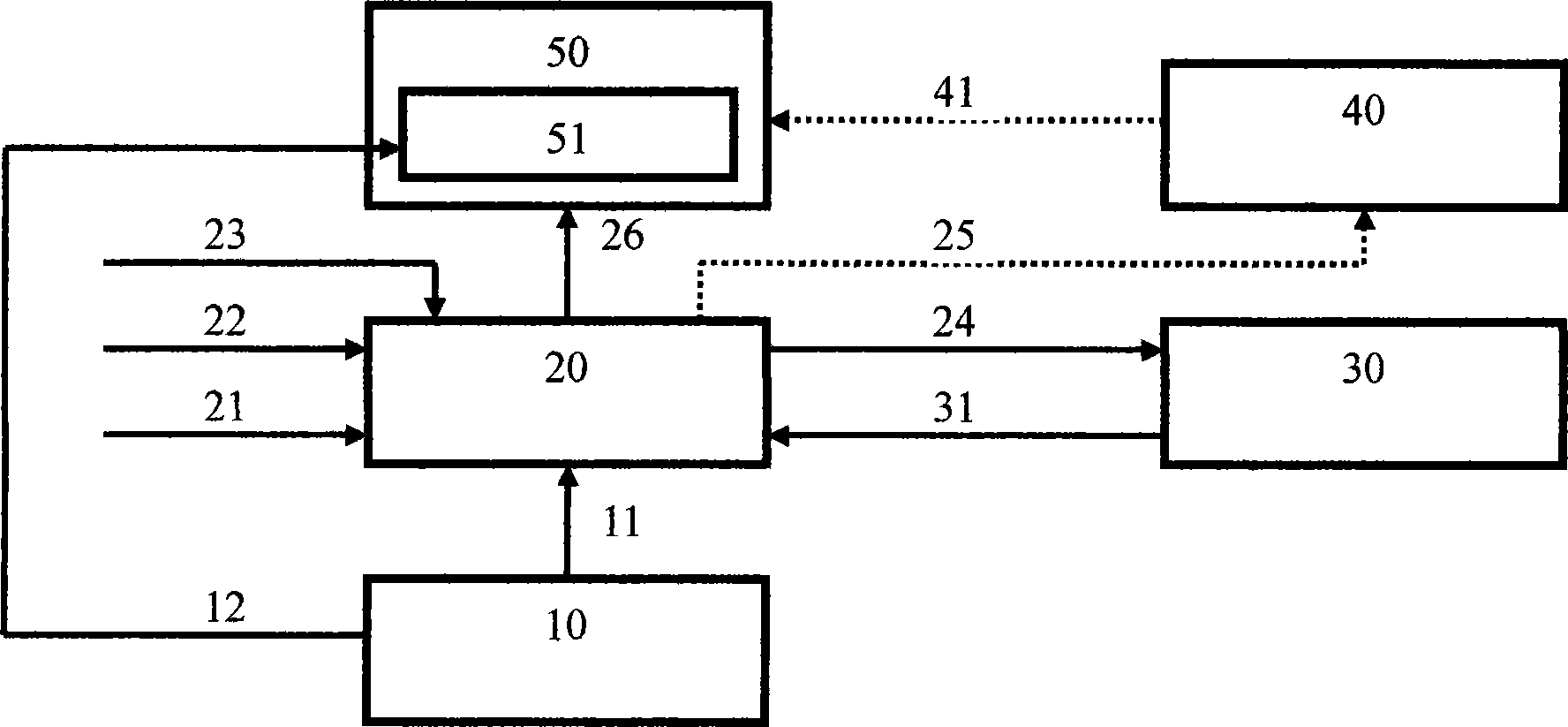
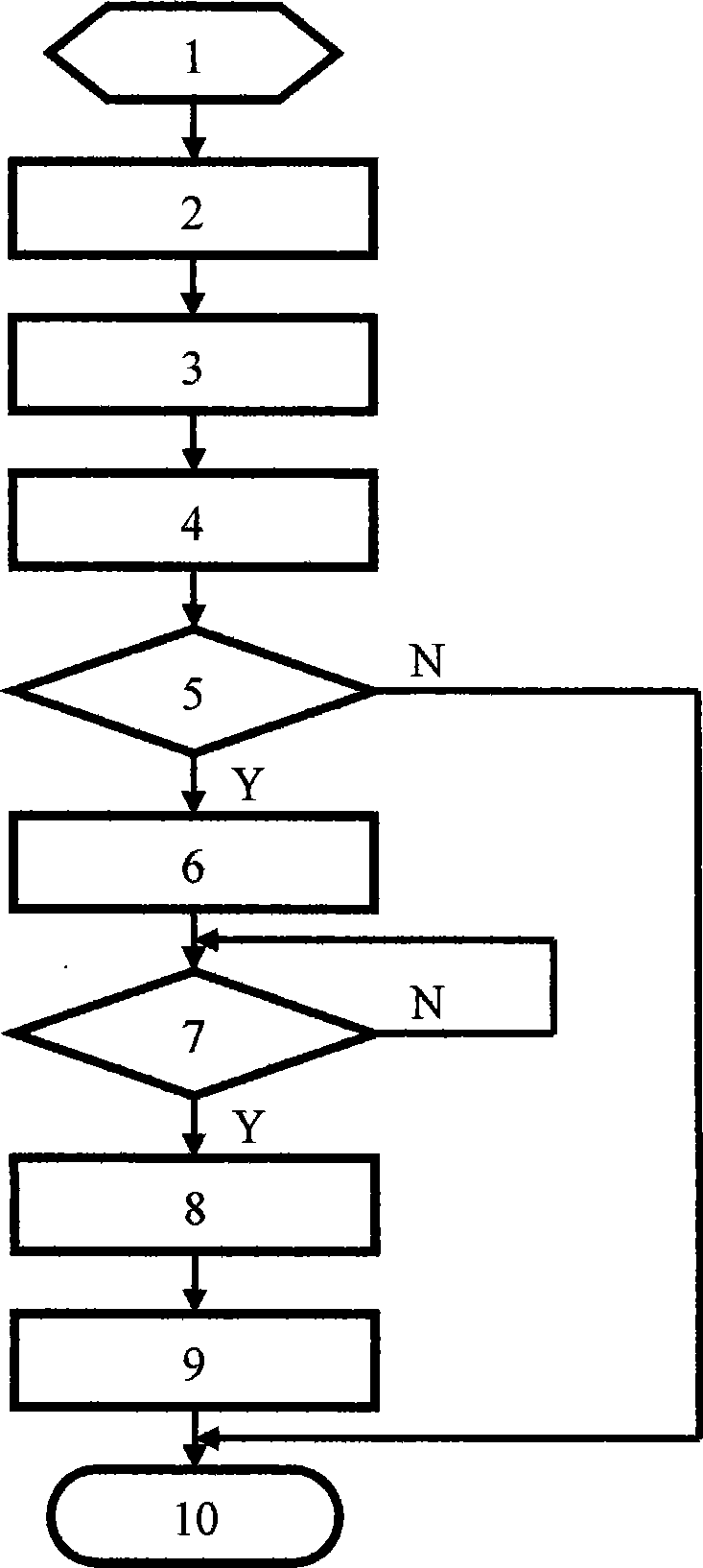
Login protection method
A technology for login interface and login information, which is applied in the fields of computer software, network communication and information security, and can solve the problems of accurate judgment, inability to solve the hidden worries of eavesdropping on the keyboard and peeping at the screen, and upgrading the operating system version.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] Set the target operating environment as Microsoft's Windows operating system, using the Visual Studio.Net integrated development platform.
[0017] 1. Implementation of hook protection.
[0018] Develop a Visual C++ type MFC dynamic link library (DLL) project, only create an empty callback function LRESULT CALLBACK RecoveryCallWndProc(int nCode, WPARAM wParam, LPARAM lParam){
[0019] / / return CallNextHookEx();
[0020] return NULL;
[0021]}
[0022] As a defensive hook program, the code in it is only executed to return a value of 0, but not to return the API function call CallNextHookEx(), which intentionally deprives subsequent hooks of running opportunities. The DLL project is compiled to generate the recovery.dll file. For the login program to be protected, obtain its window pointer hWnd, and then call the API function to obtain and save the identity of its belonging thread
[0023] dwWinThreadID = GetWindowThreadProcessId(hWnd, NULL);
[0024] Periodi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com