Authentication key negotiation method with anti-key exposure characteristic in Internet of Vehicles environment
An authentication key negotiation and Internet of Vehicles technology, applied in the field of authentication key negotiation mechanism, can solve problems such as long duration of damage, security attacks, smart card theft attacks, etc., to achieve anti-key exposure, session key security, The effect of increased communication costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
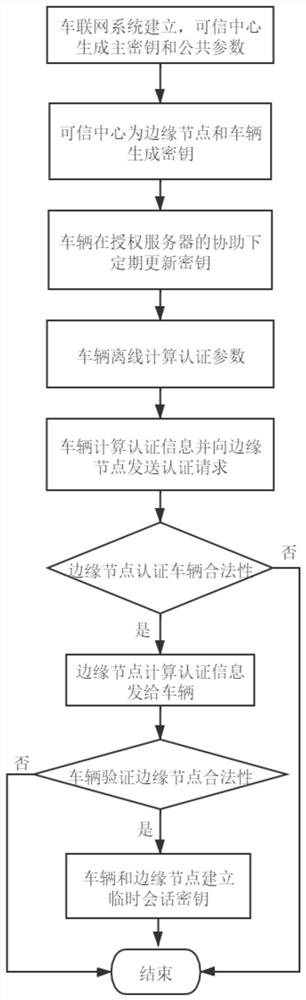
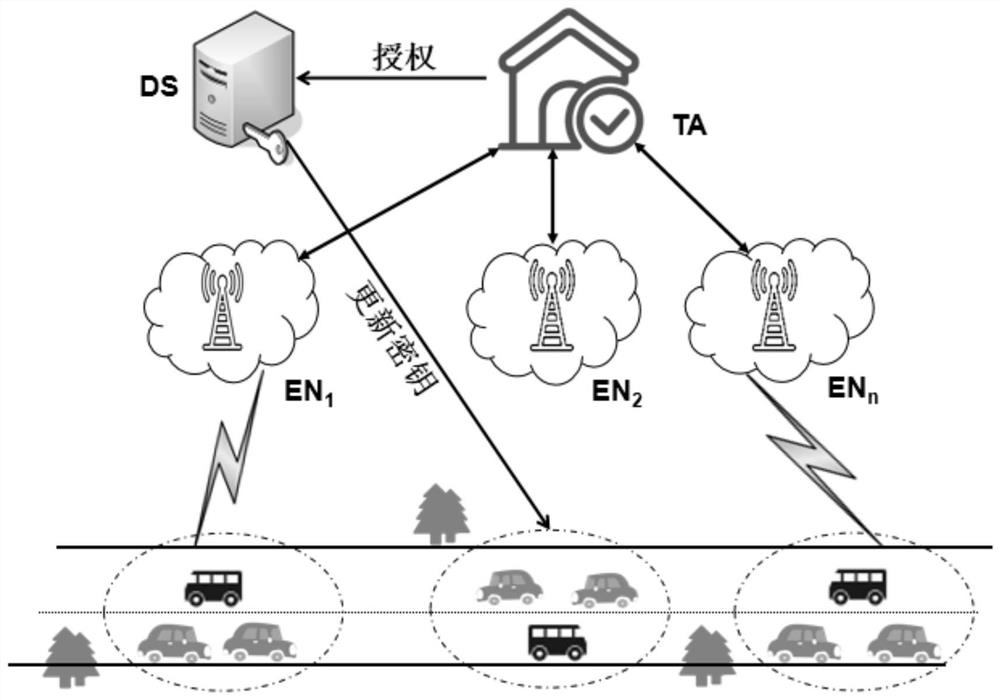
[0044] In recent years, with the rapid development of intelligent transportation systems, Internet of Vehicles has become a research hotspot, which is of great significance to improve traffic efficiency and safety, but it also faces some challenges. On the one hand, in the Internet of Vehicles, information is transmitted on open channels, so it is vulnerable to attacks from illegal users, such as forgery attacks, impersonation attacks, and replay attacks. Therefore, how to protect the privacy and security of users is the focus of research; on the other hand, due to the fast-moving characteristics of vehicles, the designed solution needs to be efficient, flexible, and low-latency while meeting the communication security requirements. Authenticated key agreement protocol is an important mechanism to protect data transmission. At present, some scholars have proposed an authenticated key agreement protocol suitable for the Internet of Vehicles environment. However, none of these p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com