Android malicious software detection system and method based on heterogeneous graph learning
A malware and detection system technology, applied in the field of network security, which can solve the problems of inability to detect encryption and dynamically loaded malicious programs, and the detection rate cannot guarantee fast streaming response, achieving high path coverage, high-efficiency detection performance, and detection. high performance effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
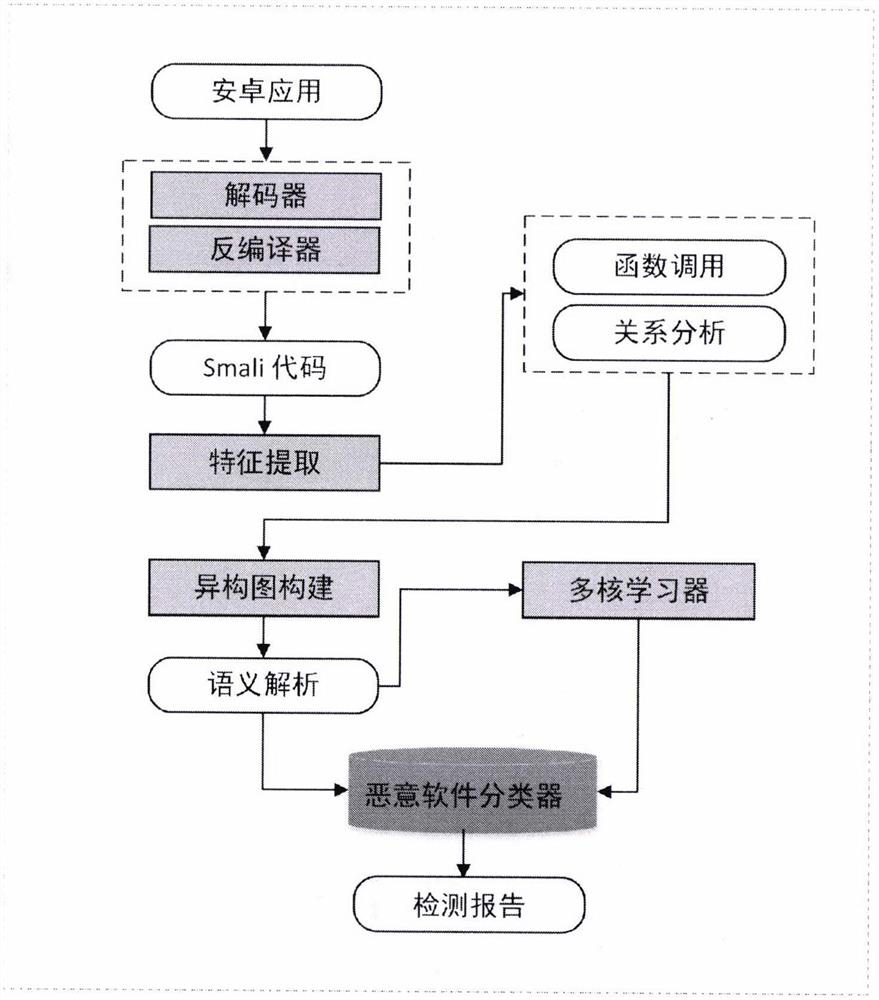
[0035] Such as figure 1 As shown, as a preferred embodiment, the Android malware detection system based on heterogeneous graph learning of the present invention includes Android software decompression and decompilation unit, feature extraction unit, heterogeneous graph construction unit, multi-core learning unit and malicious software Software detection unit.
[0036] The Android software decoding and decompiling unit utilizes currently public and common decoding and decompiling techniques to decode and decompile the Android software to be detected. Specifically, at first the software to be detected is decoded into an APKs file, and then the APKs file after decoding is decompiled into Smali code using a decompilation tool, and the Smali code after the decompilation includes the internal function call relationship and Link structure relationship.
[0037] The feature extraction unit extracts the internal function call relationship of the software to be detected, and according...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com