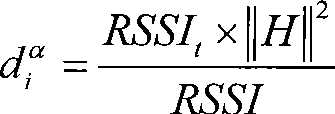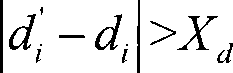Method for detecting Sybil attack
A sybil attack and detection threshold technology, applied in electrical components, wireless communication, network topology, etc., to achieve the effect of reducing energy consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The new scheme is divided into four stages: cluster head election, cluster establishment, time slot allocation and data transmission. In order to express the detection algorithm with the formula conveniently, table 1 shows some parameters used when the algorithm is realized.
[0041] Table 1 Parameters used by the detection algorithm
[0042]
[0043] (1) Cluster head election stage
[0044] The candidate cluster head node broadcasts its own information to the whole network, announcing itself as the cluster head node. At the same time, only one cluster head node can broadcast its own information. Candidate cluster head node H broadcasts message {sequence|ID in plaintext H} Give yourself the surrounding nodes, tell the current round number sequence and cluster head ID H .
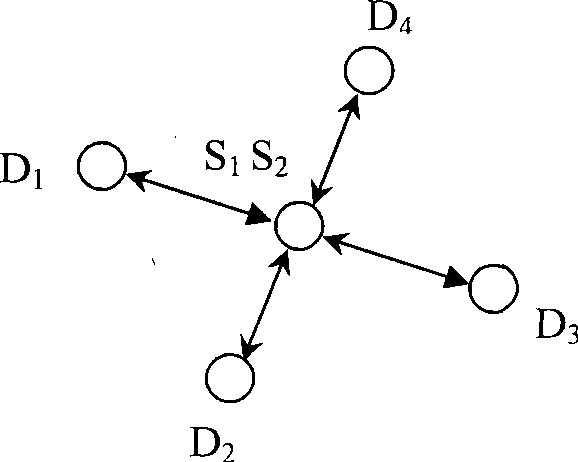
[0045] 1) At this time, the cluster head node detection algorithm is carried out. Suppose a cluster head node communicates directly with more than four member nodes: cluster head node u i To...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com