Mobile application traffic identification method and system based on machine learning
A mobile application and machine learning technology, applied in the field of traffic identification, can solve the problem that the traffic identification method is not suitable for mobile application traffic identification processing, there is no way to effectively meet the application requirements, and the specific application program that the traffic comes from cannot be identified. Achieve the effect of improving information richness, improving classification and recognition ability, and reducing misclassification rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
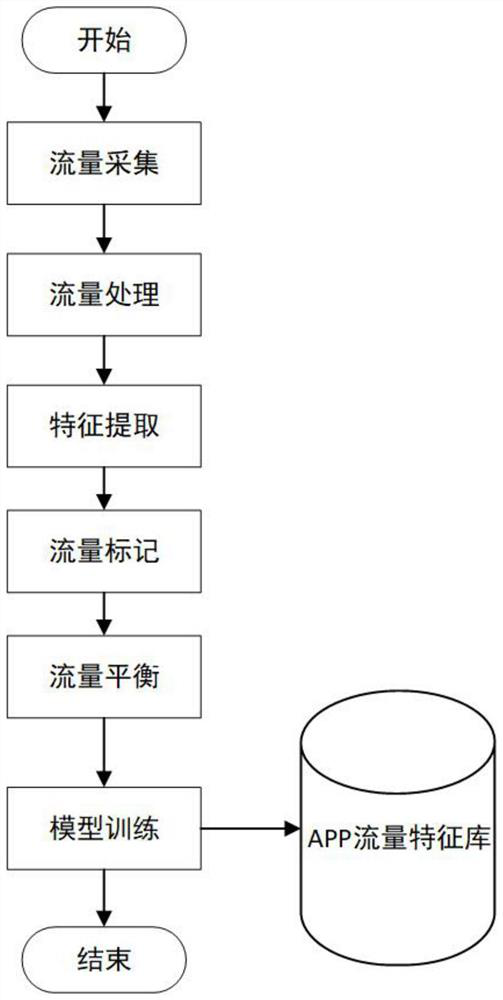
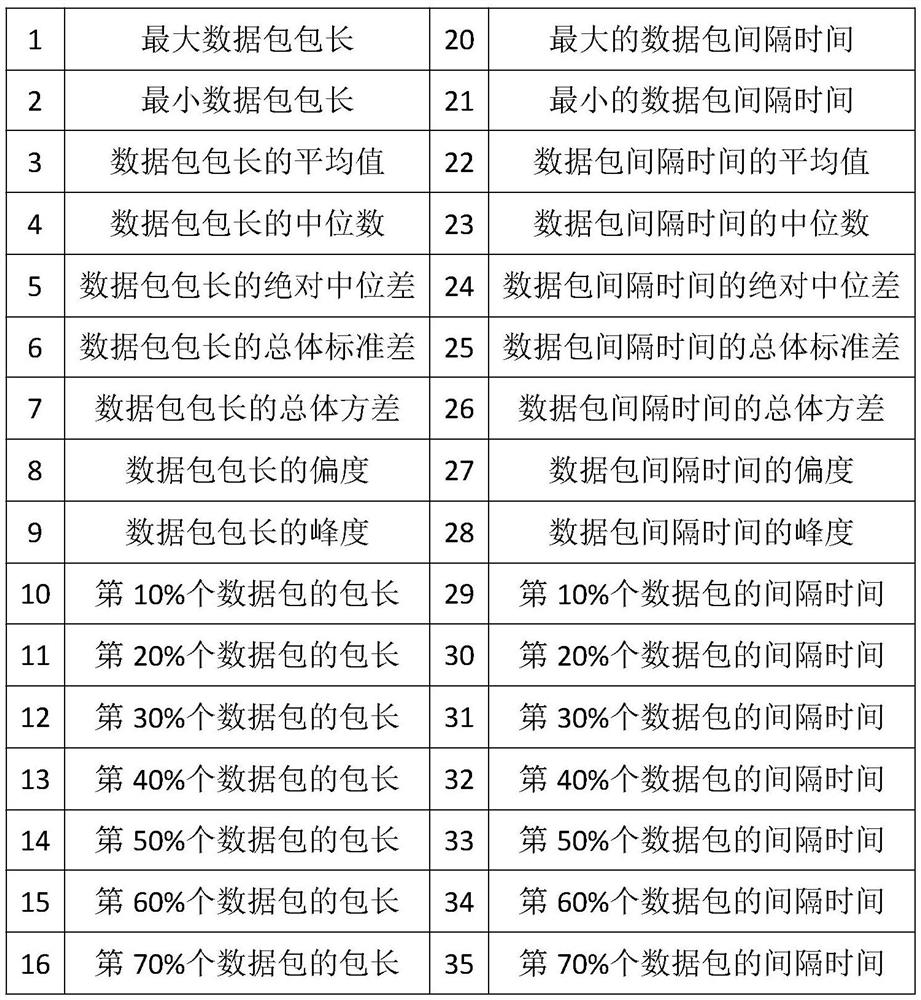
[0054] Use a mobile phone without any application to connect to the hotspot on the PC side. When collecting the traffic of a target application, obtain and only run the apk file of the application, close the program background running function of the mobile phone system, and prohibit the background running. Open wireshark on the PC side to capture the traffic data packets sent by the mobile terminal. The traffic data packets collected by each application are based on the amount of characteristic data generated subsequently. The collection goal is: after the collected traffic is processed and generated, the amount of characteristic data can reach about 3000. In the collected data set, the detailed information of each data packet is recorded. After collecting data, the application traffic is dumped locally in pcap format.
