Provable data integrity verifying method, apparatuses and system
a data integrity and verification method technology, applied in knowledge representation, instruments, computing models, etc., can solve the problems of affecting the privacy of users, affecting the service life of users, and difficult for mobile clients to enjoy high bandwidth connection,
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
concrete example
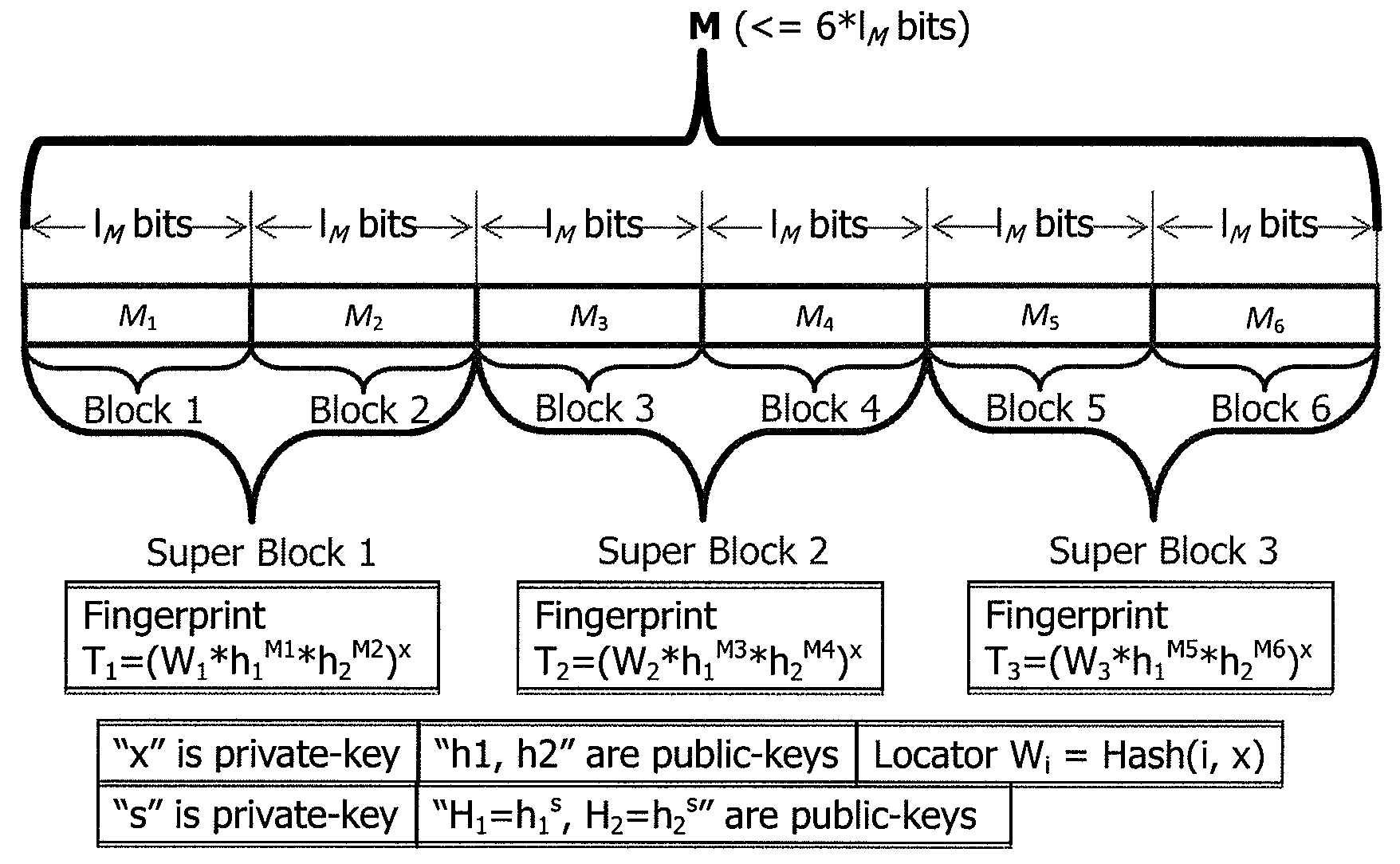
[0143]FIGS. 4-7 shows a concrete example of the present invention and its demonstration of the correctness, in which 6 blocks M1-M6 are used and 3 super blocks are formed with nB=2. It is believed that those skilled in the art may understand the present invention quite clearly by referring to FIGS. 4-7 in conjunction with the above description step by step.
