Authentication device, method and system
A technology for authentication equipment and authentication methods, which is applied in the field of information security, and can solve problems such as inconsistent authentication passwords, unstable information security equipment, and failure of legitimate users to log in successfully.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
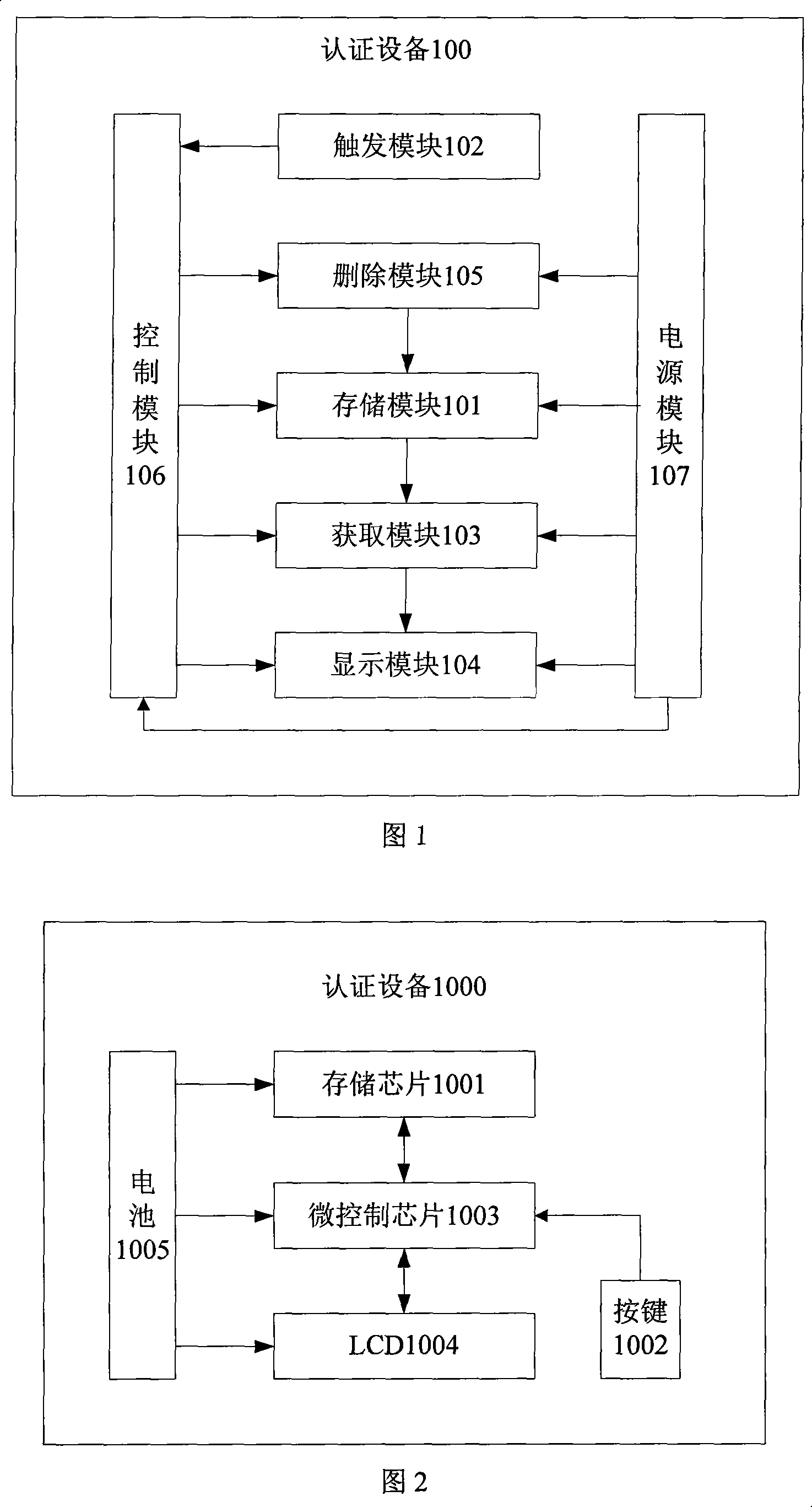
[0112] Referring to Fig. 1, an embodiment of the present invention provides an authentication device 100, which specifically includes a storage module 101, a trigger module 102, an acquisition module 103, a display module 104, a deletion module 105, a control module 106 and a power supply module 107:
[0113] The storage module 101 is connected with the control module 106, and is used for storing a set of authentication passwords;
[0114] Storage module 101 can be an independent storage device, as FLASH chip, SD (Secure Digital, safe digital) card, microhard disk or smart card etc., also can be the storage device in the control chip (as the security design chip with storage unit etc.), the storage medium can be RAM (Random Access Memory, random access memory), ROM (Read-Only Memory, read-only memory), EPROM (Erasable Programmable Read-Only Memory, erasable programmable read-only memory), EEPROM (Electical Erasable Programmable Read-Only Memory, electrically erasable programma...
