Security camera media data encryption technology
A media data and data encryption technology, which is applied in image communication and key distribution, can solve the problems of inability to play back and watch the player software, improve the usability and practicability of multiple scenes, prevent leakage and diffusion, and meet the effect of timely encryption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The embodiments of the present application will be described in detail below with reference to the accompanying drawings and examples, so as to fully understand and implement the implementation process of how to apply technical means to solve technical problems and achieve technical effects in the present application.
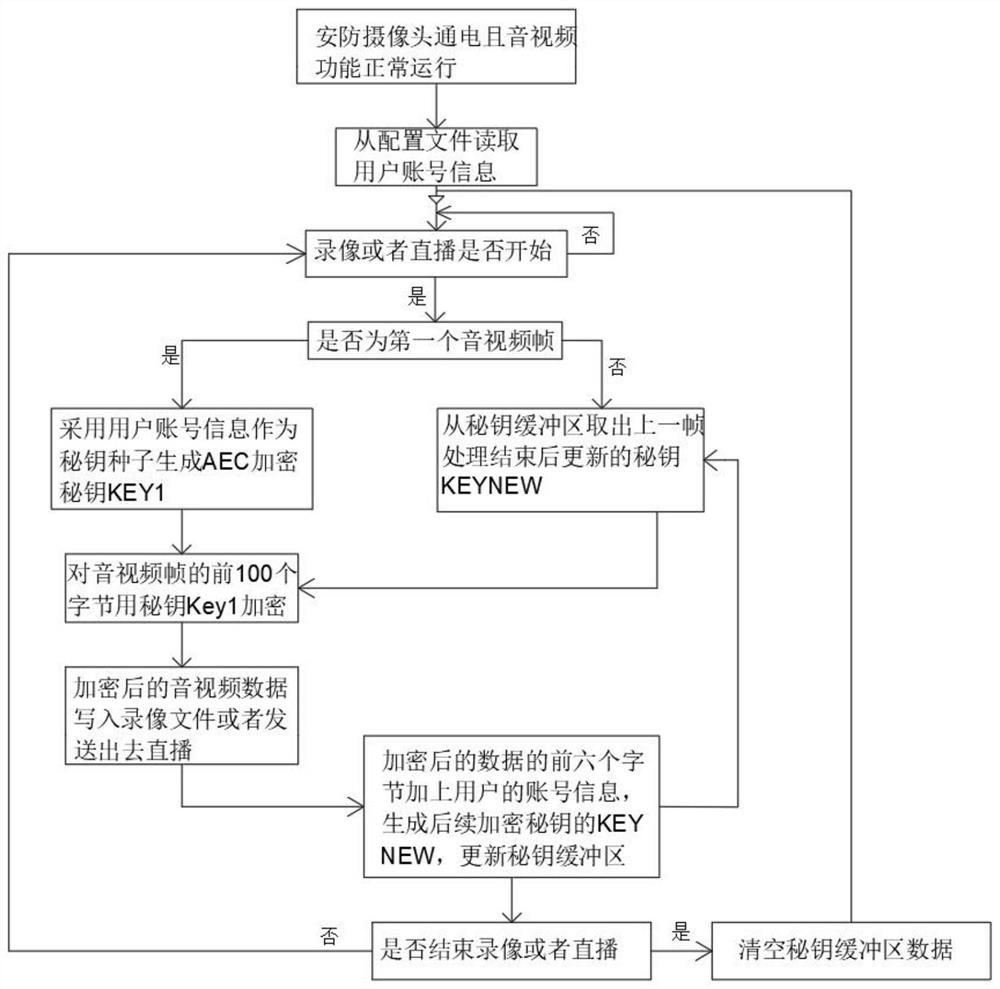
[0031] like figure 1 As shown, the security camera media data encryption technology provided by this embodiment includes the following steps:
[0032] S1: Power on the security camera, then read the user's account information from the configuration file, and then find the video or live broadcast data inside the security camera; if the video data or live broadcast fails to be opened, the next step will not be entered, and the video data will be recorded. or the re-opening of the live broadcast;
[0033] Among them, the security camera ensures the normal operation of audio and video functions when it is powered on, so as to ensure the successful encryptio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com