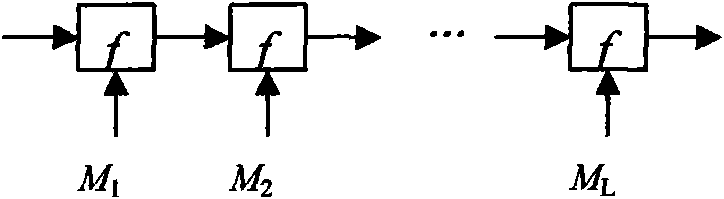
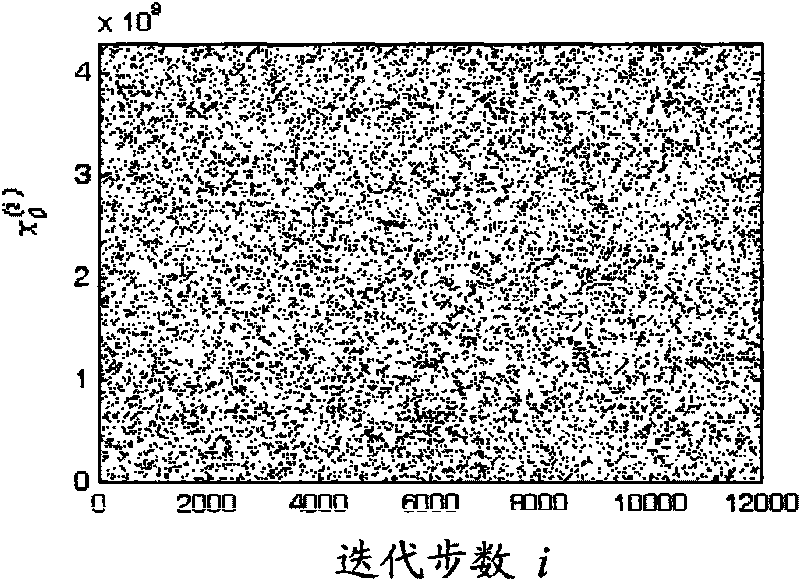
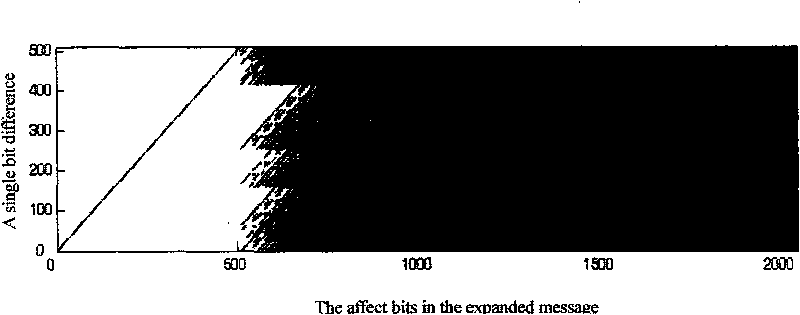
Integral nonlinear mapping-based hash function constructing method
A non-linear mapping, hash function technology, applied in the field of information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0172] Embodiment 1: apply the present invention to carry out digital signature
[0173] Digital signature is a way to sign and confirm electronic messages transmitted online. It has been used in online security payment systems, electronic banking systems, electronic securities systems, secure mail systems, electronic booking systems, online shopping systems, and online bonded systems. A series of signature authentication services for e-commerce applications. Digital signatures have higher requirements on security and anti-forgery, and require verification speed to be faster than signature speed, especially online real-time verification. At present, the secure hash algorithm (SHA-1) is widely used in the digital signature algorithm. When the security of SHA-1 is seriously threatened, it is necessary to use a more secure hash algorithm. The method of the invention has good security and fast execution speed, and is especially suitable for digital signatures. An example of digi...
Embodiment 2
[0195] Embodiment 2: Apply the present invention to carry out password protection
[0196] The security protection of user accounts is an important technical issue in current e-commerce activities. For the user, the most concerned issue is the confidentiality of the password, and the leakage of the password will lead to the user's account being stolen by others. Usually the user's account information is stored in the user account database. If the user's password is stored in plain text in the database, all individuals who have the right to access the user account database can easily obtain other people's passwords. If a hacker gains access to the user account database, all user passwords will be leaked. If the hash value of the password is stored instead of the password of the user directly in the user account database, the purpose of effectively protecting the password of the user can be achieved. In order to prevent "dictionary" attacks, the hash value of the password is n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com