A mobile identity authentication system and its authentication method
An identity authentication, mobile technology, applied in the direction of user identity/authority verification, character and pattern recognition, telephone communication, etc., can solve the problems of insecurity, cracking, inconvenience, etc., and achieve a wide range of applications.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0081] Embodiment 1: Mobile phone car key based on palmprint recognition
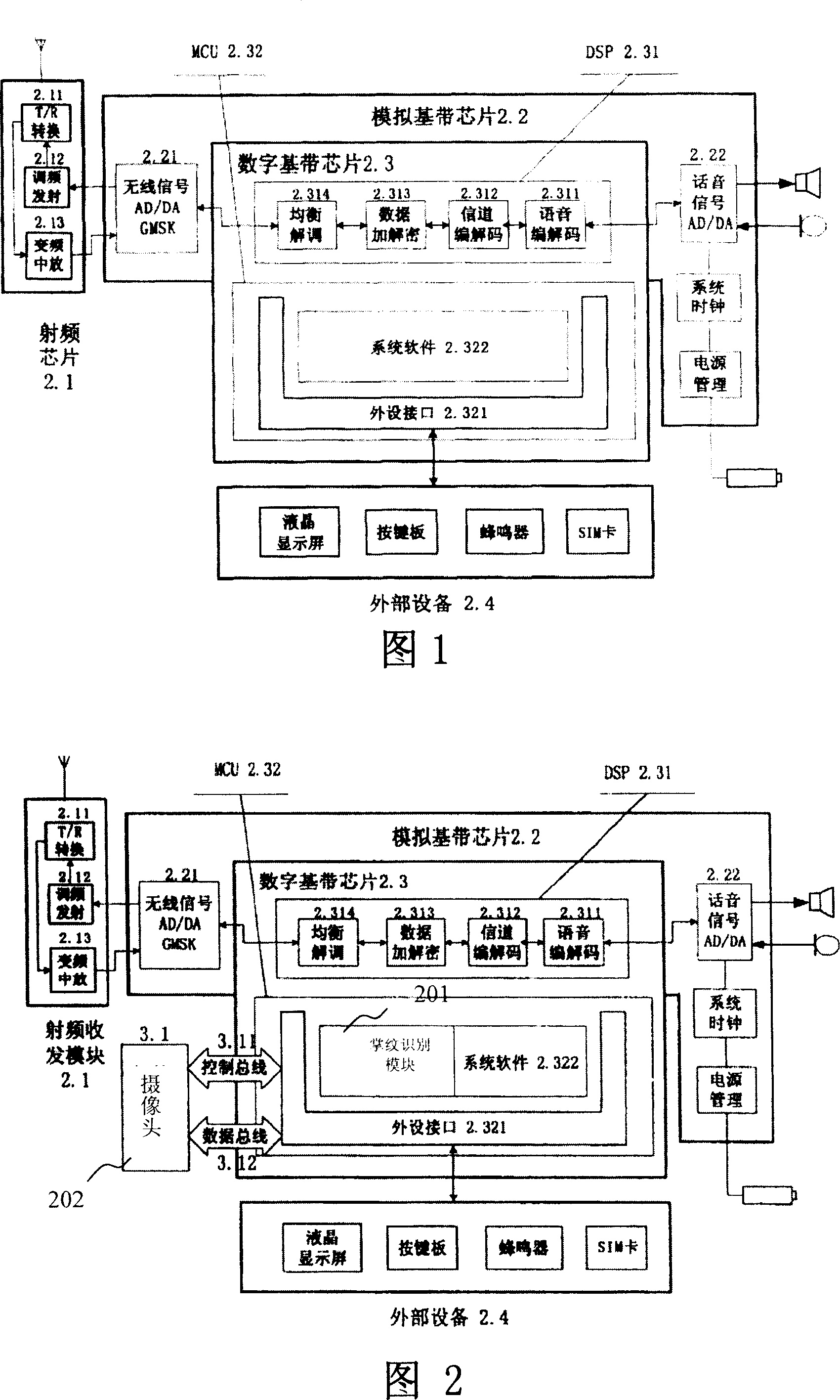
[0082] Embed non-contact IC chip in the mobile phone, just can have remote control function, and this is prior art. In this example, the user chooses to use the mobile phone as the key of the car, and writes the corresponding secret information (which can be a key) in the car lock and the IC chip of the mobile phone. Assume that the mobile phone IC chip has the following characteristics:
[0083] One is protected, the internal information cannot be deciphered;
[0084] The second is controllable, and the transmission of radio frequency information can be started or stopped with control commands.
[0085] The advantage of above-mentioned mobile phone car key is convenient, and general user has mobile phone, needn't carry car key to go out in addition. But if the user loses his phone, his car is also at risk of being stolen.
