Link security certification method, device and system in wireless relay network
A wireless relay network, security authentication technology, applied in the field of link security authentication, can solve problems such as anti-replay attacks, and achieve the effect of preventing replay attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0049] IEEE 802.16j is an air interface protocol formulated by IEEE to realize relay capability on the basis of 16e. The network architecture defined by it is shown in Figure 3, including:
[0050] MR-BS: a device that provides connection, management and control for relay stations and user terminals;
[0051] RS (Relay Station, relay station): a device that relies on the MR-BS to provide connections for other RSs or mobile stations. Some RSs can also provide management and control for subordinate RSs or user terminals. The air interface between RS and MS is the same as that between MR-BS and MS. The RS is a station that transfers data between the base station and the terminal, so that the wireless signal can reach the destination through multiple transmissions (multi-hops).
[0052] MS (Mobile Station, mobile station): the user uses this device to access the WiMAX network.
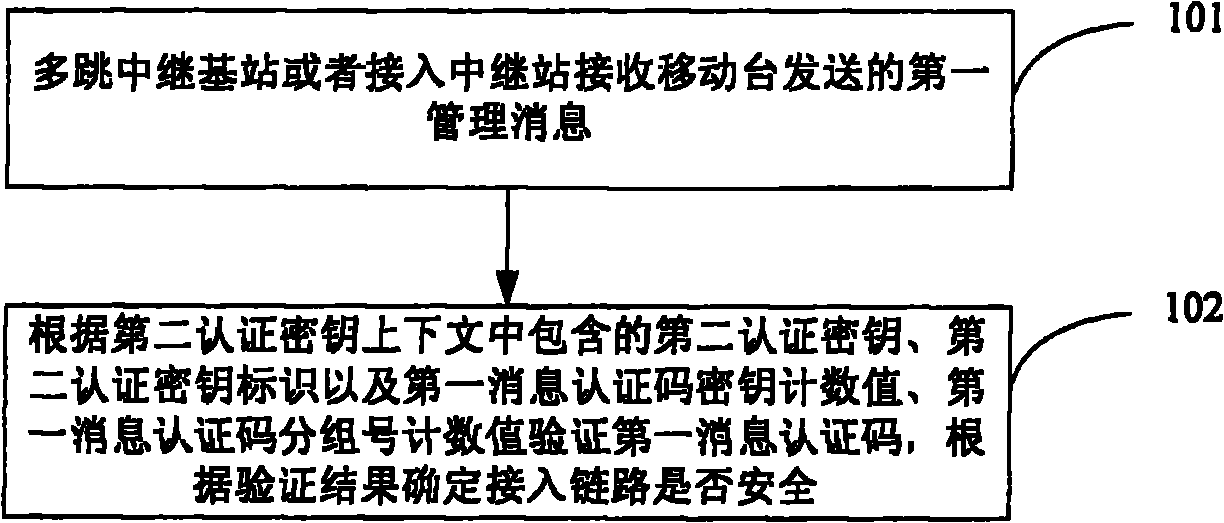
[0053] In the link security authentication method in the wireless relay network provided by this em...
Embodiment 2
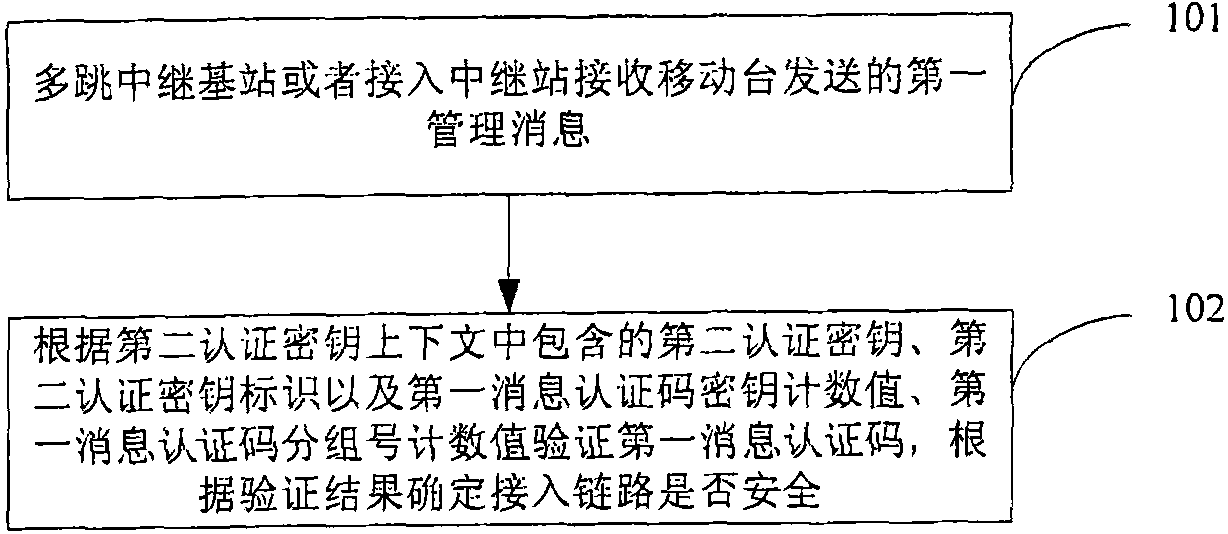
[0102] In the link security authentication method in the wireless relay network provided in this embodiment, the security of the access link is verified first, and then the security of the relay link is verified. The security verification of the access link is based on the MS-related AK context. The security verification of the link