Real Experiment
[0144]FIGS. 8-11 shows the result of the real experiment in which 256 blocks each having 27 bytes are combined into one super block, Φ=2Θ=512 boxes are used, and the data file has a size of 64 M bytes. Meanwhile, FIGS. 9-11 also list the result of Reference 7, from which it can be seen that as compared with Reference 7, the present invention has great improvements on the calculation time costs.
Other Embodiments
Alternative Scheme 1:
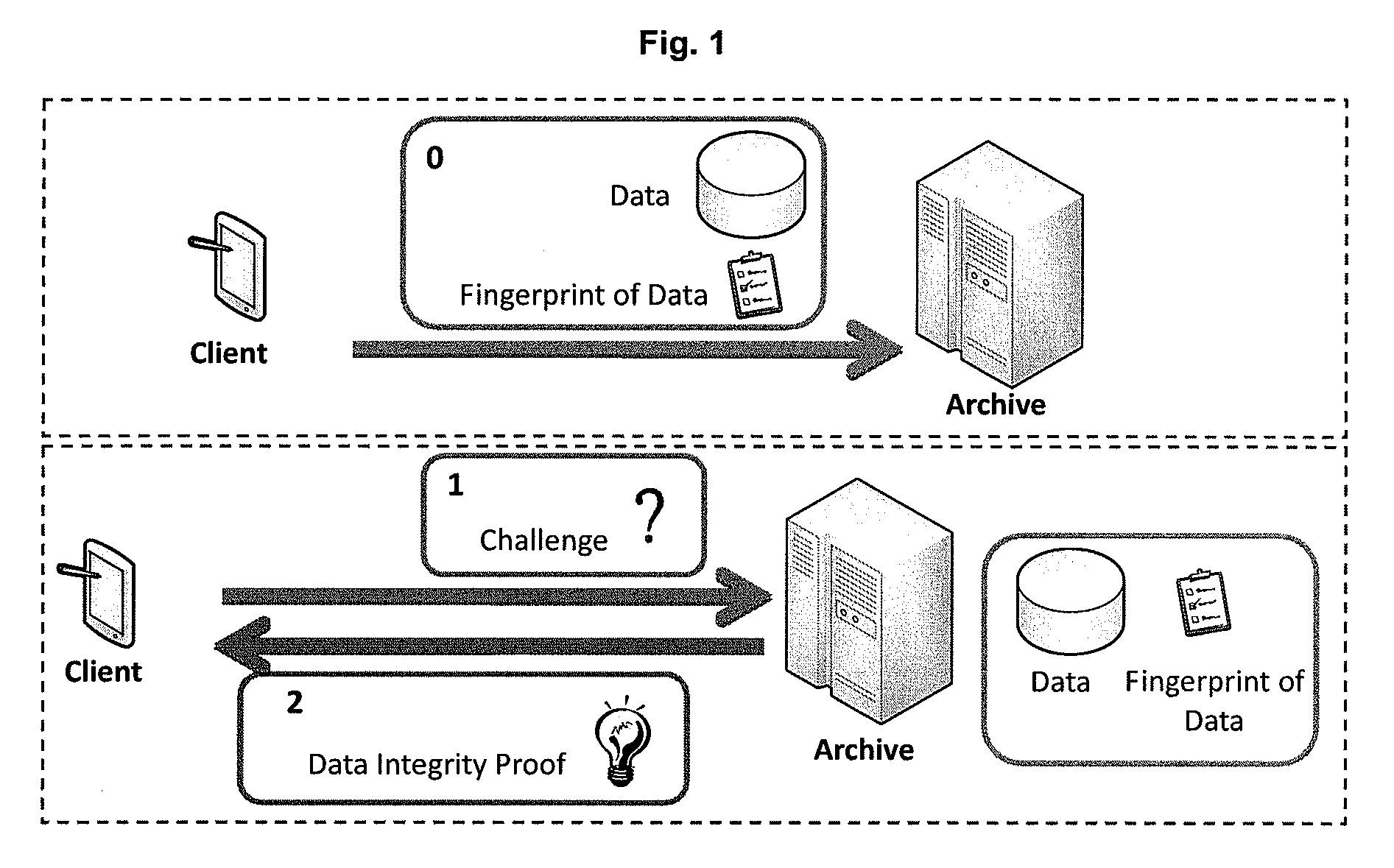
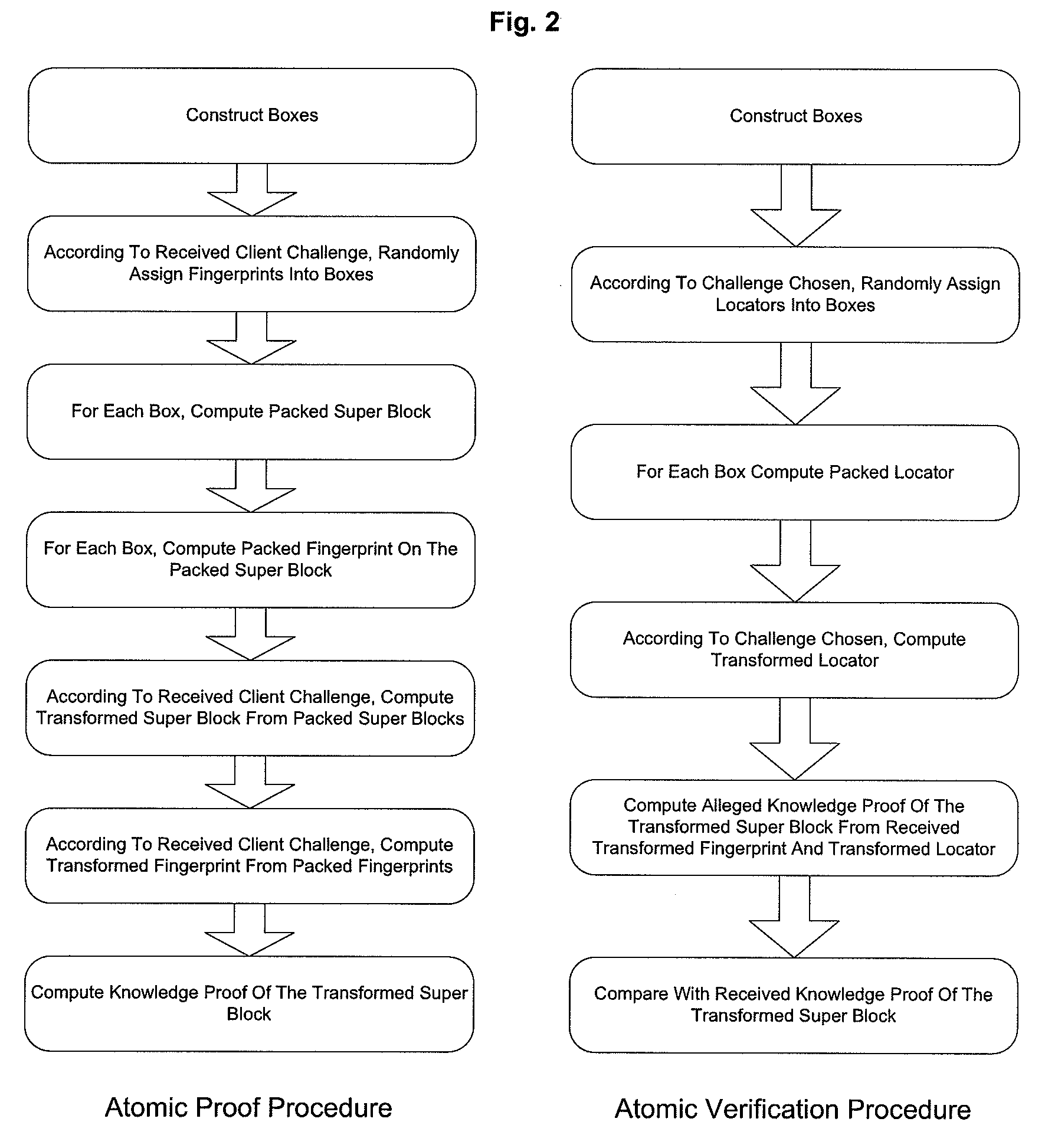
[0145]Slight modification to step iii-d. of “Archive Proves Data Integrity” and step IV) of “Client Verifies Data Integrity” yields PDI-2 scheme. This is a scheme that supports public veri...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com