Fine particle data protection method based on security model
A security model and data protection technology, applied in digital data protection, electronic digital data processing, computer security devices, etc., can solve problems such as difficulty in implementation and data leakage, and achieve authority, consistency, efficiency and security. sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] The present invention will be further described below in conjunction with the accompanying drawings.
[0037] The technical problem that the present invention mainly solves has following two aspects:
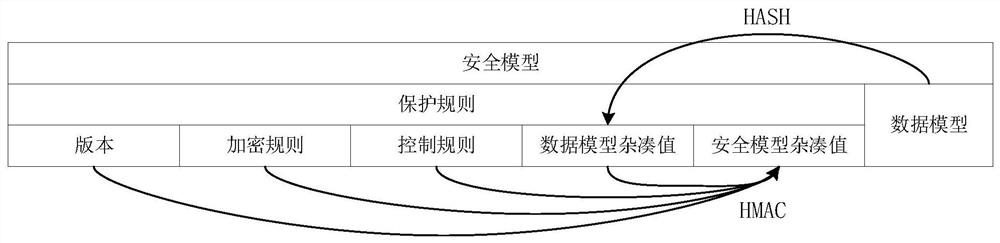
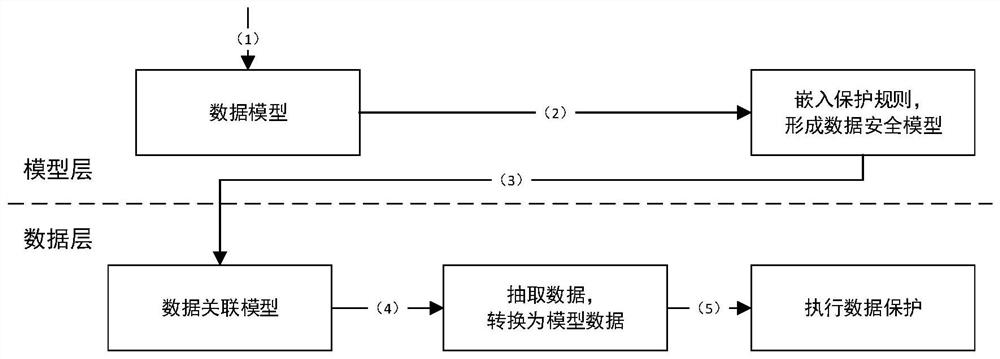
[0038] 1) The password-based security model generation method embeds protection rules in the data model to solve the problem of data protection configuration management complexity, high professional requirements, and possible insufficient protection, resulting in data leakage. This method abstracts the common business data into a data model, configures protection methods for the data model by professional security personnel, embeds protection rules in the data model, and implements strong binding between the protection rules and the data model based on cryptographic technology, forming a tamper-proof Capabilities security model that simplifies the management of data protection.
[0039] 2) Batch data protection technology, by associating and mapping the actual data to be...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com