Digital content safeguard system based on transparent encryption and decryption method thereof
A technology of transparent encryption and decryption, digital content, applied in the field of information security, can solve the problems of subdivided authority control, low security, affecting user habits and so on
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0088] The applicable operating system of the present invention has: Microsoft Windows XP, Microsoft Windows2000, Microsoft Windows 2003, Microsoft Windows vista etc.; Hardware environment: Pentium (R) 3CPU, more than 256M memory; Application software: Microsoft Office2000 / XP / 2003 / 2007, Adobe Reader, AutoCAD, etc.; Applicable development languages: C++, C, C#.
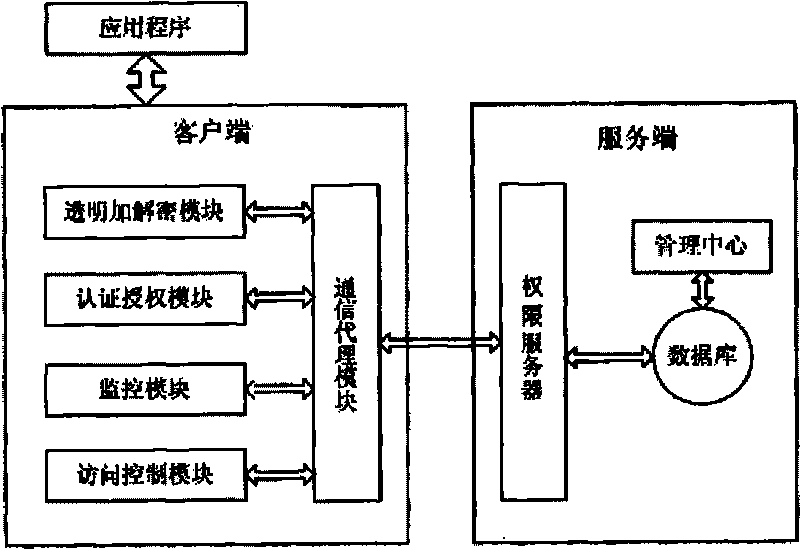
[0089] see figure 1 , a digital content security protection system based on transparent encryption and decryption, including a client and a server, wherein,
[0090] The client includes the following units:
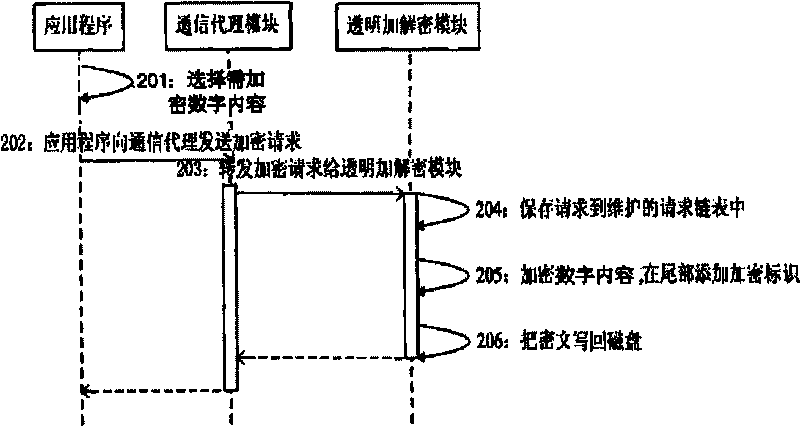
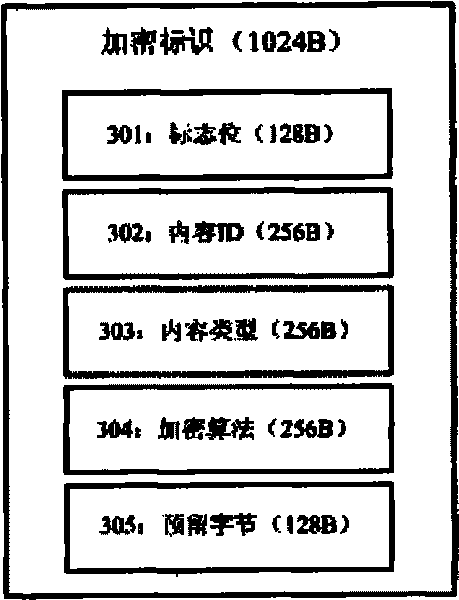
[0091] The transparent encryption and decryption module interacts with the communication proxy module, and is used to receive the digital content encryption request sent by the application program through the communication proxy module, and encrypt the digital content according to the request; during the opening, reading and writing operations, through the communication proxy module Dynamically obtain the requir...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com