[0055] Use the wireshark tool to process the pcap file stored locally, filter and delete the wrong and retransmitted data packets. Then use the tshark com...
Embodiment 2
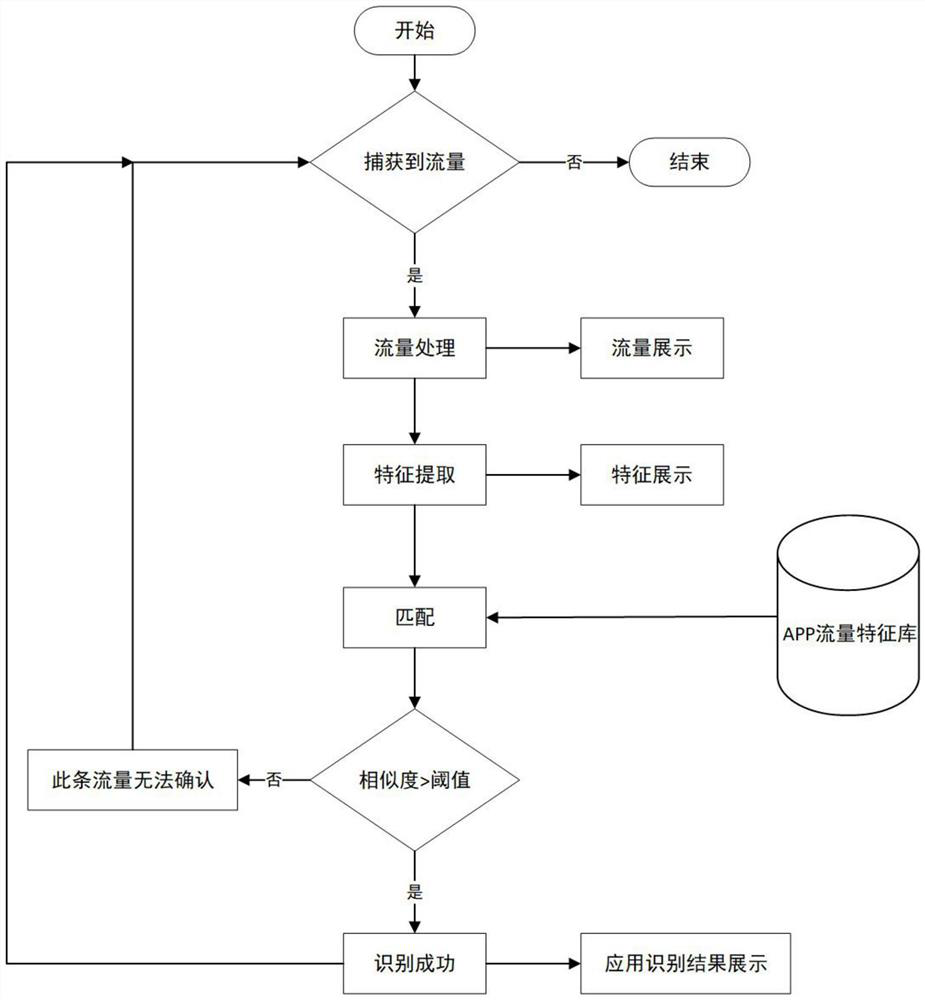
[0065] like figure 2 , the mobile application traffic identification system used in the present invention includes a traffic monitoring module, a traffic processing module, a traffic display module, a feature extraction module, a feature display module, an application identification module, and a result display module;
[0066] Traffic monitoring module: Deploy the traffic monitoring tool wireshark to capture the application traffic sent by the mobile phone, and save every 1000 data packets captured to the local automatically;
[0067] Traffic processing module: For the traffic to be detected in the form of pcap stored locally, use the tshark command "-Tfields-eframe.time_delta-e frame.len-e ip.src-e ip.dst-e tcp.srcport-etcp.dstport "Analyze the pcap file, obtain the interval between sending two data packets, the size of the data packet, the source IP address, destination IP address, source port, and destination port of each data packet, and redirect them to the CSV file;
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com