Biological recognition device for computer security control system
A computer security and biometric identification technology, applied in the field of biometric information identification, can solve problems such as poor security, and achieve the effects of thorough cleaning, reducing costs, and reducing the frequency of cleaning.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
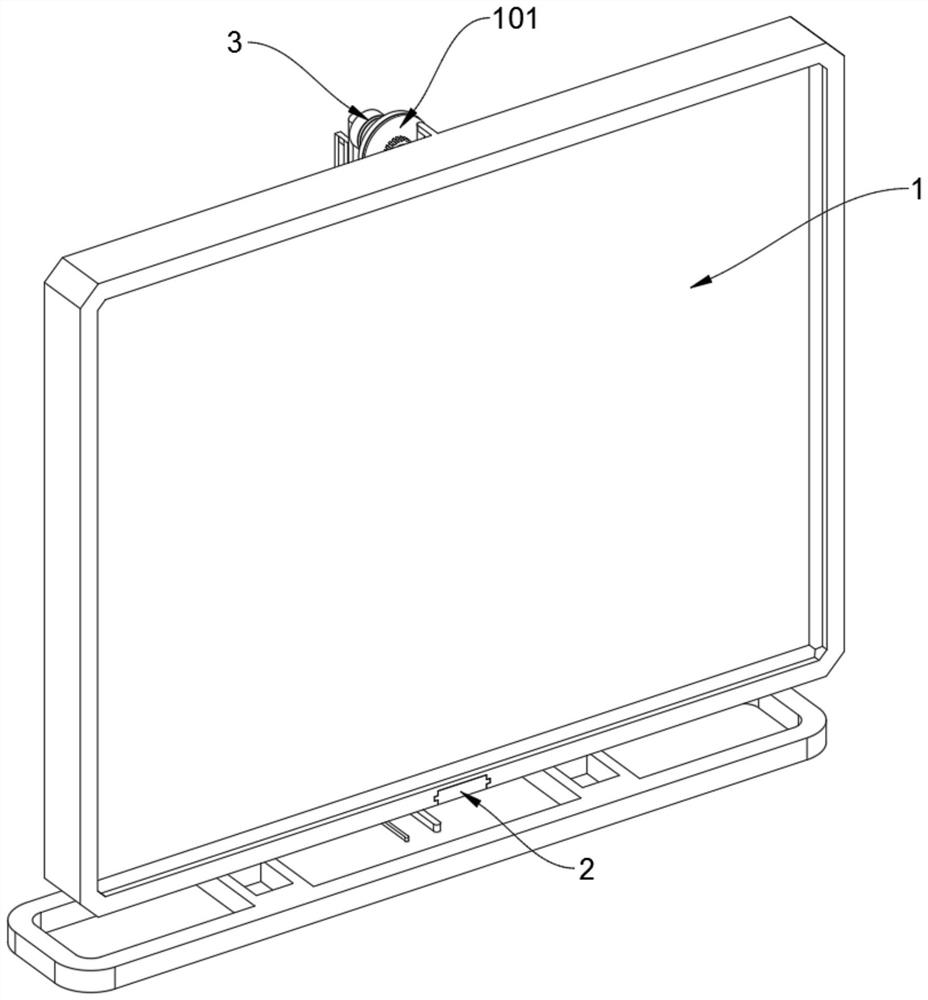
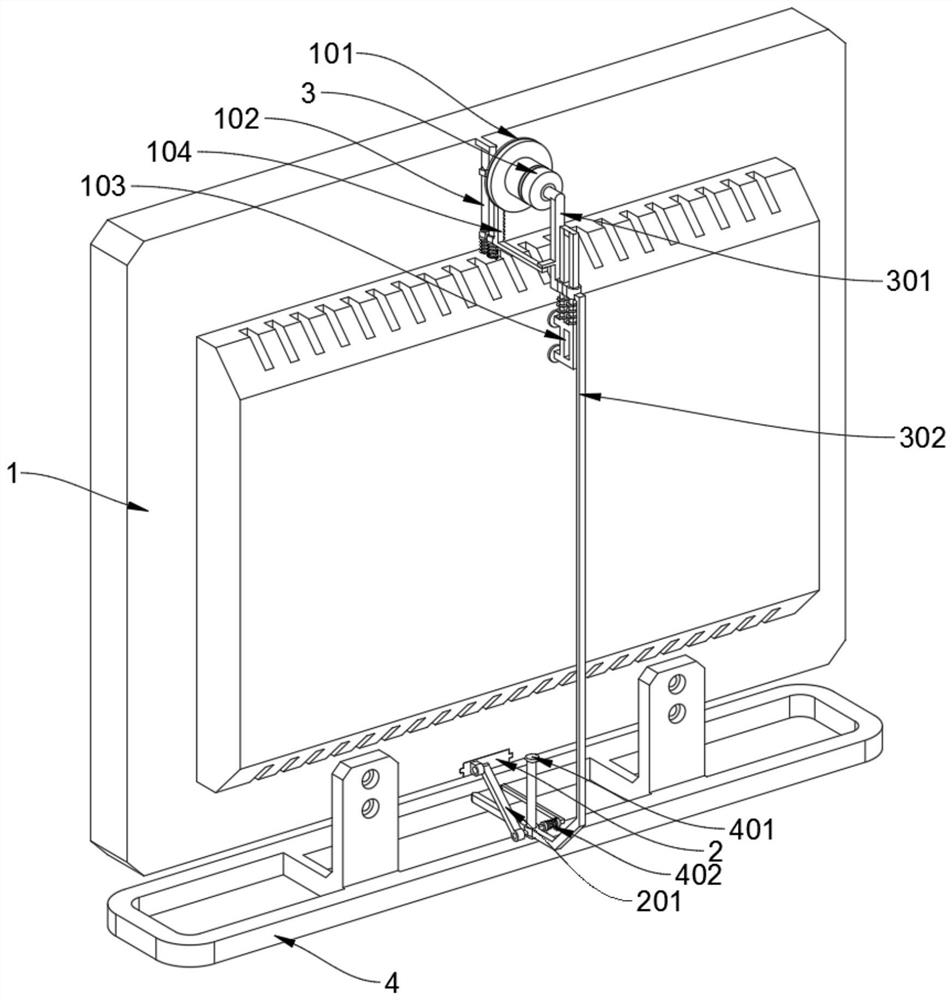
[0031] see Figure 2 to Figure 9 , Embodiment 1 provided by the present invention: a biometric identification device for a computer security control system, including a display screen 1; the display screen 1 includes a vertical support 103, and the back of the display screen 1 is square and protrudes from the middle top position lock of the casing A vertical support piece 103 is closely installed, and the vertical support piece 103 is composed of two vertical support poles welded at intervals, and a camera assembly 3 is installed on the two vertical support poles through spring pushing and sliding; the display screen 1 also Including the brush plate 101, a brush plate 101 is rotatably installed in the middle position of the top of the back shell of the display screen 1, and a circular sponge is fixed on the rear end surface of the brush plate 101 by Velcro, and the center of the rear end surface of the brush plate 101 is There is a driven gear at the center. Through the driven...
