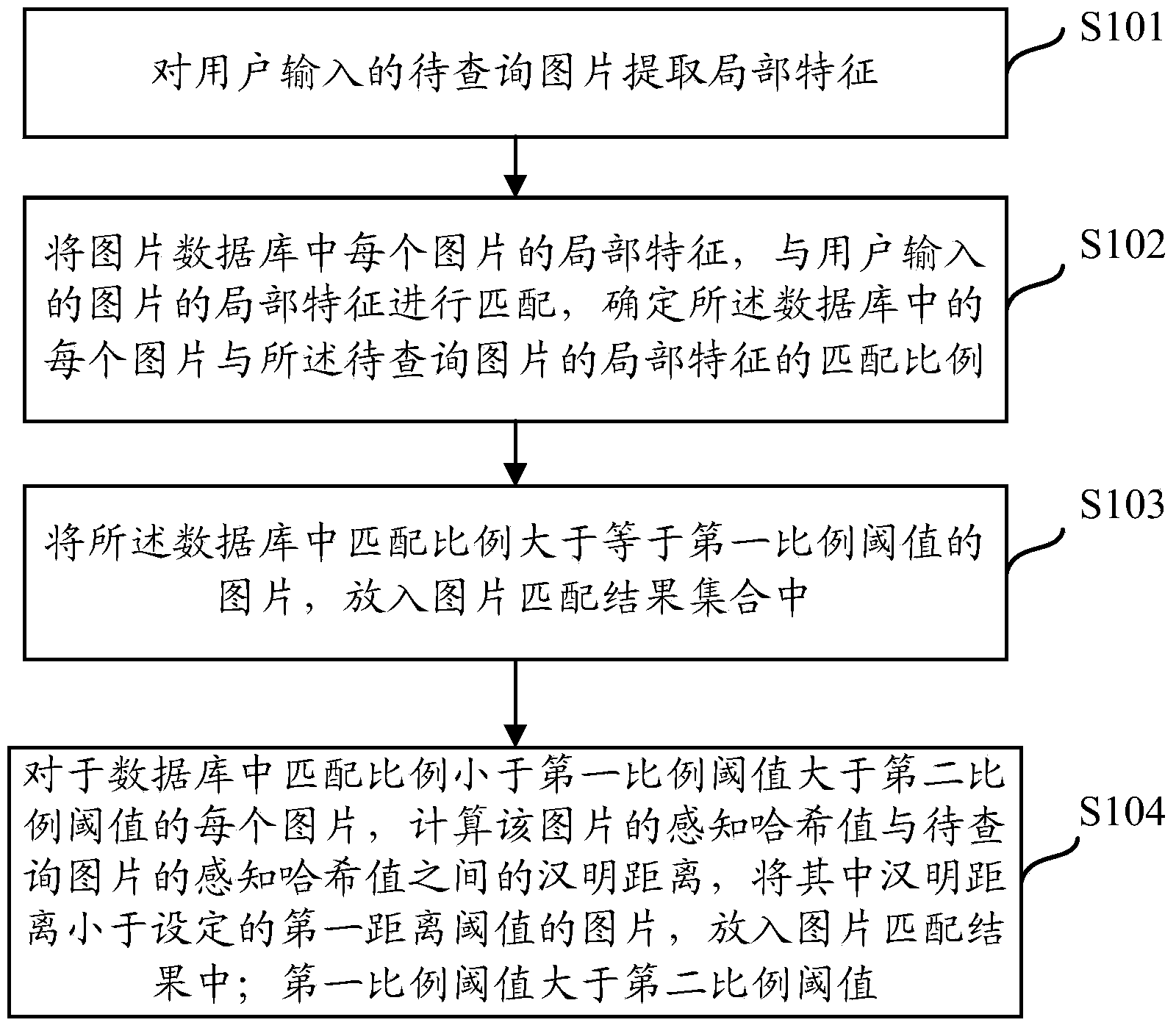
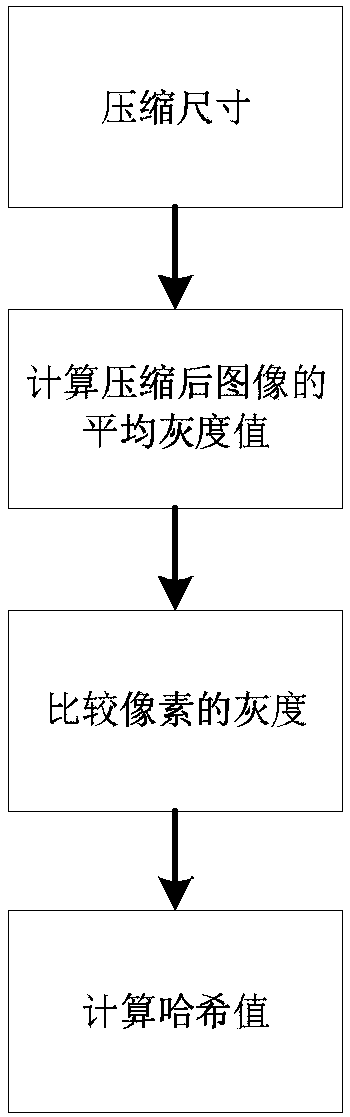
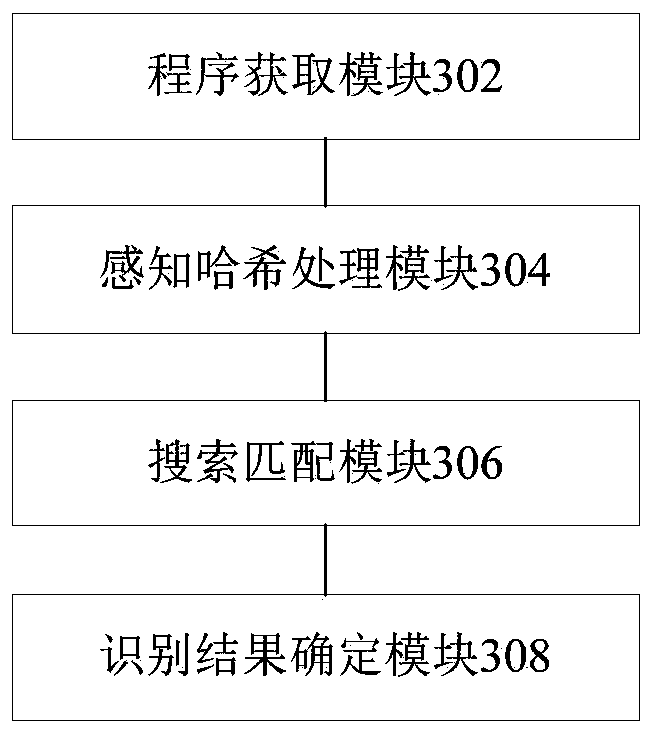
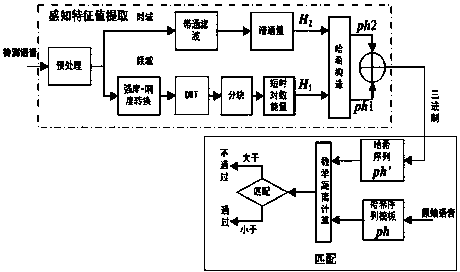
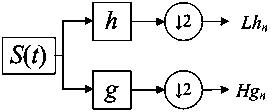
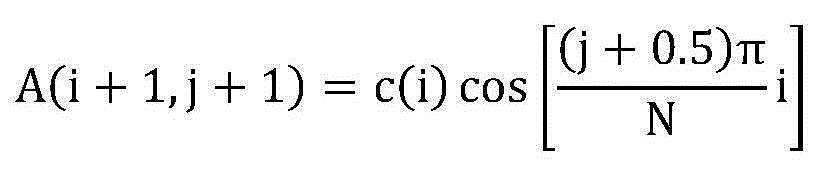Patents
Literature
147 results about "Perceptual hashing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
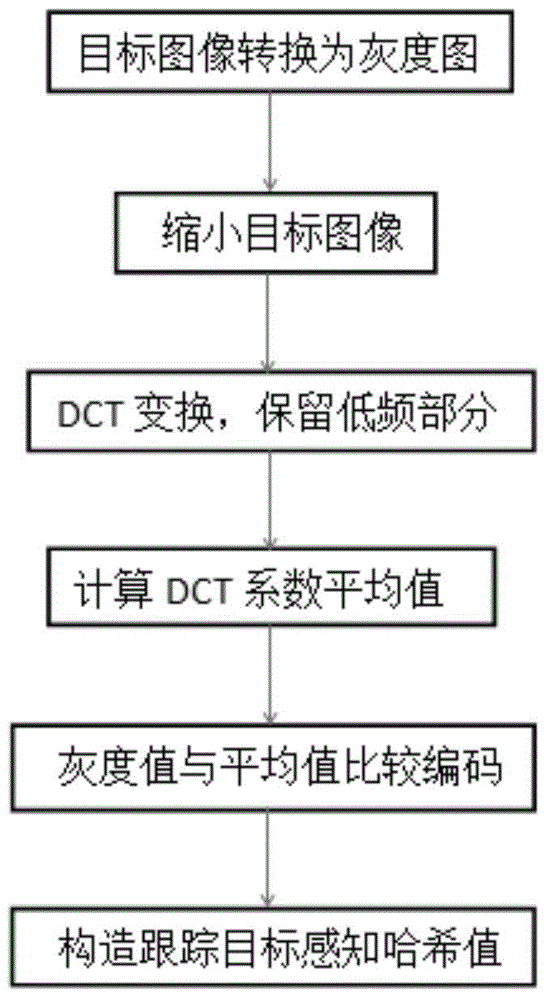
Perceptual hashing is the use of an algorithm that produces a snippet or fingerprint of various forms of multimedia. Perceptual hash functions are analogous if features are similar, whereas cryptographic hashing relies on the avalanche effect of a small change in input value creating a drastic change in output value. Perceptual hash functions are widely used in finding cases of online copyright infringement as well as in digital forensics because of the ability to have a correlation between hashes so similar data can be found (for instance with a differing watermark). For example, Wikipedia could maintain a database of text hashes of popular online books or articles for which the authors hold copyrights to, anytime a Wikipedia user uploads an online book or article that has a copyright, the hashes will be almost exactly the same and could be flagged as plagiarism. This same flagging system can be used for any multimedia or text file. Based on research at Northumbria University, it can also be applied to simultaneously identify similar contents for video copy detection and detect malicious manipulations for video authentication. The system proposed performs better than current video hashing techniques in terms of both identification and authentication.
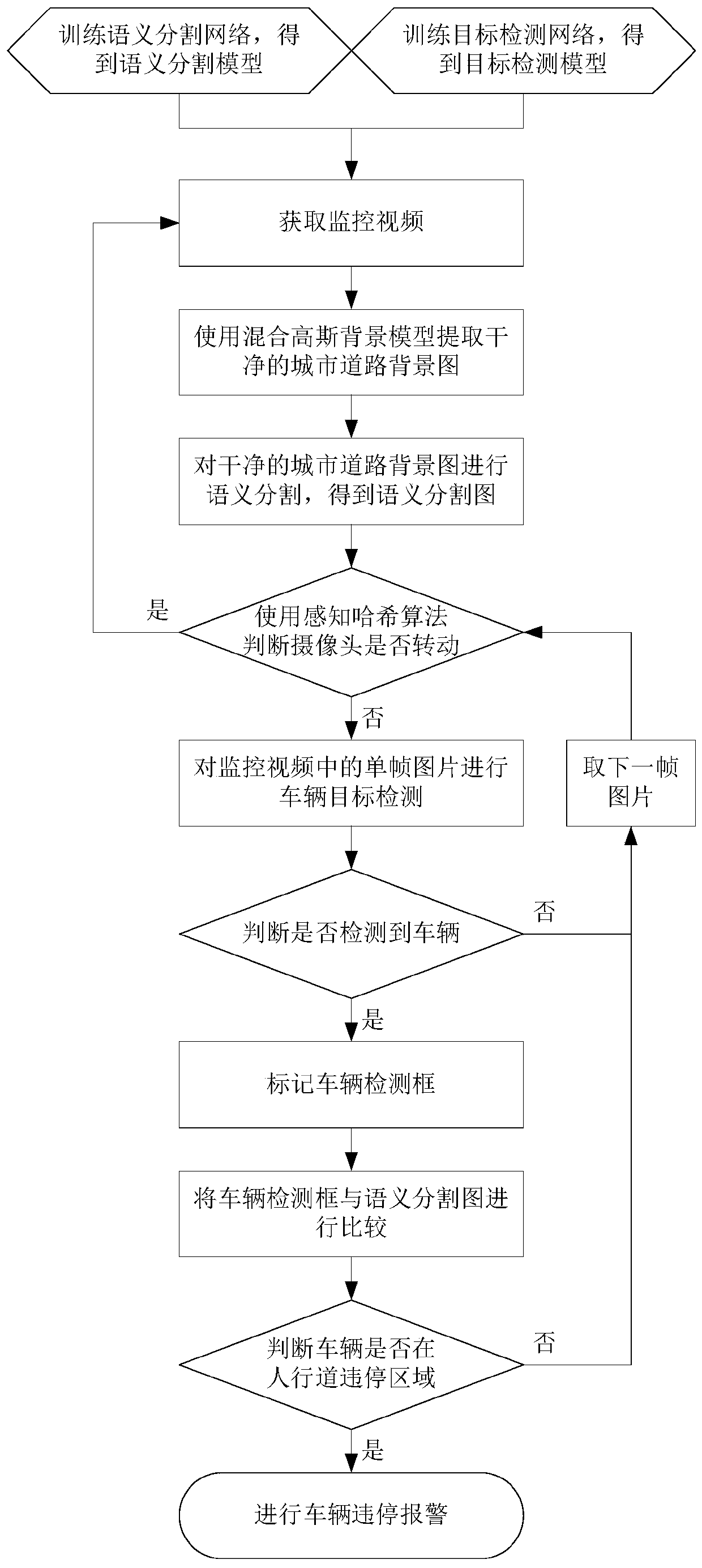
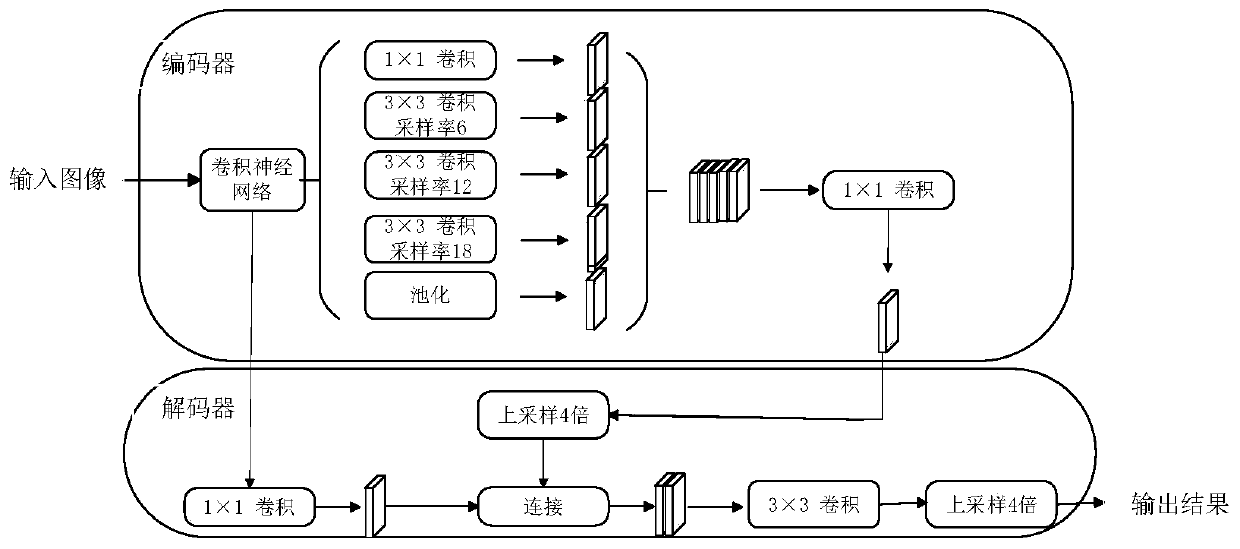
Sidewalk vehicle illegal parking detection method based on target detection and semantic segmentation
ActiveCN111368687AAccurately identify illegal parking and call the policeReduce human errorCharacter and pattern recognitionNeural architecturesPattern recognitionParking area
The invention discloses a sidewalk vehicle illegal parking detection method based on target detection and semantic segmentation, and belongs to the field of deep learning and computer vision, and themethod comprises the steps: respectively training a semantic segmentation network and a target detection network at a training stage, and obtaining a semantic segmentation model and a target detectionmodel; the method comprises the following steps of: extracting an urban road background image by using a Gaussian mixture background model; the method comprises the following steps: acquiring a semantic segmentation model, performing semantic segmentation by using a semantic segmentation algorithm and the semantic segmentation model to obtain a semantic segmentation graph, judging whether a camera rotates or not by using a perceptual hash algorithm, performing vehicle detection by using a target detection algorithm and the target detection model, marking a vehicle detection frame, and finallycomparing the vehicle detection frame with the semantic segmentation graph. The problems that an existing vehicle illegal parking detection method is high in misjudgment rate and poor in real-time performance, a sidewalk illegal parking area needs to be manually calibrated, and when a camera rotates, the illegal parking area needs to be manually calibrated again, so that the camera is not suitable for rotating are solved.
