Distributed system access control method based on component and access control system
A distributed system and access control technology, applied in the direction of multi-program devices, etc., can solve the problems of insufficient granularity of access control, ignoring other attributes, lack of interfaces and standards, etc., to achieve safe and reliable query and response, and avoid duplication. Development, the effect of reducing development costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
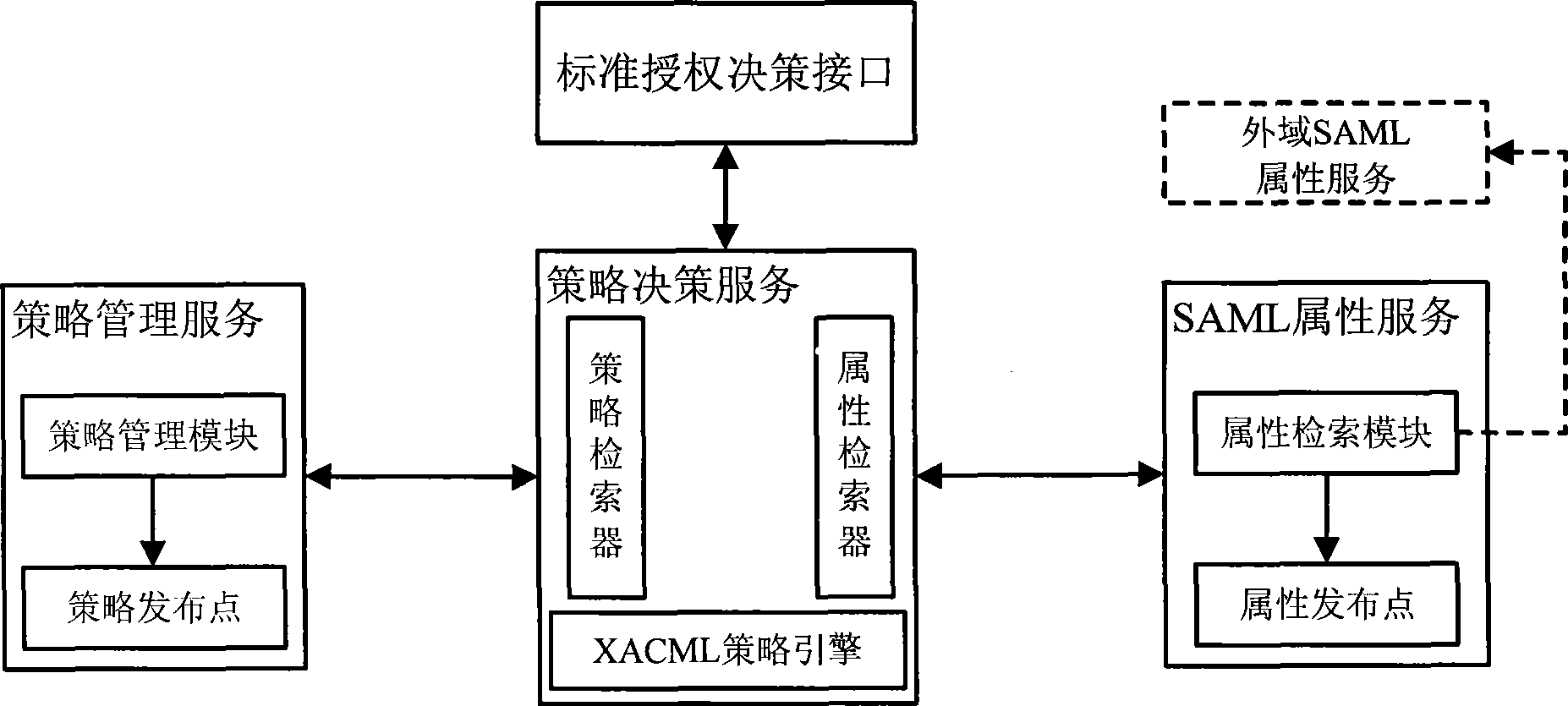
