Subchannel security at the optical layer
a security and optical layer technology, applied in the field of network optimization, can solve the problems of not being able to address certain significant realities of existing sdn networks, unable to solve solutions, and unable to purchase popular dvds, etc., and achieve the effects of facilitating sdn flow optimization, facilitating decision-making, and minimizing network congestion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040]In the detailed embodiments described below, it should be noted that the physical form in which architectural components, processes and other functionality is embodied can vary from dedicated computer hardware to software running on a general-purpose computer to a myriad of hybrid implementations allocating such functionality among different hardware and software components. It should be noted that even software components are typically embodied in physical non-transitory storage media (i.e., memory), such as hard disk drives, flash memory, etc.
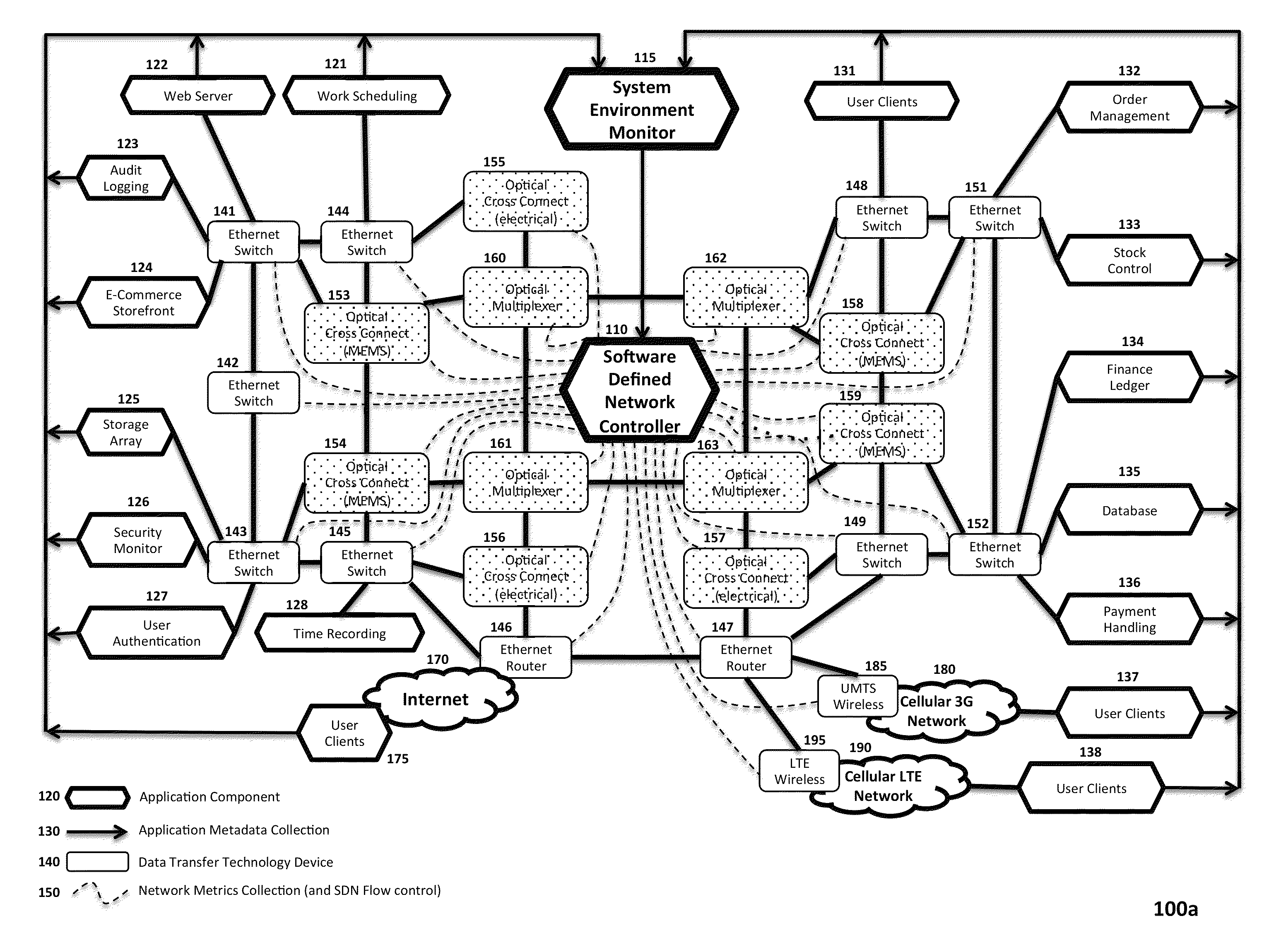
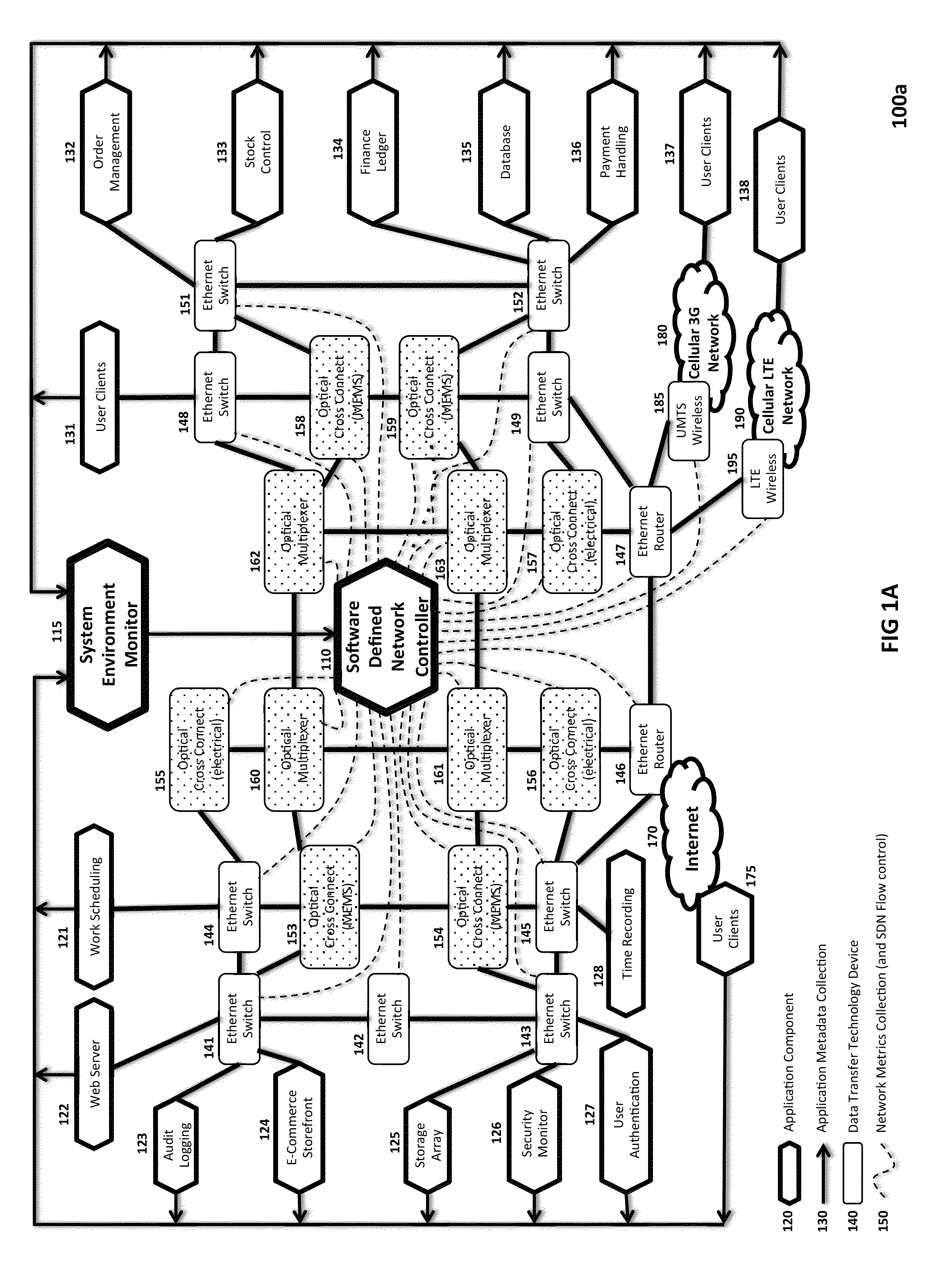