Embodiment 2
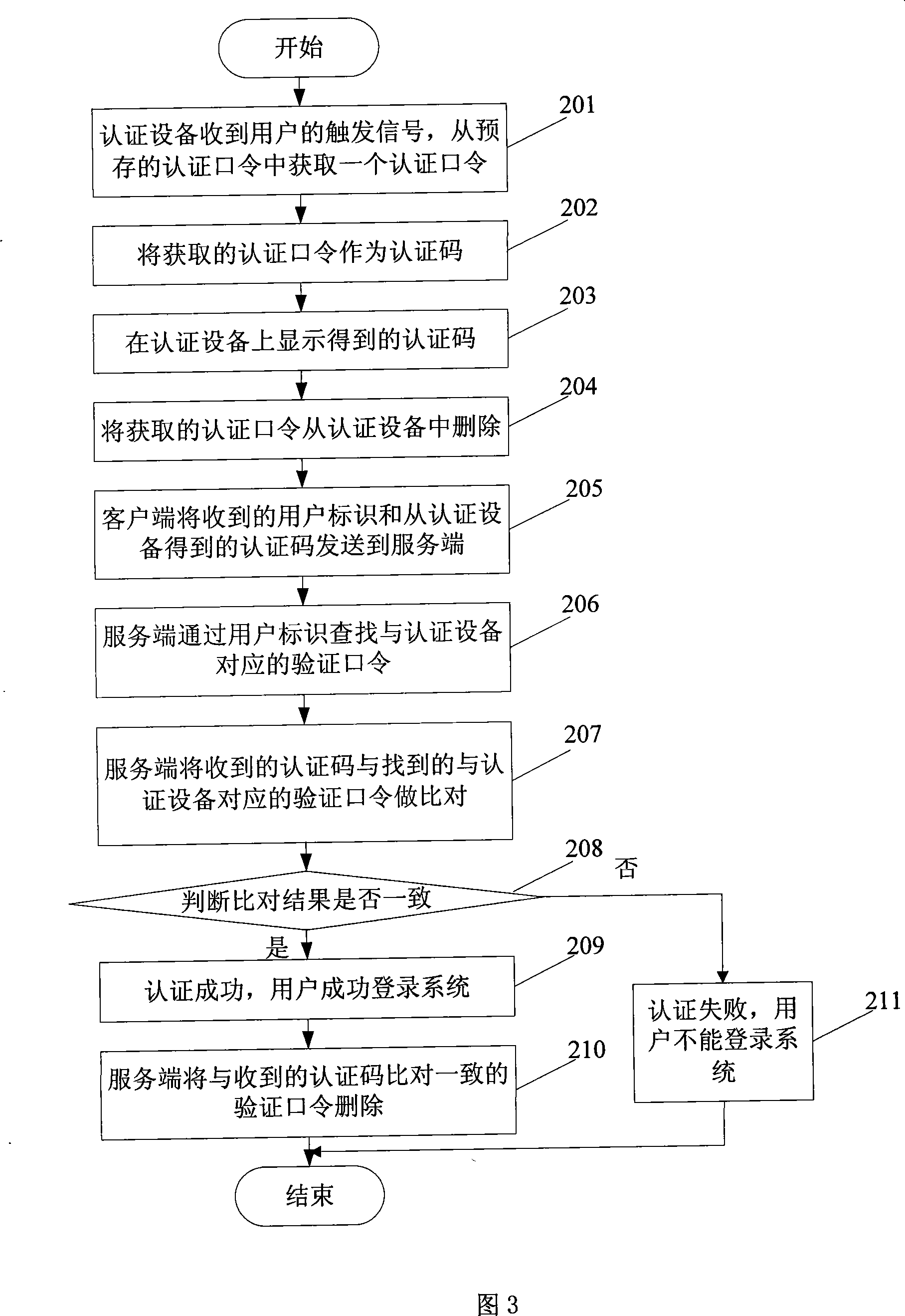
[0151] The embodiment of the present invention provides an authentication method, in which a set of corresponding authentication passwords and verification passwords are stored in the authentication device and the server in advance, the authentication device obtains the authentication password as the authentication code after receiving the trigger signal, and the client receives the user Enter the user ID and authentication code, and send the user ID and authentication code to the server, and the user can log in only after the server authentication is passed.
[0152] In this embodiment, a set of authentication passwords needs to be stored in the authentication device in advance, and a user ID and a set of verification passwords corresponding to the set of authentication passwords stored in the authentication device are stored on the server side. The authentication password and the verification password can be provided by the device Produced by the manufacturer, it can also be ...