Embodiment 2
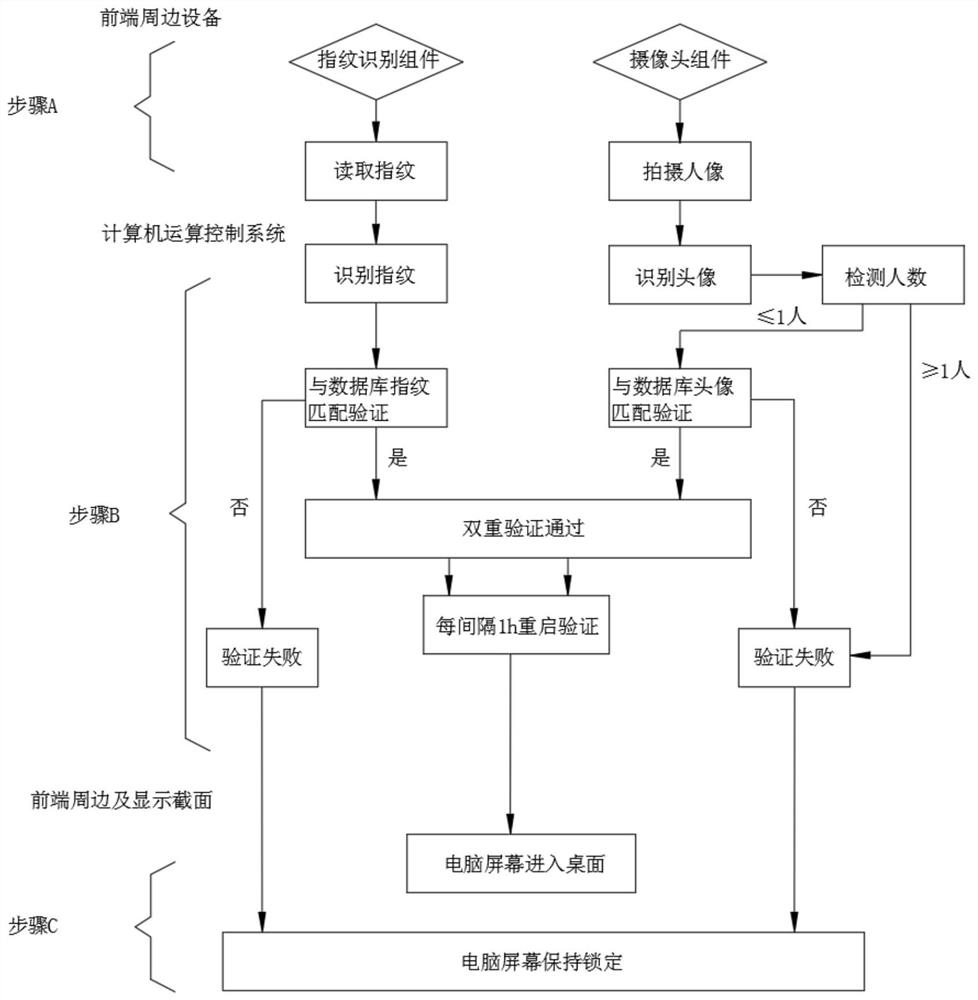
[0036] see figure 1 , Embodiment 2 provided by the present invention: a biometric identification device for a computer security control system, which also includes the following workflow:
[0037] 1. First, the fingerprint identification component 2 and the camera component 3 collect the fingerprint and facial features of the operator at the same time;
[0038] 2. Identify the collected fingerprints and facial features and match them with the fingerprints and facial features in the computer database;
[0039] 3. If the verification of fingerprints and facial features is successful, the computer screen will work normally on the desktop. If the fingerprints and facial features are not all verified, the computer screen will remain locked on the welcome interface;
[0040] 4. After the verification is successful, restart the verification program every one hour. If the verification is successfully passed, continue to enter the desktop office. If the verification fails, exit the d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com