Software authorization method and system and storage medium
A technology of software authorization and software, which is applied in the direction of program/content distribution protection, instruments, and electronic digital data processing. The method and usage scenarios are flexible, the cost of cracking is increased, and the effect is suitable for popularization and application
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
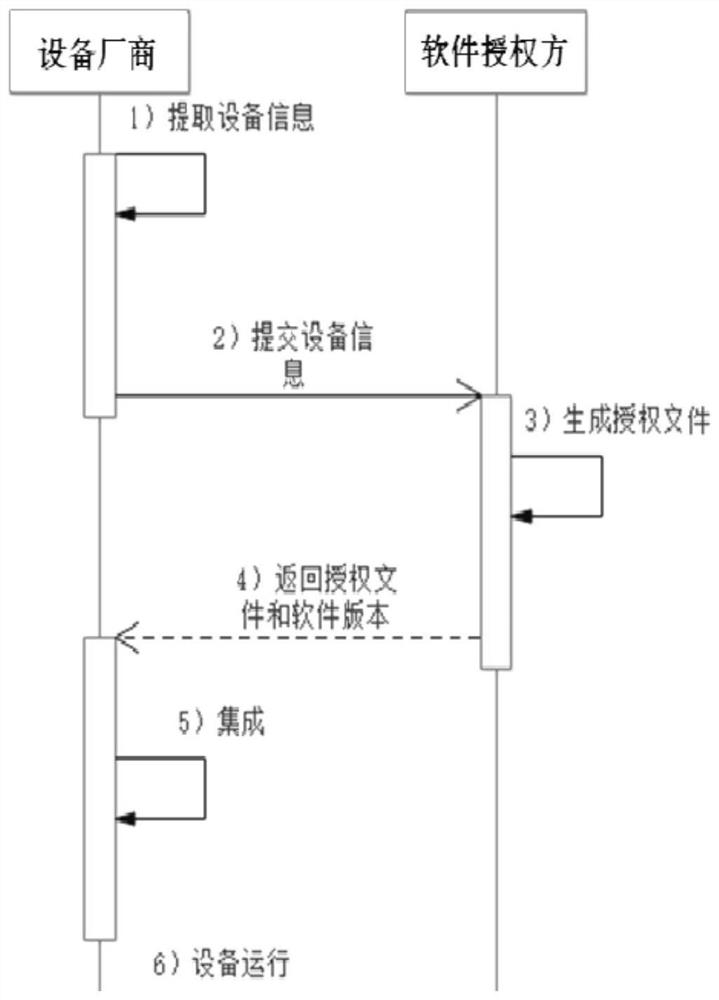
[0058] Such as figure 1 as shown, figure 1 It is a schematic flowchart of the software authorization method provided by Embodiment 1 of the present invention.
[0059] In this embodiment, the software authorization method includes the following steps:
[0060]S101. The software authorizer receives the device information collected by the device manufacturer;
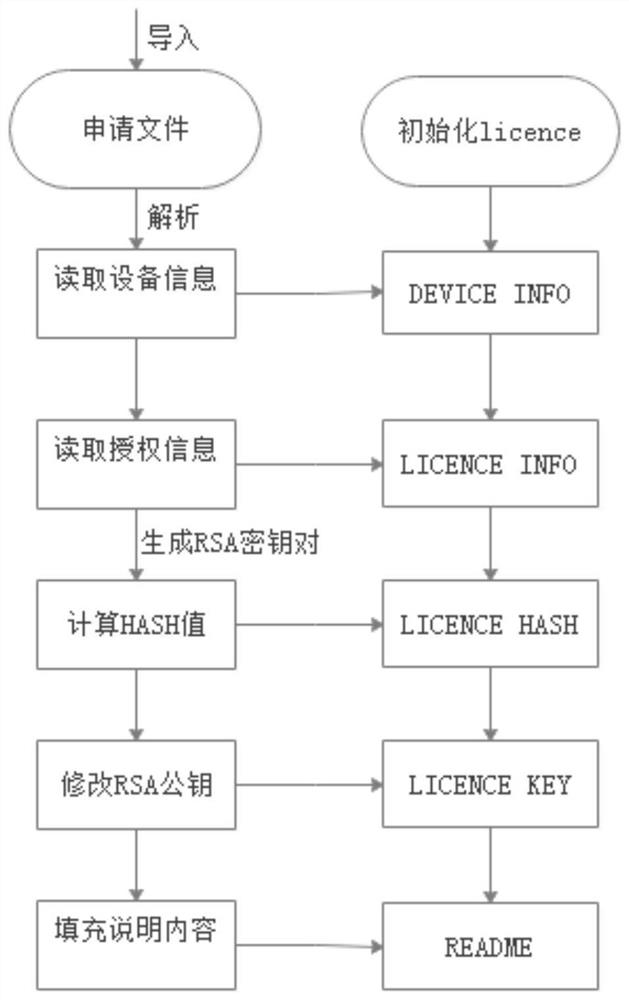
[0061] S102. The software authorizer generates an authorization file according to the received device information and corresponding authorization information;
[0062] S103. The software authorizer returns the authorization file and software version to the device manufacturer;
[0063] S104. The device manufacturer integrates the software version and places the authorization file as required;
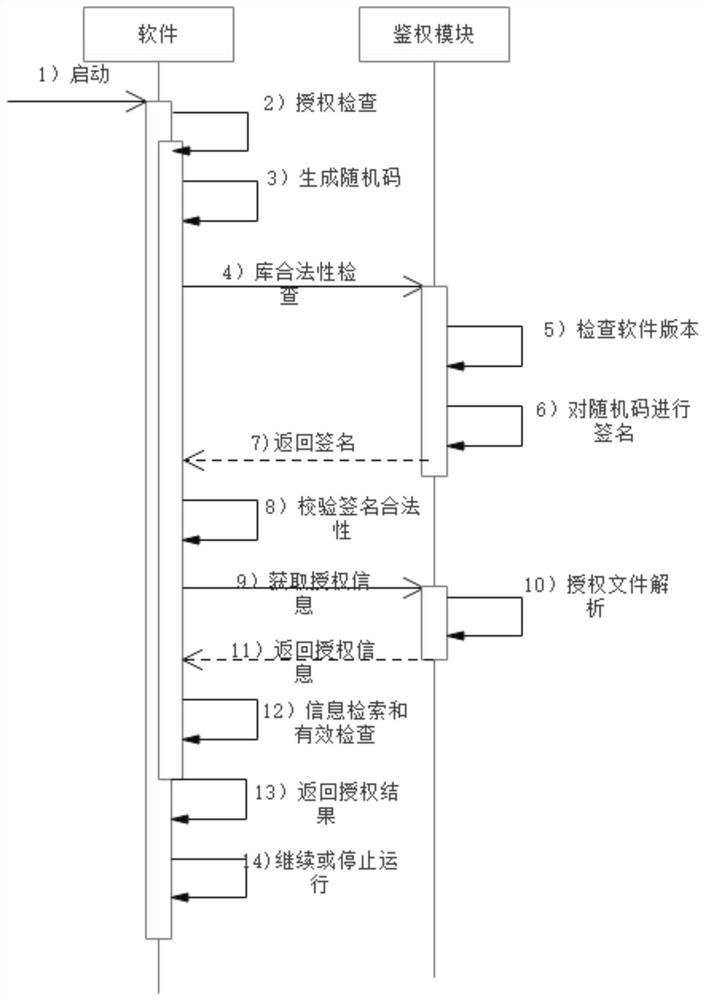
[0064] S105. After the device is running, the software loads the authentication module and performs authorization verification. If the verification is passed, it will run normally, otherwise it will stop running. It should be ...
Embodiment 2
[0069] In this embodiment, the software authorization method includes the following steps:
[0070] S201. The software authorizer receives the device information collected by the device manufacturer;
[0071] S202. The software authorizer generates an authorization file according to the received device information and corresponding authorization information;
[0072] S203. The software authorizer returns the authorization file and software version to the device manufacturer;
[0073] S204. The device manufacturer integrates the software version and places the authorization file as required;
[0074] S205. After the device is running, the software loads the authentication module and performs authorization verification. If the verification is passed, it runs normally, otherwise it stops running. It should be noted that after the device is running in this embodiment, the preferred setting mode is to select the software to automatically load the authentication module, but it is ...
Embodiment 3
[0087] In this embodiment, the software authorization method includes the following steps:
[0088] S301. The software authorizer receives the device information collected by the device manufacturer;
[0089] S302. The software authorizer generates an authorization file according to the received device information and corresponding authorization information;
[0090] S303. The software authorizer returns the authorization file and software version to the device manufacturer;
[0091] S304. The device manufacturer integrates the software version and places the authorization file as required;
[0092] S305. After the device is running, the software loads the authentication module and performs authorization verification. If the verification is passed, it runs normally, otherwise it stops running. It should be noted that after the device is running in this embodiment, the preferred setting mode is to select the software to automatically load the authentication module, but it is ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com