Transparent encryption method and device for industrial control network, equipment and storage medium
An industrial control network and transparent encryption technology, which is applied in network interconnection, secure communication devices, data exchange networks, etc., can solve cumbersome problems and achieve the effects of convenient access, difficult troubleshooting, and error-prone
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
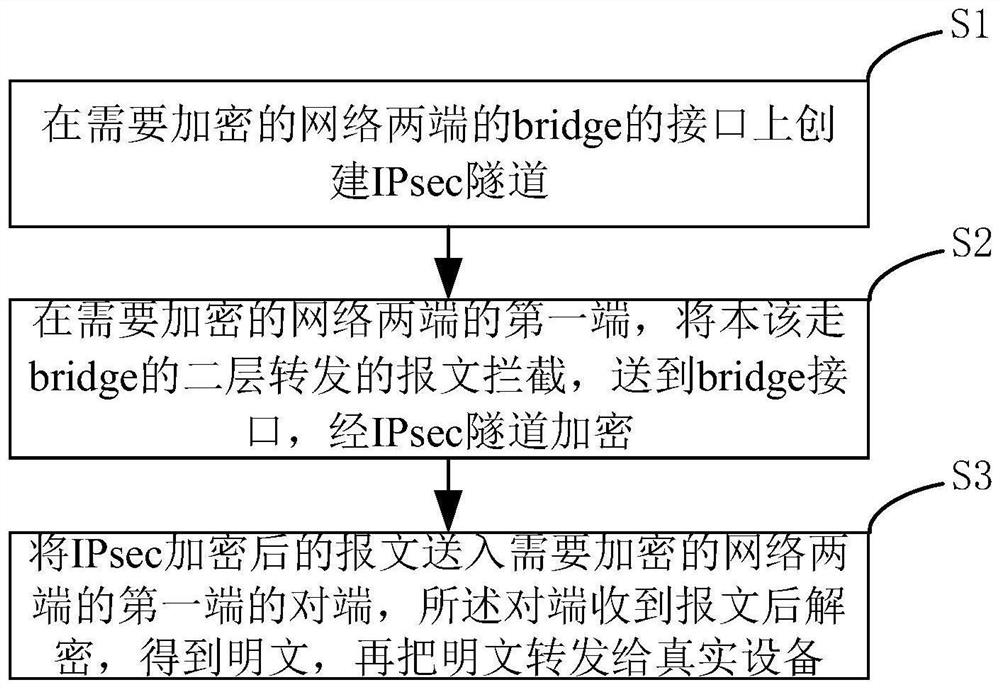
[0029] like figure 1 As shown, the transparent encryption method of the industrial control network provided by the embodiment of the present application,
[0030] include:
[0031] S1: Create an IPsec tunnel on the interface of the bridge at both ends of the network that needs to be encrypted;
[0032] S2: At the first end of the two ends of the network that need to be encrypted, intercept the second-layer forwarded message that should go through the bridge, send it to the bridge interface, and encrypt it through the IPsec tunnel;
[0033] S3: Send the IPsec-encrypted message to the first peer at the two ends of the network that needs to be encrypted. After receiving the message, the peer decrypts the message to obtain the plaintext, and then forwards the plaintext to the real device.
[0034] In some embodiments, before creating an IPsec tunnel on the interfaces of bridges at both ends of the network requiring encryption, the method further includes: connecting two encrypti...
Embodiment 2
[0041] A transparent encryption device for an industrial control network, comprising:
[0042] Linux operating system, first encryption module, second encryption module, Bridge and IPsec channel;
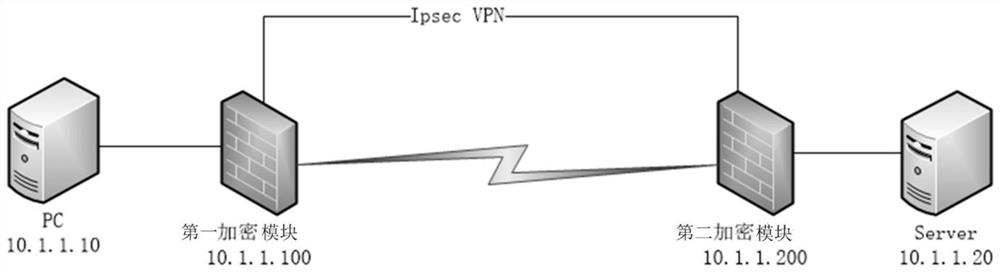
[0043] Access the first encryption module and the second encryption module at both ends of the network that require encryption; the first encryption module and the second encryption module both have two interfaces, and the first interface in the two interfaces is used as an encryption interface, The second interface is the sending interface, add these two interfaces into a bridge, configure the IP address on the bridge interface according to the network environment, create an IPsec tunnel on the bridge interface at both ends of the network that needs to be encrypted, and apply the IPsec protocol to the VPN ; At the first end of the two ends of the network that need to be encrypted, in the linux kernel protocol stack, intercept the message that should be forwarded by the second layer...
Embodiment 3
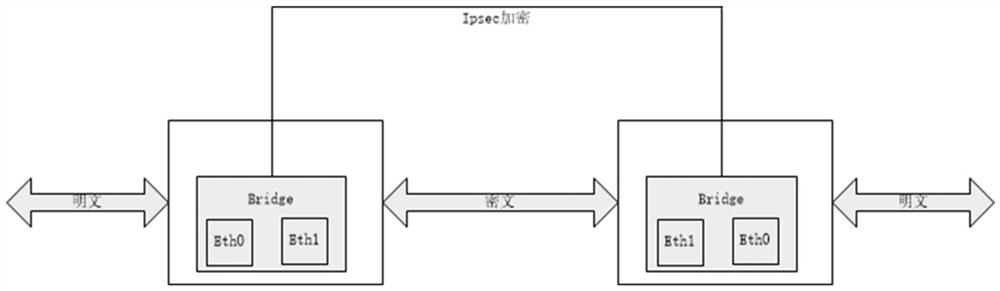
[0045] like figure 2 As shown, a transparent encryption device for industrial control network, including:
[0046] Linux operating system, first encryption module, second encryption module, Bridge and IPsec channel;
[0047] Access the first encryption module and the second encryption module at both ends of the network that needs to be encrypted; the first encryption module and the second encryption module all have two interfaces eth0 and eth1, and the first interface in the two interfaces serves as The encrypted interface eth0 and the second interface is the sending interface eth1. Add these two interfaces to a bridge, configure IP addresses on the bridge interface according to the network environment, create IPsec tunnels on the bridge interfaces at both ends of the network that need to be encrypted, and set the IPsec The protocol is applied to the VPN; at the first end of the two ends of the network that need to be encrypted, rules are created through ebtable, and the mes...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com