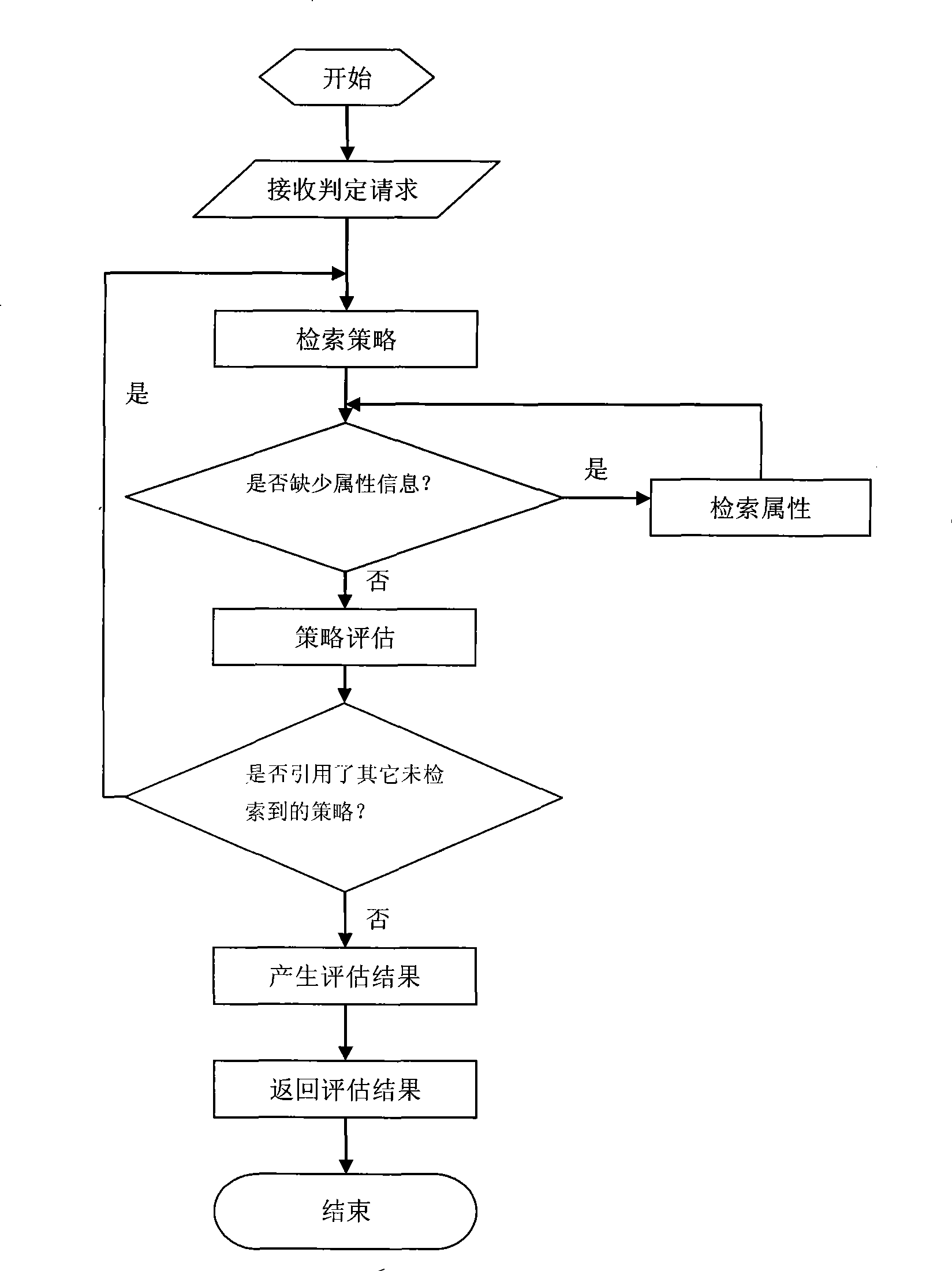
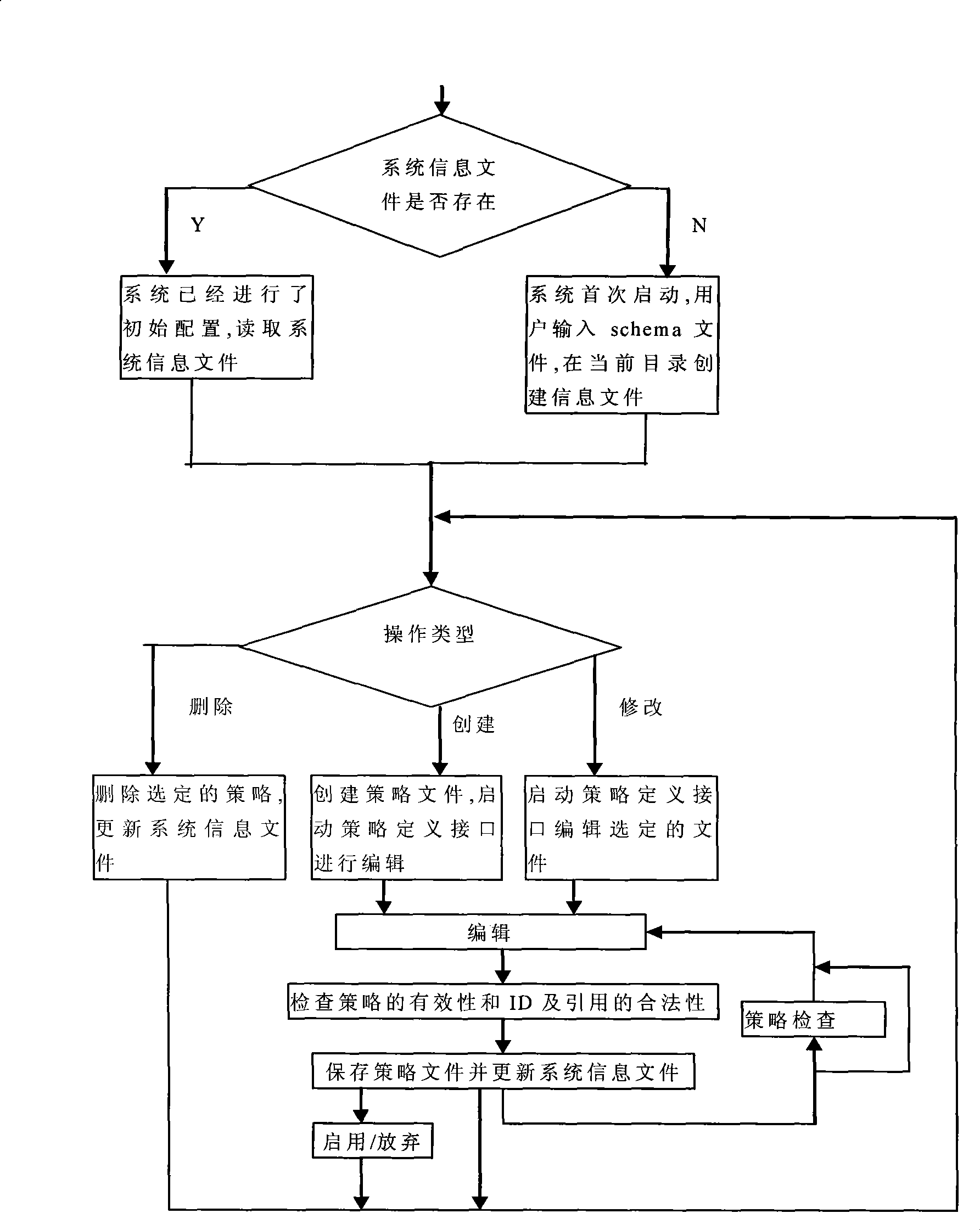
[0079] 1. The standard authorization decision interface (LOIS ADI) implements a general authorization interface that supports multiple information formats, and the application server can request access control services through calling this interface. Another function of the standard authorization decision interface is to convert the access control information into a decision request format conforming to the XACML specification and submit it to the policy decision service. Because some interfaces are not fully compatible with the format described by XACML, the definition of some data structures and services can be extended and modified in the process of implementation, so as to work with the XACML specification and maintain the expressive ability of XACML.
[0080] The authorization decision interfaces in LOIS ADI mainly include the following categories:
[0081] 1. Subject-resource-behavior-environment category: The application calls the interface by specifying subject informa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com