Simulation system and simulation method of wireless network security protocol
A security protocol, wireless network technology, applied in the field of wireless network protocol simulation, to achieve the effect of convenient loading, reducing program complexity and low coupling
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
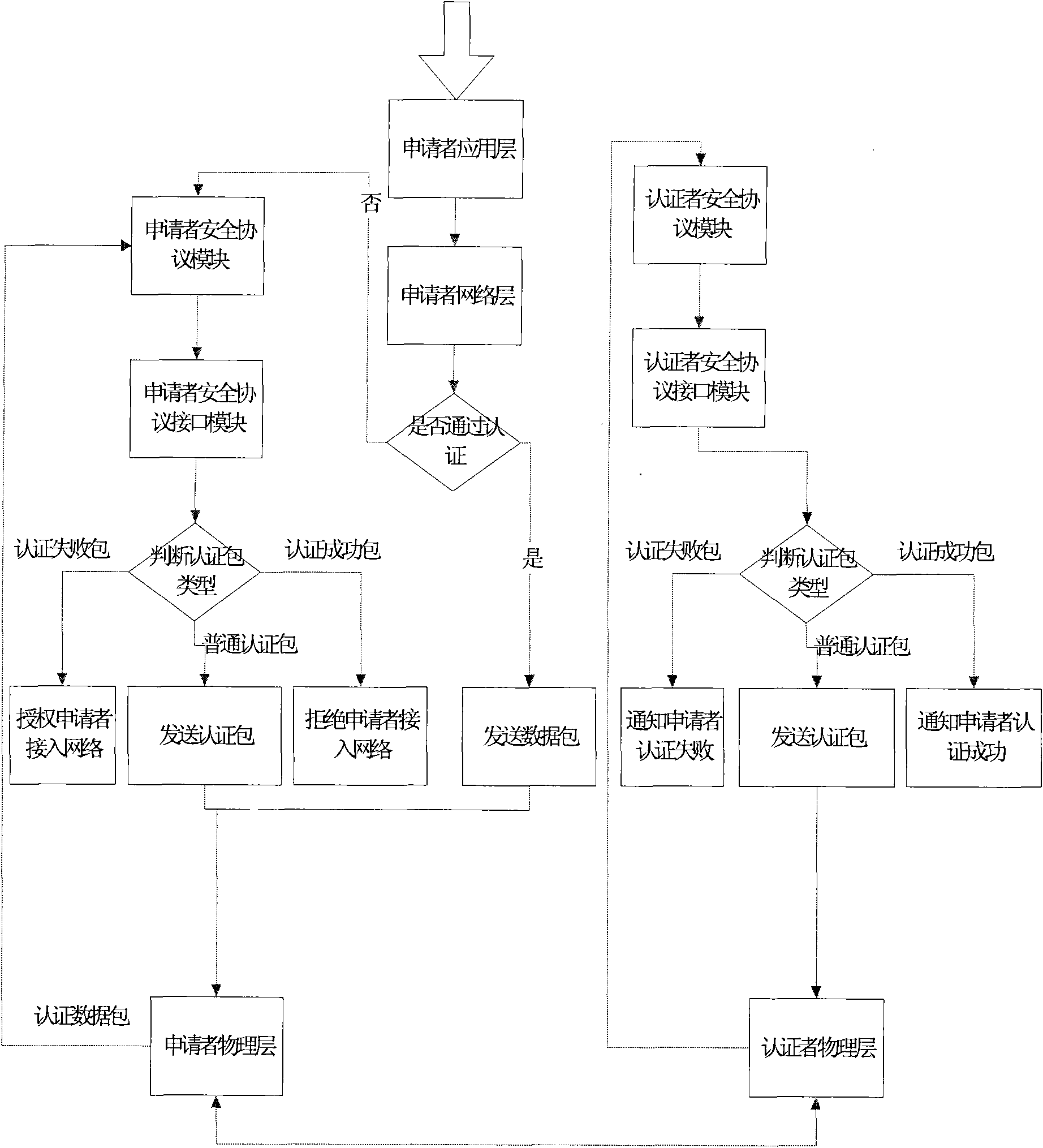
[0086] In order to test the validity of the simulation platform, the present invention takes the test of the WEP security protocol module implemented by the user as an example to illustrate the simulation of the present invention.
