Industrial control equipment vulnerability mining method, system and equipment and storage medium
A technology for industrial control equipment and vulnerability mining, applied in the field of vulnerability analysis, can solve problems such as the failure of normal operation of industrial control equipment, and achieve the effect of avoiding failure to operate normally.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
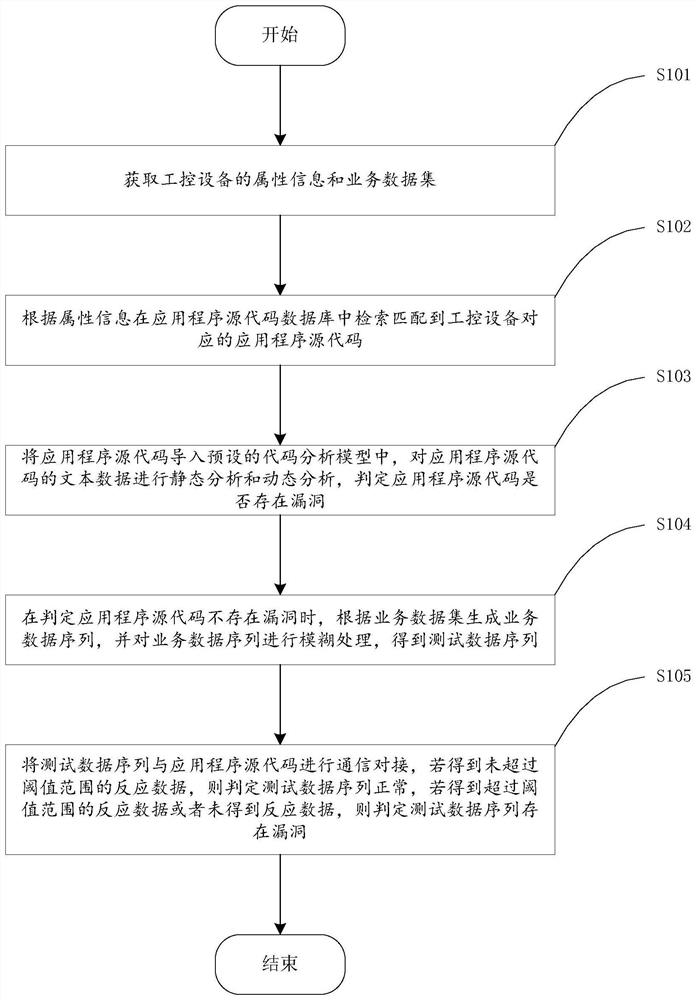
[0052] This embodiment provides a method for mining vulnerabilities in industrial control equipment, such as figure 1 shown, including the following steps:
[0053] S101. Obtain attribute information and business data sets of industrial control equipment.
[0054] During specific implementation, the attribute information and business data sets of the industrial control equipment can be obtained by obtaining the IP address of the industrial control equipment. The specific process includes: obtaining the IP address of the industrial control equipment; then accessing the industrial control equipment according to the IP address, and collecting the properties of the industrial control equipment information and business data. Attribute information includes identification information such as type, model, software and hardware information of industrial control equipment.
[0055] S102. Search the application program source code matching the industrial control device in the applicati...