Owner:成都市微泊科技有限公司 +1
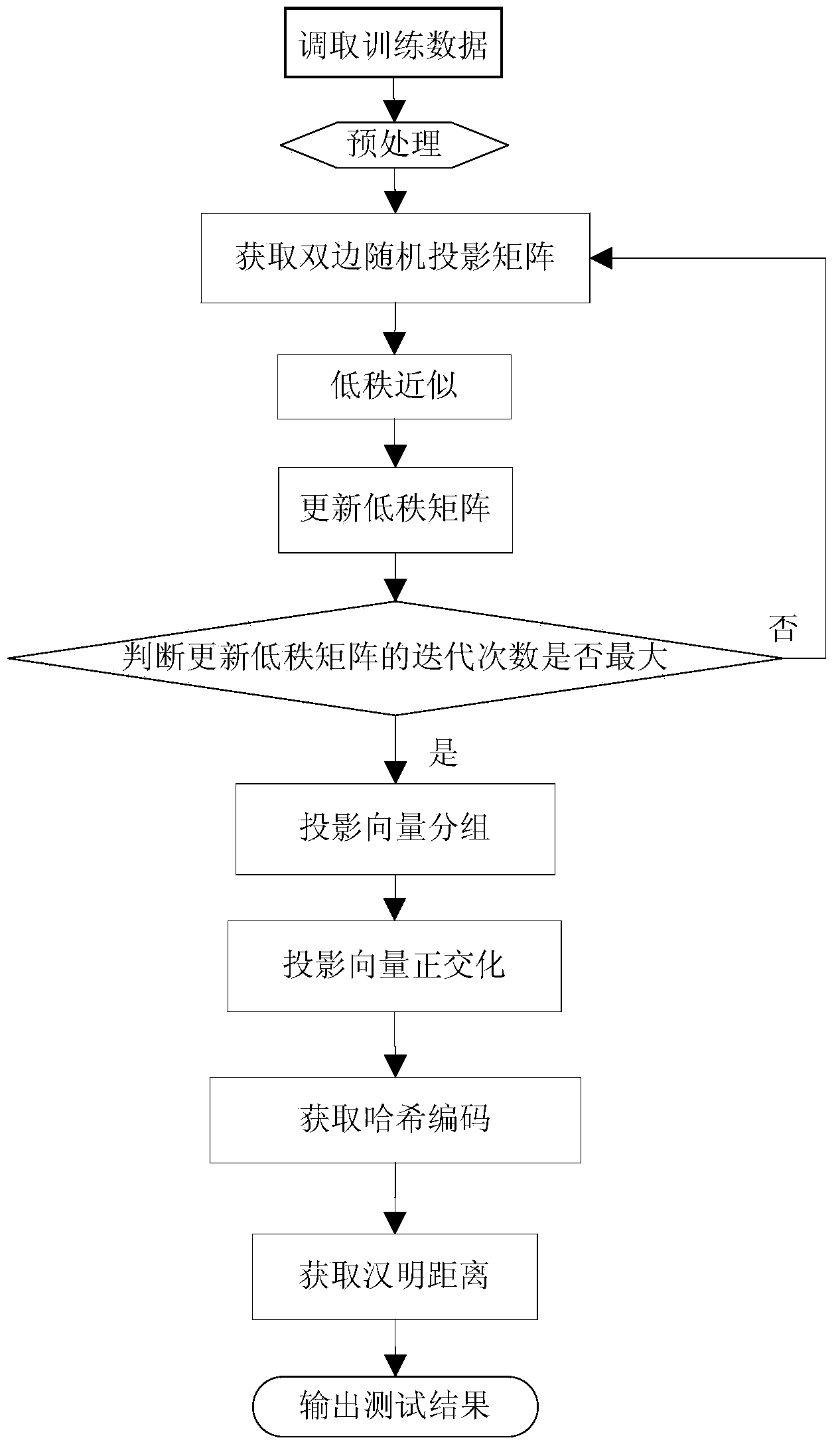
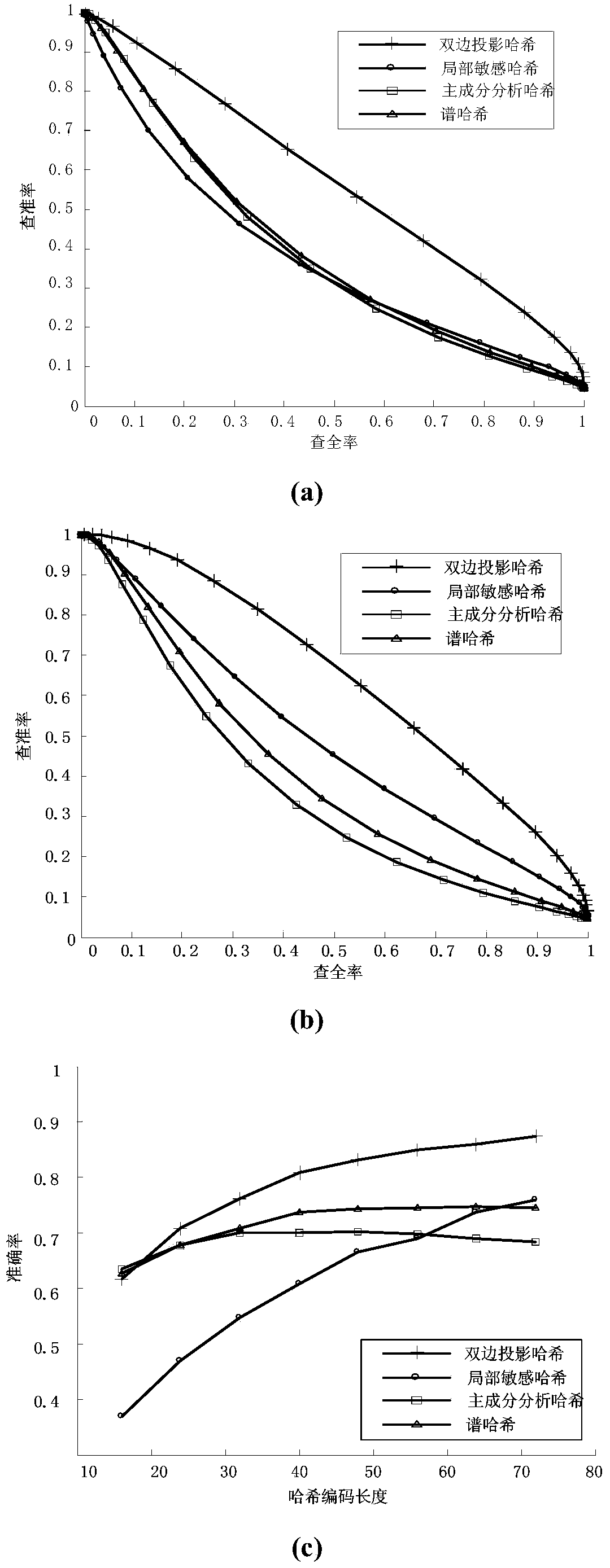
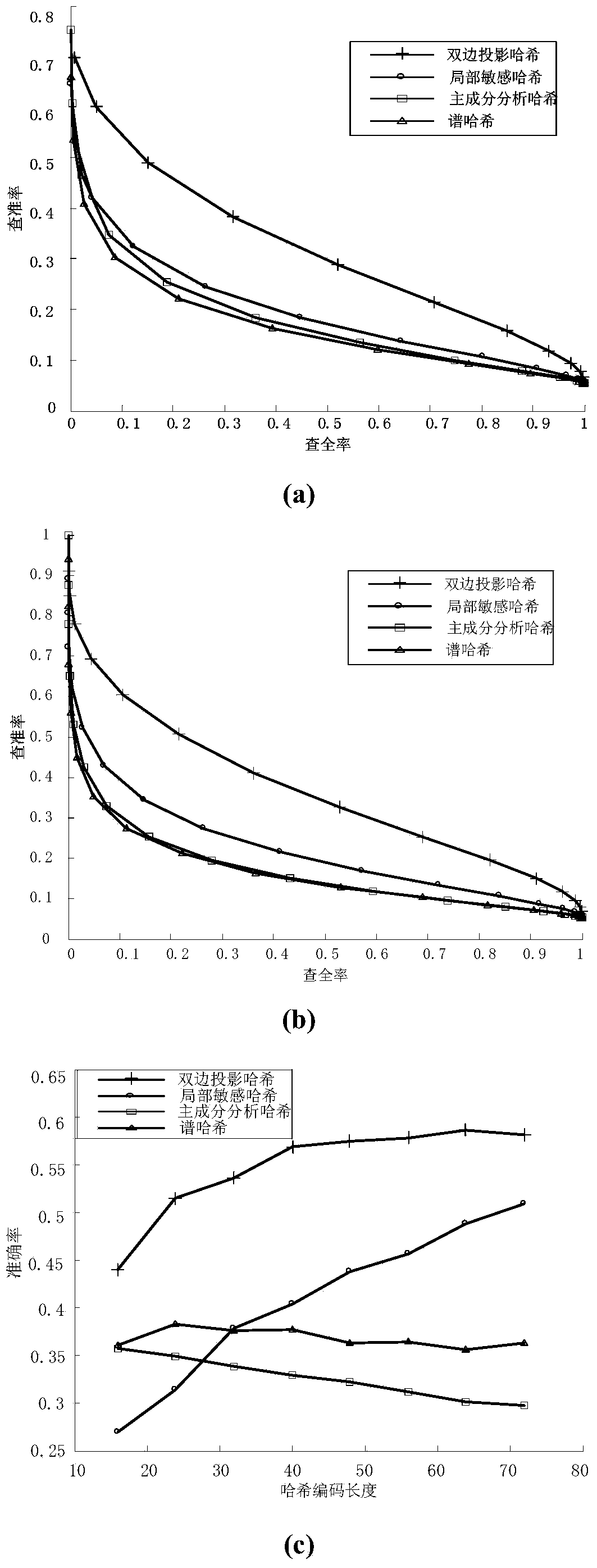
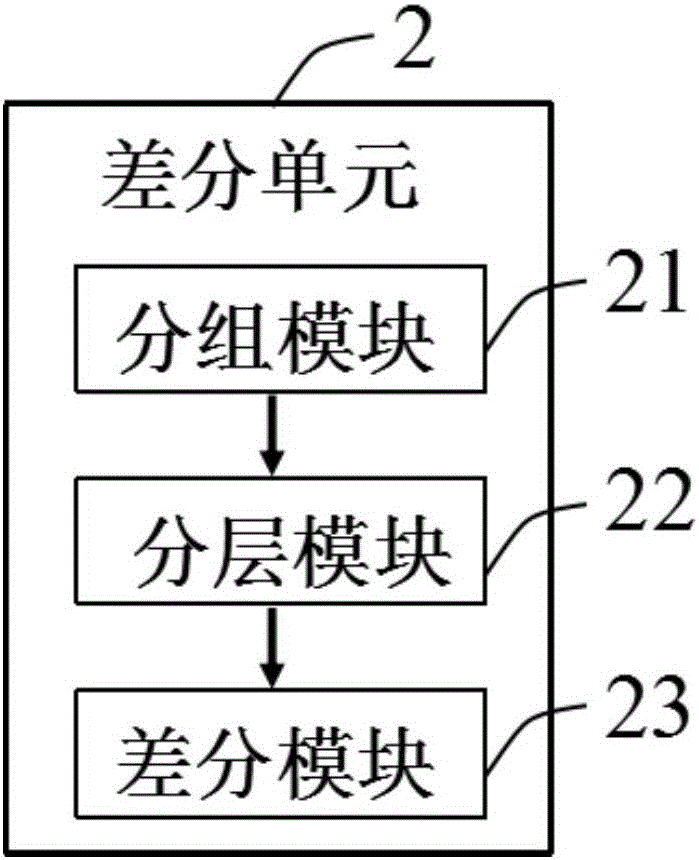
Image perceptual hashing method based on two-sided random projection
InactiveCN103412960AOvercome the disadvantage of instabilityThe optimal projection vector has high stabilitySpecial data processing applicationsTerminal equipmentImage retrieval
The invention discloses an image perceptual hashing method based on two-sided random projection, which mainly solves the problem of quick searching of massive image data. The method comprises the following steps of (1) preprocessing original image data; (2) obtaining a two-sided random projection matrix; (3) carrying out low-rank approximating; (4) updating a low-rank matrix; (5) judging if the number of iteration times of the updated low-rank matrix is maximum or not; (6) grouping projection vectors; (7) orthogonalizing the projection vectors; (8) obtaining hashing codes; (9) obtaining a hamming distance; and (10) outputting test results. The hashing method has the advantages that the better projection vector can be obtained, the effective hashing codes can be obtained, the memory consumption is reduced, the searching time is saved, the comprehensive performance of precision ratio and recall ratio of image searching can be improved, and the hashing method is applied to the image searching services of electronic businesses and mobile terminal equipment.
Owner:XIDIAN UNIV
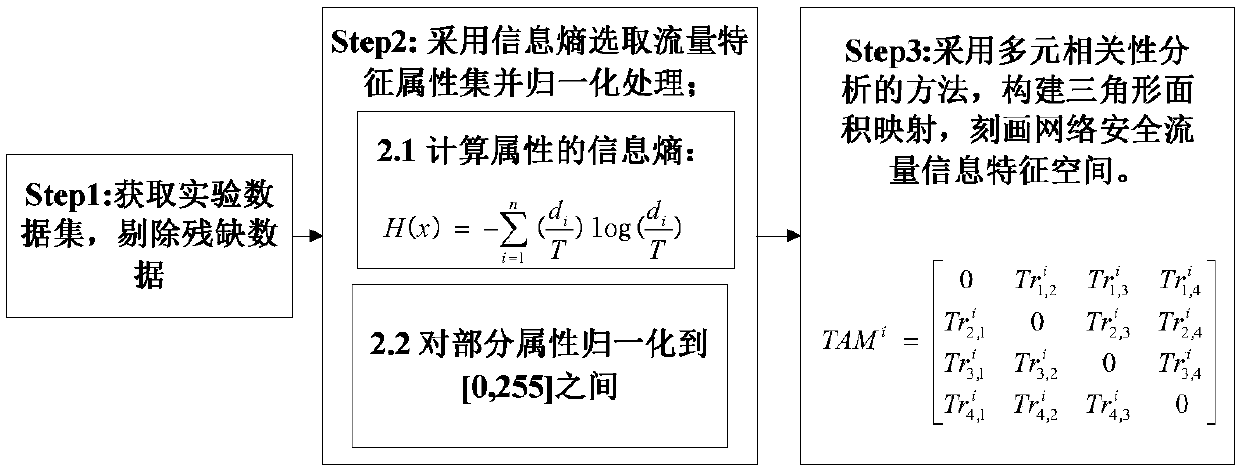
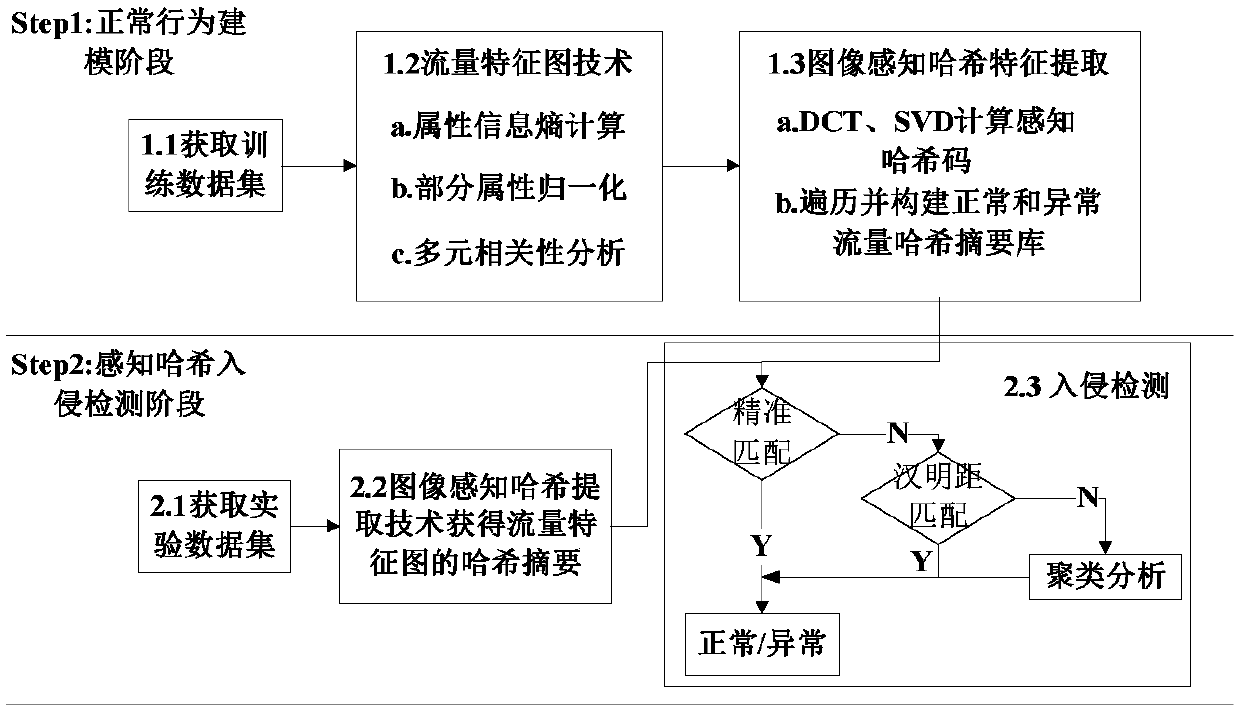
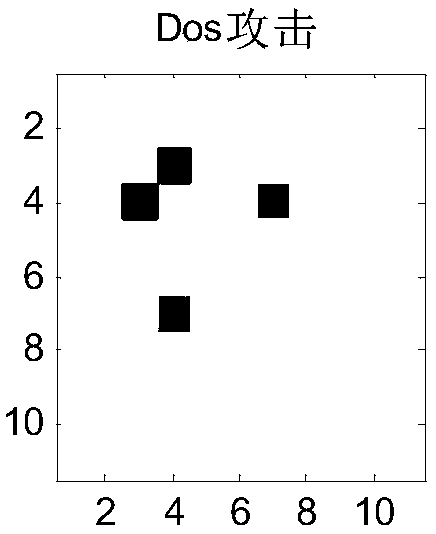
Industrial Internet intrusion detection method based on flow feature map and perception hash
InactiveCN107070943AMeet the robustnessGood intrusion detection performanceData switching networksSingular value decompositionData set
The invention provides an industrial Internet intrusion detection method based on a flow feature map and perception hash for mainly solving the problems of low detection performance and poor adaptability of the existing industrial Internet intrusion detection method. The industrial Internet intrusion detection method draws lessons from an image processing method and comprises the following steps: firstly obtaining a standard test bed experimental data set, performing feature selection by using an information entropy method to construct a flow feature vector, and performing a normalization operation on a part of attributes; then, converting the flow feature vector into a triangle area mapping matrix by using a multivariate correlation analysis method to construct the flow feature map; and finally, obtaining a hash abstract of the flow feature map by using an image perception hash algorithm based on discrete cosine transform SVD and singular value decomposition SVD, and generating an intrusion detection rule set in the form of a binary character string. Moreover, hash matching is performed by using an accurate matching method based on character strings, a similarity measurement method based on a normalized Hamming distance and a clustering analysis method based on a Euclidean distance so as to detect abnormal flow and malicious intrusion in the industrial Internet.
Owner:LANZHOU UNIVERSITY OF TECHNOLOGY
Method for searching matched pictures and method and device for searching pictures
InactiveCN104036009ACharacter and pattern recognitionSpecial data processing applicationsImage retrievalHamming distance
Owner:BEIJING QIHOO TECH CO LTD +1
Particle filter and perceptual hash-based video target tracking method
ActiveCN105139420AThe description is validImprove robustnessImage enhancementImage analysisPattern recognitionVideo sequence
The invention discloses a particle filter and perceptual hash-based video target tracking method which comprises the following steps: 1) selecting a target to be tracked from an original image as a target area, extracting a perceptual hash characteristic of the target area as a template feature, and initialization positioning a weight particle set; 2) performing a state coordinate prediction for the weight particle set and labeling the prediction area; 3) extracting the perceptual hash characteristic for each predicting particle area, and calculating a similarity degree of the predicting particle area and the target area; 4) according a position contribution of a distance from the target and a similarity degree refreshing particle weight of the perceptual hash characteristic, adopting a minimum variance to estimate and obtain a new target area; and and 5) according the size of the weight and a resample estimation value, obtaining the weight particle set of a next frame, and repeating from the step 2 to the step 4 till an end of all video sequences. The particle filter and perceptual hash-based video target tracking method disclosed by the invention is high in efficiency, and can realize fast and effective tracking on the premise of great illumination variance and change of the target scale.