[0087] 1. Simulation scene
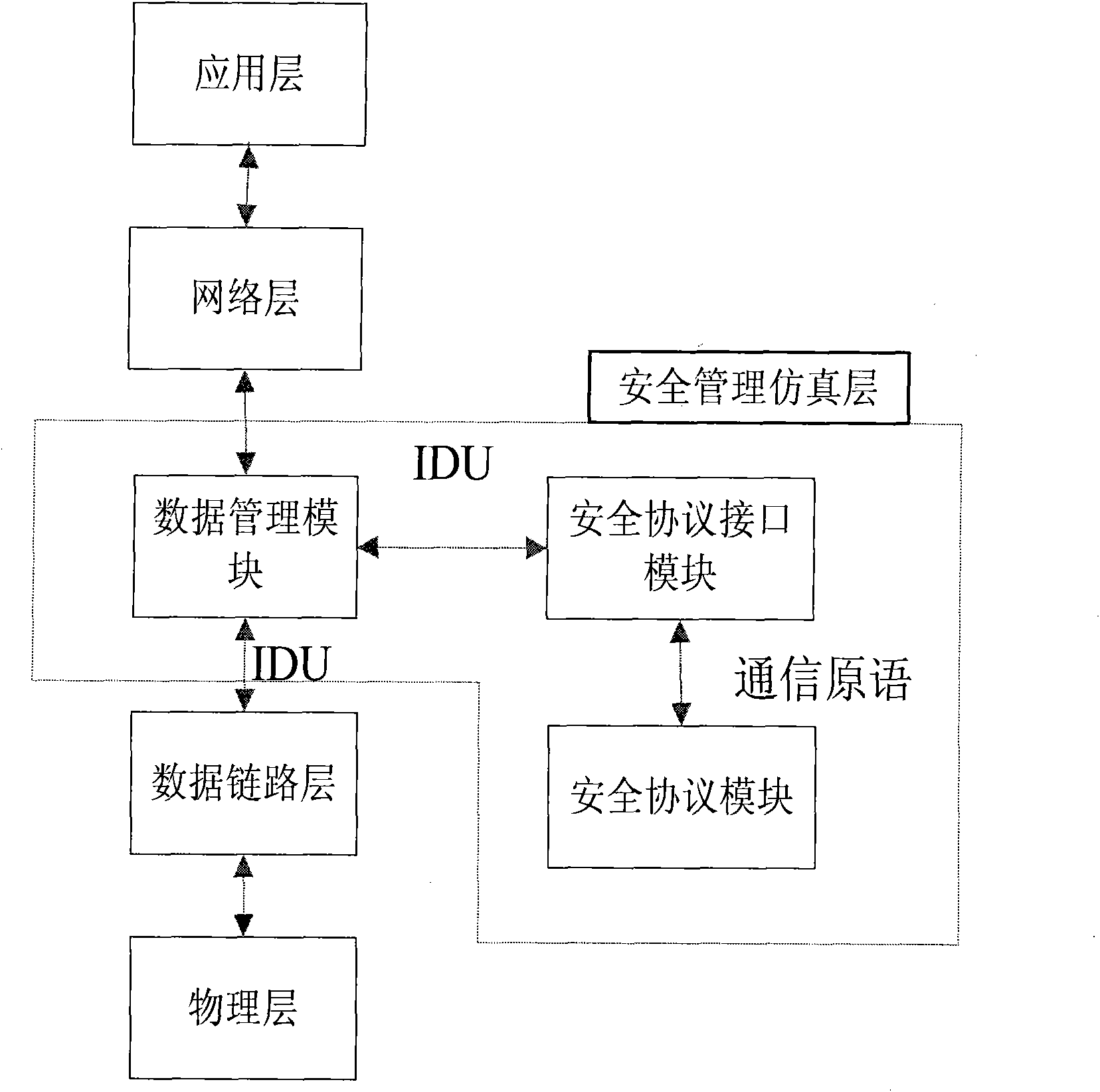
[0088] Figure 4 Shown is the scenario used in this test, S is the applicant, AP is the authenticator, and STA is the destination node for S to send data packets. Figure 5 Shown is the node model of the applicant S who joined the WEP security protocol module, Image 6 Shown is the node model of the applicant S that has not joined the WEP security protocol module.
[0089] This test uses two simulation scenarios, the parameter settings of the two simulation scenarios are the same, S starts to send data packets from the 0th second, the working time is 30 seconds, and the non-working time is 15 seconds. The STA sends a data packet, and the simulation running time is set to 30 minutes. This test adopts the single-facto...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com