Method for generating electronic invoice and interactively using based on communication network
An electronic invoice and communication network technology, applied in the application field of network security technology, can solve the problems of inconvenient data collection and reuse, high cost of paper invoices, lagging invoice transmission, etc., to save invoice costs, facilitate real-time monitoring, and be difficult to forge and the effect of cracking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
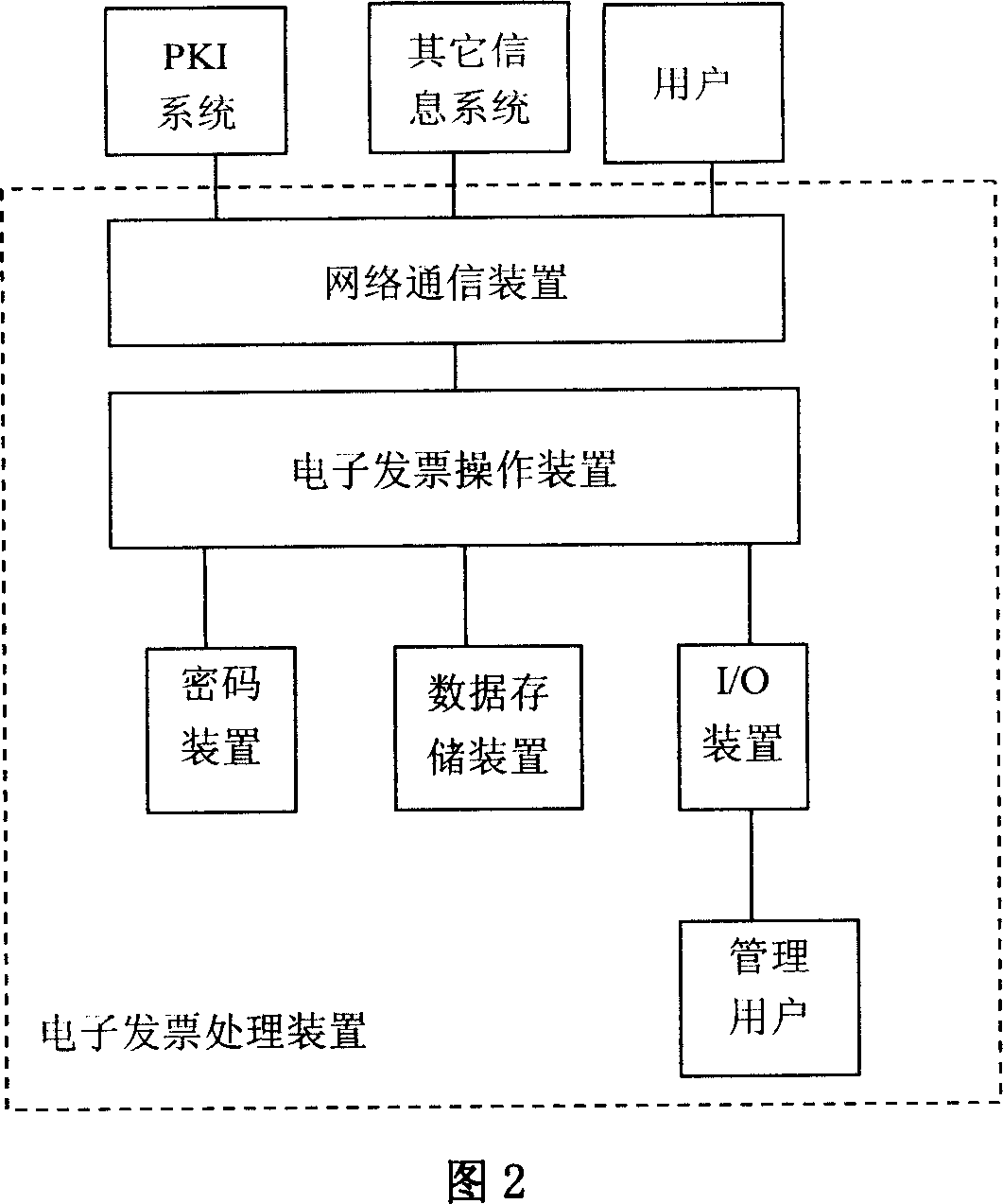
Image
Examples
Embodiment Construction
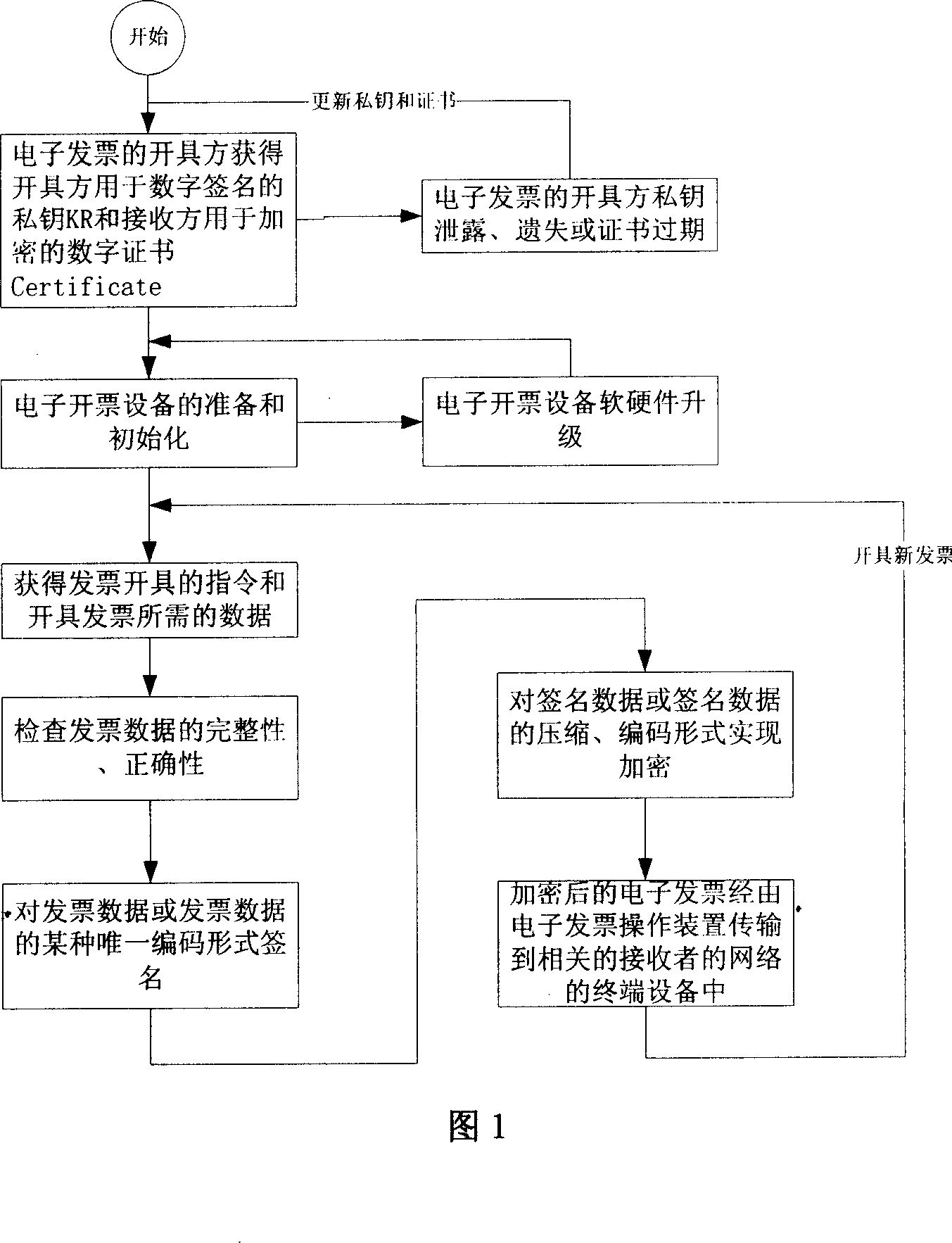
[0008] The generation process of online electronic invoice is as follows: (see Figure 1)
[0009] In the first step, the issuer of the electronic invoice obtains the private key KR used by the issuer for digital signature and the digital certificate used by the recipient for encryption.
[0010] The issuer of the electronic invoice must obtain the private key string KR used to sign the invoice data and the corresponding digital certificate Certificate used to identify the holder before issuing the invoice. The digital certificate contains the public key string KP used to verify the signature of the private key. Digital certificates are generally issued by an authoritative certificate authority (CA) to prove the identity of the certificate holder to a third party. Digital certificates can be downloaded from the download address provided by the certificate authority, or obtained by other means. The private key can be obtained by the issuer using a key generation device (such a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com