Network inbreak event association detecting method
An event correlation and detection method technology, applied in the field of network security, can solve the problems of large system resources and time consumption, low alarm information matching efficiency, low efficiency, etc., to achieve accurate identification of attacks, improve accuracy, and improve speed and efficiency. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
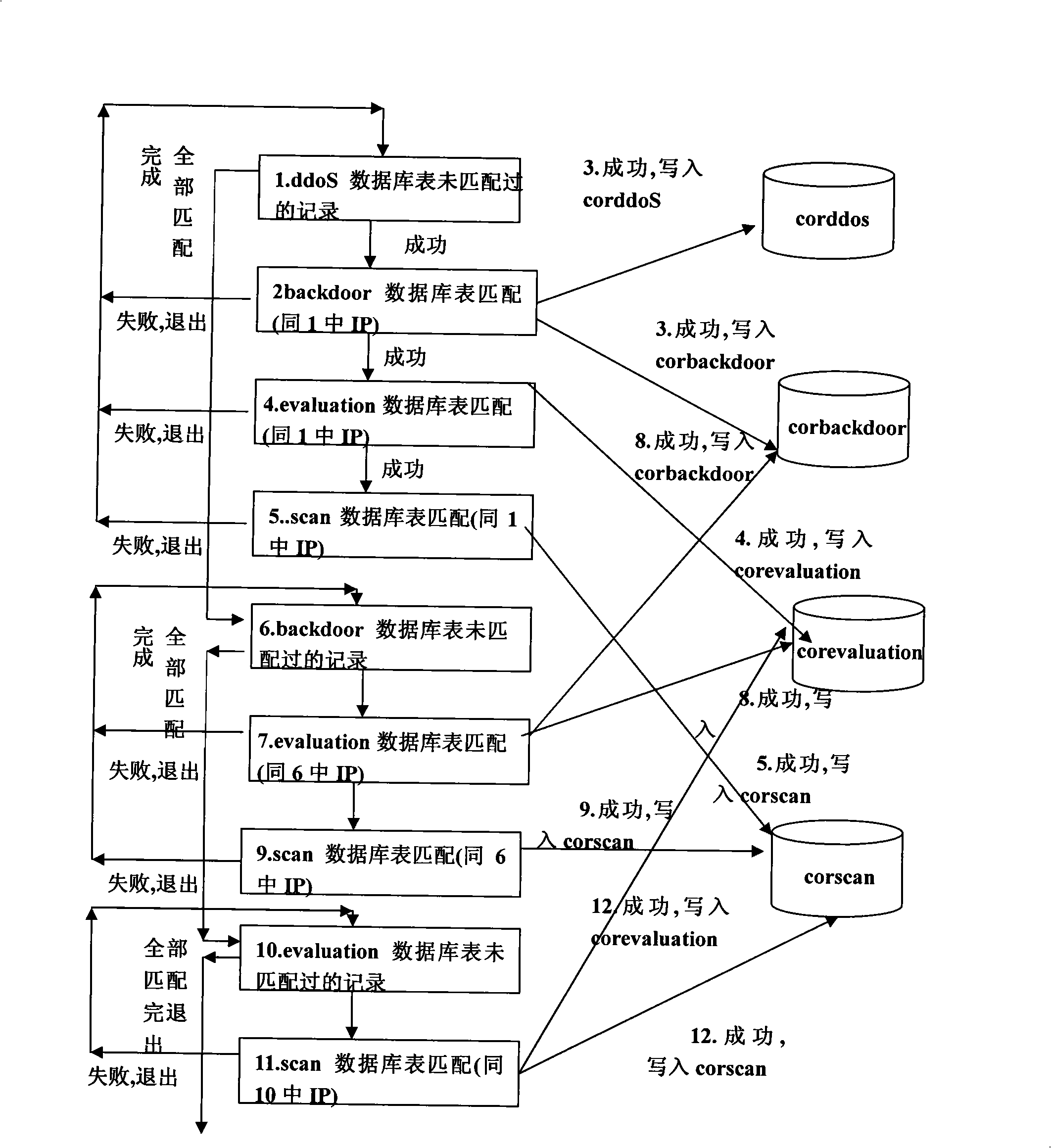
Image
Examples
Embodiment Construction
[0021] The embodiments of the present invention are described in detail below in conjunction with the accompanying drawings: this embodiment is implemented on the premise of the technical solution of the present invention, and detailed implementation methods and specific operating procedures are provided, but the protection scope of the present invention is not limited to the following the described embodiment.
