Technique for generating correlation number for use in lawful interception of telecommunications traffic
A telecommunication service and legitimate technology, applied in the direction of telephone communication, wireless communication, electrical components, etc., can solve problems such as consumption and achieve the effect of overall performance improvement
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
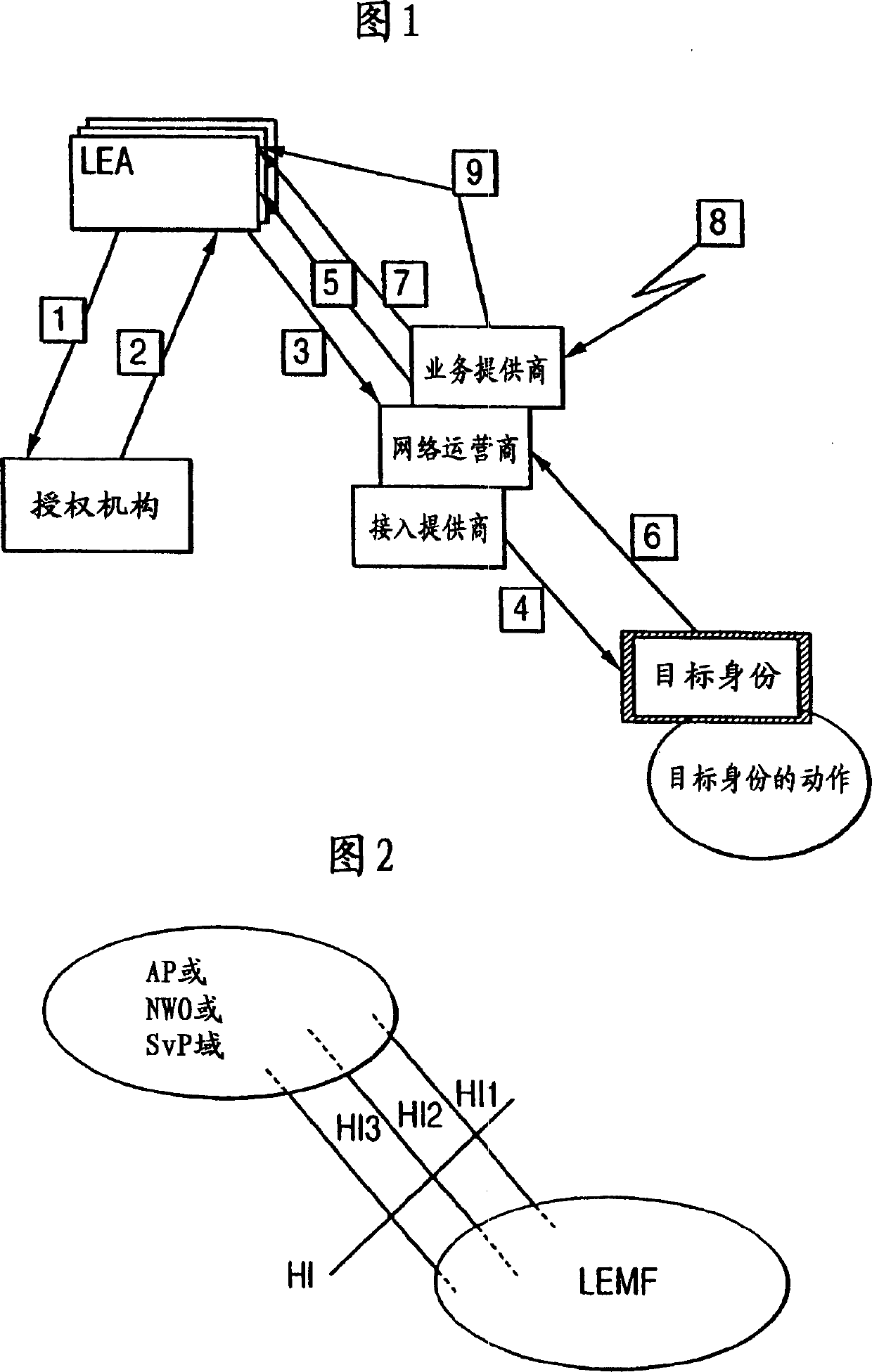
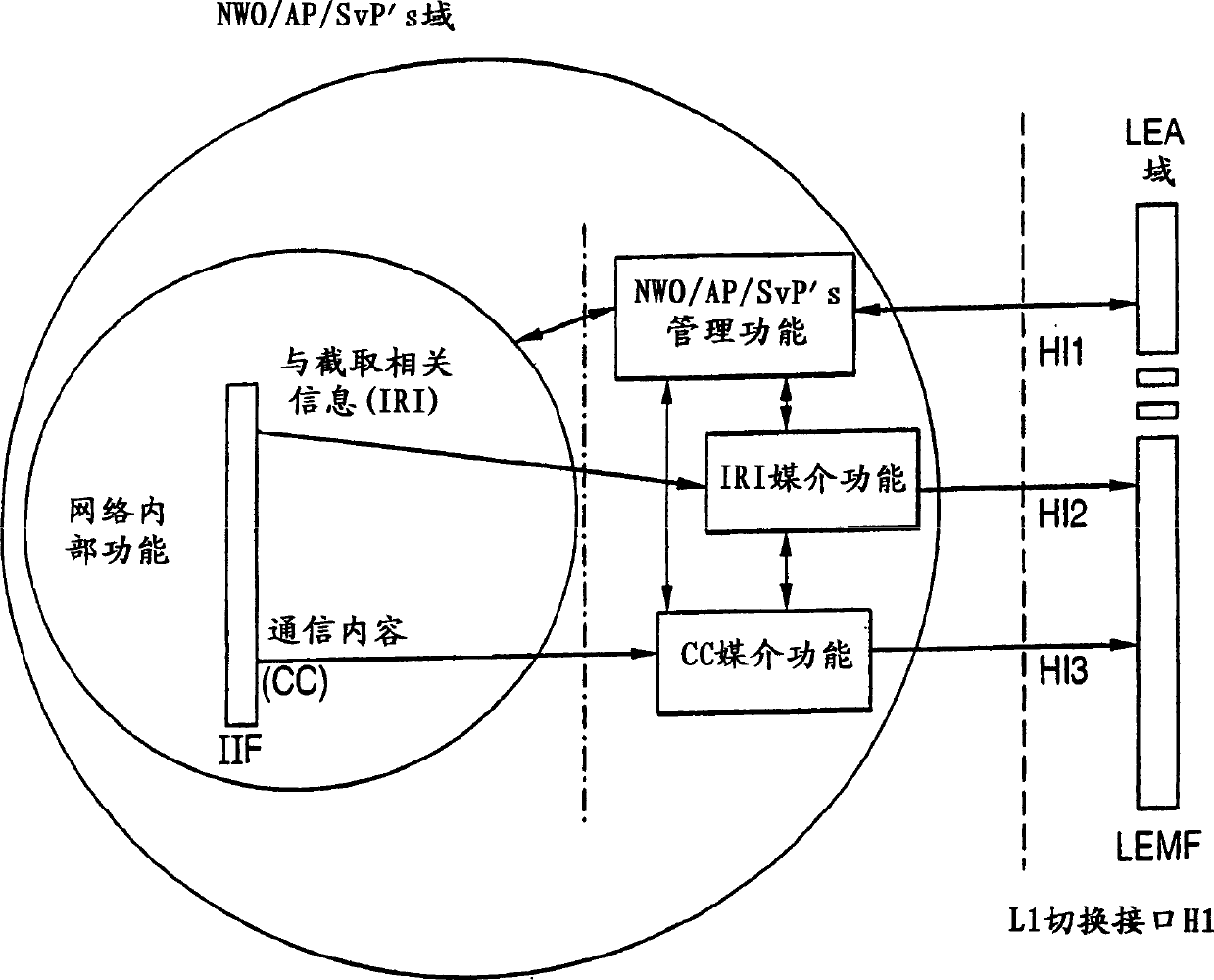
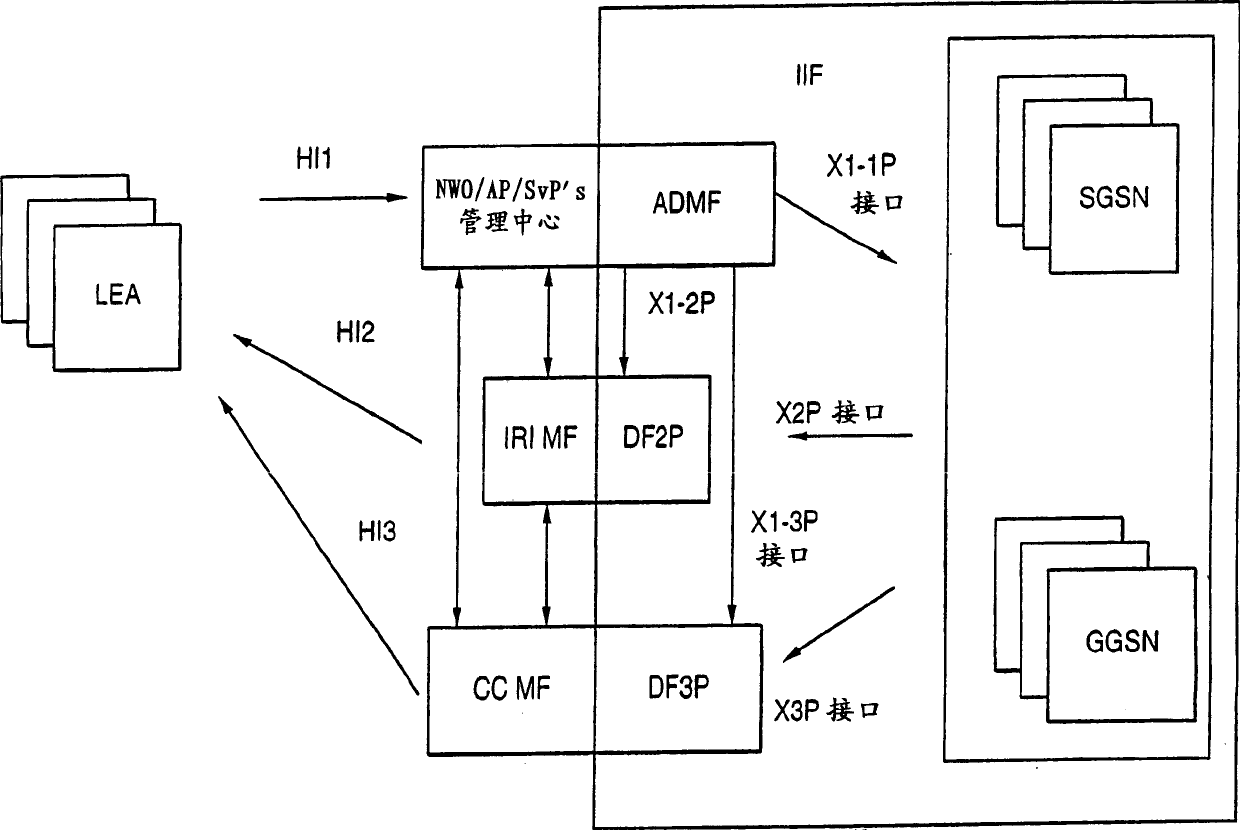
[0028] Before beginning the detailed description of the invention, it is appropriate to make the following remarks. Where appropriate, the same numerals and symbols may be used to designate equivalent, corresponding or like parts in different drawings. In addition, in the following detailed description, an example size / model / value / range may be given, but the present invention is not limited thereto. Furthermore, arrangements are shown in block diagram form to avoid obscuring the invention, and given that details regarding the implementation of the block diagram arrangements are largely dependent on the platform within which the invention is implemented, in other words they should within the knowledge of those skilled in the art. Where specific details have been set forth for the purpose of describing exemplary embodiments of the invention, it will be apparent to those skilled in the art that the invention may be practiced without or with changes to the specific details. In c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com