Protection rotation method for presetting protective ring
A protection switching and protection ring technology, applied in data exchange networks, digital transmission systems, electrical components, etc., can solve the problem of not formally proposing a preset protection ring protection switching method, etc., to achieve less data loss, less bandwidth occupation, transmission The effect of low time delay
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0011] In order to better understand the technical solutions of the present invention, the implementation manners will be described in detail below in conjunction with the accompanying drawings.
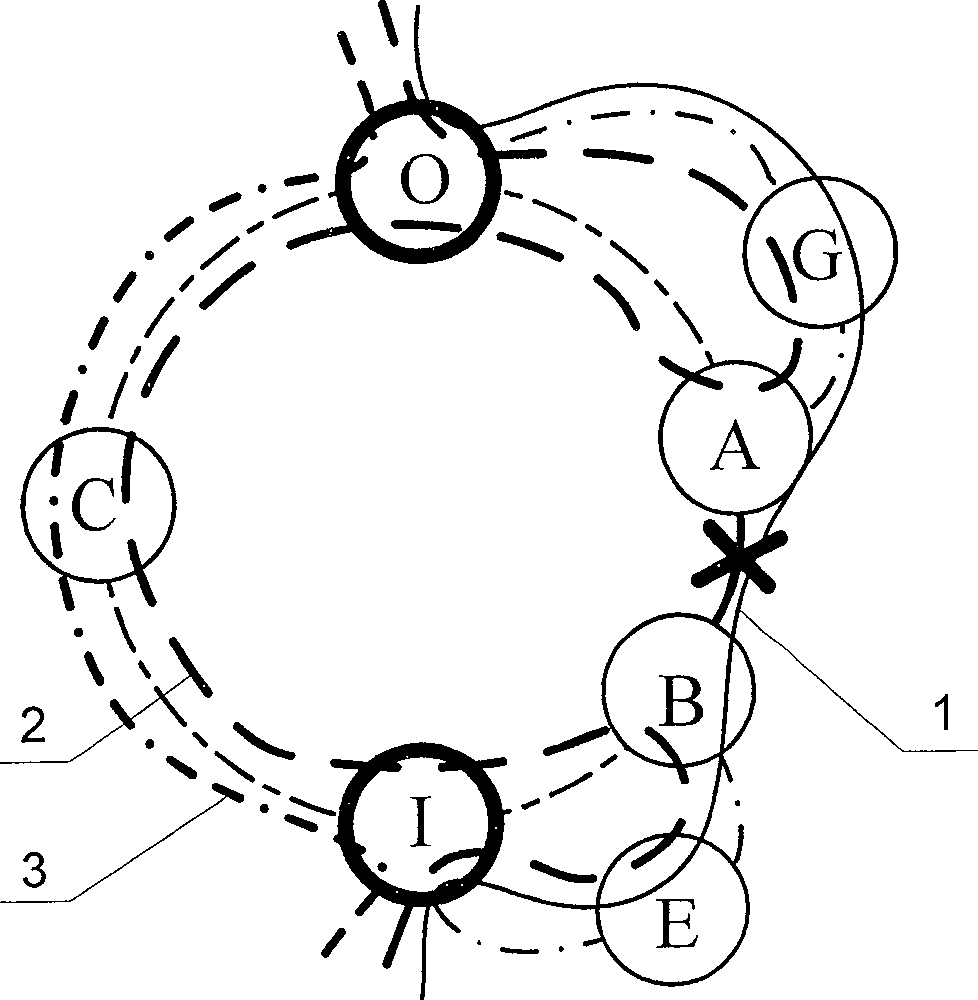
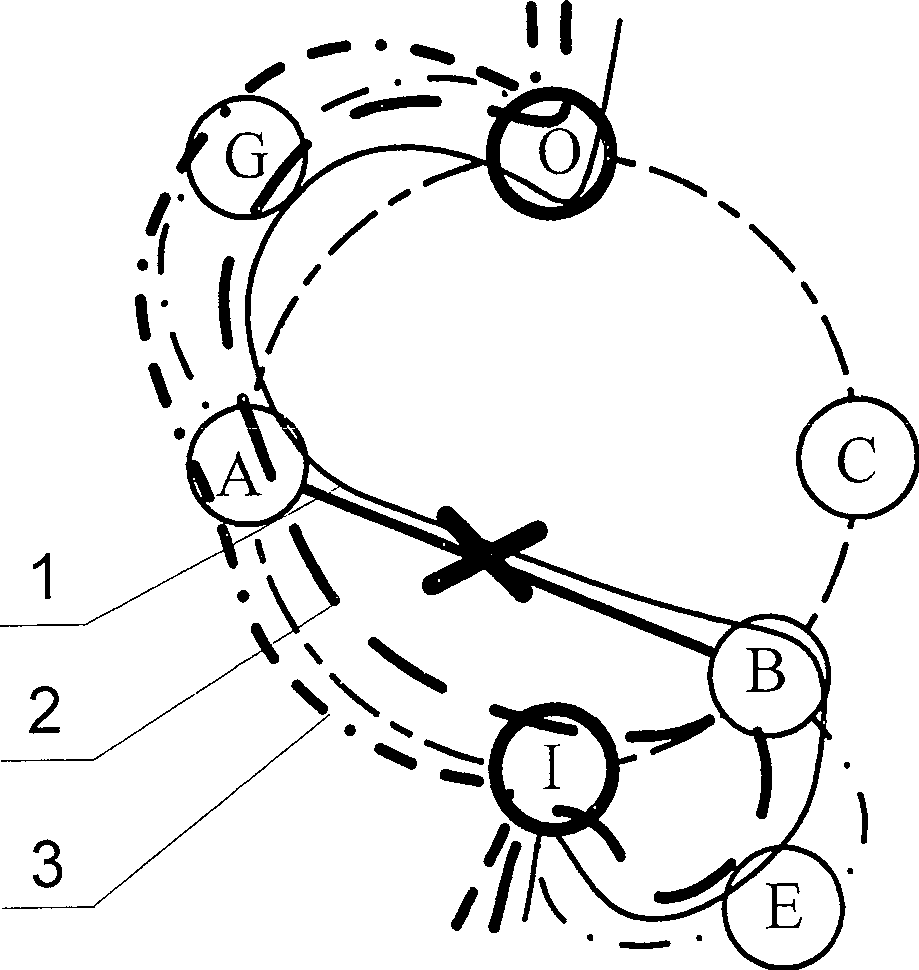
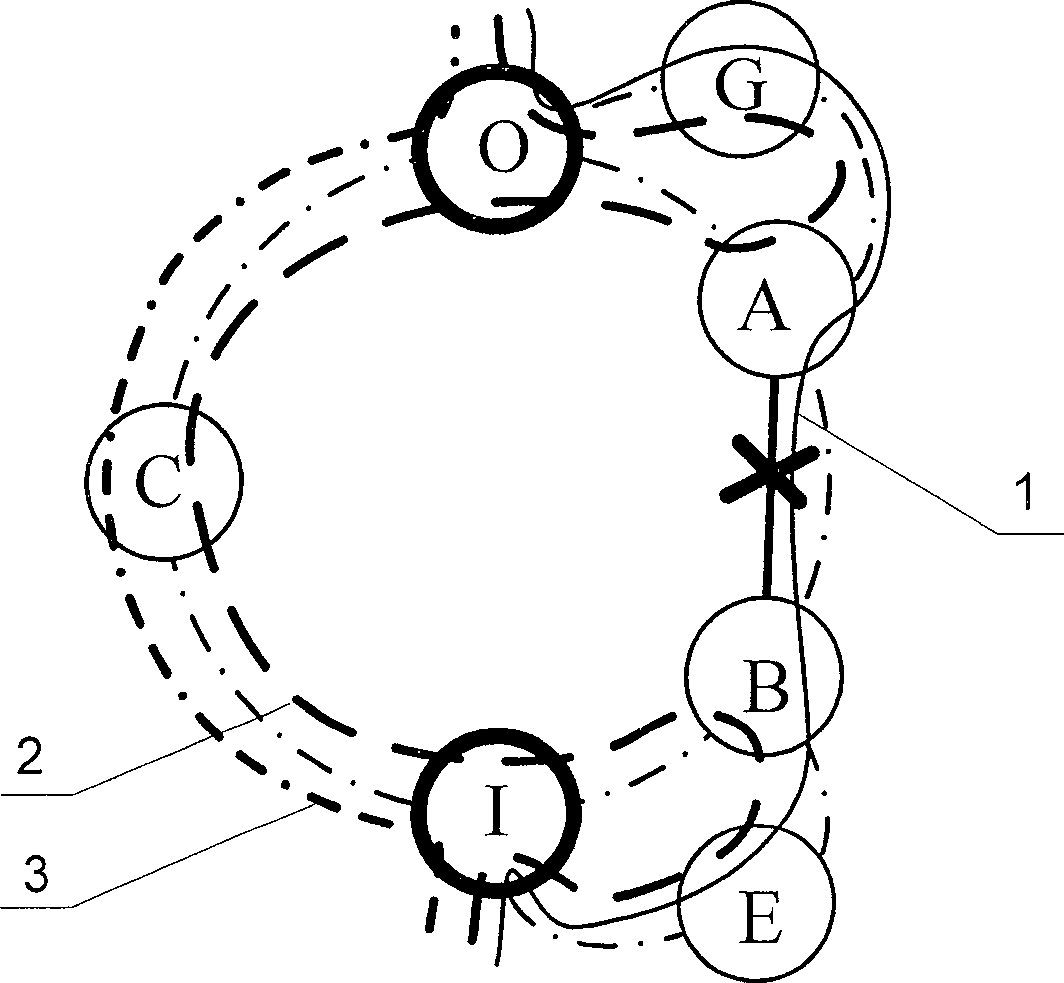
[0012] figure 1 —7 shows the application of the foldback protection switching method and the source routing protection switching method in different types of preset protection circles. In the figure, 1 is the working service; 2 is the recovery path using the foldback protection switching method; 3 is using the source routing switching method recovery path. exist figure 1 In —7, it is assumed that work business 1 passes through nodes I, E, B, ( Figure 7 D), F, A, G, O in D). Among them, nodes I, B, A, O and C are nodes on the preset protection circle, Figure 4 —The node F in 5 cannot be a node on the preset protection circle, and Figure 7 The nodes F and D in can be the nodes on the preset protection circle. exist figure 1 In each figure of —7, there are two recovery paths r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com