Distributed certificate verification method
A verification method and distributed technology, applied in the field of IT information security, can solve problems such as the absence of certificate serial numbers, reduced system performance, and difficulty in deploying PKI systems, to ensure integrity and authority, and reduce data traffic.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
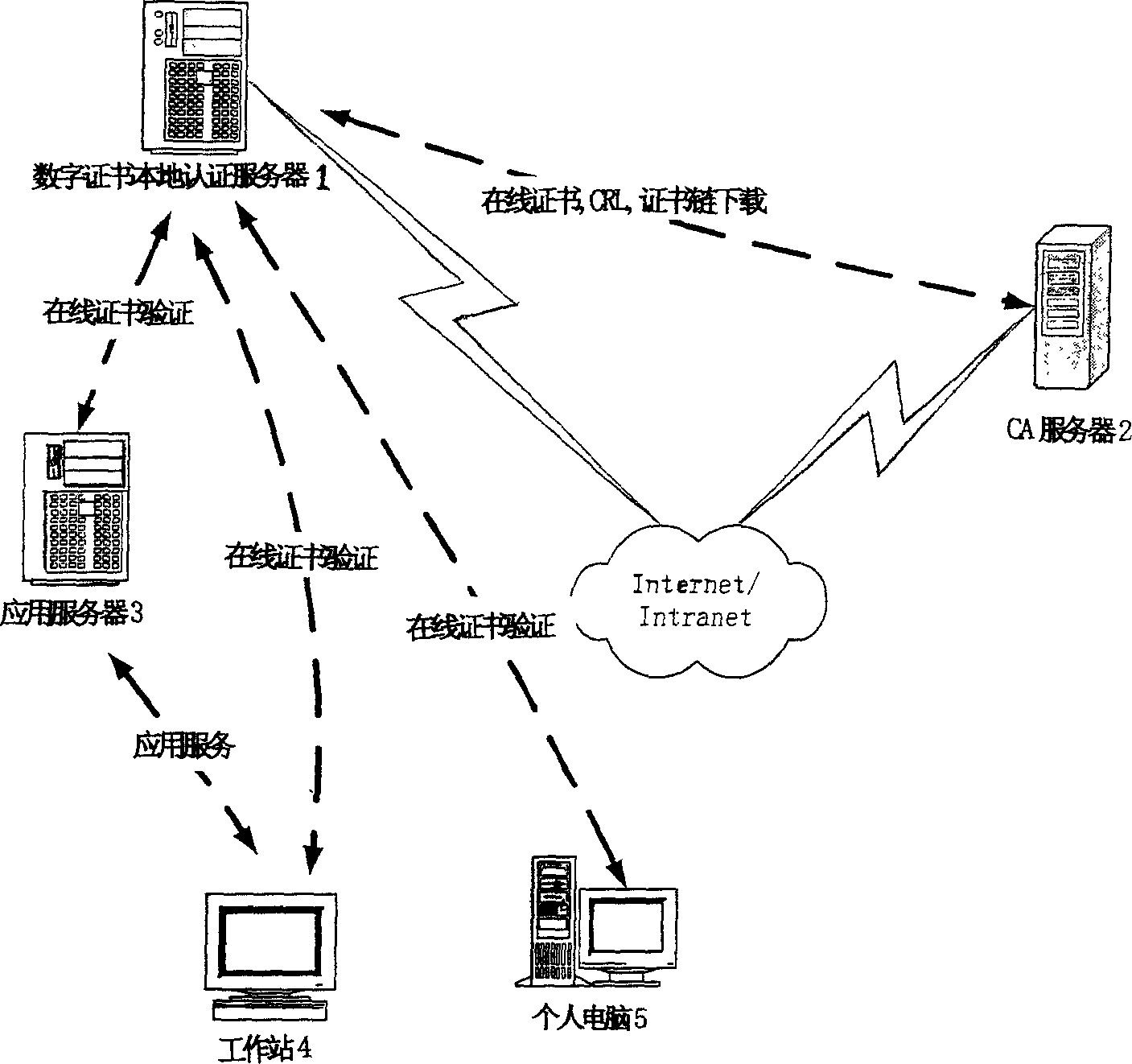
[0035] Such as figure 1 Shown, combined with the content of the method of the present invention, specific embodiments are provided. The distributed certificate verification server 1 used in the embodiment of the present invention can be deployed in a local area network composed of external application systems such as application servers 3 , workstations 4 , and personal computers 5 , and is bidirectionally connected with the CA server 2 . The distributed certificate verification server 1 can be connected to the Internet, while the above-mentioned application server 3, workstation 4, and personal computer 5 are not directly connected to the Internet.
