Network security protecting system and method
A network security and protection system technology, applied in the direction of user identity/authority verification, etc., can solve the problems of telecom operators, the impact of broadband access servers, and the impact on the network, so as to reduce the risk of virus infection and reduce the risk of virus knowledge Requirements, the effect of solving the waste of system resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
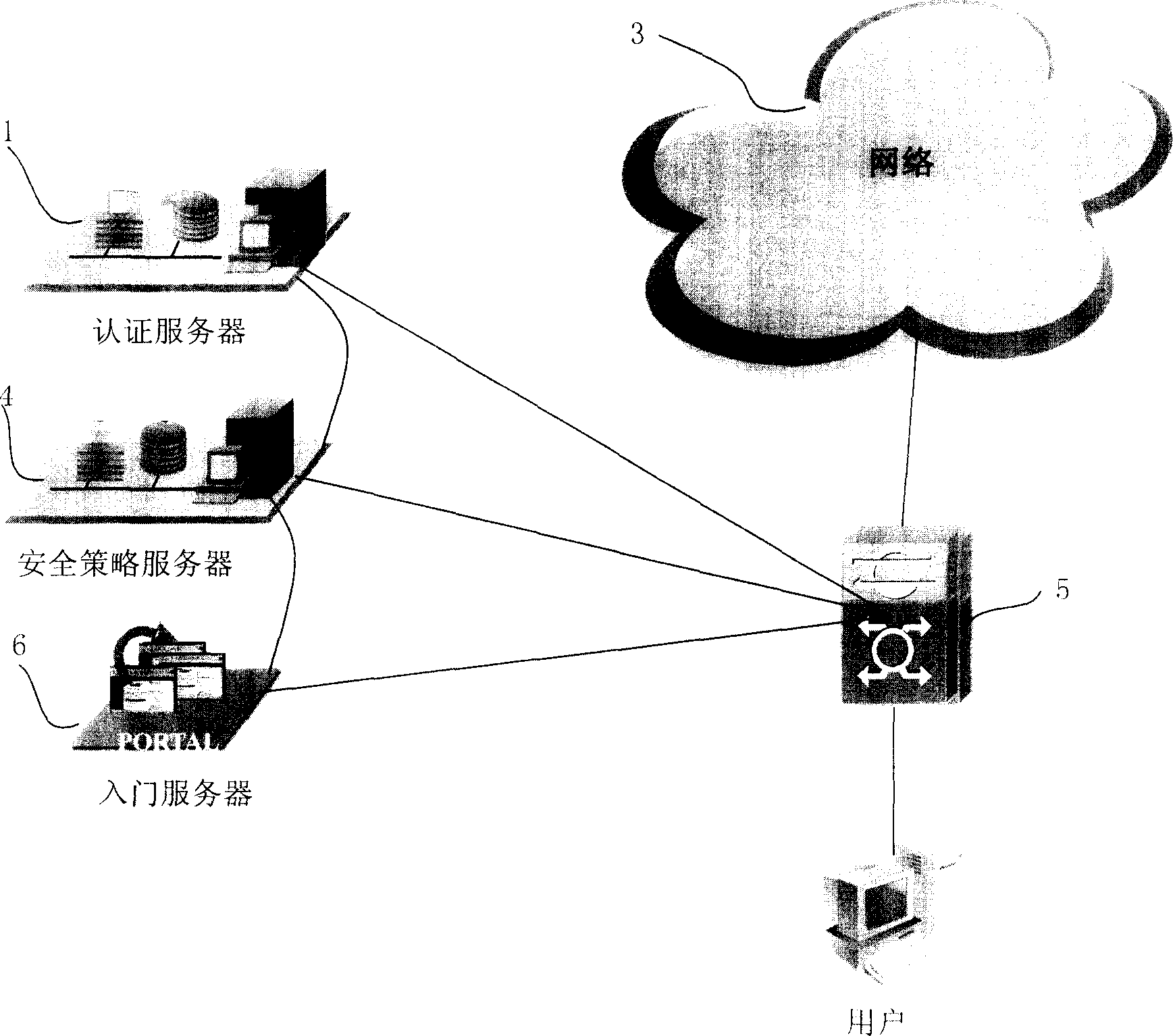
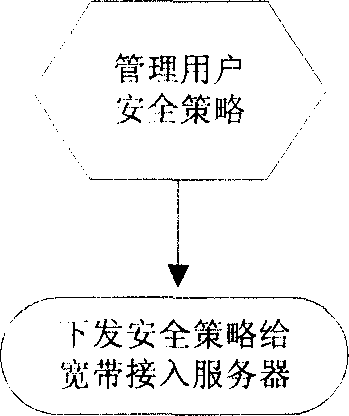
[0031] The network security protection system and method of the present invention are implemented based on the existing network system, and the existing network system generally includes:
[0032] Broadband Access Server (BAS, Broadband Access Server): It mainly completes the user's access, and usually has access methods such as xDSL / / LAN / HFC (x digital subscriber line / local area network / optical fiber / coaxial hybrid network).