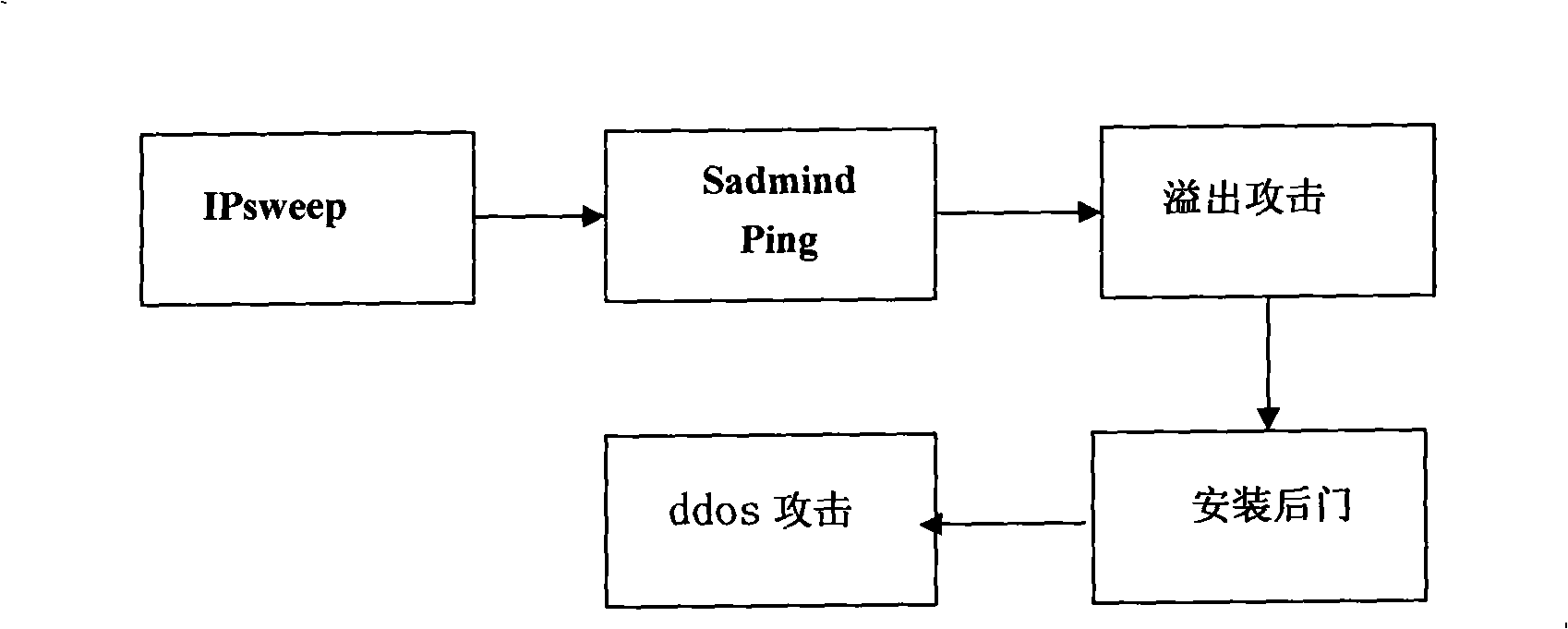
[0022] like figure 1 As shown, the behavior of hackers invading the system has a certain sequence relationship. Take the use of the Sadmind vulnerability (a system security vulnerability) on the Solaris (a UNIX operating system) host to carry out a denial of service attack as an example. This attack first Buffer overflow attack to obtain the root user authority on the host, and then launch a denial of service attack. Its general intrusion steps are as follows:
[0023] 1. Use the port scanning tool (IPsweep) to scan the target network to detect active host informatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com