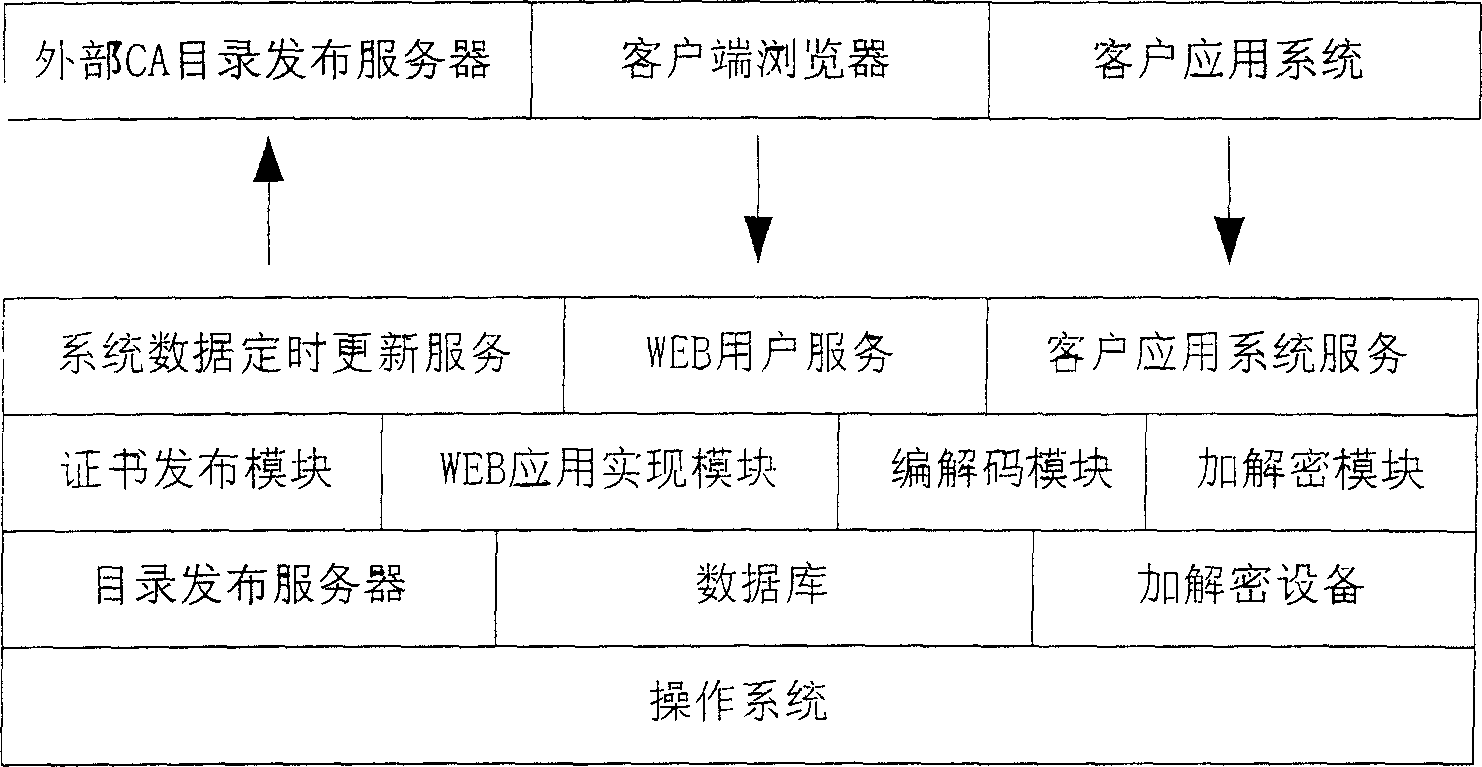
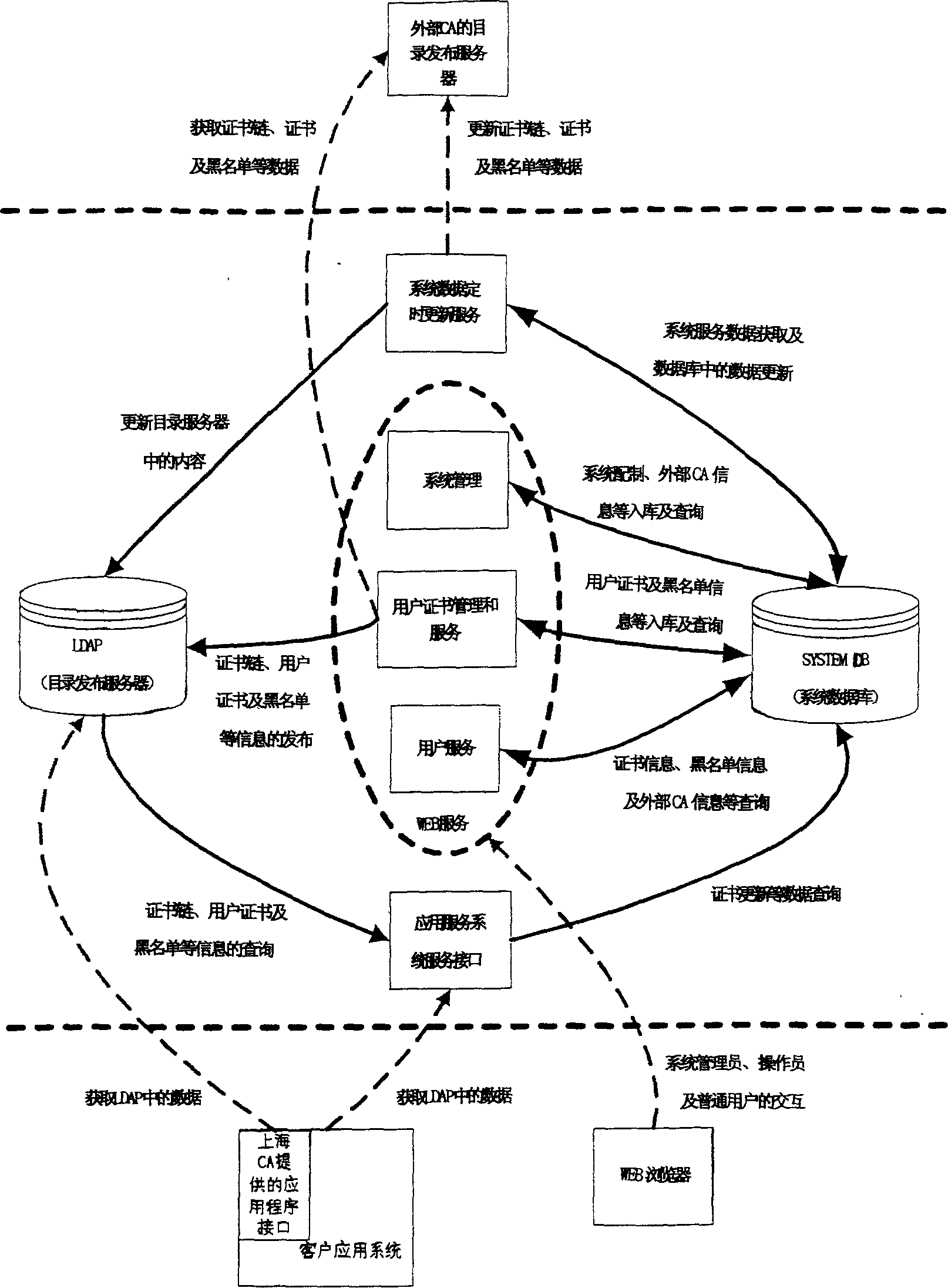
[0036] Such as figure 2 As shown, the distributed certificate verification server of the method embodiment of the present invention includes the following functional modules:
[0037] The first layer is the service module connected with the external system: system data regular update service, WEB user service, customer applica...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com