Encoding method for condition code of false proof code
An encoding method and anti-counterfeiting code technology, applied in the field of anti-counterfeiting data storage, can solve the problems of loss of anti-counterfeiting digital anti-counterfeiting effect, increase system maintenance cost, affect system query speed, etc., to prevent data leakage, reduce operation and maintenance costs, and improve availability. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] 1. Anti-counterfeiting code coding
[0019] The encoding of the anti-counterfeit number is a number of 16-21 digits. Now take the encoding method of 16 digits as an example to illustrate as follows:
[0020]
[0021] The encoding structure is described as follows:
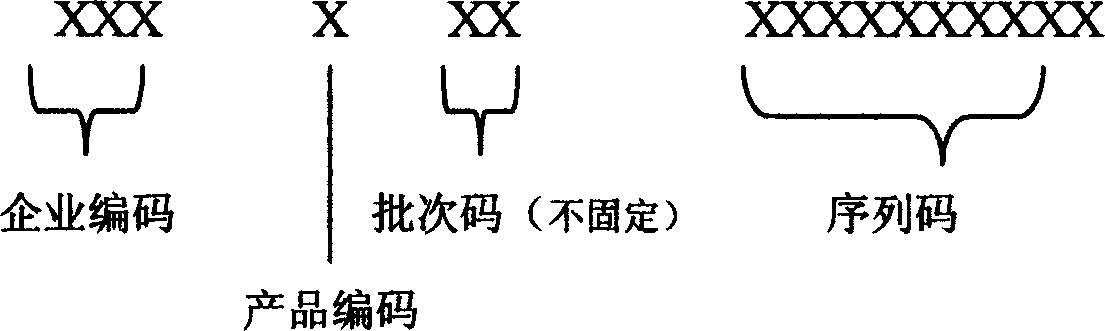
[0022] 1st to 3rd place: enterprise code, which can compile the codes of 1000 enterprises;
[0023] The 4th digit: product code, which can compile 10 kinds of product codes;
[0024] The 5th and 6th digits: batch code, not fixed, can be two digits, can be said to be three digits. Identify the batch number of each batch of anti-counterfeiting codes;
[0025] No. 7-16: serial number, indicating the serial number of each group of anti-counterfeiting numbers of each product;
[0026] According to the above encoding rules, a set of plaintext codes can be compiled for each product, and through the encryption of the encryption algorithm, the plaintext codes become irregular anti-counterfeiting numbers.
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com