Owner:SHANDONG UNIV
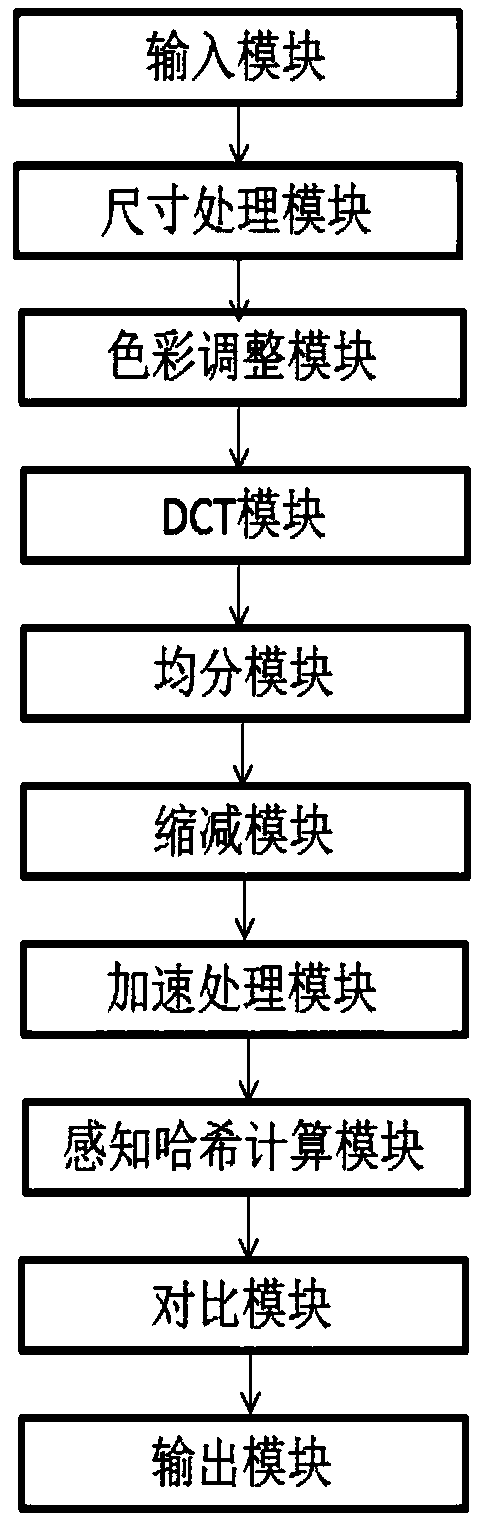
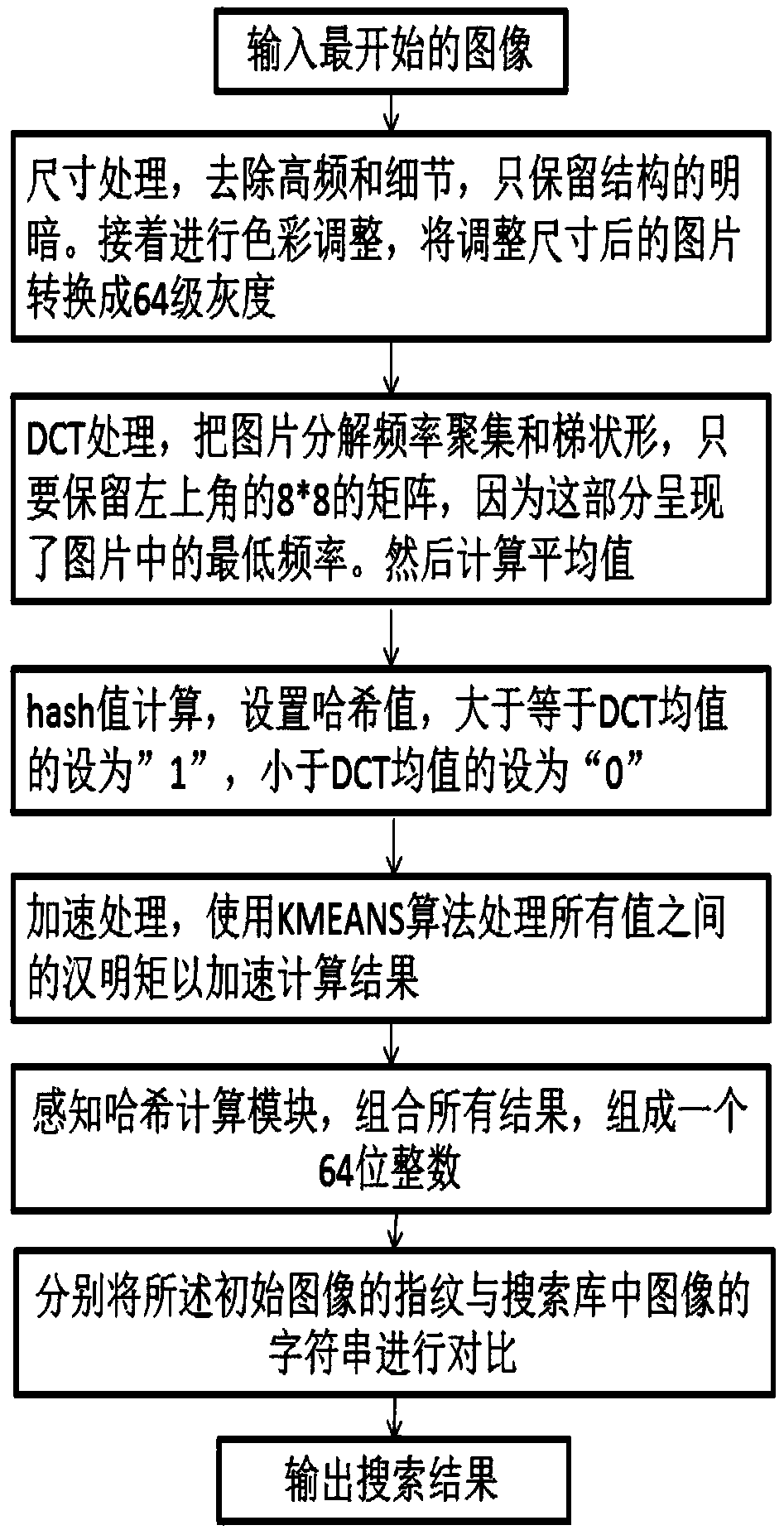
Fast image recognition system and method based on perceptual hashing
PendingCN108897775ACharacter and pattern recognitionSpecial data processing applicationsEqualizationEfficient algorithm
The invention relates to a fast image recognition system and method based on perceptual hashing, and belongs to the technical field of image recognition. The fast image recognition system comprises aninput module, a size processing module, a color adjustment module, a DCT module, an equalization module, a reduction module, an acceleration processing module, a perceptual hashing calculation module, a comparison module and an output module. The advantages and the significance of the invention are that after the initial image inputted, the KMEANS algorithm is applied to perform acceleration calculation of the Hamming moment, then processing is performed by using the perceptual hashing algorithm and then comparison with all the image databases is performed so that the problems of time consumption and labor consumption and low efficiency of calculation of the single perceptual hashing algorithm can be solved and a new and more efficient algorithm for similarity search between images can beprovided.
Owner:KUNMING UNIV OF SCI & TECH
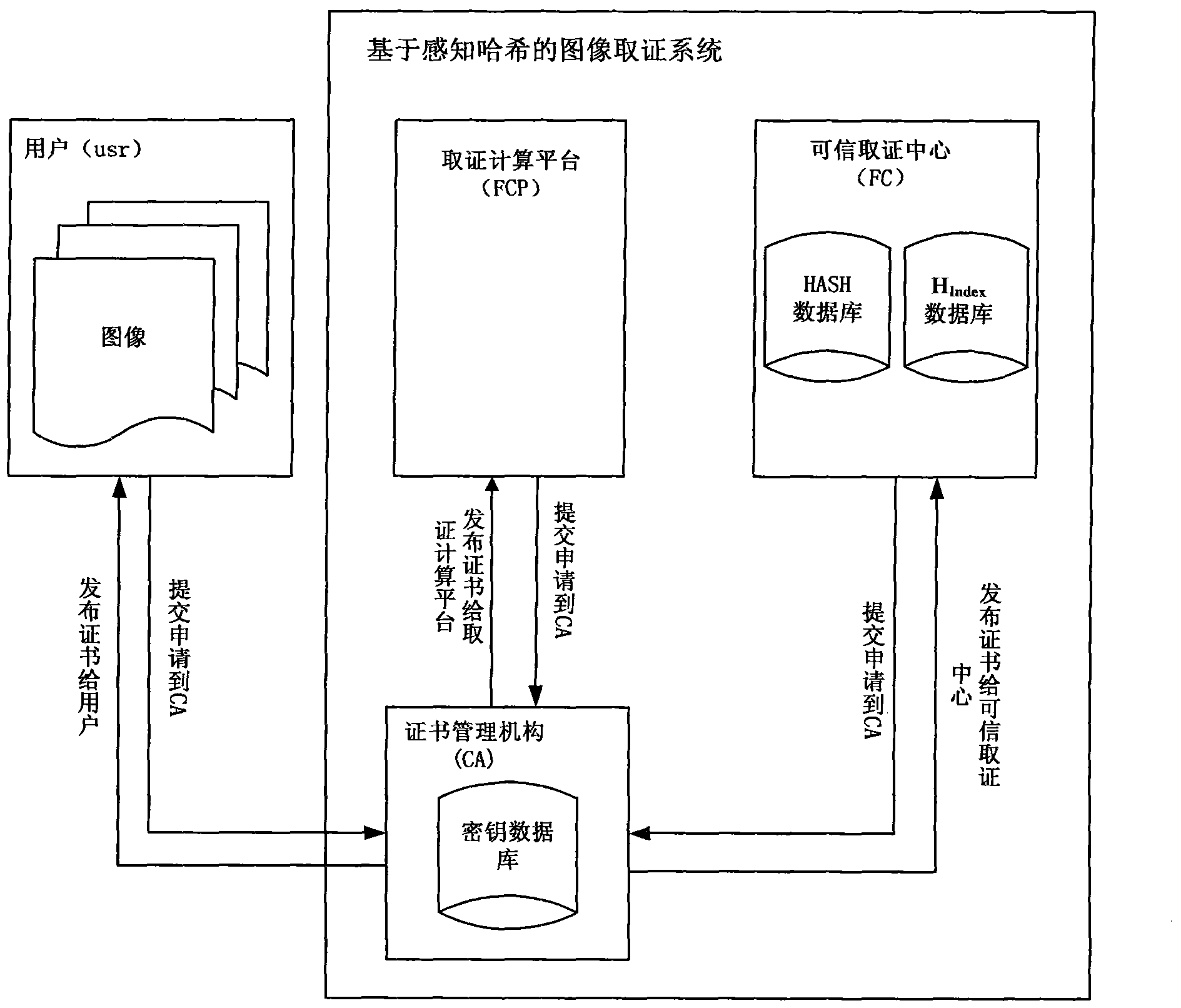
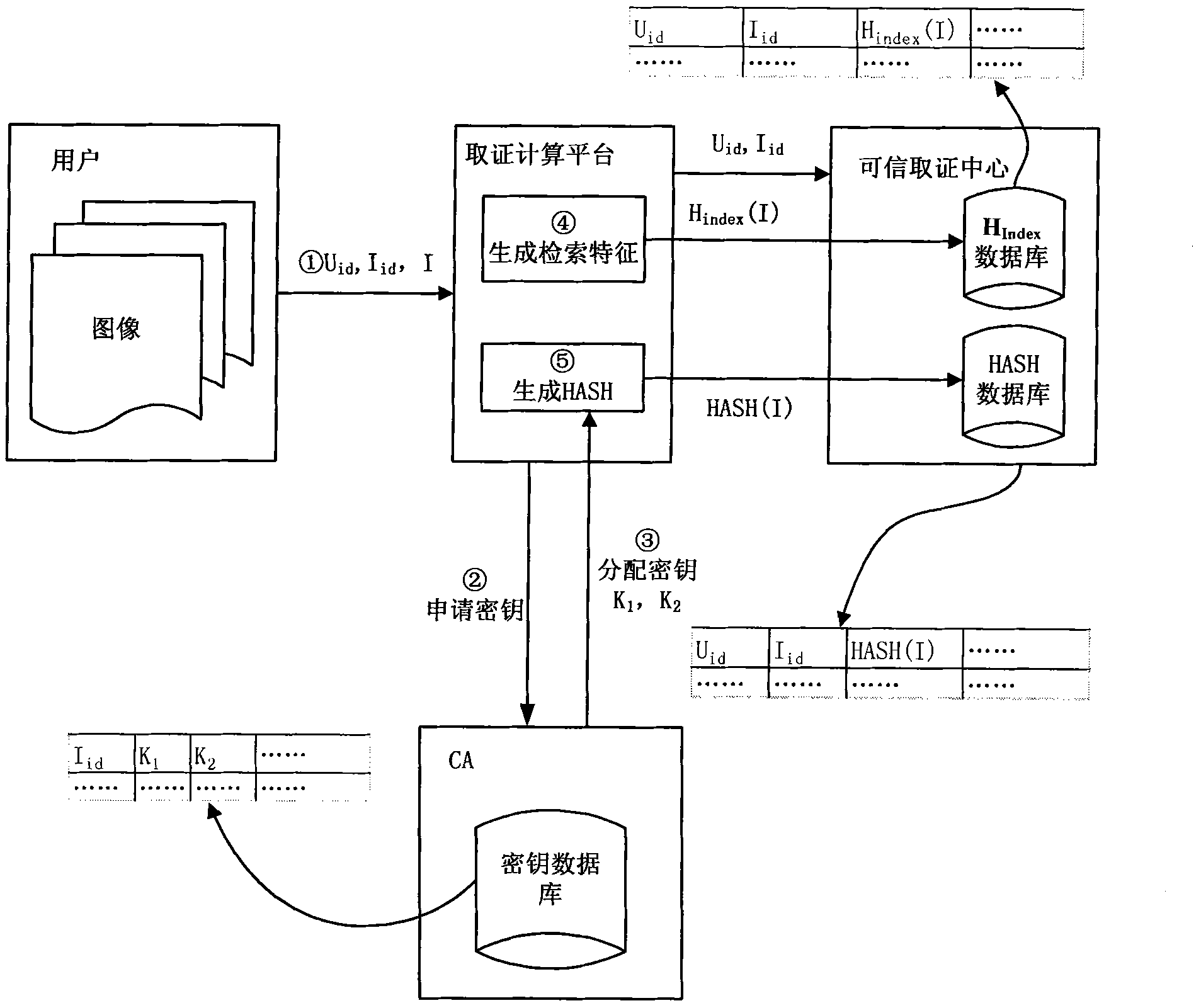
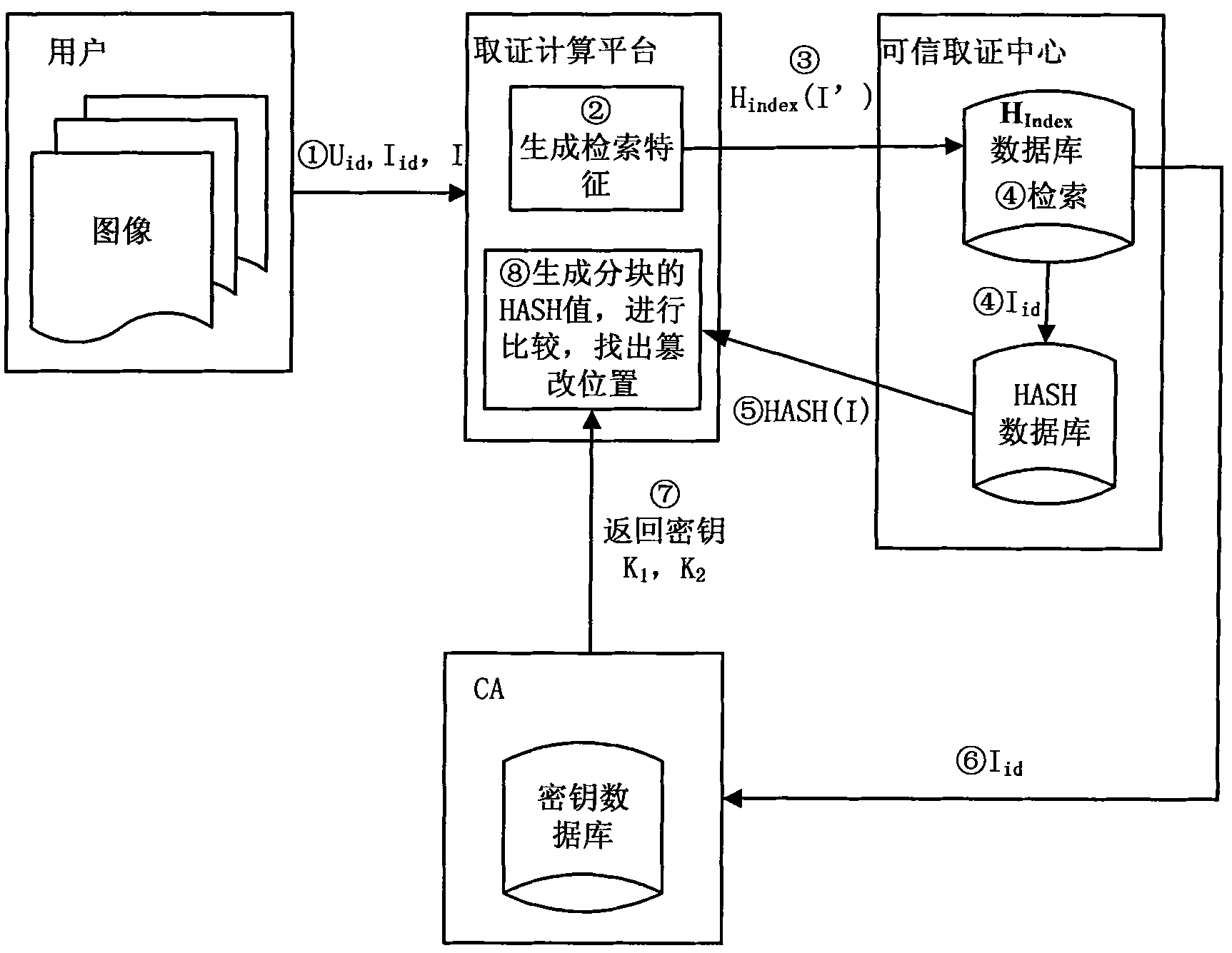
Perceptual hashing-based practical and safe image forensic system and forensic method
ActiveCN101964041AReliable evidence collectionPrecise positioningDigital data authenticationImage data processing detailsUser needsImage retrieval
The invention discloses a perceptual hashing-based practical and safe image forensic system and a perceptual hashing-based practical and safe image forensic method. The system comprises a certificate authority (CA), forensics computing platform (FCP) and a forensic center (FC). The method comprises the following steps that: the CA provides a certificate for a user, the FCP and the FC and distributes and manages a control key of a hash function for the FCP and the FC; the FCP calculates a characteristic value and generates a hash value of an image at a registration or forensics stage; the FC manages an image hash value from the FCP and provides retrieval and forensics services; the user submits the image to the FCP, extracts an image retrieval characteristic by using the FCP, calculates the hash value of an image segment by using a key distributed by the CA and submits the hash value to an FC database; and when the user needs an authentication image, the image is also submitted to the FCP, the retrieval characteristic is extracted to retrieve the most coincident original image from the FC, the image is segmented and the hash value is calculated by using the same key and the difference between the image and the hash value is compared so as to determine a position on which content tampering occurs. The system achieves high balanced performance in the aspects of safety, robustness, sensibility, rapid retrieval and the like.
