Perceptual hashing-based practical and safe image forensic system and forensic method
A perceptual hashing and image authentication technology, which is applied in image data processing, image data processing, computer security devices, etc., can solve problems such as slow retrieval speed, security damage, and impact on putting into use, and achieve fast retrieval balance and enhancement The effect of identity authentication and ensuring reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
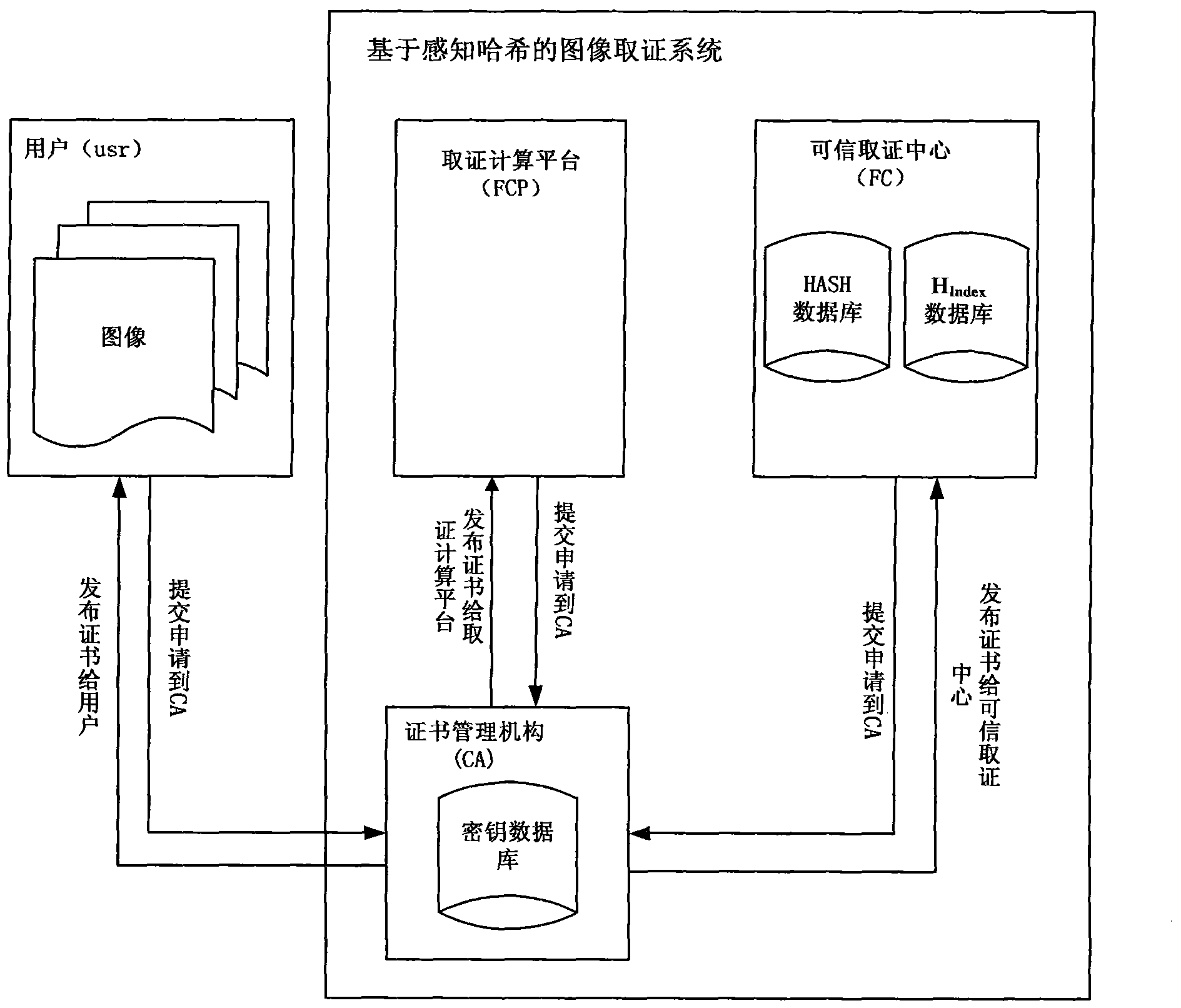