is based on the AK context related to the A-RS and the CMAC_KEY_COUNT value used by the access link RNG-REQ. In this embodiment, the MS maintains an MS-related AK context, which contains the CMAC_KEY_COUNT value X M , A-RS maintains a MS-related AK context, which contains CMAC_KEY_COUNT value Y M , the authenticator maintains an MS-related AK context, which contains the CMAC_KEY_COUNT value Z M , A-RS also maintains an A-RS-related AK context, MR-BS maintains an A-RS-related AK context, and maintains an MS-related CMAC_KEY_COUNT value Y MR . Compared with Embodiment 1, there is no need to maintain the A-RS related CMAC_KEY_COUNT value in this em...
Embodiment 3
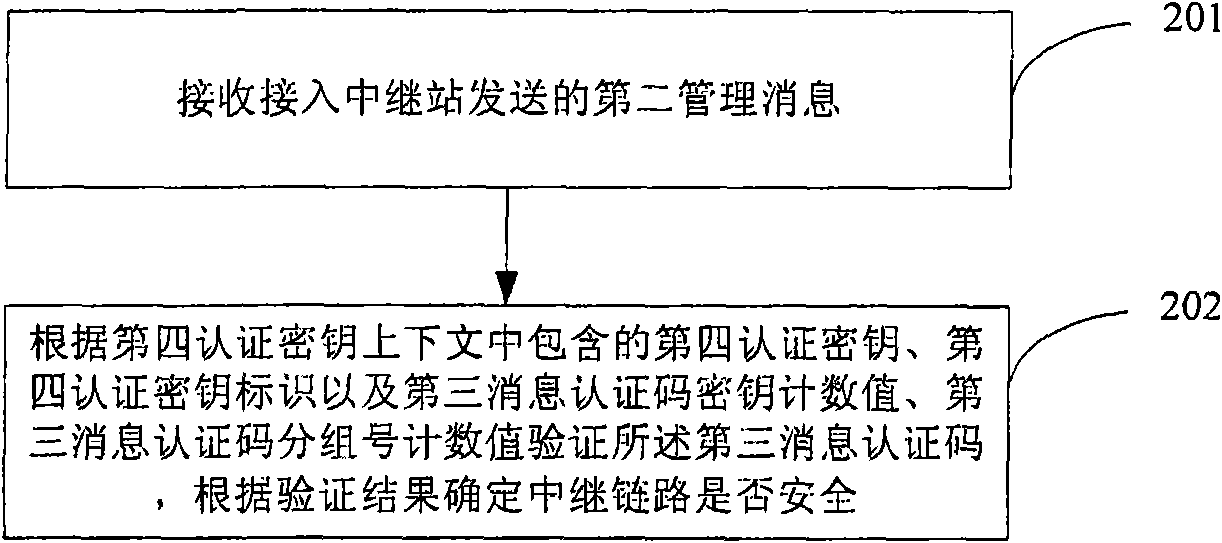
[0137] In the link security authentication method in the wireless relay network provided in this embodiment, the security of the relay link is verified first, and then the security of the access link is verified. The security verification of the access link is based on the MS-related AK context, and the security verification of the relay link is based on the A-RS related AK context. In this embodiment, the MS maintains an MS-related AK context, which contains the CMAC_KEY_COUNT value X M , A-RS maintains a MS-related AK context, which contains CMAC_KEY_COUNT value Y M , the authenticator maintains an MS-related AK context, which contains the CMAC_KEY_COUNT value Z M , A-RS maintains an A-RS related AK context, which contains CMAC_KEY_COUNT value X R , MR-BS maintains an A-RS related AK context, which contains CMAC_KEY_COUNT value Y R . Compared with Embodiment 1, this embodiment first verifies the security of the relay link, and then verifies the security of the access lin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com