Owner:ANHUI TELECOMM ENG
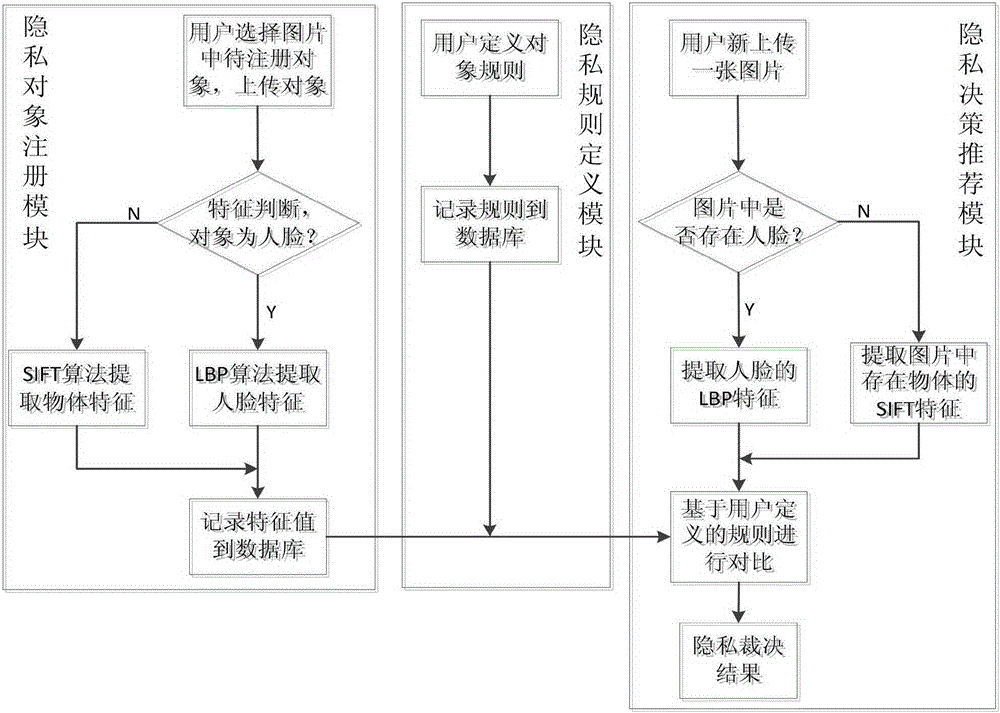
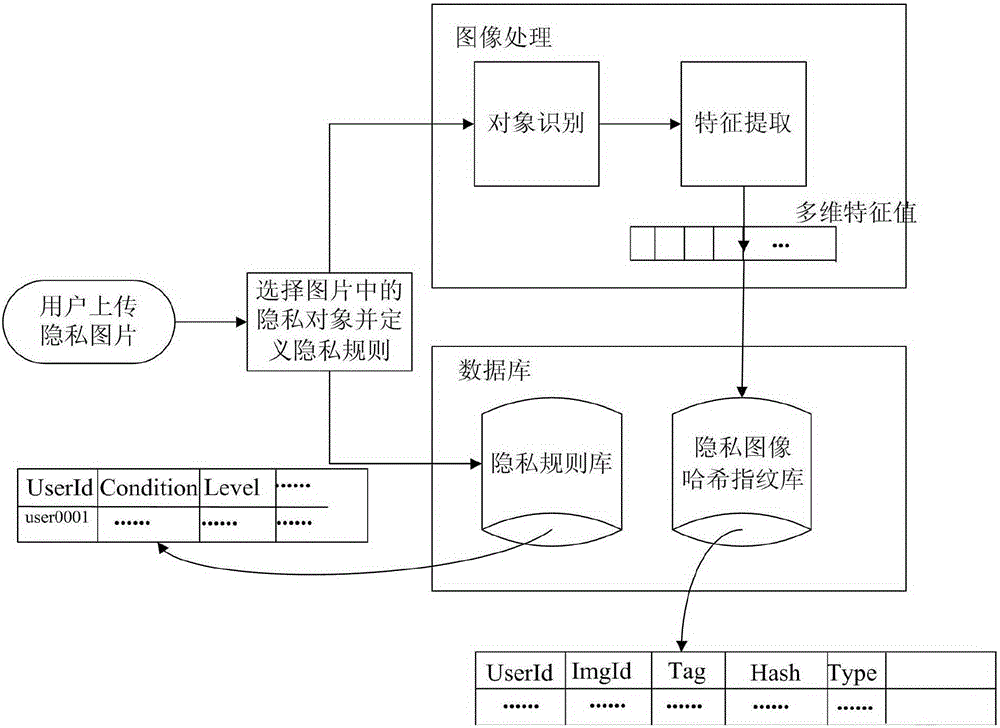
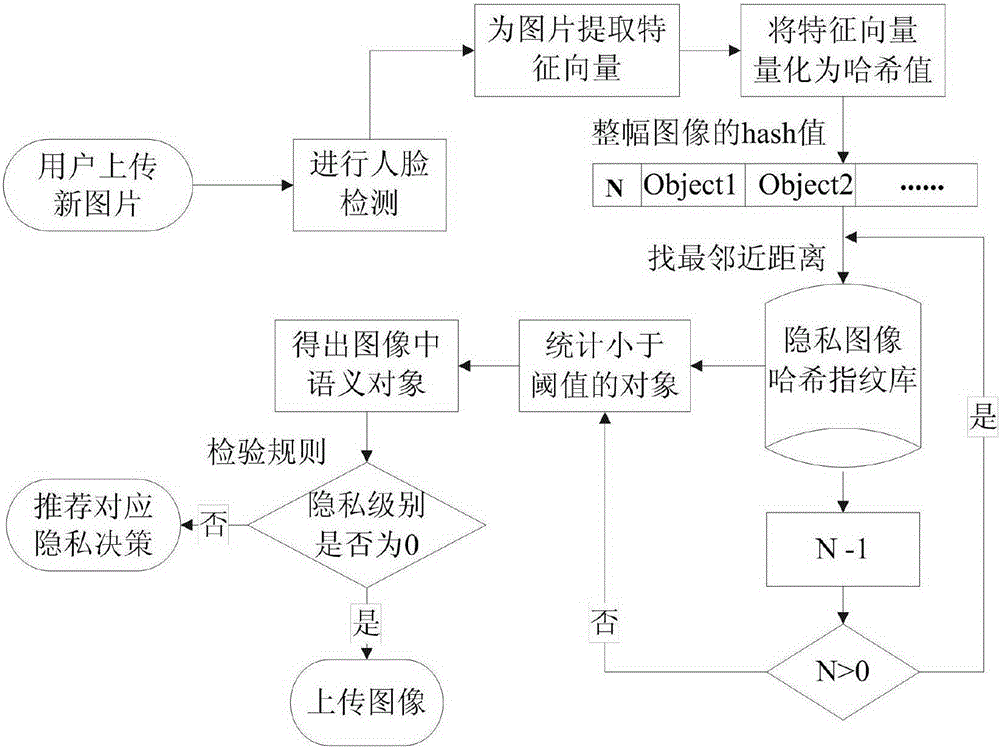
Image privacy decision recommendation system and method under social network on the basis of privacy rule and perceptual Hash
ActiveCN105260676AReduce the risk of privacy breachesSuitable for personalizationData processing applicationsWeb data indexingInternet privacyPrivacy rule
The invention discloses an image privacy decision recommendation system and method under a social network on the basis of a privacy rule and perceptual Hash. The invention is characterized in that the system comprises a privacy object registration module, a privacy rule definition module and a privacy decision recommendation module, wherein the privacy object registration module provides a registration function of an object to be protected for a user; the privacy rule definition module defines a privacy security level for a to-be-protected objet of the user; and the privacy decision recommendation module identifies a to-be-uploaded object of the user, compares the to-be-uploaded object of the user with a protected object in a Hash fingerprint database and a privacy rule in a privacy rule base, and finally submits the privacy security level of the to-be-uploaded object to the privacy decision recommendation module of the user. The quick and convenient automatic calculation of the privacy level and decision recommendation can be realized, and the leakage risks of individuals and the families of the individual can be effectively lowered so as to greatly improve the protection safety of user individual image privacy.
Owner:HEFEI UNIV OF TECH
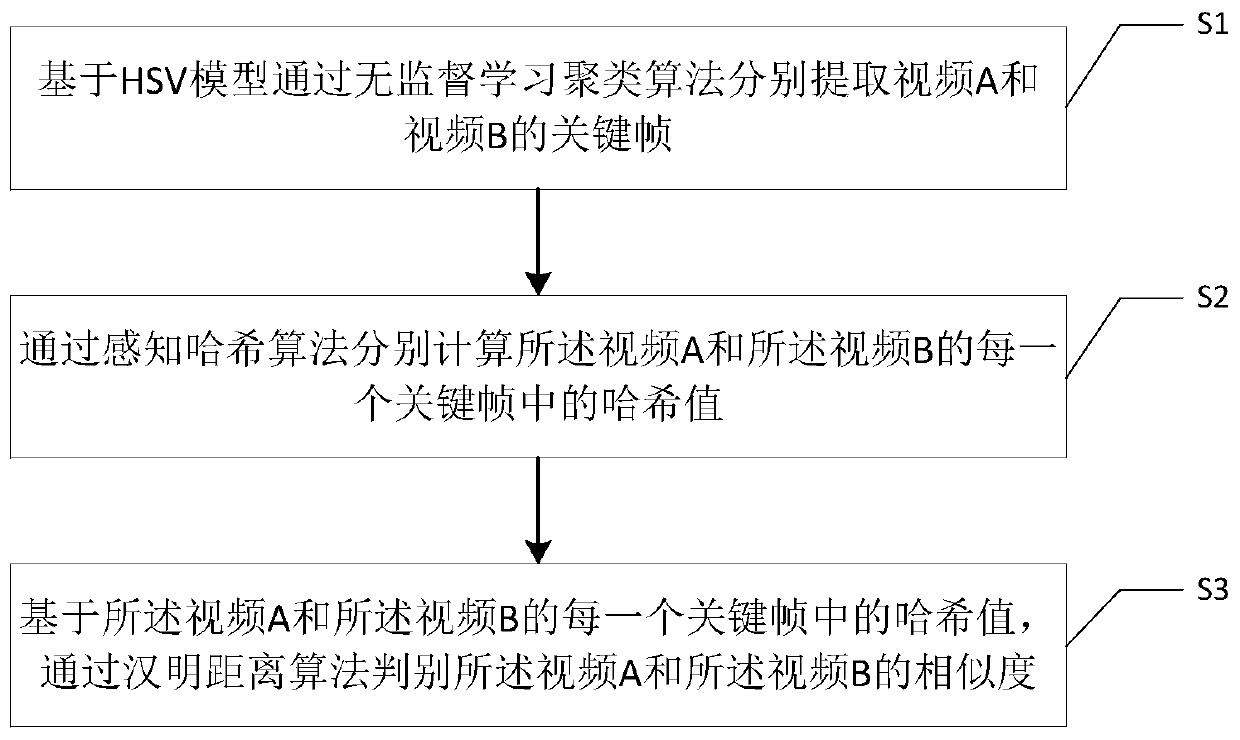
Video content similarity discrimination method and system based on computer vision
InactiveCN110427895ATo achieve the purpose of determining copyright infringementPoor resolutionVideo data indexingCharacter and pattern recognitionCluster algorithmCopyright infringement
The embodiment of the invention discloses a video content similarity discrimination method and a system based on computer vision, and relates to the technical field of video image processing, and themethod comprises the following steps: respectively extracting key frames of a video A and a video B through an unsupervised learning clustering algorithm based on an HSV model; respectively calculating a hash value in each key frame of the video A and the video B through a perceptual hash algorithm; and based on the hash value in each key frame of the video A and the video B, judging the similarity of the video A and the video B through a Hamming distance algorithm. According to the method and the system, the problems that the representativeness of key frames is not enough, the accuracy can begreatly reduced under the condition that the content change amplitude between the frames is relatively small, and the effect of the existing picture local feature value processing technology is poorunder the condition of image brightness change are effectively solved; hash value comparison is carried out through the Hamming distance, similarity judgment is carried out on videos of different channels, and therefore the purpose of video copyright infringement judgment is achieved.
Owner:李震
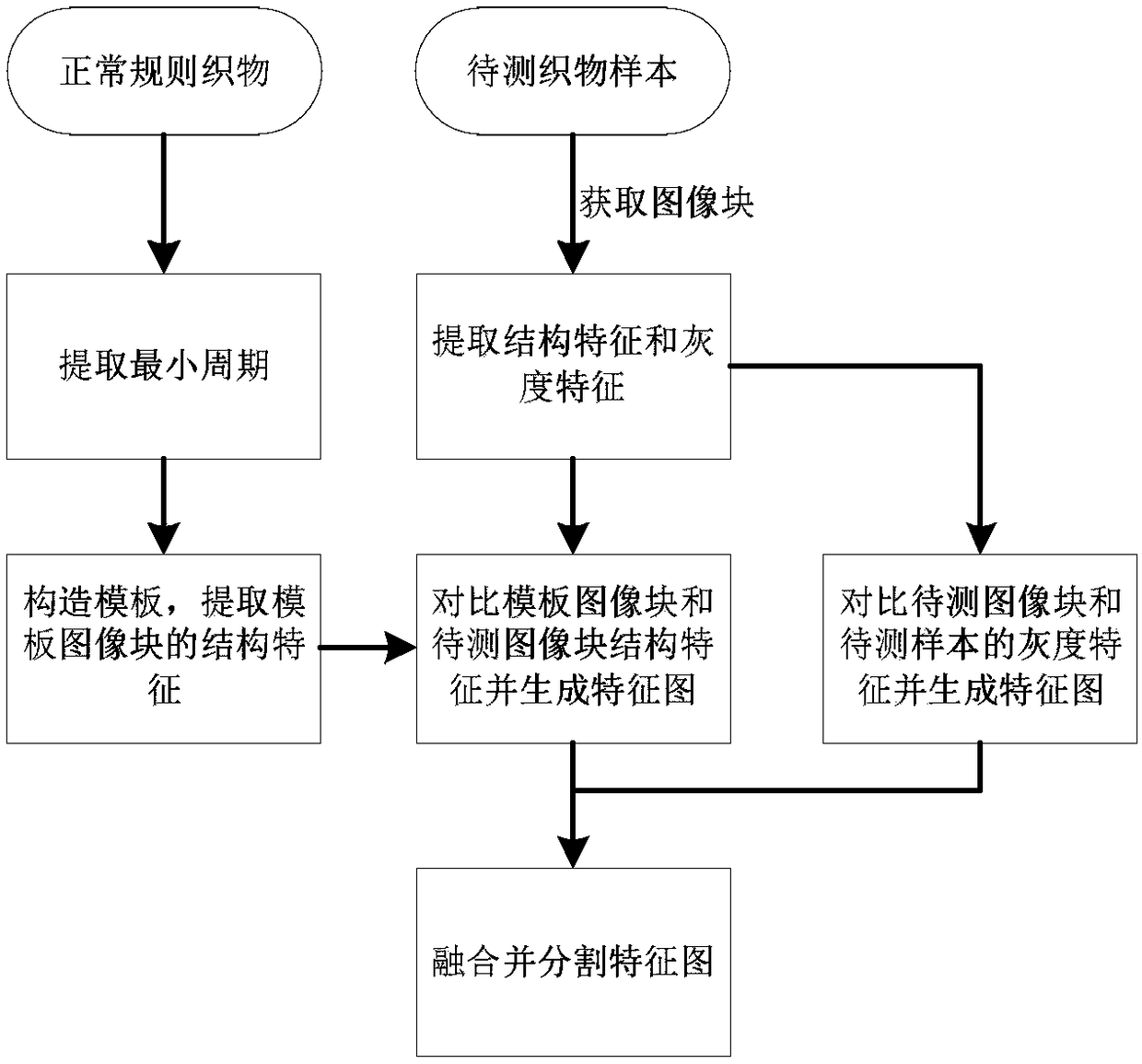
Fabric defect detection method based on distance matching function and perceptual hash algorithm
ActiveCN108090894AEfficient representation of structural featuresStructural feature representationImage enhancementImage analysisPattern recognitionHamming distance
The present invention discloses a fabric defect detection method based on a distance matching function and a perceptual hash algorithm. According to the method, the minimum period of a regular fabricis calculated through using the distance matching function, and the minimum period can be applied to obtaining image blocks; a repeat unit template is constructed, and the structure features of the template image block are extracted through adopting the perceptual hash algorithm; the structural features and grayscale features of image blocks of a sample to be tested are extracted, and are comparedwith the structural features and global gray average value of the template image block, so that a minimum Hamming distance feature image and a gray average value comparison feature image are obtained; and the merging and segmentation of the feature images are performed. The results show that the method of the present invention comprehensively considers the structural features and gray average value feature of the minimum period of the regular fabric, can effectively extract the defect area of the fabric and realize the defect detection of the fabric.
Owner:江苏知聚知识产权服务有限公司
Sensing Hash value extracting method and sensing Hash value authenticating method for voice sensing Hash authentication
Disclosed are a sensing Hash value extracting method and a sensing Hash value authenticating method for voice sensing Hash authentication. According to the characteristics of LPC (linear prediction coefficients), robustness of an LPC method is improved by optimizing the LPC method and performing three steps of optimizing and blocking of the LPC and disintegrating matrix of parameters after blocking, the optimized LPC are high in robustness and calculating efficiency, and robustness of a sensing Hash sequence formed is improved as well. The sensing Hash value calculated by the optimized LPC maintains the advantages of good instantaneity of a simple LPC method while having good robustness for attacks to the voice during transmission.
