System and method for managing security of general network
A security management, general network technology, applied in transmission systems, digital transmission systems, data exchange networks, etc., can solve the problems of weak functional completeness, poor scalability, poor openness, etc., and achieve the advantages of functional completeness, scalability, good openness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
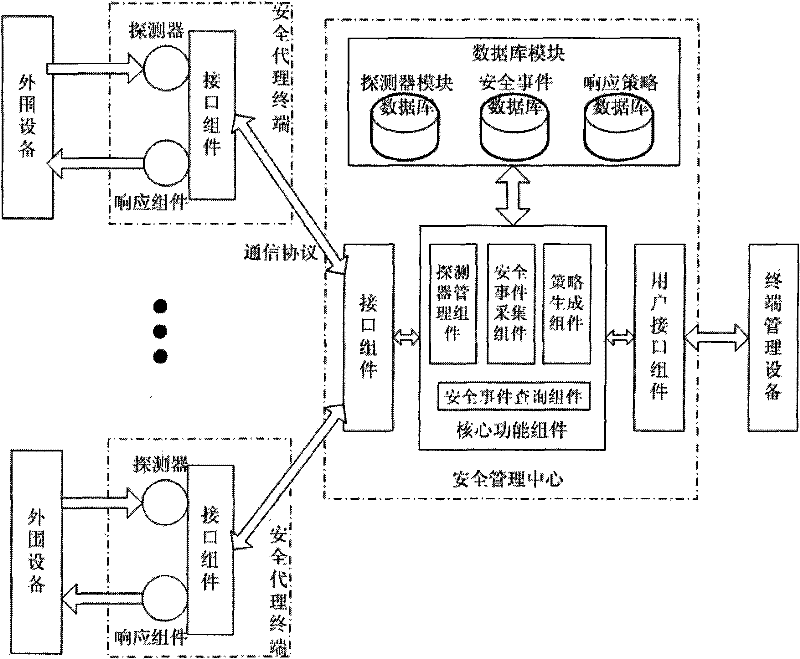
[0047] refer to figure 1 , the general network security management system of the present invention comprises:
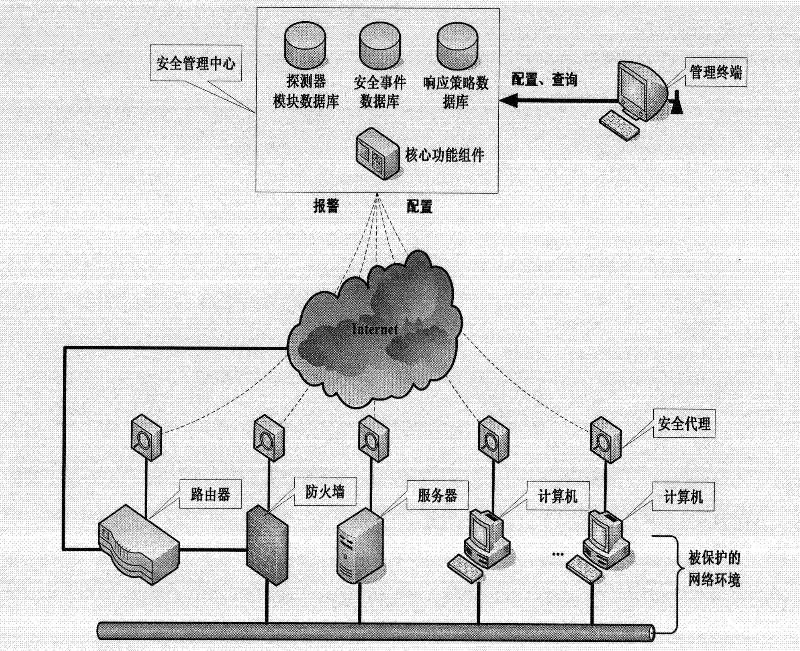
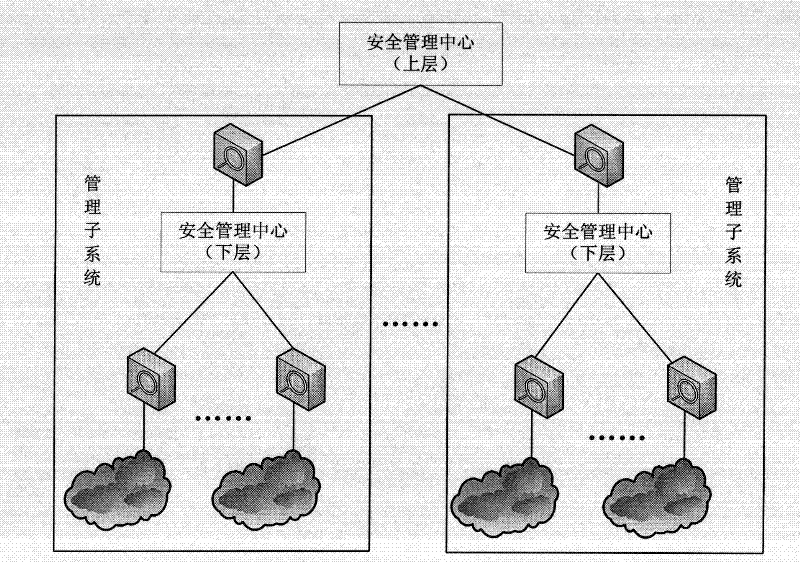
[0048] A. The security agent terminal is installed on the peripheral network equipment, connected with the security management center, and provides security services for the network environment where it is located. It is mainly composed of detectors, response components and interface components. The detector is loaded and configured by the security management center according to the characteristics of the peripheral equipment, and completes the functions of equipment operation status monitoring, intrusion detection, behavior monitoring, log collection, and vulnerability detection; the response component guides the network according to the response command of the security management center Configure the device and eliminate threats, and can complete the functions of configuring the device, blocking intruders, sending warnings to intranet users, and repairing vulnerabi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com