[0070] see figure 1 , the image authentication system based on perceptual hashing in this embodiment includes module a, module b and module c; wherein:
[0071] Module a is the certificate management unit, denoted as CA; module b is the forensics computing unit, denoted as FCP; module c is the trusted forensics center, denoted as FC;
[0072] see figure 2 , when the user registers with the CA, the CA issues a digital certificate to the authenticated user for identity authentication in future communication; CA also issues a digital certificate to FCP and FC to authenticate the identity during communication;
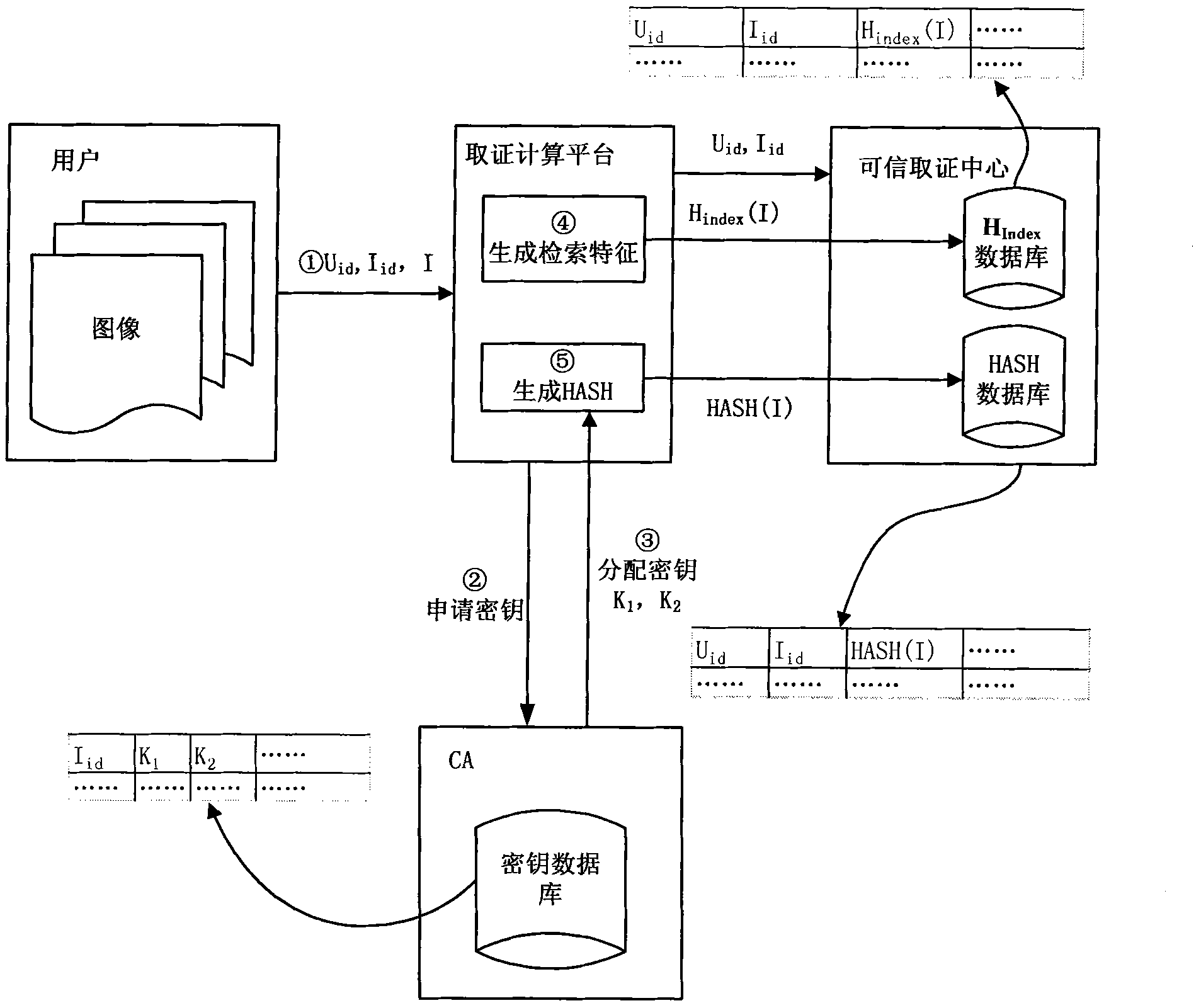
[0073] When the FCP calculates the image hash value, the CA assigns the partition key and the encryption key to the FCP, see Figure 4 , used to calculate the hash value;
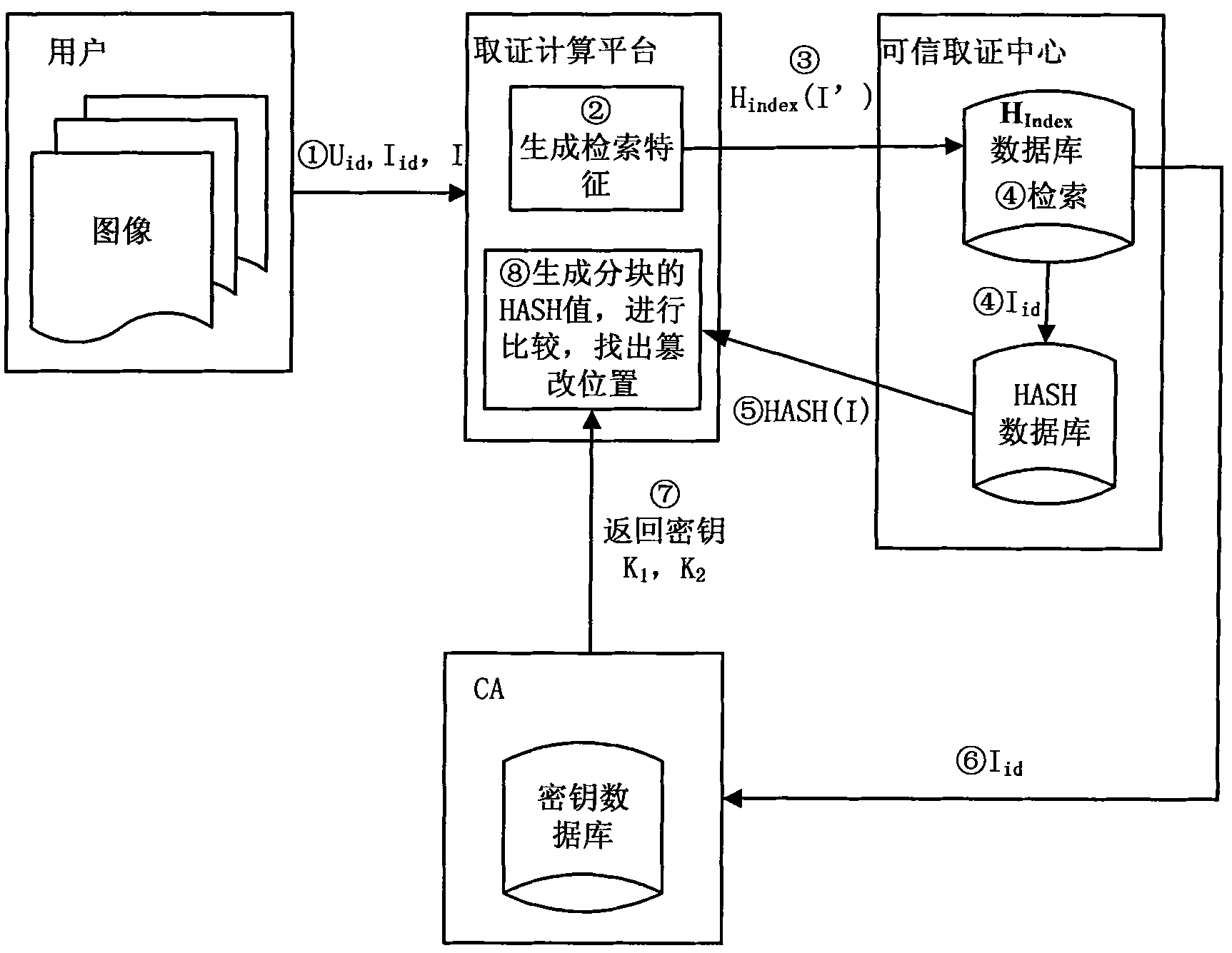
[0074] When performing image authentication, FC sends the image ID to CA, and CA sends the regional key and encryption key to FCP for comparison calculation according to the received image ID;
[0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com