Owner:LANZHOU UNIVERSITY OF TECHNOLOGY
Intelligent-texture anti-counterfeiting method based on perceptual hashing
InactiveCN103353990ARealize automatic identificationImprove accuracyImage analysisCommerceFeature extractionNormalized correlation coefficient
Owner:HAINAN UNIVERSITY
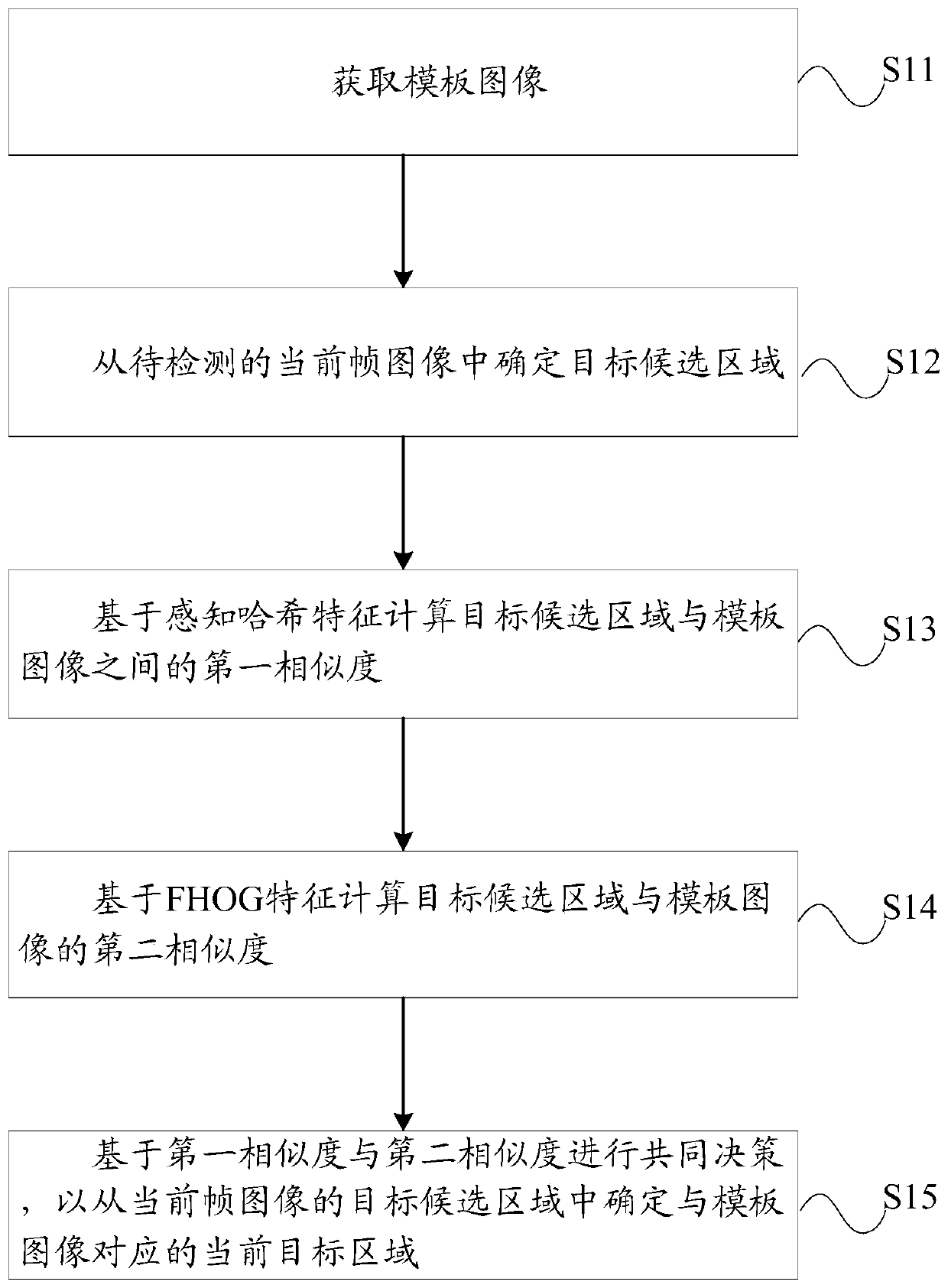
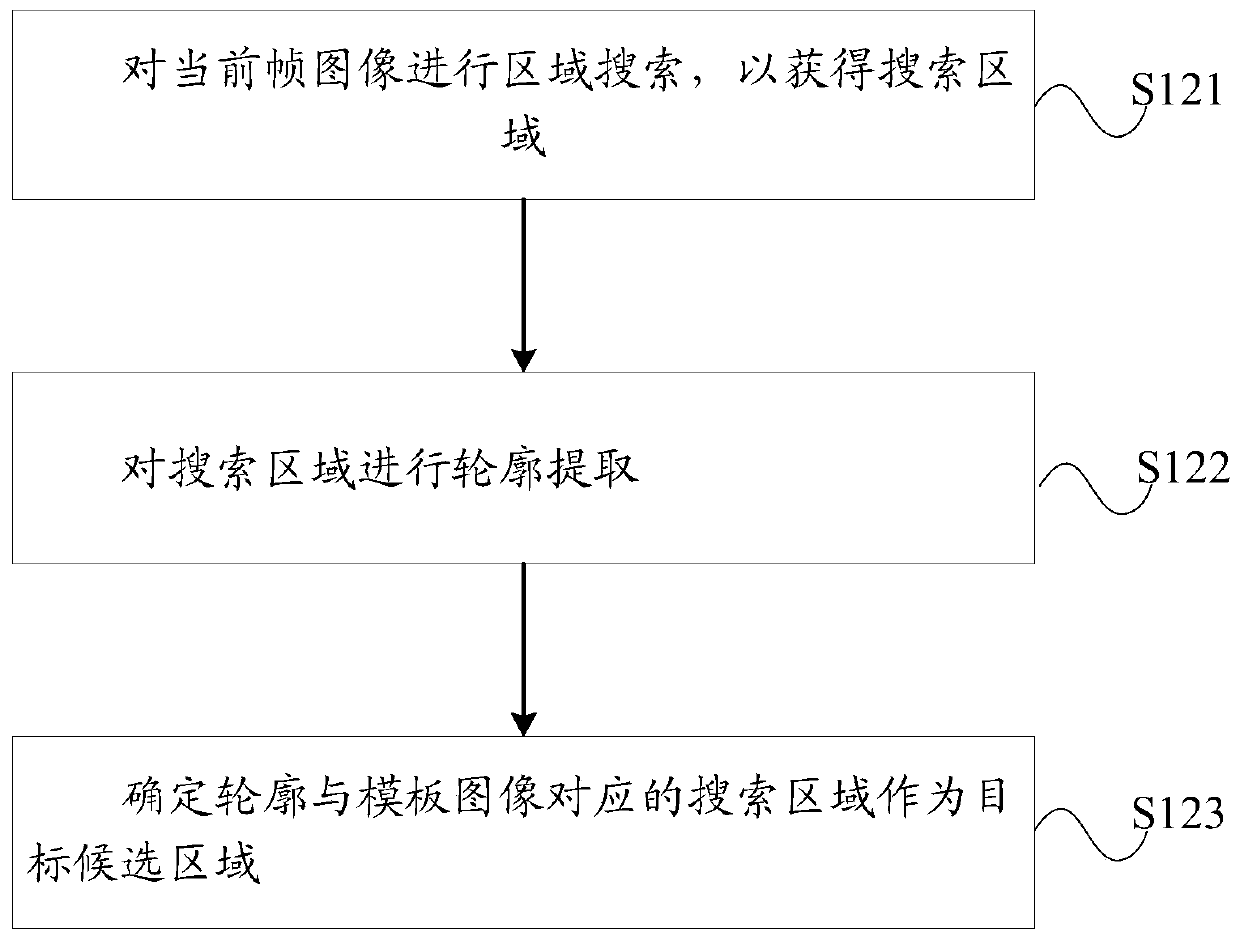
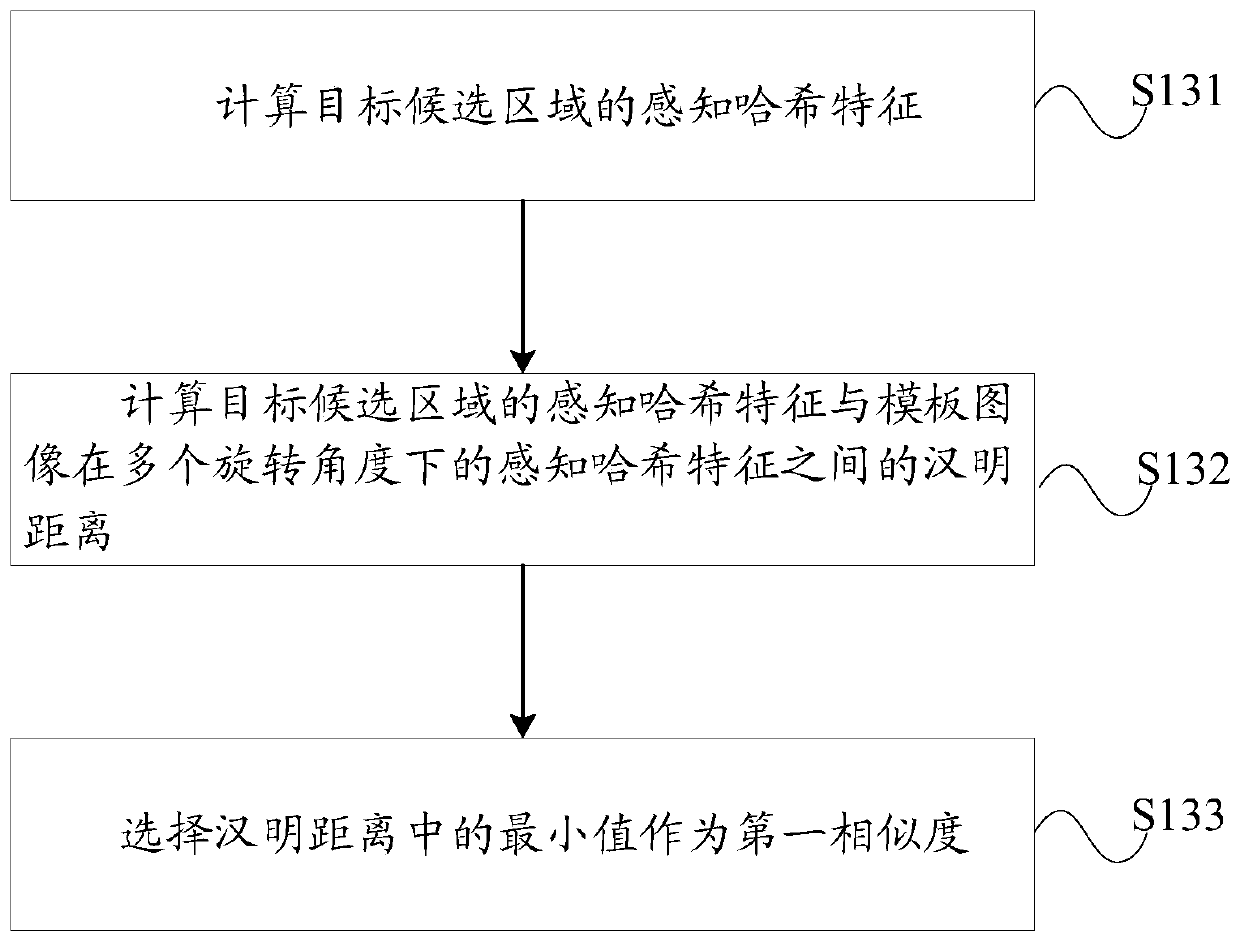
Target detection method and device and computer storage medium
ActiveCN110807473AReduce the impactQuick fixCharacter and pattern recognitionPattern recognitionRadiology
The invention discloses a target detection method and device, and a computer storage medium. The target detection method comprises the steps of obtaining a template image; determining a target candidate region from the current frame image to be detected; calculating a first similarity between the target candidate region and the template image based on the perceptual hash feature; calculating a second similarity between the target candidate region and the template image based on the FHOG features; and making a common decision based on the first similarity and the second similarity so as to determine a current target area corresponding to the template image from the target candidate areas of the current frame image. In this way, the current target area can be accurately determined.
Owner:ZHEJIANG DAHUA TECH CO LTD
Video tamper detection method and device based on time-domain perceptual hashing
InactiveCN103747254ASolve complexitySolve the speed problemDigital video signal modificationTime domainPattern recognition
The invention discloses a video tamper detection method and a video tamper detection device based on time-domain perceptual hashing. The method comprises the steps of performing the same random partitioning on each frame of image in a to-be-detected video; calculating the brightness mean value of each partition by taking each frame as a unit, and counting the brightness mean value change condition of each partition on a time-domain passage for forming a time-domain feature matrix of the to-be-detected video; quantizing the time-domain feature matrix to obtain a corresponding hashing sequence; extracting a hashing sequence corresponding to an original video with the same video length; calculating the time-domain feature distance between the to-be-detected video and the original video according to the hashing sequences of the to-be-detected video and the original video; comparing the time-domain feature distance with a set threshold value, if the time-domain feature distance is smaller than the threshold value, the to-be-detected video is determined to be not tampered, and otherwise, the to-be-detected video is determined to be tampered. The video tamper detection speed and accuracy are greatly improved.
Owner:SHENZHEN UNIV
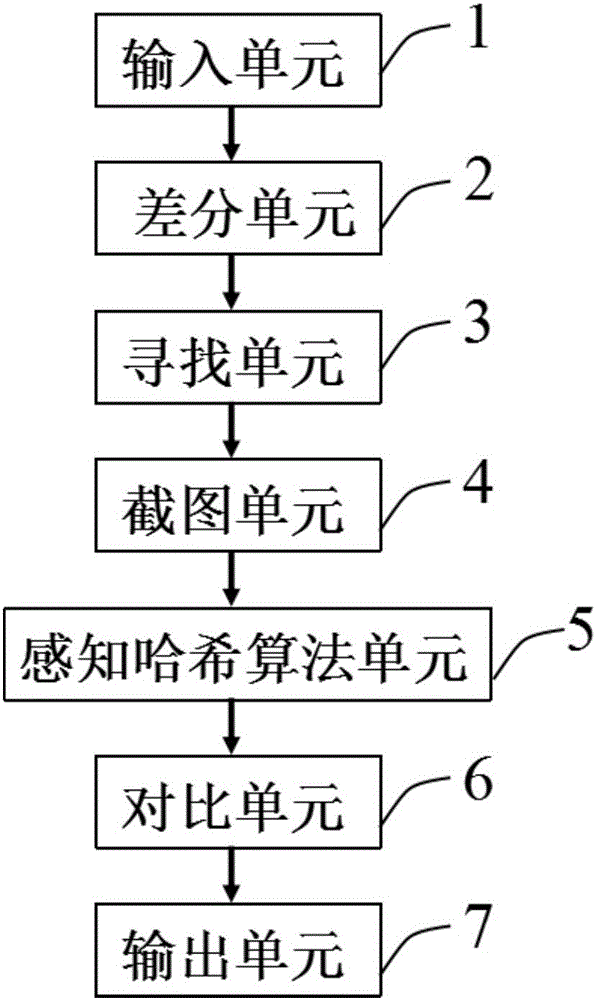
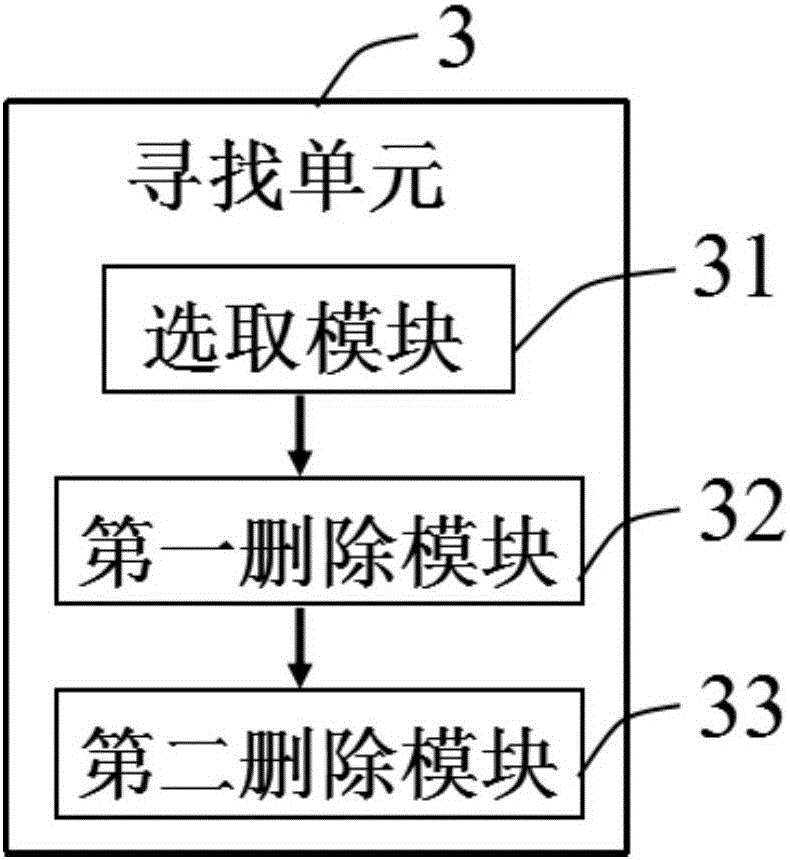
Method and device for searching similar image based on perceptual hash
ActiveCN105956020AImprove readinessMake up for the errorImage enhancementImage analysisImage basedPattern recognition
The invention provides a method and a device for searching similar images based on perceptual hash. The device comprises an input unit, a difference unit, a searching unit, a screenshot unit, a perceptual hash algorithm unit, a comparison unit, and an output unit. The device has beneficial effects that after an input original image and a screenshot image of the original image are processed by the perceptual hash algorithm, the input original image and the screenshot image are respectively compared with images in a search library, so that under the condition that the input image is the screenshot image of a certain image, the source of the original image can be found. The device and the method improve accurate rate of the perceptual hash algorithm, and provide a new thinking for searching similar images.
Owner:GUANGDONG KINGPOINT DATA SCI & TECH CO LTD
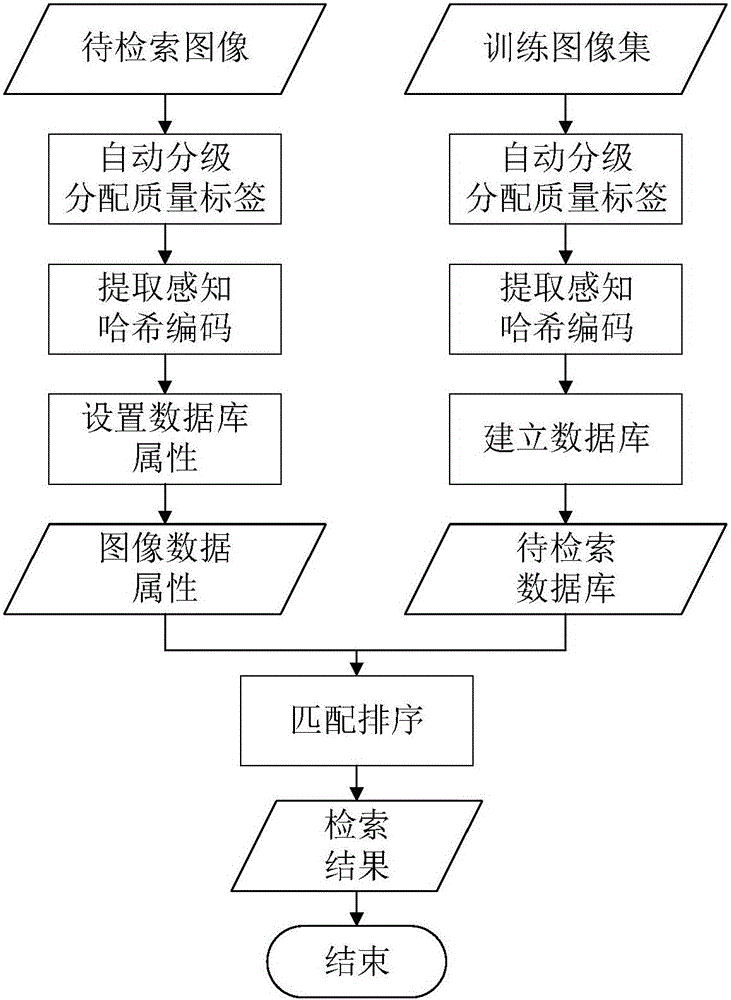
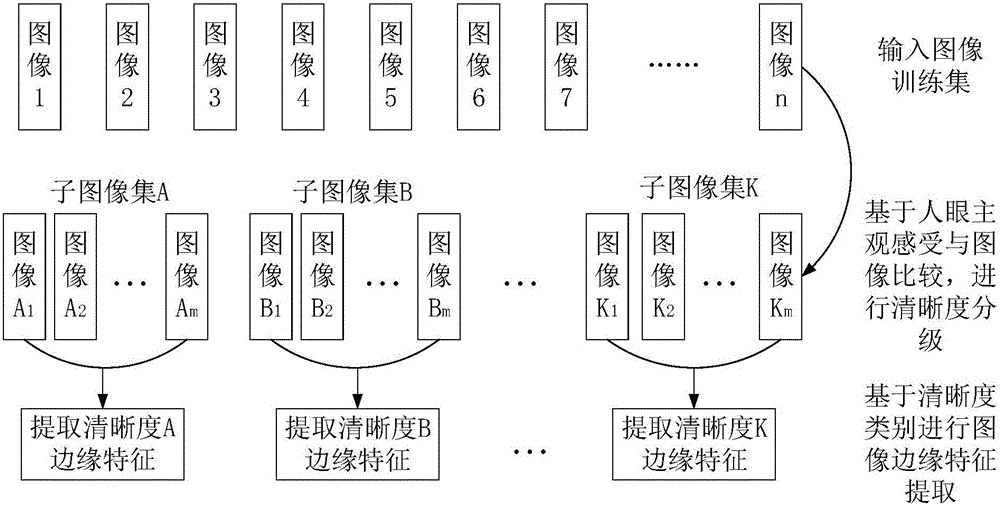
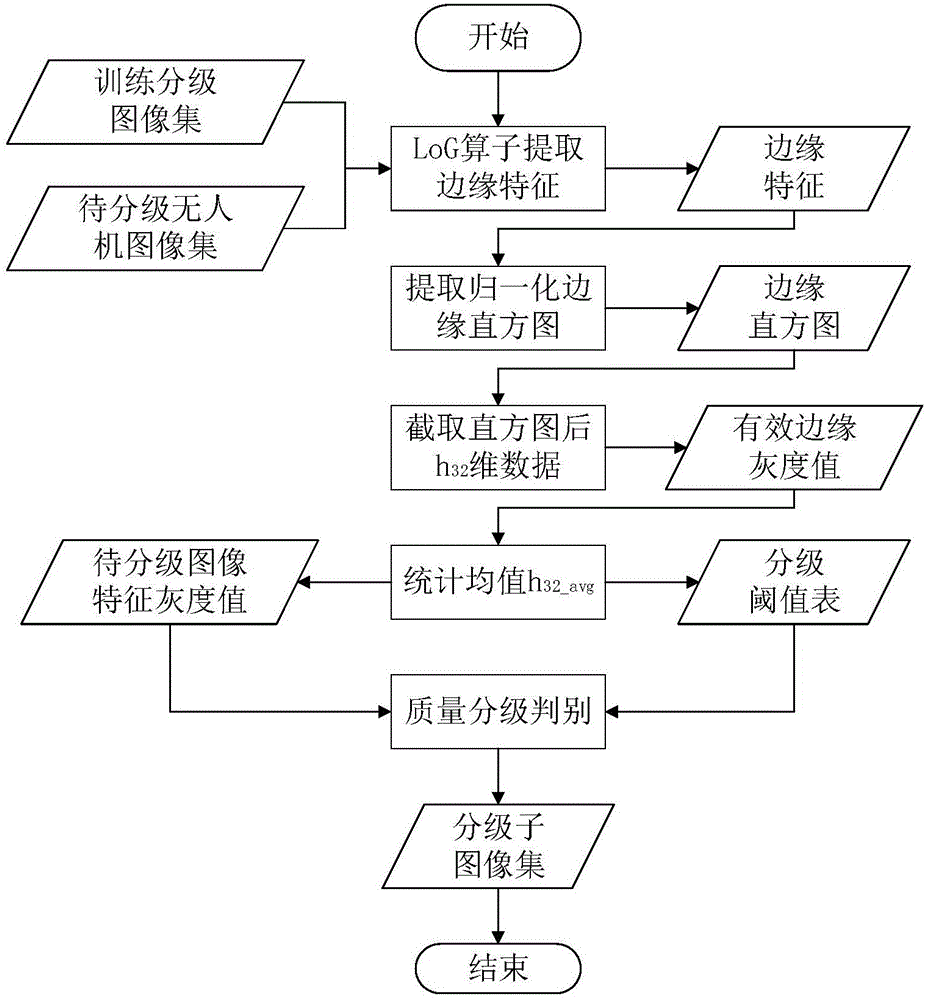
Quality grading and perceptual hash characteristic combination-based unmanned aerial vehicle image retrieval method
ActiveCN106126585AReduce data dimensionalityAlgorithm time performance is goodSpecial data processing applicationsImaging processingImaging quality
The invention discloses a quality grading and perceptual hash characteristic combination-based unmanned aerial vehicle image retrieval method, and belongs to the technical field of image processing. The method comprises the steps of firstly, performing automatic quality grading and quality label allocation on an unmanned aerial vehicle training image set, extracting perceptual hash codes, and establishing database applications corresponding to images and texts; secondly, setting quality label and perceptual hash code-based data attributes for to-be-retrieved images, like the sub-steps in the first step; thirdly, performing Hamming distance matching on the obtained data attributes of the to-be-retrieved images and images in a database; and finally, allocating a certain weight to a similar image set obtained by matching in combination with similarity and quality labels to establish a weight function, performing resorting according to a weight progressive increase sequence, and outputting an image result. According to the method, image characteristics can be quickly extracted and image quality grading can be effectively finished, so that quick and accurate retrieval of the unmanned aerial vehicle images is realized.