[0086] If a set of palmprint recognition application module is installed on...
Embodiment 2
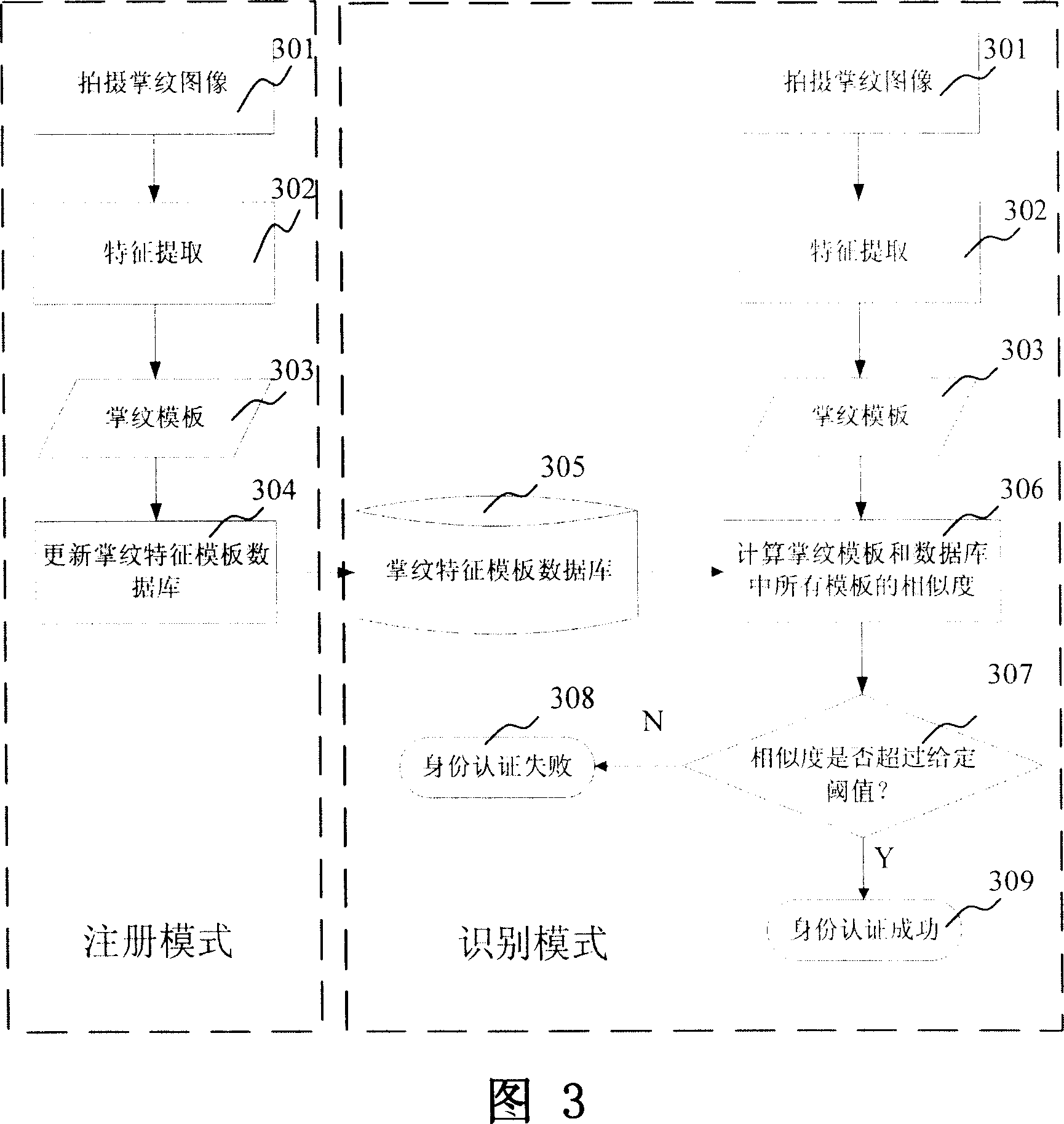
[0096] Criminals with previous convictions will collect their palmprint characteristics when they enter prisons or public security bureaus, and a central palmprint database for criminals will be established nationwide, which will be dynamically updated through wired or wireless networks. Each suspect has 3 images on each palm, and the feature size of each palmprint image is 512 bytes. Assuming that 10 million suspects’ palmprint features are collected, the storage space of the database is about 30G bytes. The capacity of the hard disk is generally 80G to 200G, which is enough to record the central palmprint database of all criminals in the country. The policeman on patrol is equipped with a mobile palmprint recognition system, that is, palmprint recognition software and communication software are installed on the PDA. If a suspicious fugitive is seen on the street, the police can use the camera on the PDA to collect the palmprint image of the suspect, automatically extract the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com