Embodiment 3
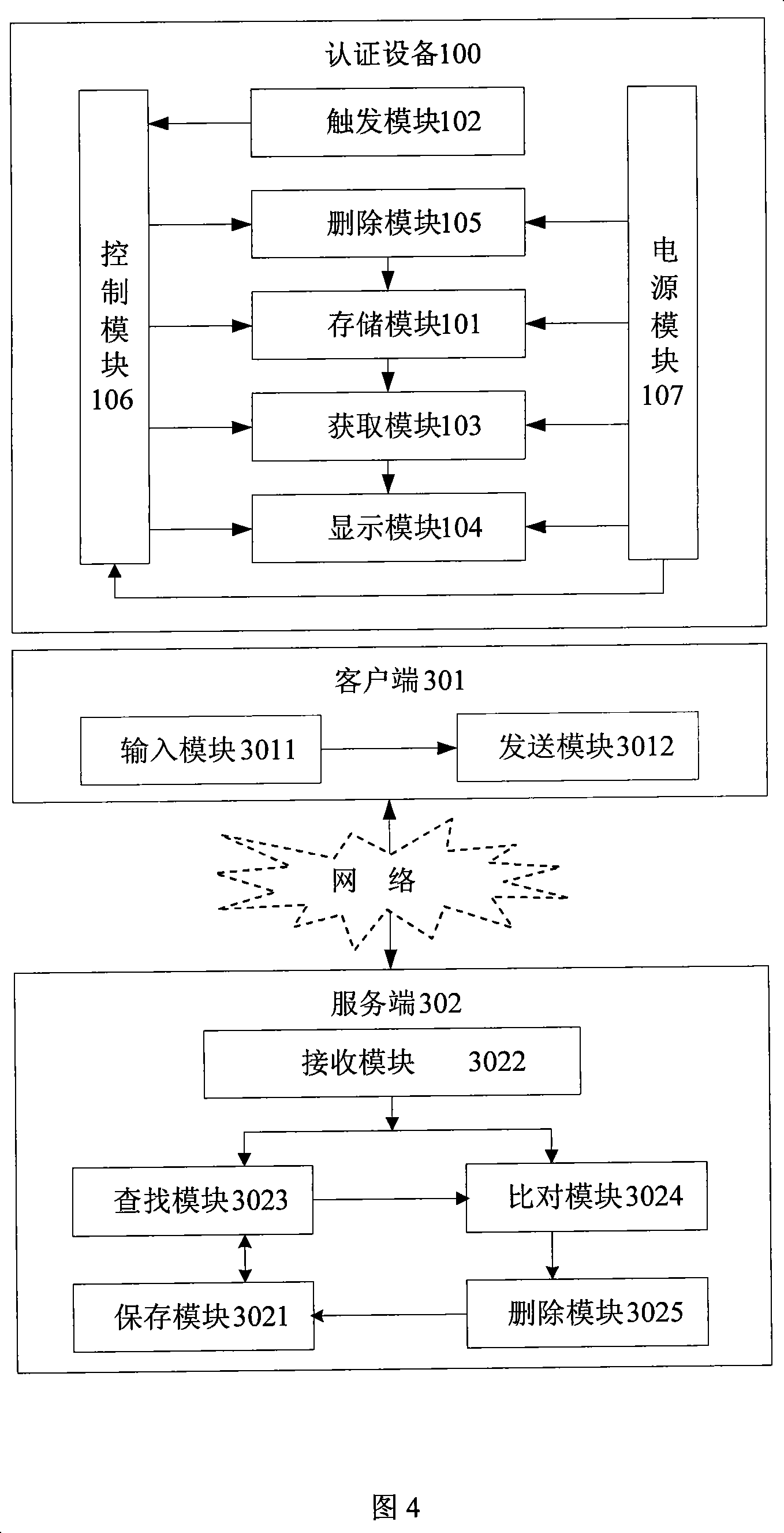
[0186] Referring to Fig. 4, the embodiment of the present invention also provides an authentication system, the system includes an authentication device 100, a client 301 and a server 302;
[0187] Authentication device 100 includes:
[0188] The storage module 101 is connected with the control module 106, and is used for storing a set of authentication passwords;
[0189] The trigger module 102 is connected to the control module 106 for generating a trigger signal;
[0190] The obtaining module 103 is connected with the control module 106, and is used to obtain an authentication password from the storage module 101 under the control of the control module 106 as an authentication code;
[0191] The display module 104 is connected to the control module 106, and is used to display the authentication code obtained by the acquisition module 103 under the control of the control module 106;
[0192] The deletion module 105 is connected with the control module 106, and is used to d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com