Owner:BEIHANG UNIV
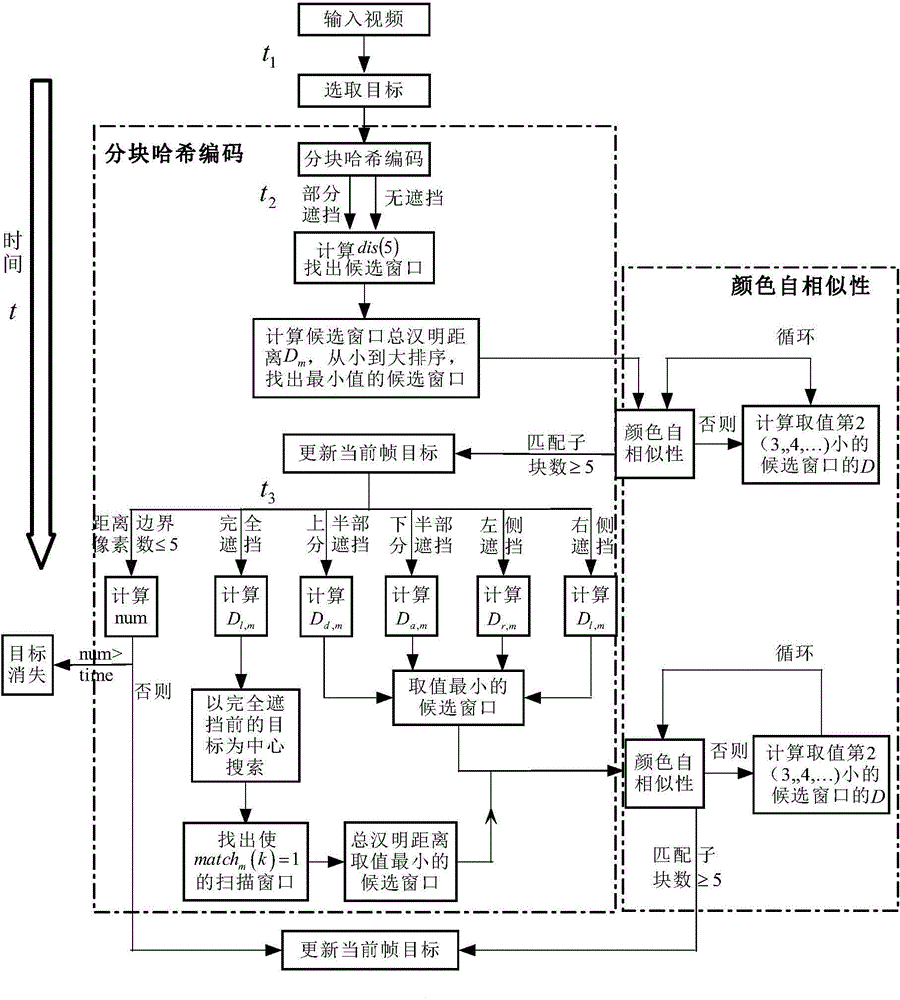
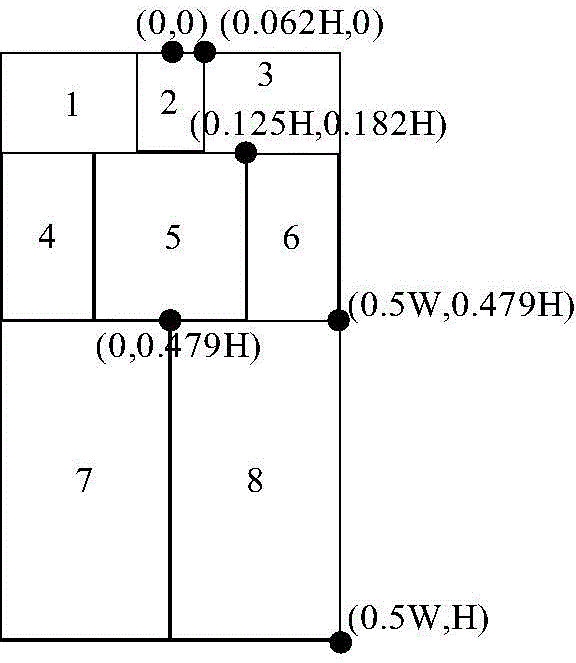
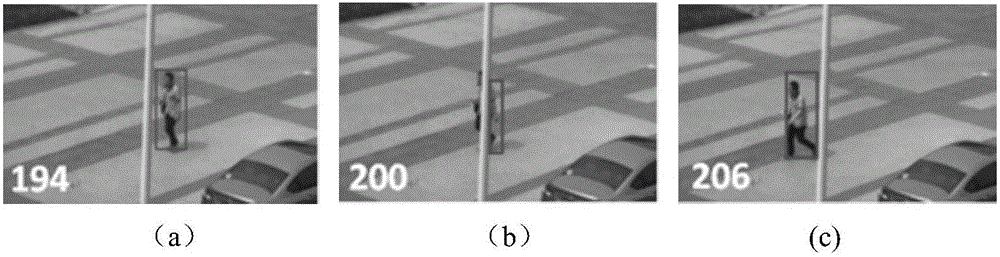
Blocking perception Hash tracking method with shadow removing
InactiveCN105989611ASolve the problem of losing trackImprove robustnessImage analysisShadowingsComputer graphics (images)
The invention discloses a blocking perception Hash tracking method with shadow removing. The method comprises the steps of: determining shadow areas in an image according to the distribution characteristics of a shadow image in each channel grey-scale map of a CIELAB color space; then utilizing a color constancy theory to recover pixel points in the shadow areas to a non-shadow effect; combining blocking perception Hash coding values with color self-similarity for forming a similarity measure, and carrying out matching on tracked target sub-blocks of adjacent frames based on the similarity measure; and finally, combining the above sub-blocks to obtain the regional position of the tracked target in the current frame, and realizing the tracking of the tracked target in a video. The blocking perception Hash tracking method has the advantages that according to different moving ranges and deforming degrees of human body parts, a human body target is divided into eight sub-blocks, and on this basis, and the blocking perception Hash coding method is provided to solve the problem of an existing tracking algorithm that the tracking is unsuccessful when the human body is partially or totally shielded or partially rotated and when the illumination in the shadow areas and non-shadow areas of a natural scene changes suddenly.
Owner:NANJING UNIV OF SCI & TECH
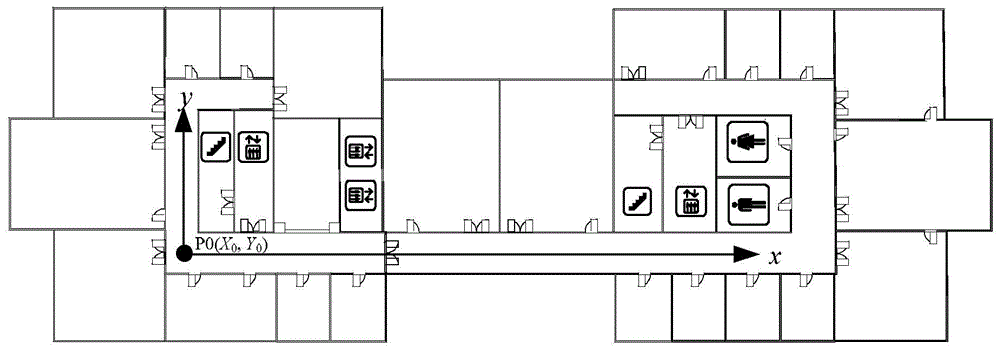
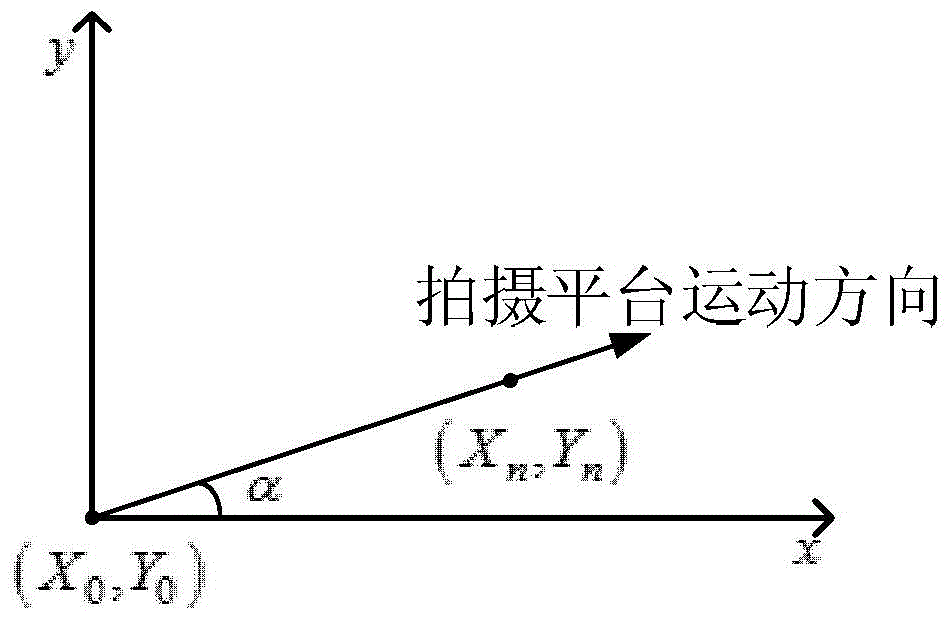
Video-acquisition-based Visual Map database establishing method and indoor visual positioning method using database
ActiveCN104457758AReduce workloadHigh precisionNavigational calculation instrumentsSpecial data processing applicationsLinear motionVisual positioning
The invention discloses a video-acquisition-based Visual Map database establishing method and an indoor visual positioning method using a database, relates to the field of indoor positioning and navigation, and aims to solve the problems of low indoor visual positioning accuracy, high time consumption and high labor consumption of an existing method. The indoor visual positioning method using the database is characterized in that a platform carrying a video acquisition device is used for recording videos in the constant-speed linear motion process on the basis of the quickly established video-based Visual Map database; the acquired videos are processed for recording coordinate position information and image matching information of frames of the videos; in an on-line positioning stage, a system is used for roughly matching an image uploaded by a positioned user with the video-based Visual Map database by using a hash value which is obtained by calculating by using a perceptual hash algorithm, and completing the visual indoor positioning by virtue of the roughly matched frames and the uploaded image by using an SURF algorithm and a corresponding epipolar geometry algorithm. The indoor visual positioning method is applied to indoor visual positioning places.
Owner:哈尔滨工业大学高新技术开发总公司
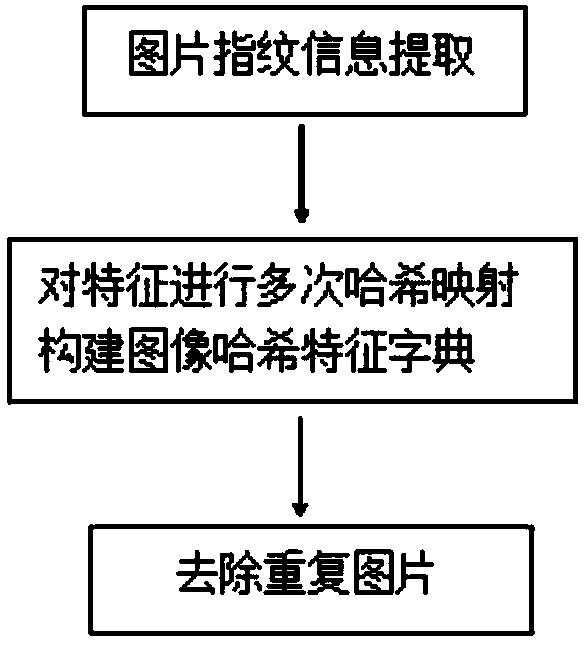
Quick massive-picture deduplication method
InactiveCN108595710AQuick extractionFast deduplicationCharacter and pattern recognitionSpecial data processing applicationsImaging FeatureComputer science
The invention discloses a quick massive-picture deduplication method. Each of to-be-deduplicated pictures is used to generate image fingerprint information through a perceptual hash algorithm; and multiple sets of random hash mapping are employed to construct an image hash feature dictionary, and thus duplicate pictures are removed. Compared with the prior art, the method generates image fingerprints through constructing low-dimensional image features, constructs the image hash feature dictionary, thus carries out quick deduplication of the massive images, completely removes image feature comparison consuming more time, alleviates the mapping space sparse problem caused by the low-dimensional image features and local-sensitive hashes through designing multiple reasonable hash mapping, canquickly extract the image features, and position the duplicate images, also reduces feature comparison frequency of the images to 0, and greatly improves deduplication efficiency of the massive imagesin a case of ensuring accuracy.
Owner:杨晓春
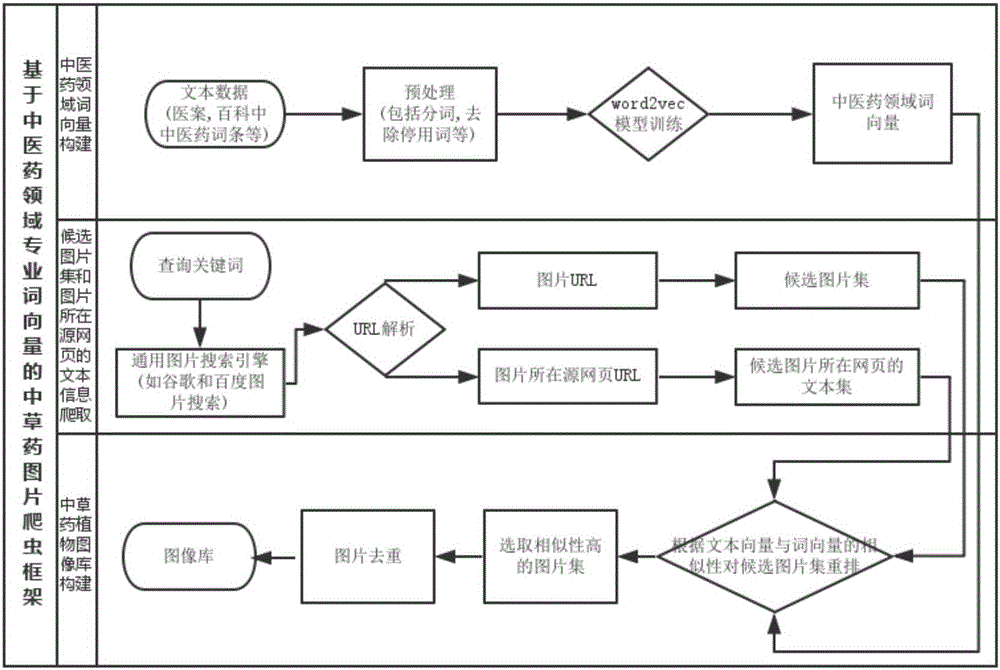
Chinese herbal medicine plant picture capturing method based on professional term vector of traditional Chinese medicine and pharmacy field
The invention discloses a Chinese herbal medicine plant picture capturing method based on a professional term vector of the traditional Chinese medicine and pharmacy field. The Chinese herbal medicine plant picture capturing method comprises the following steps: firstly, selecting and collecting traditional Chinese medicine and pharmacy text data, text information of medicine books and dictionary entry information relevant to traditional Chinese medicine and pharmacy, captured from an encyclopaedia website; secondly, training a Word2Vec model by using the text data so as to obtain professional term vectors of the traditional Chinese medicine and pharmacy field; then, acquiring a candidate picture set and text information thereof on source web pages through an image retrieval function based on texts provided by common search engines, such ash Google and Baidu, and calculating characteristic vectors of the source web pages by using a Doc2Vec model; finally, according to the similarity of the characteristic vector of the source web page and the corresponding Chinese herbal medicine term vector, rearranging the candidate picture set, and selecting a plurality of pictures arranged at the front, and de-duplicating the picture set by using a perceptual hash algorithm so as to obtain a final picture set.
Owner:ZHEJIANG UNIV
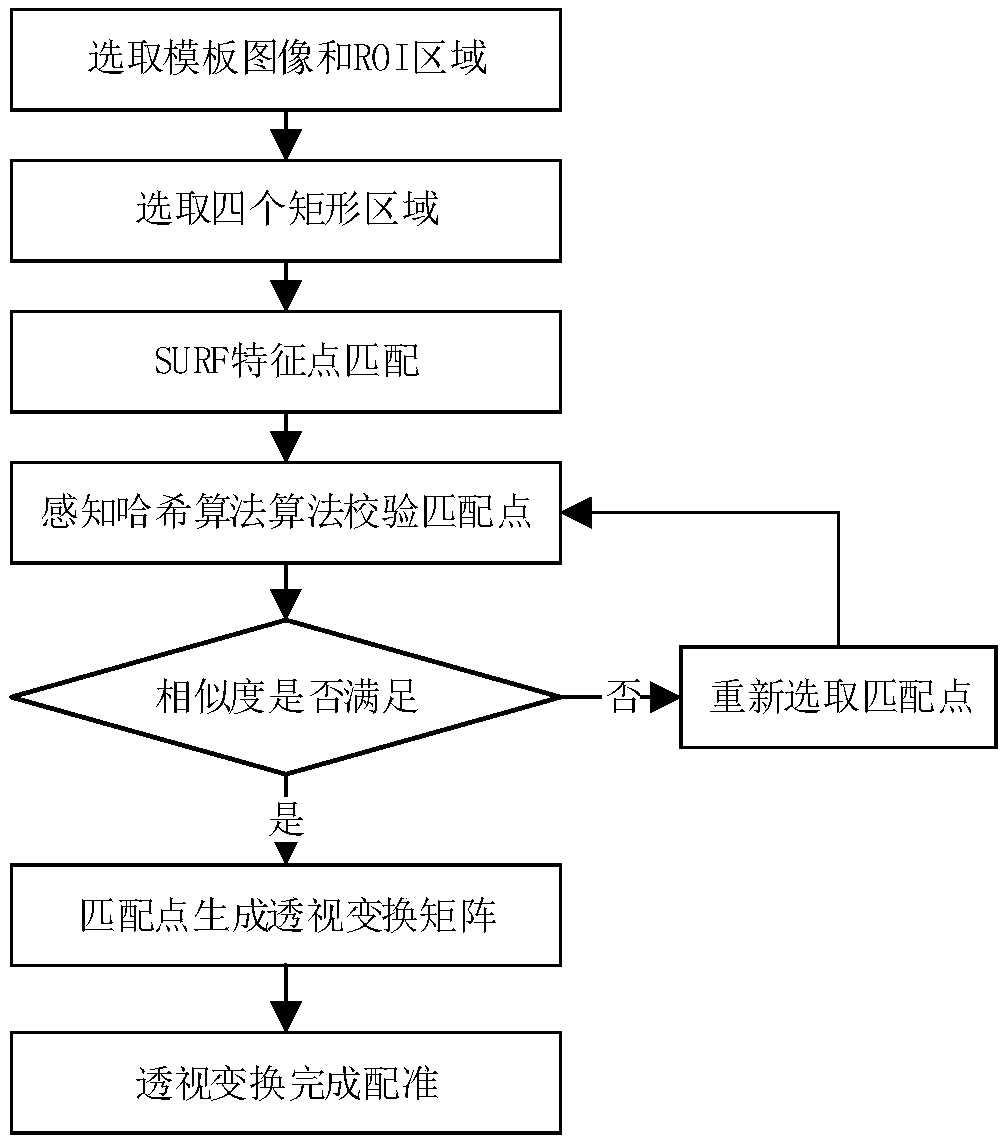
Automatic registration of FPC images based on SURF features and hash perception algorithm
InactiveCN109271996AImprove matching accuracyGood effectImage analysisCharacter and pattern recognitionPattern recognitionPattern perception
Automatic registration of FPC images based on SURF features and hash perception algorithm. The invention discloses a FPC image registration method based on SURF feature and hash perception algorithm,including: first selecting the template image and ROI area, selecting four rectangular regions within the ROI region, matching the rectangular region and the SURF feature points of the image to be registered is realized by using force matching or FLANN, checking the similarity of the rectangular region around the matched feature points by using perceptual hashing algorithm, and finding four pairsof matched feature points to generate perspective transformation matrix, and then registering the image to be registered by perspective transformation. The invention verifies the matched SURF characteristic points by using the perceptual hash algorithm, greatly improves the matching accuracy of the SURF characteristic points, simultaneously establishes a perspective transformation matrix by usingthe matched characteristic points, and completes the image registration by using the perspective transformation and obtains a better effect.