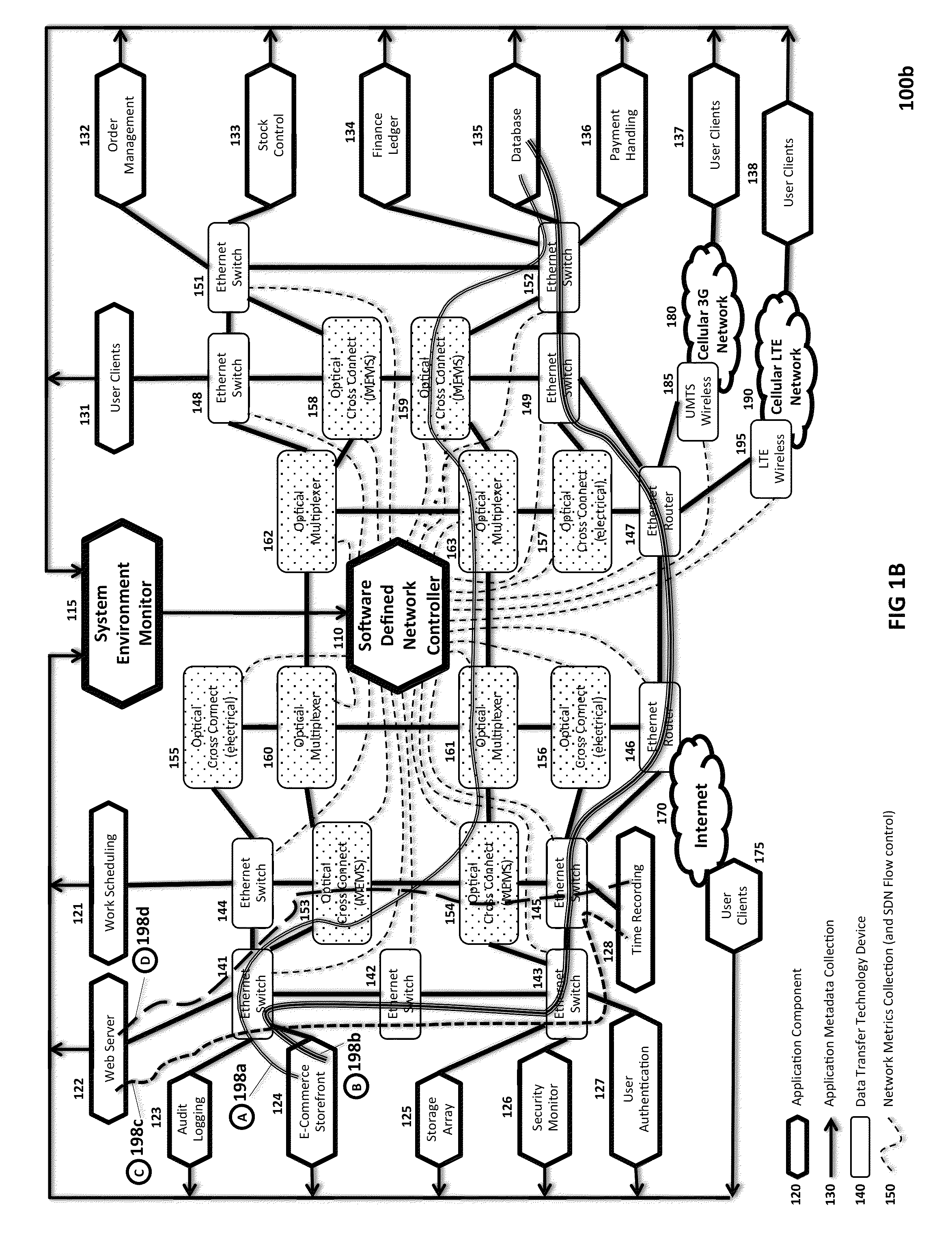
[0041]FIG. 1A is a block diagram illustrating one embodiment of an SDN Network 100a of the present invention, including a centralized SDN Controller 110 and a System Environment Monitor 115 for monitoring network nodes and extracting and analyzing real-time data reflecting the performance of SDN Network 100a at various levels of abstraction, including the Application Layer (containing various Application Components 120) and the lower-le...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com