Strong authentication method based on symmetric encryption algorithm
A symmetric cipher algorithm and block cipher algorithm technology, applied in the field of strong authentication based on symmetric cipher algorithm, can solve problems such as large management load, security vulnerability, reliability changes, etc., to prevent replay attacks, prevent eavesdropping, and resist dictionary attacks. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
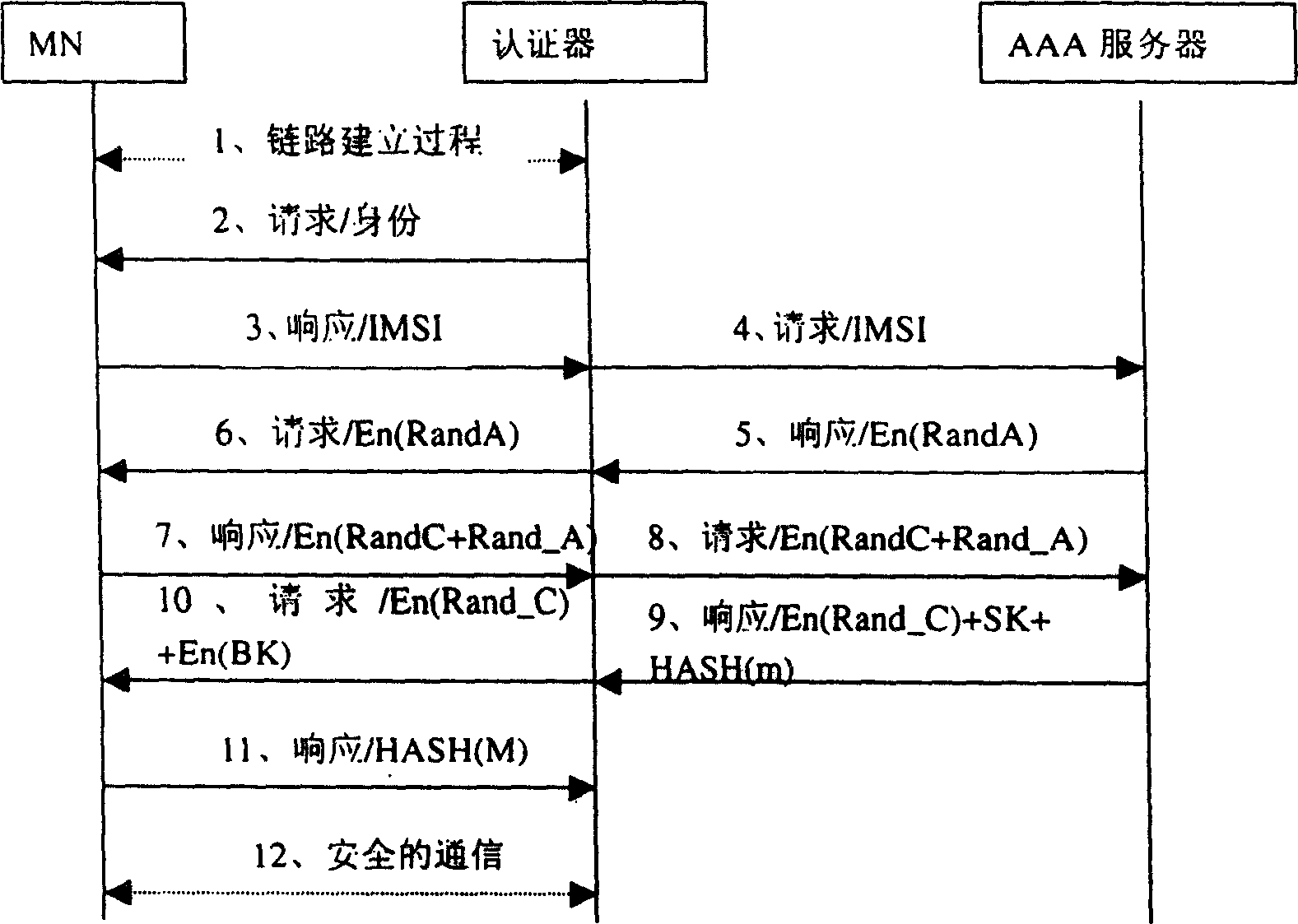
[0061] This section mainly describes examples of the specific implementation and application of the inventive authentication method in the PPP protocol.
[0062] In order to establish communication over a point-to-point link, each end of the PPP link must first send LCP packets to set up and test the data link. After the link is established, the peer can be identified. PPP must then send NCP packets to select and configure one or more network layer protocols. Once each selected network layer protocol is configured, packets from each network layer protocol can be sent on the link. The link will remain in the communication configuration until direct LCP and NCP packets close the link, or when some external event occurs (inactivity timer expires or network administrator intervenes). In the process of setting up, maintaining and terminating a point-to-point link, a PPP link goes through several distinct stages, such as figure 2 shown. This diagram does not show all state tran...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com