Owner:NANJING UNIV OF SCI & TECH
Cipher text speech perception hashing and retrieving scheme based on time-frequency domain trend change
InactiveCN104835499AImprove retrieval efficiencyImprove matching speedSpeech analysisTransmissionTime domainCiphertext
The invention discloses a cipher text speech perception hashing and retrieving scheme based on time-frequency domain trend change. A piece of speech is divided into a time domain part and a frequency domain part for extracting perception hash, the speech is encrypted by a high-efficiency chaotic XOR encryption algorithm adapting to large-scale data, and a perception hash sequence is embedded into the least significant bit of the cipher text speech by the digital watermarking technology to generate a cipher text speech library and a system perception hash table. The cipher text speech library and the perception hash table are uploaded to the cloud. During retrieval, a perception hash sequence is extracted from an index speech provided by a user, the abstract sequence is submitted to a cloud server as an index, and matching retrieval is carried out in the system hash table of the cloud. When the perception hash sequence is matched with a perception hash value in the system hash table, a cipher text speech corresponding to the hash abstract in the hash table is returned to the user, and retrieval succeeds. Rapid and accurate retrieval of an encrypted speech in the cloud is realized. According to the method, weight distinguishing is carried out, matching is carried out successively, and therefore, the matching efficiency in large-scale application is improved.
Owner:SOUTHWEST JIAOTONG UNIV
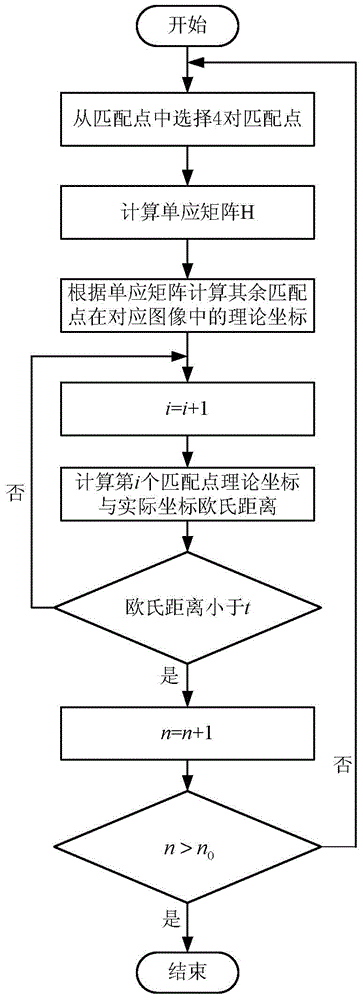
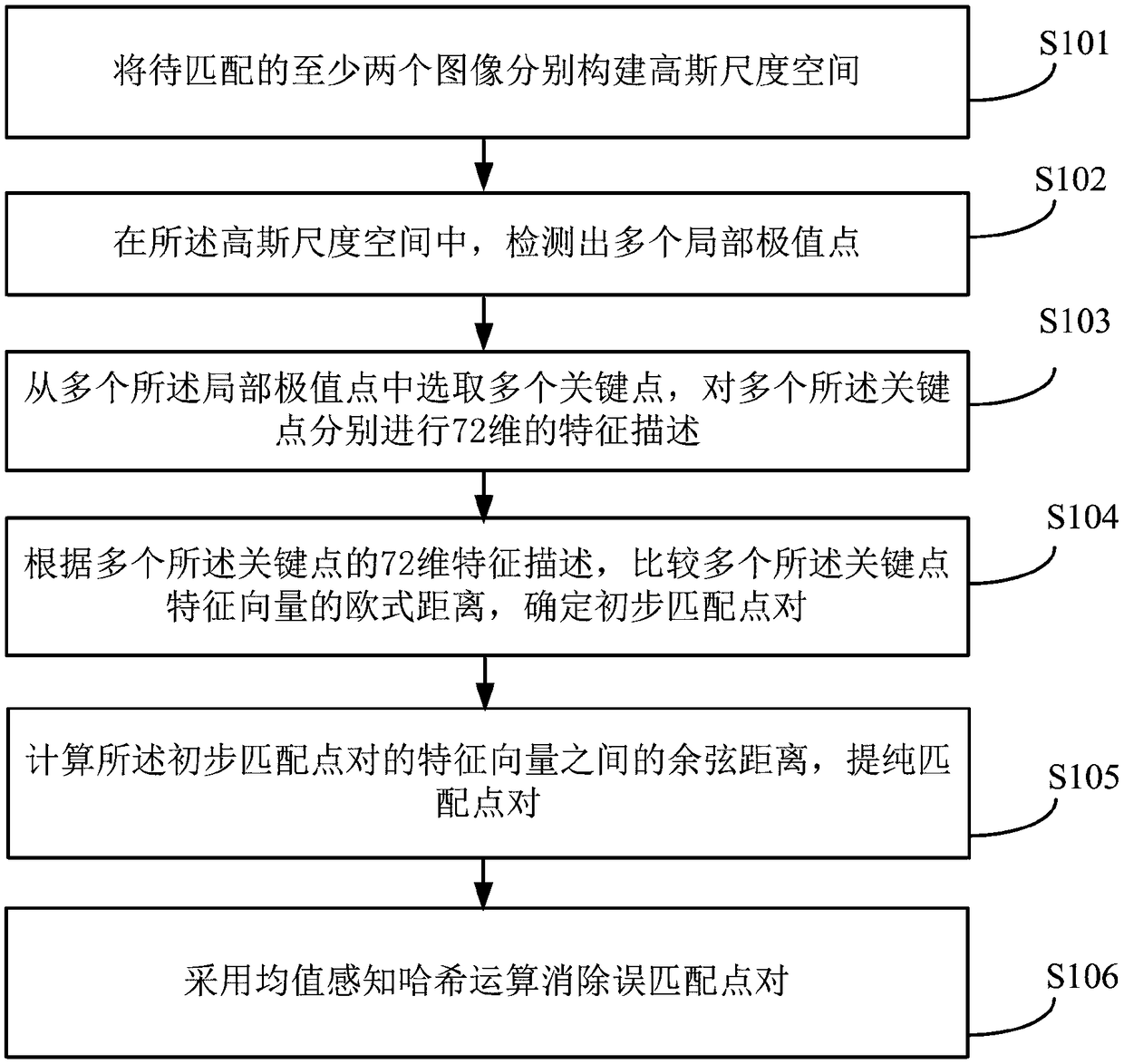
An image registration method and apparatus based on an improved SIFT and hash algorithm
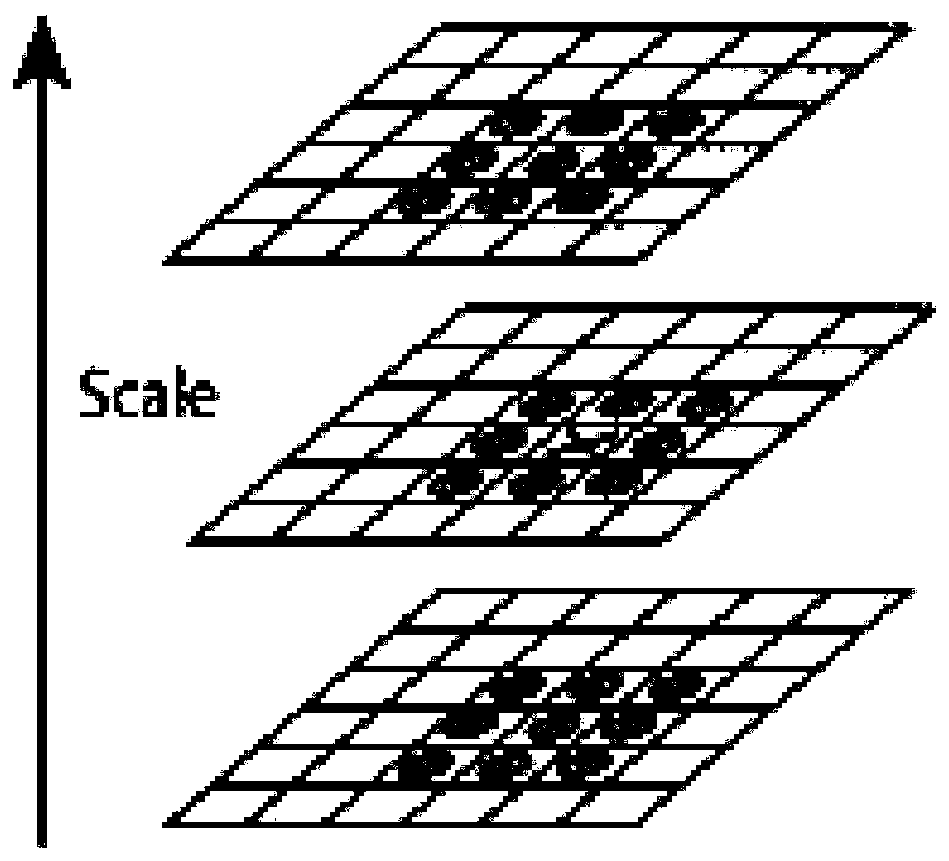
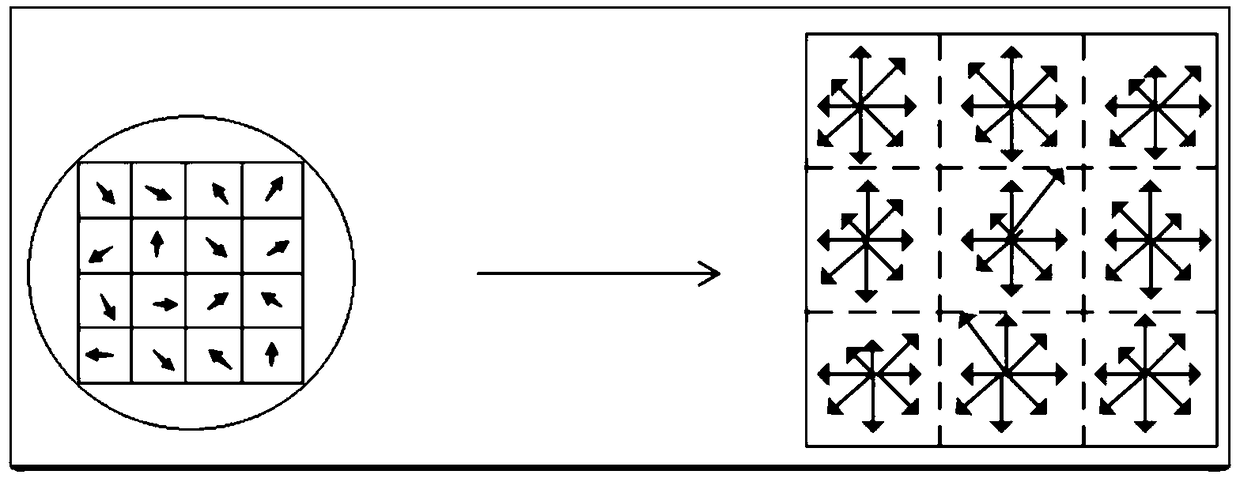
InactiveCN109410255AReduce dimensionalityReduce computational complexityImage analysisData setComputation complexity
The invention relates to an image registration method and a device based on an improved SIFT and a hash algorithm. The method comprises the following steps: at least two images to be matched are respectively constructed into a Gaussian scale space; detecting a plurality of local extreme points in the Gaussian scale space; selecting a plurality of key points from the plurality of local extreme points, and respectively describing 72-dimensional features of the plurality of key points; by narrowing the neighborhood of the selected feature points, the dimension of the traditional SIFT descriptor is reduced, the computational complexity is reduced, and the matching speed is improved. Then, by increasing the cosine distance between the feature point vectors, the similarity between the two feature vectors to be matched can be calculated better and more effectively, and the matching precision can be improved. Finally, by means of mean-perceptual hashing operation to eliminate some mismatched point pairs, the invalid data in the sample data set is reduced, and the iterative search for the optimal parameter matrix in the matching point data set is more efficient.
Owner:CHINA UNIV OF MINING & TECH
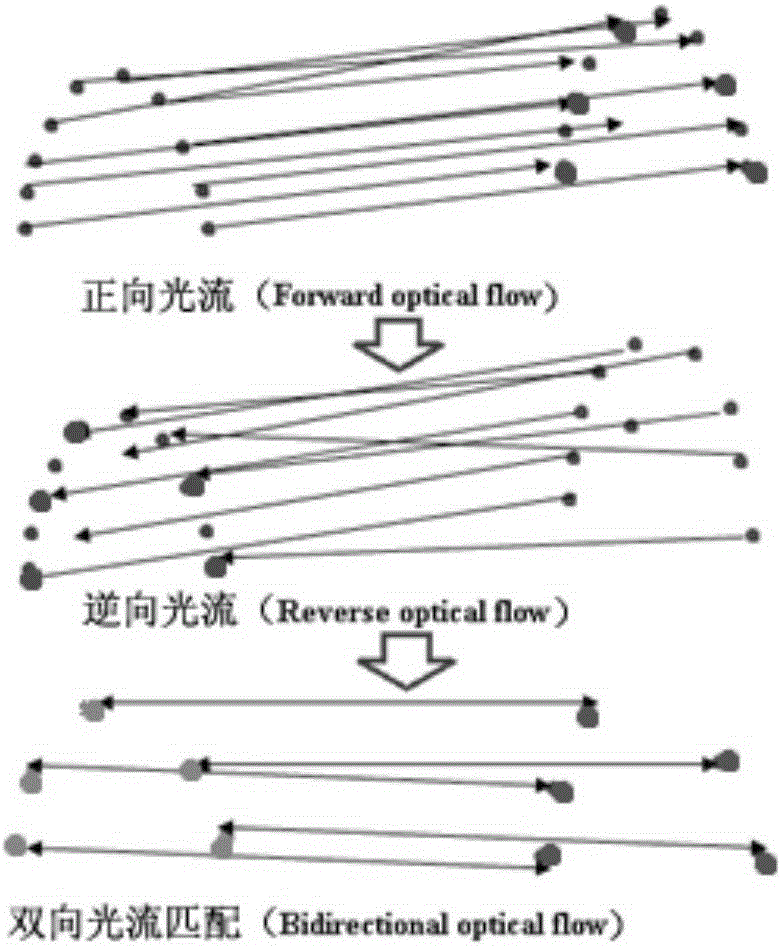
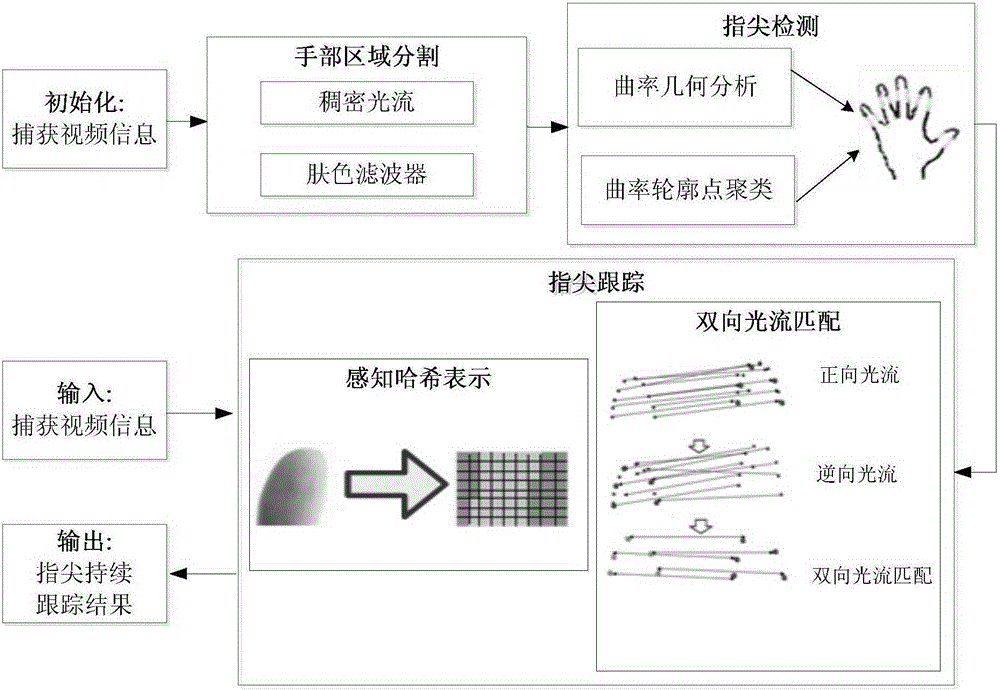
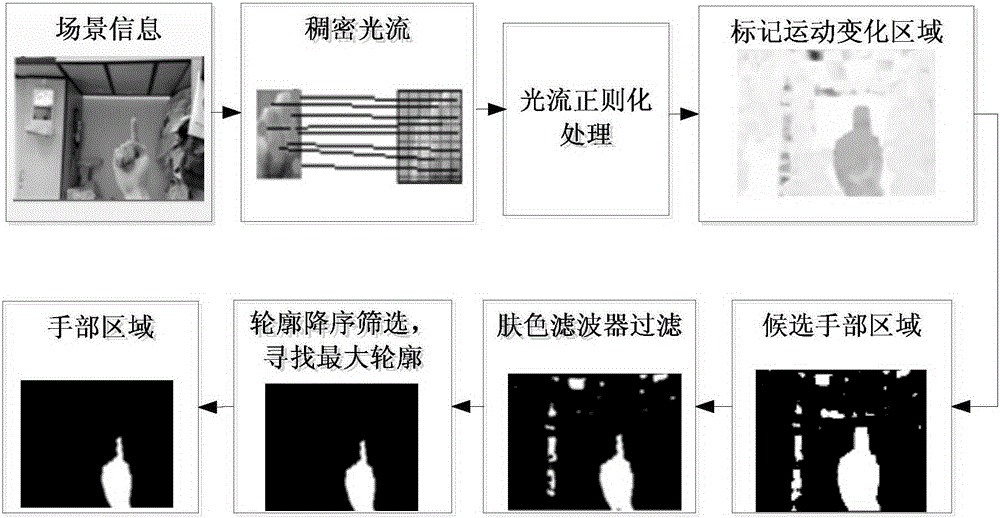
Bidirectional optical flow and perceptual hash based fingertip tracking method
ActiveCN105261038ATracking is stable and efficientAchieve continuous trackingInput/output for user-computer interactionImage analysisSkin colorOptical flow
The invention provides a bidirectional optical flow and perceptual hash based fingertip tracking method. The method comprises the steps of S1, calculating dense optical flow information corresponding to scene information, and constructing a skin color filter to acquire a hand area; S2, carrying out vector dot product and cross multiplication calculation on each contour point so as to remove non-fingertip contour points, detecting the position of a fingertip point according to geometrical features of the fingertip, and acquiring fingertip contour points; and S3, calculating the fingertip contour points by using a bidirectional pyramid optical flow algorithm, acquiring bidirectionally matched fingertip contour points so as to carry out estimation on a fingertip moving area, generating a 64-bit perceptual hash sequence by adopting a perceptual hash algorithm, and matching the 64-bit perceptual hash sequence with a fingertip hash sequence template, wherein the maximum matching area is a fingertip area; and judging whether a next turn of fingertip tracking is carried out or not, and realizing fingertip continuous tracking. The method provided by the invention can effectively realize continuous tracking for the fingertip in a complex environment, and a problem of poor fingertip tracking effect caused by discontinuous fingertip tracking trajectory is avoided at the same time.
