Public key cipher encrypting and decrypting method based on nerval network chaotic attractor
A chaotic attractor and public key cryptography technology, which is applied in the field of public key cryptography encryption and decryption based on neural network chaotic attractors, can solve the problems of large amount of calculation, increased difficulty and difficulty in key management, and achieve high security, Conducive to the control of confidential information, the effect of fast encryption speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
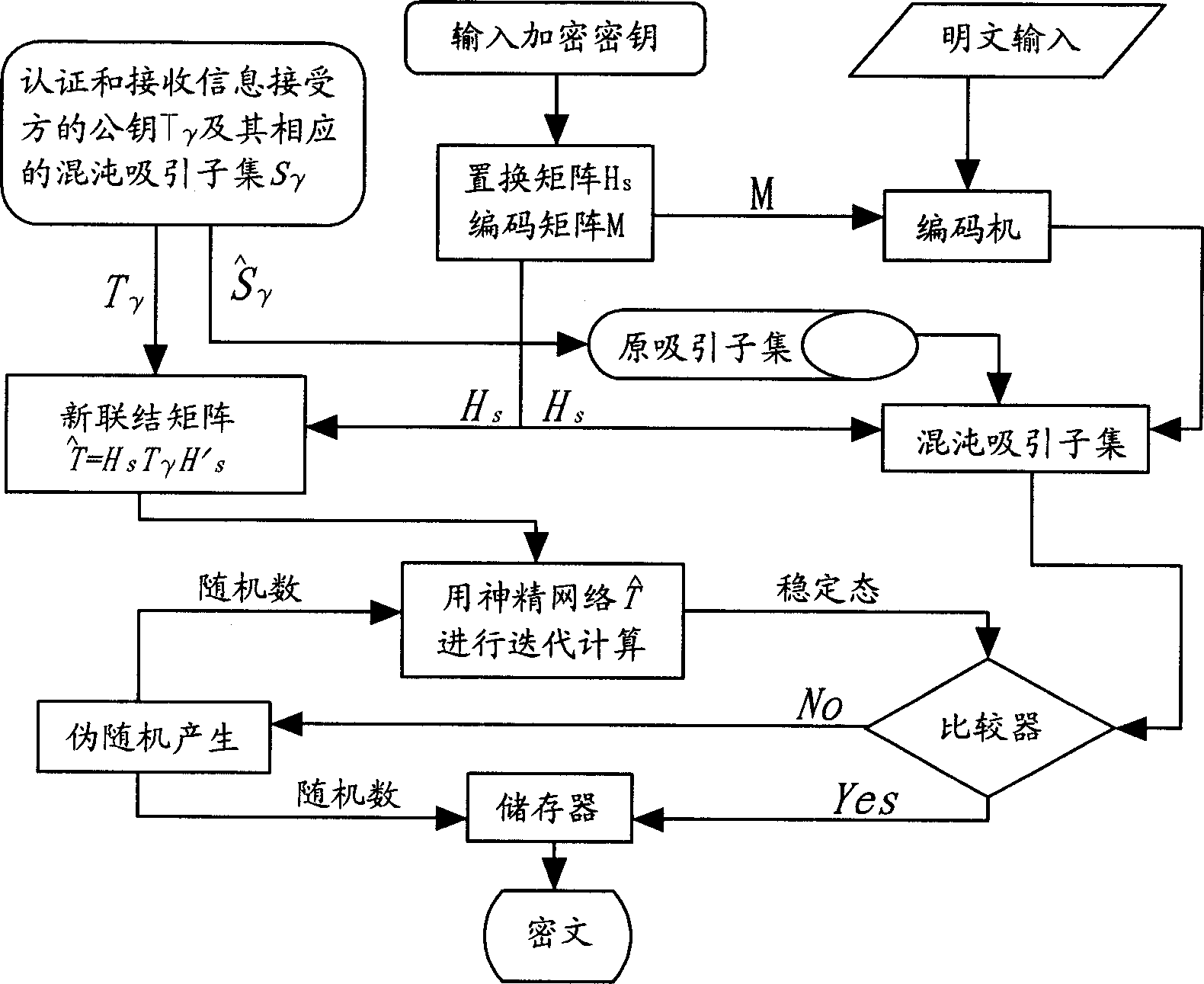
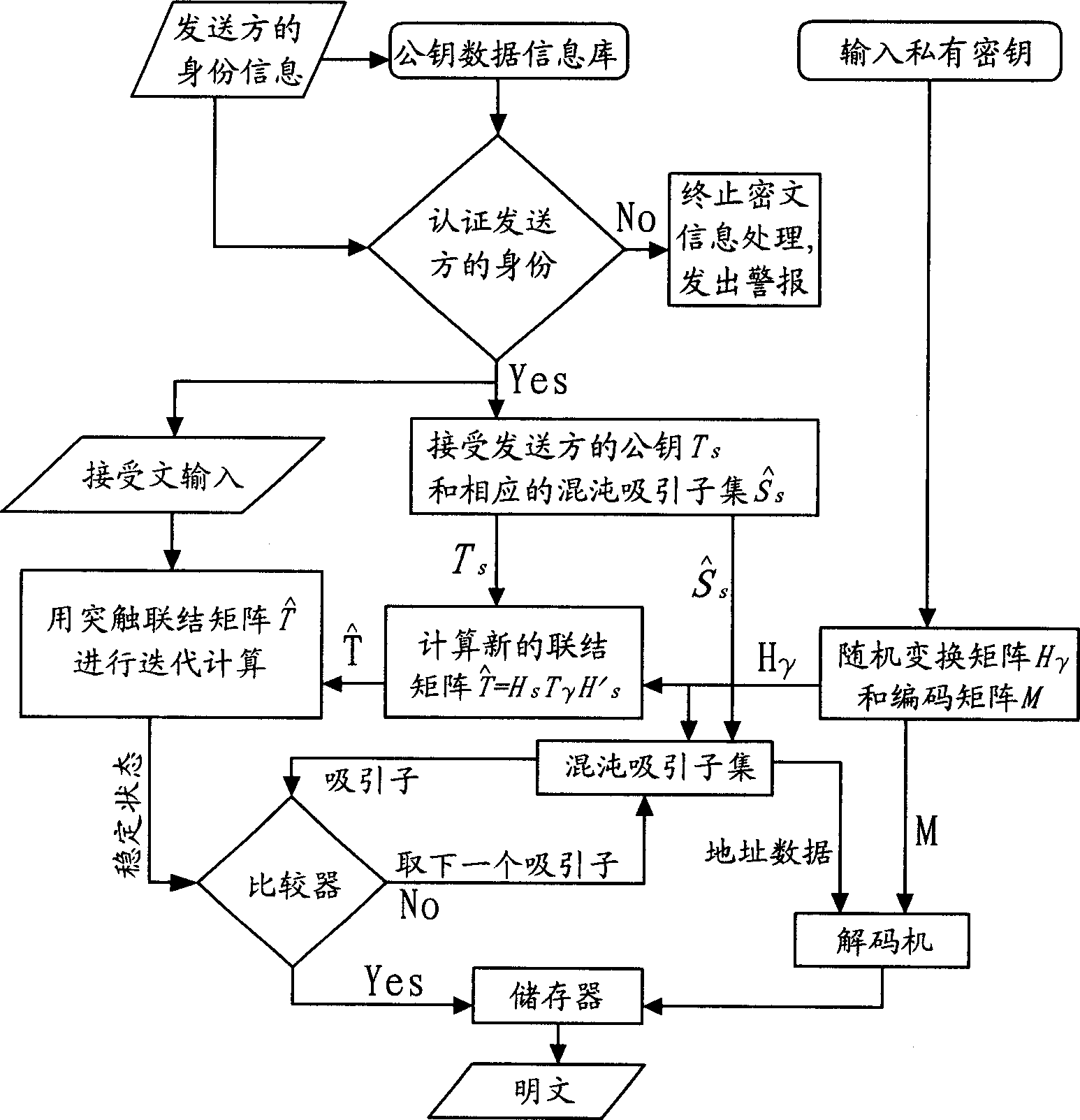
[0019] One, encryption and decryption method of the present invention:
[0020] The present invention is a kind of public key cryptographic encryption and decryption method based on neural network chaotic attractor, comprising the following steps:
[0021] Step 1: Key Generation and Distribution
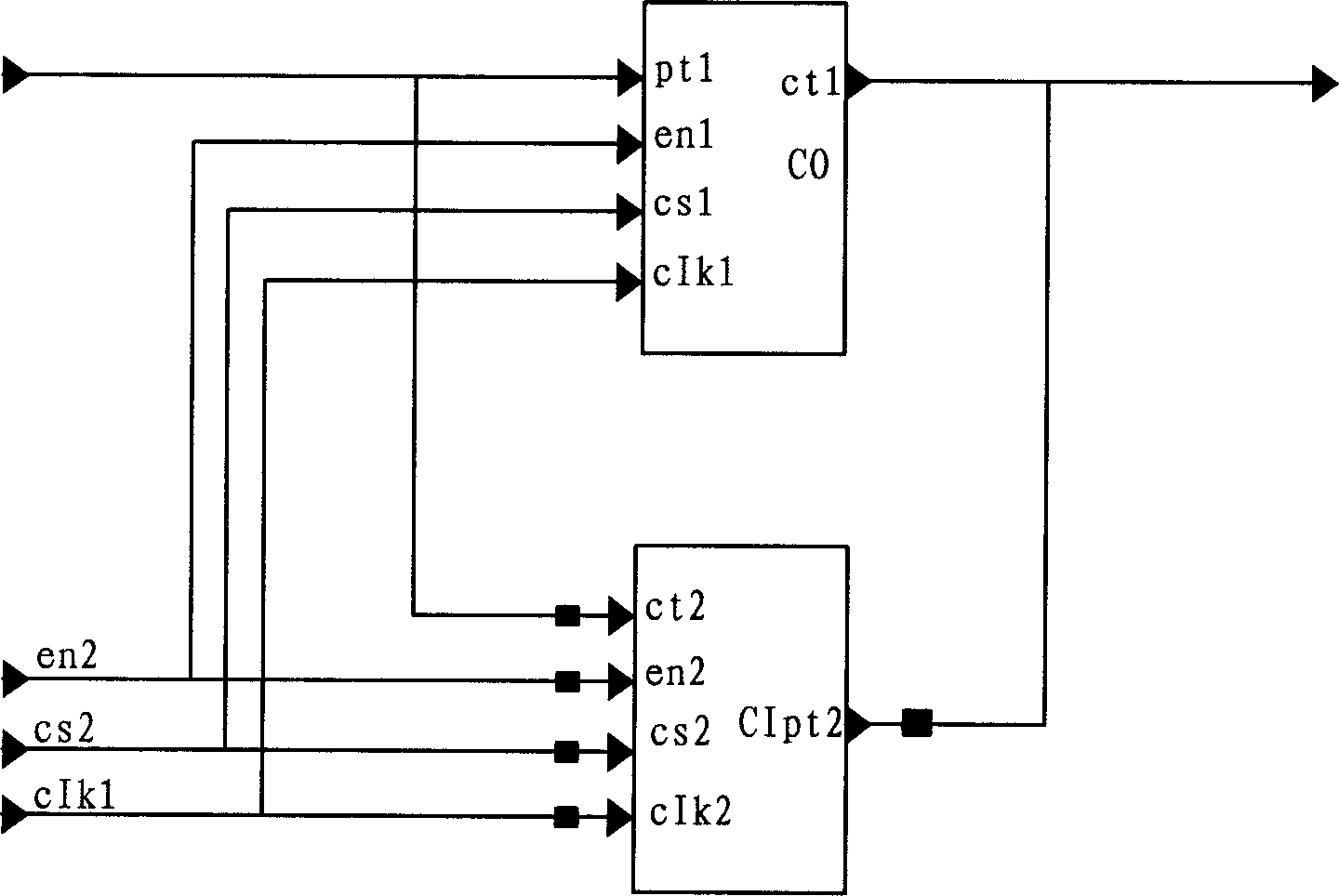
[0022] A group of users who need to communicate securely share a carefully selected synaptic connection matrix T 0 , the users in the group should jointly determine an ideal plaintext encoding and decoding method, that is, the encoding matrix M. Each user randomly selects a different transformation matrix in the nth-order square matrix exchange family, for example, the H selected by user i i , calculate T i =H i T 0 h i ′ and its corresponding chaotic attractor set (according to formula 1), the H i secrecy, while the T i public. Then each user saves his own public key and its corresponding chaotic attractive subset, together with other information such as user name and addre...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com