Method and system for realizing security audit function in remote control process
A security auditing and remote control technology, applied in the information field to avoid remote transmission of entity data and improve security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
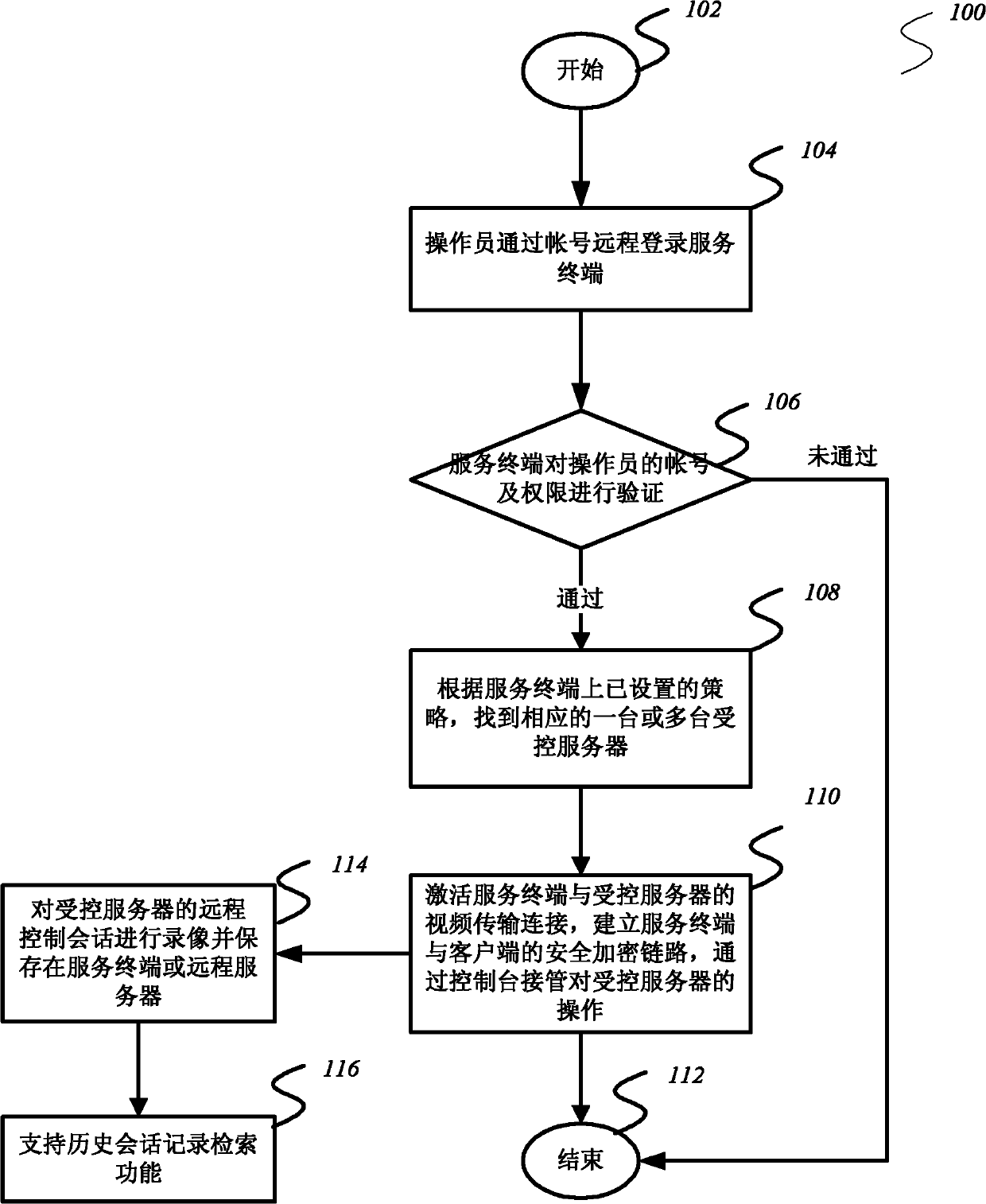
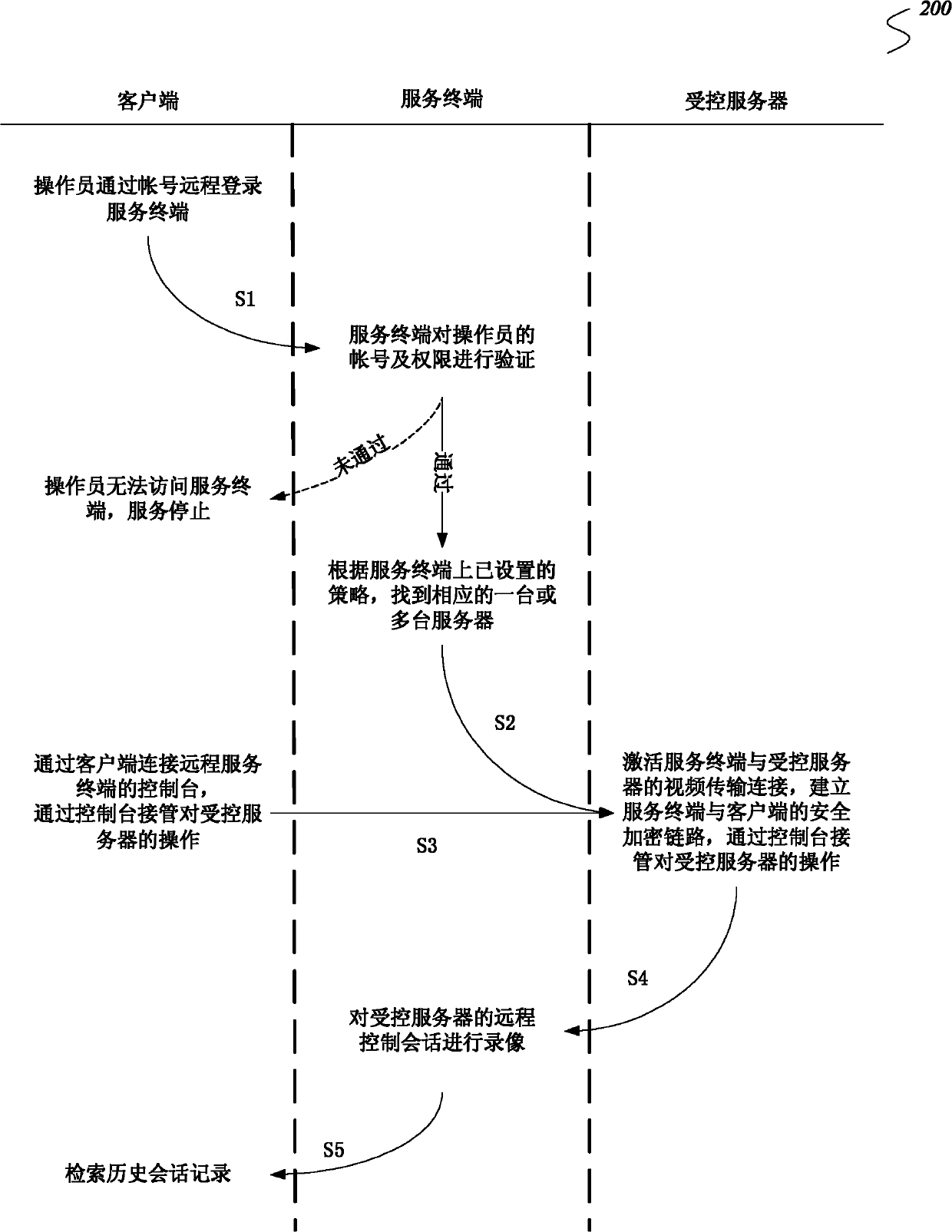
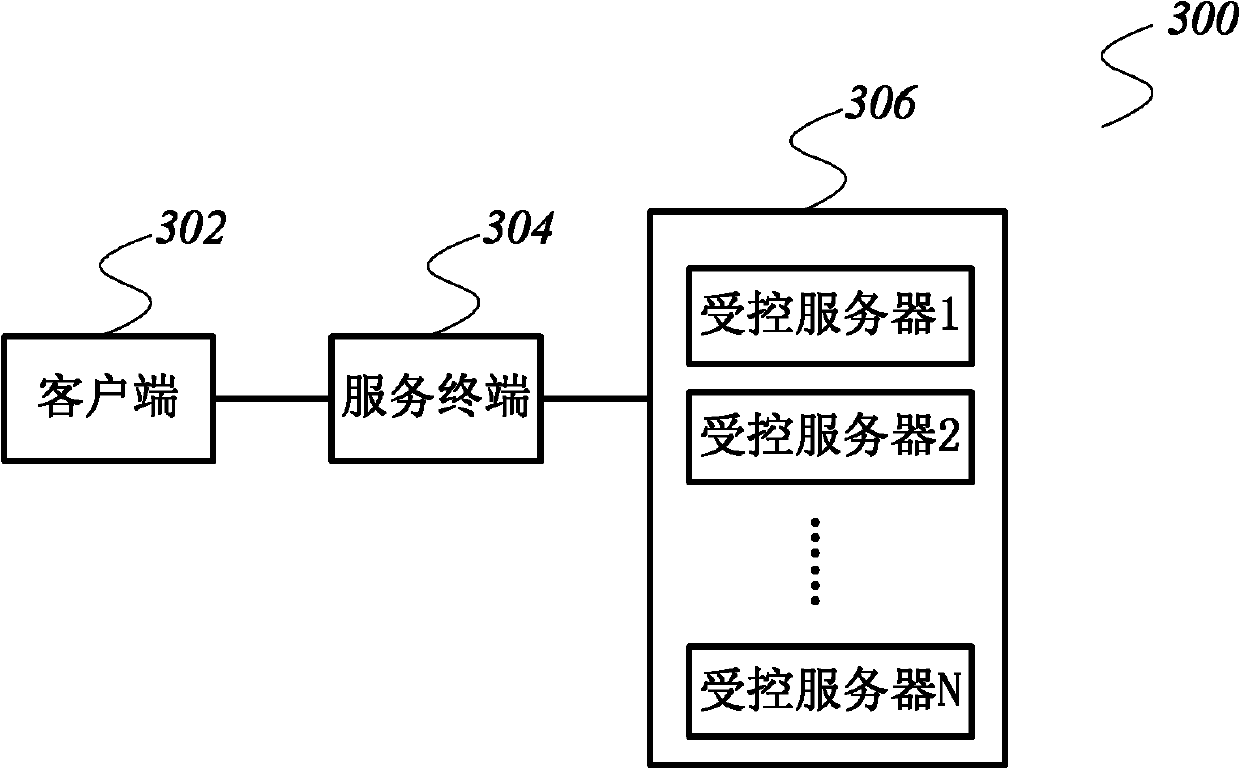
[0032] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
[0033] The invention aims at proposing a method for realizing the safety audit function in the remote control process, which is used to realize the safety and auditability of the remote access control from the external network to the internal network. The invention ensures that the equipment and data of the internal network will not be exposed to the external network. During the whole service process, the service terminal does not need to access the internal network, and only needs to pass through a dedicated video transmission line, and the operator and the controlled The servers transmit interactive information such as mouse, keyboard, and screen display changes. During the whole process, no actual business data flows to the client. What the clien...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com