Embodiment 2
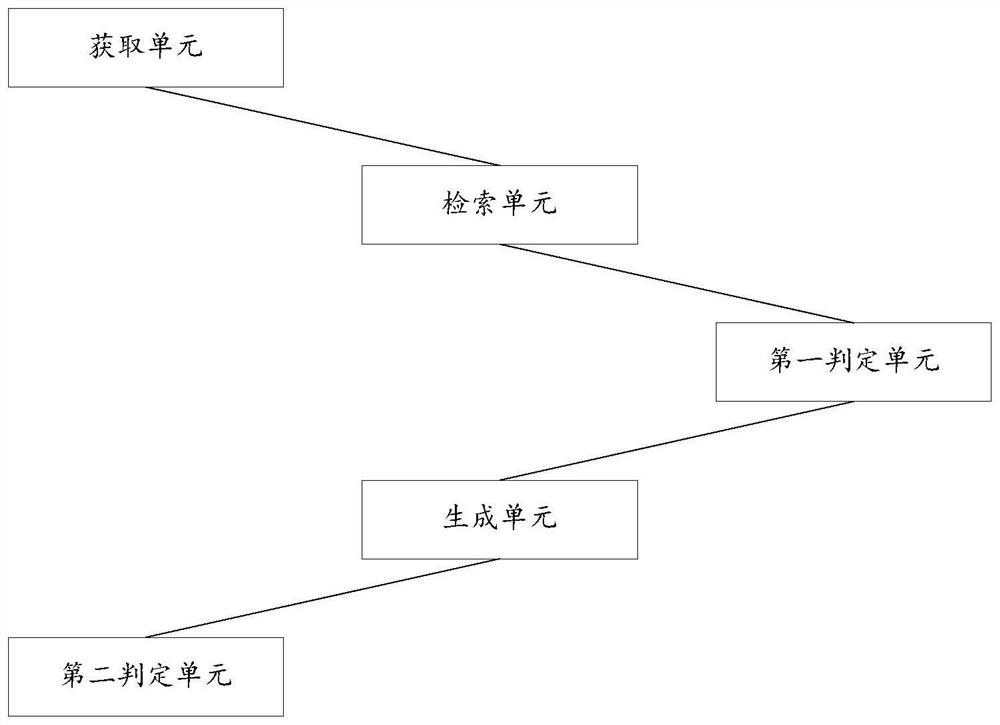
[0072] This embodiment provides a system for mining vulnerabilities in industrial control equipment, such as figure 2 shown, including:
[0073] The acquisition unit is used to acquire attribute information and business data sets of industrial control equipment;
[0074] A retrieval unit, configured to retrieve the application source code corresponding to the industrial control device in the application source code database according to the attribute information;
[0075] The first judging unit is used to import the application program source code into a preset code analysis model, perform static analysis and dynamic analysis on the text data of the application program source code, and determine whether there is a loophole in the application program source code;
[0076] The generation unit is used to generate a business data sequence according to the business data set when determining that there are no loopholes in the application program source code, and perform fuzzy proc...
Embodiment 3
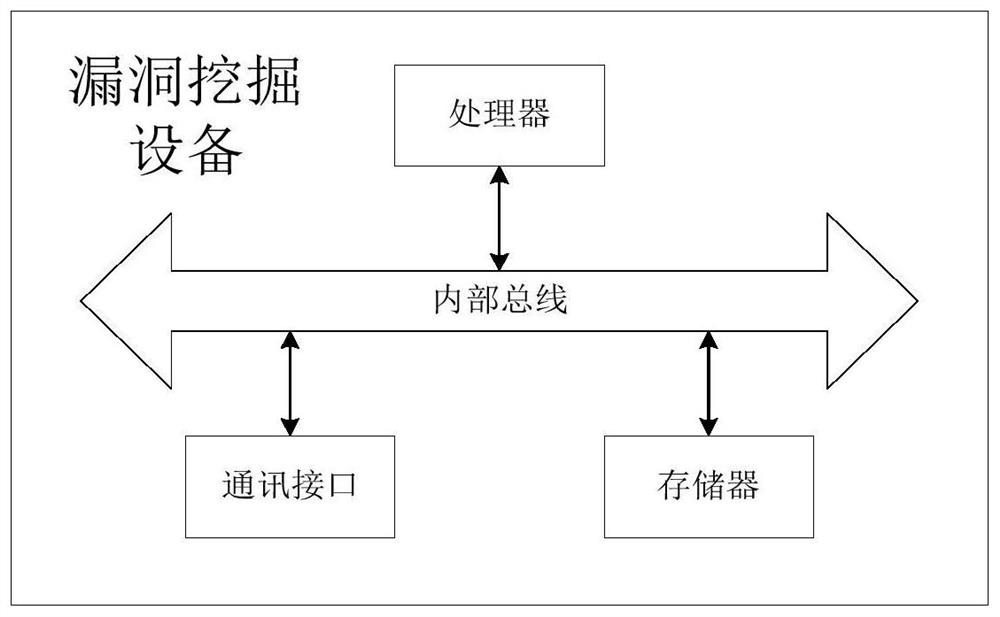
[0079] This embodiment provides a device for exploiting vulnerabilities in industrial control equipment, such as image 3 As shown, at the hardware level, including:
[0080] memory for storing instructions;
[0081] The processor is configured to read the instructions stored in the memory, and execute the method for mining vulnerabilities of industrial control equipment described in Embodiment 1 according to the instructions.
[0082] Optionally, the computer device also includes an internal bus and a communication interface. The processor, the memory and the communication interface can be connected to each other through an internal bus, which can be an ISA (Industry Standard Architecture, industry standard architecture) bus, a PCI (Peripheral Component Interconnect, peripheral component interconnection standard) bus or an EISA (Extended Industry Standard Architecture, extended industry standard architecture) bus, etc. The bus can be divided into address bus, data bus, con...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com