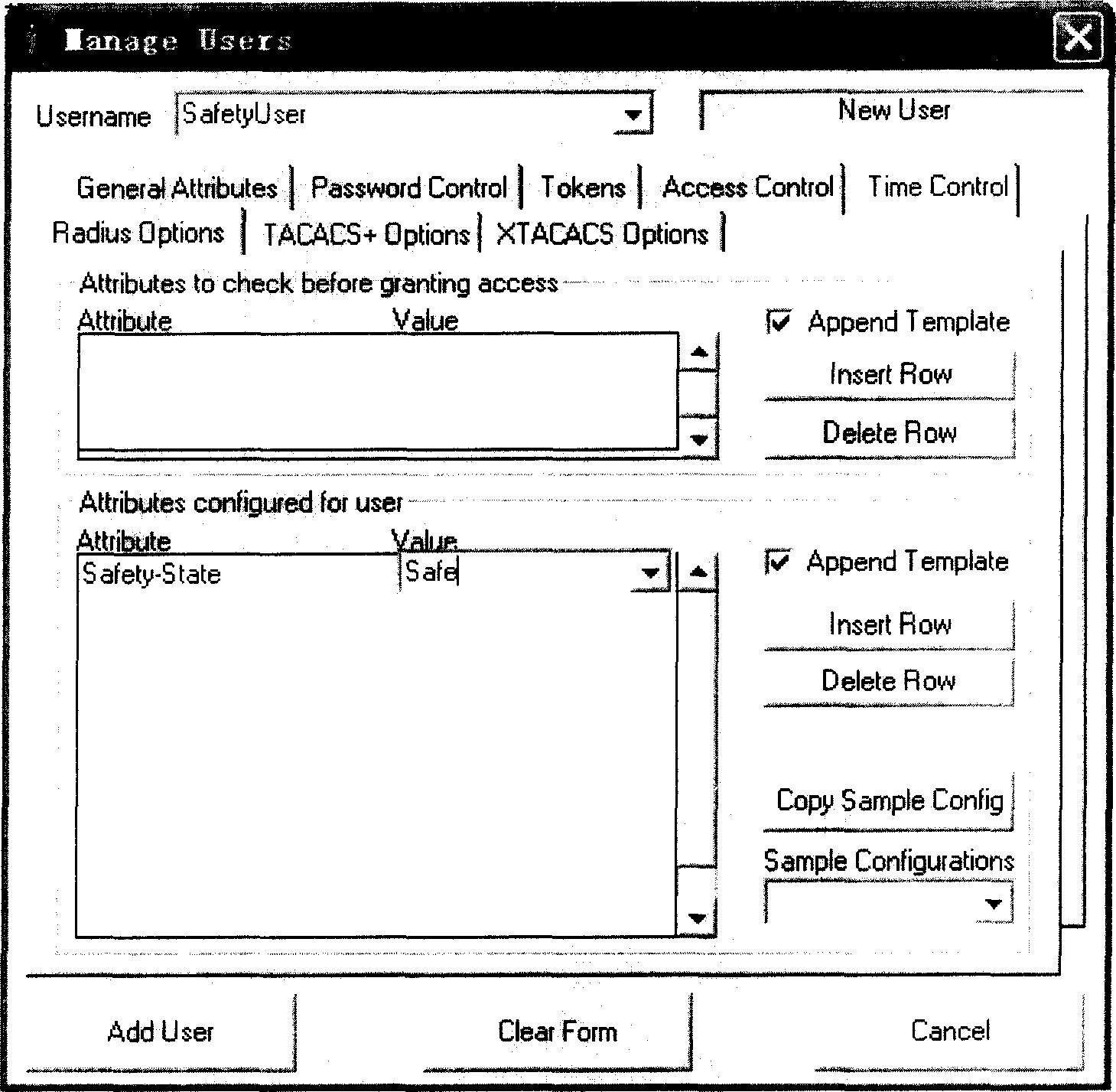
[0033] Authentication server: AAA is the abbreviation of Authentication, Authorization and Accounting (Authentication, Authorization and Accounting), which provides a consistent framework for configuring the three security functions of authentication, authorization and accounting. AAA is usually accomplished by using a remote authentication (verification) dial-in user service protocol (Radius, Remote Authentication Dial-In User Service). The authentication server is a PC or network device that implements the Radius protocol. It cooperates with the broad...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com