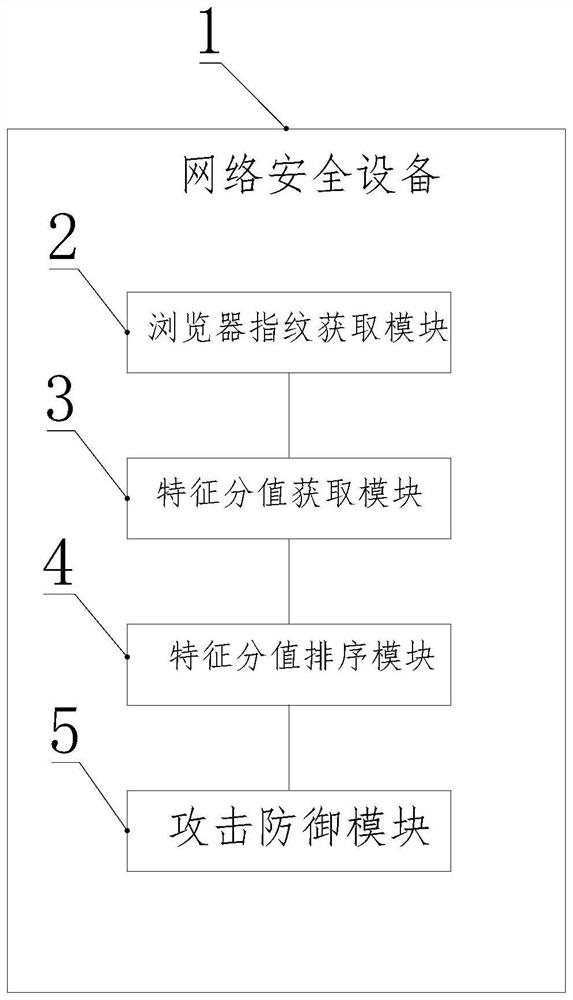
[0088] The present invention also provides a DDoS attack defense device based on browser fingerprint identification, the DDoS attack defense method based on browser fingerprint identification using the first aspect or any possible implementation thereof, including:
[0089] A network security device 1, the network security device is set up at the front end of the Web server, and the network security device is used to filter HTTP requests sent to the Web server;
[0090] The browser fingerprint acquisition module 2 is used to extract the fingerprint of the browser sending the HTTP request according to the preset statistical cycle when the network security device receives the HTTP request, and obtain the browser fingerprint ID;
[0091] The feature score acquisition module 3 is used to calculate the feature score of the HTTP request when each statistical cycle ends;
[0092] The feature score sorting module 4 is used to sort the feature score from high to low to obtain the top N...
Embodiment 3
[0096] Embodiment 3 of the present invention provides a computer-readable storage medium, in which the program code of the DDoS attack defense method based on browser fingerprint identification is stored. Instructions of the DDoS attack defense method based on browser fingerprint identification in any possible implementation manner.
[0097] The computer-readable storage medium may be any available medium that can be accessed by a computer, or a data storage device such as a server, a data center, etc. integrated with one or more available media. The available medium may be a magnetic medium (for example, a floppy disk, a hard disk, or a magnetic tape), an optical medium (for example, DVD), or a semiconductor medium (for example, a solid state disk (SolidStateDisk, SSD)) and the like.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com