Owner:SOUTH CHINA UNIV OF TECH
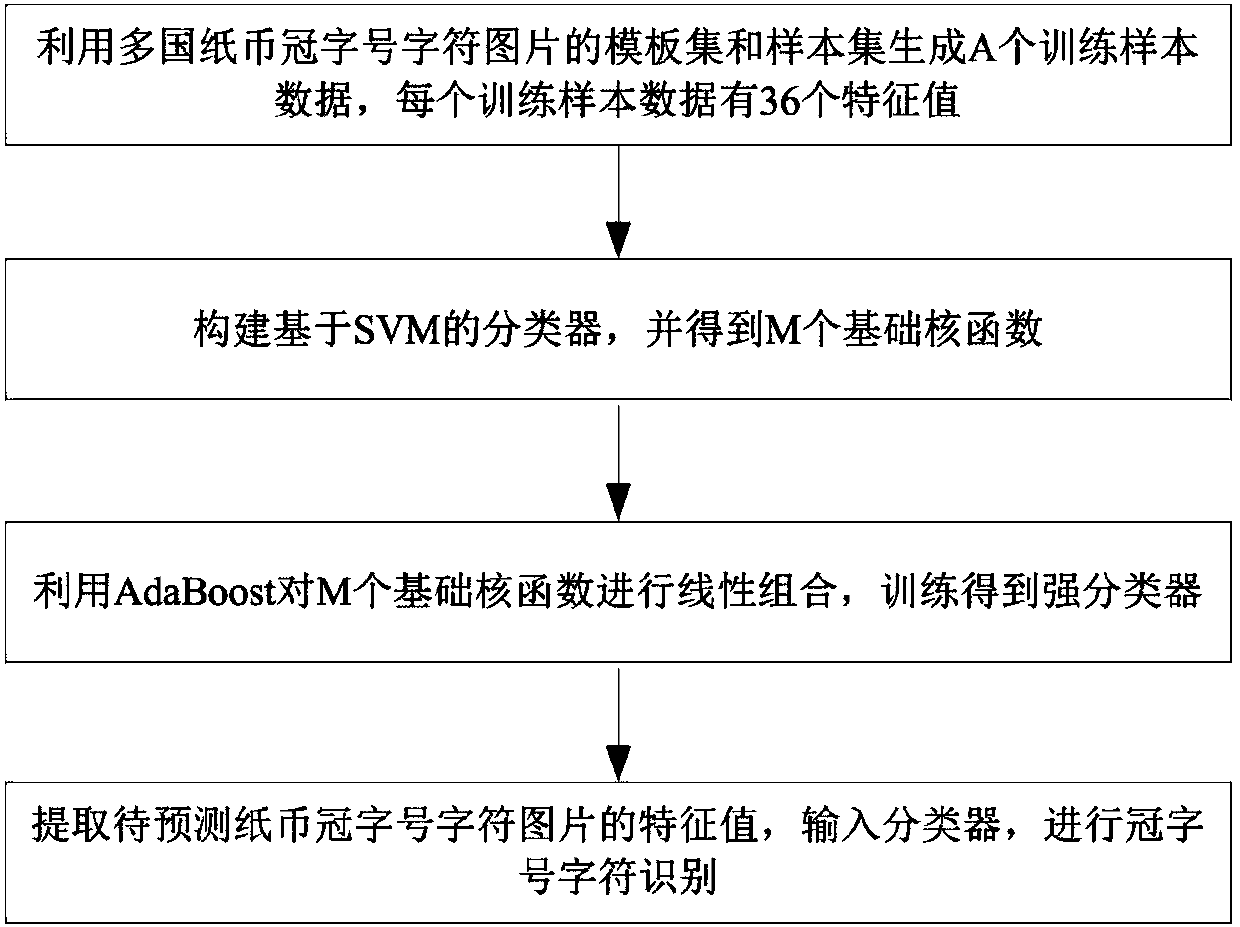
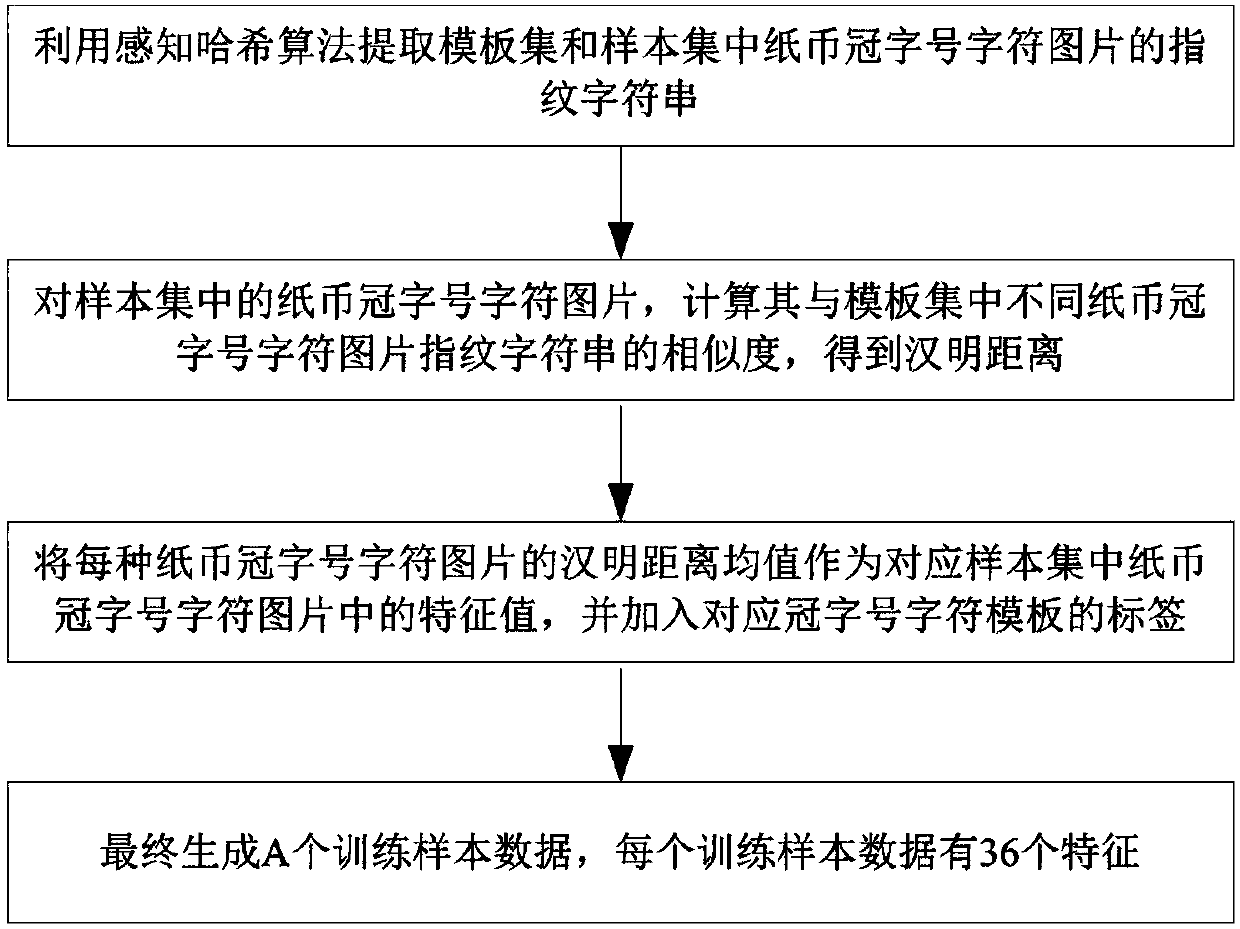
Multi-country banknote serial number character recognition method based on image fingerprints
InactiveCN108320374AReduce demandLow hardware requirementsPaper-money testing devicesCharacter recognitionFault toleranceSmall sample
The invention discloses a multi-country banknote serial number character recognition method based on image fingerprints and belongs to the technical field of banknote pattern recognition. The method comprises: based on a template set and a sample set of multi-country banknote serial number character images, generating training sample data by a perceptual hash algorithm; constructing a classification model based on a SVM classifier; training the classification model by using the training sample data; and recognizing the serial number character image of a banknote to be processed by using the trained classification module. The method of the invention converts a single feature in the process of recognizing the serial number character of the banknote into a plurality of features, and uses themethod based on the SVM classifier to recognize the characters, has small sample demand, fast training speed, fast recognition speed, a good anti-interference ability and can improve the fault tolerance rate during prediction.
Owner:CENT SOUTH UNIV
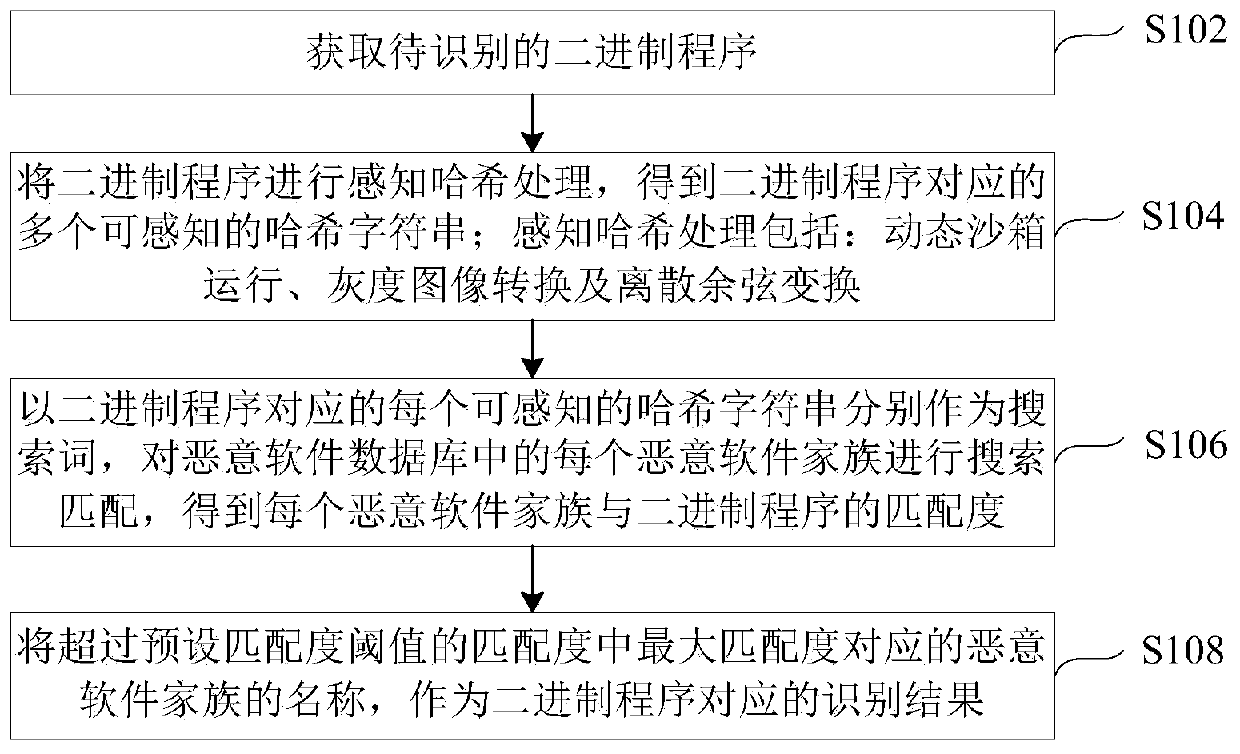
Malware family identification method and device and electronic equipment
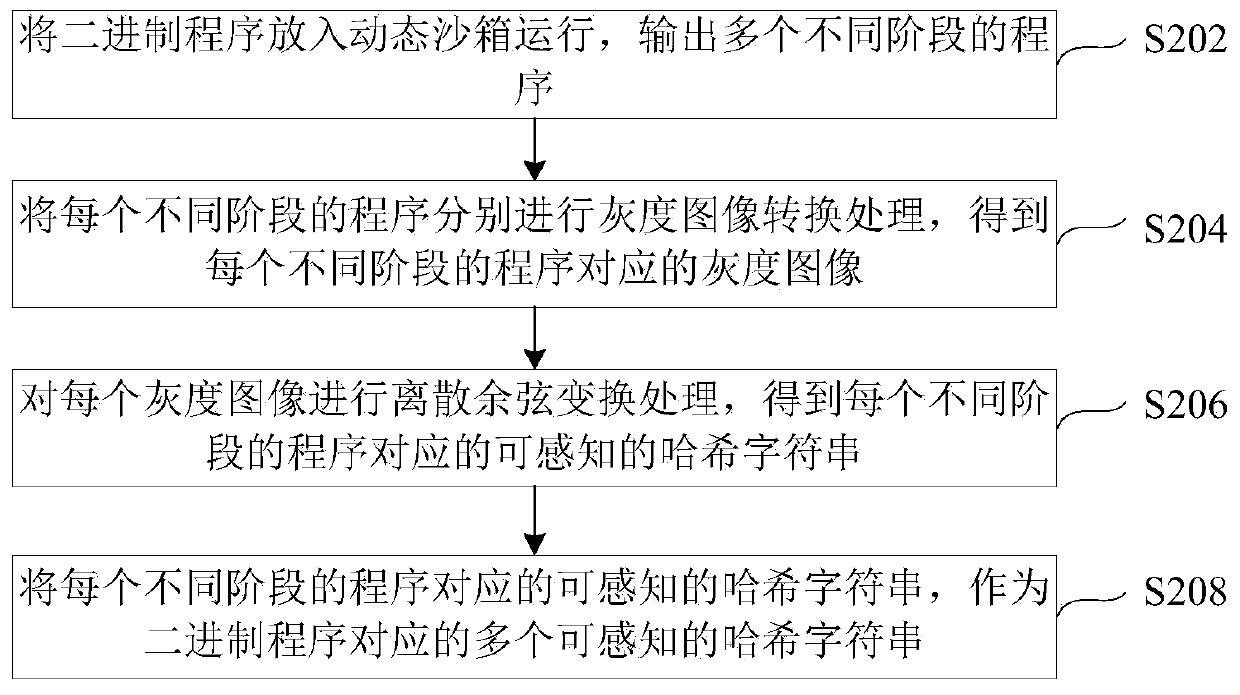
ActiveCN110222511APlatform integrity maintainanceFile metadata searchingSearch wordsPattern perception
The invention provides a malware family identification method and device and electronic equipment, and the method comprises the steps: carrying out the perception Hash processing of a binary program to be identified, and obtaining a plurality of perceptible Hash character strings, wherein the perceptual hash processing comprises dynamic sandbox operation, gray level image conversion and discrete cosine transformation; searching and matching each malicious software family in the malicious software database by taking each perceptible Hash character string as a search word to obtain a matching degree between each malicious software family and the binary program, wherein each malicious software family comprises a plurality of perceptible hash word string sequences obtained through perceptive hash processing; and taking the name of the malware family corresponding to the maximum matching degree in the matching degrees exceeding the preset matching degree threshold value as an identificationresult corresponding to the binary program. According to the invention, when the dynamic malware detection engine detects malware, the accurate name of the malware family to which the malware belongscan be given.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
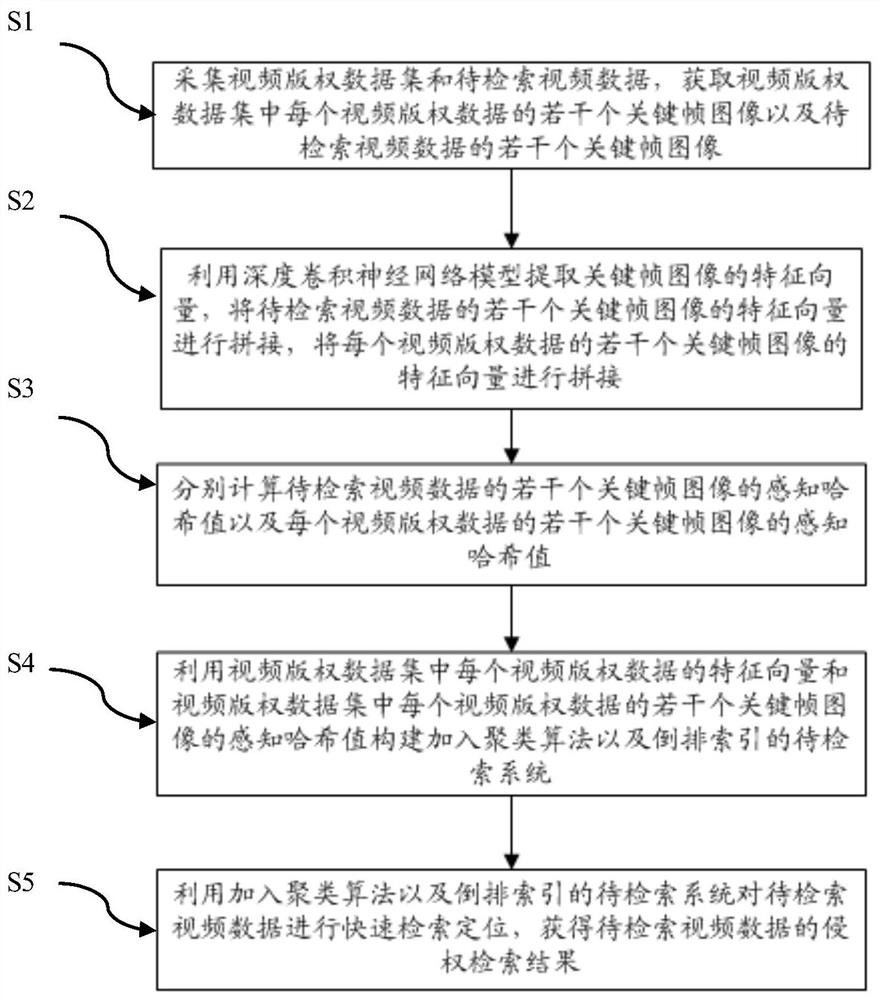
Video to-be-retrieved positioning method applied to video copyright protection
ActiveCN112395457AEasy to identifyImprove robustnessVideo data indexingVideo data queryingCluster algorithmFeature vector
The invention relates to the field of video copyright protection, and discloses a video to-be-retrieved positioning method applied to video copyright protection, which comprises the following steps: acquiring a plurality of key frame images of each video copyright data in a video copyright data set and a plurality of key frame images of to-be-retrieved video data; extracting a feature vector of the key frame image by using a deep convolutional neural network model; calculating perceptual hash values of a plurality of key frame images of the to-be-retrieved video data and perceptual hash valuesof a plurality of key frame images of each video copyright data; constructing a to-be-retrieved system added with a clustering algorithm and an inverted index; and performing quick retrieval and positioning on the to-be-retrieved video data. According to the method, the infringement fragment or the infringement picture can be accurately positioned, the identification of possible attack resistingmeans of the infringement video is enhanced, the robustness of the model is enhanced, the retrieval efficiency under mass data is improved, and the high accuracy and recall rate of video infringementretrieval are ensured.
Owner:CHINASO INFORMATION TECH
Symmetrical ternary string represented voice perception Hash sequence constructing and authenticating method
InactiveCN104134443AOvercome weaknessPerceptual hash digest is strongSpeech analysisAlgorithmVoice communication
The invention discloses a symmetrical ternary string represented voice perception Hash sequence constructing and authenticating method. The method comprises the steps that firstly, overall discrete wavelet transforming (DWT) is carried out on voice signals produced after preprocessing and intensity-loudness transformation (ILT); secondly, non-overlapping partitioning is carried out on the low-frequency part of the voice signals produced after DWT, and short-time logarithm energy of blocks is calculated to obtain the signal frequency-domain features; lastly, a final ternary perception Hash sequence is generated based on the time domain spectrum flux features (SFF) of the voice signals, and the voice frequency content is quickly authenticated through Hash matching. The symmetrical ternary string representation of the perception Hash abstract is superior to that of the binary form, the common voice content is operated between the robustness and the difference in a balanced mode, the time complexity of the algorithm is low, efficiency and the abstraction are high, precise manipulation detecting and positioning can be achieved, and the method can be used for authenticating a mobile voice communication terminal with bandwidth resources limited in real time.
Owner:LANZHOU UNIVERSITY OF TECHNOLOGY
Feature extraction and authentication method for multi-format audio perceptual Hashing authentication
InactiveCN104091104AImproved noise immunityThe solution is not universalSpeech analysisDigital data authenticationFeature extractionAlgorithm
A feature extraction and authentication method for multi-format audio perceptual Hashing authentication mainly aims to solve the problems that the audio format authenticated by an existing audio authentication algorithm is single, the authentication algorithm is not universal and authentication efficiency is low. The method is based on a dual tree complex wavelet transform (DT-CWT) principle, and includes the steps that global DT-CWT is carried out on preprocessed audio signals and a real wavelet coefficient of the audio signals is extracted; second order difference and framing are carried out on the real wavelet coefficient, and the sum of frame coefficients under a natural logarithm is calculated to serve as a feature vector of the audio signals; Hashing construction is carried out on the feature vector to generate a perceptual Hashing abstract sequence, and quick authentication of audio content is achieved through Hash match.
Owner:LANZHOU UNIVERSITY OF TECHNOLOGY
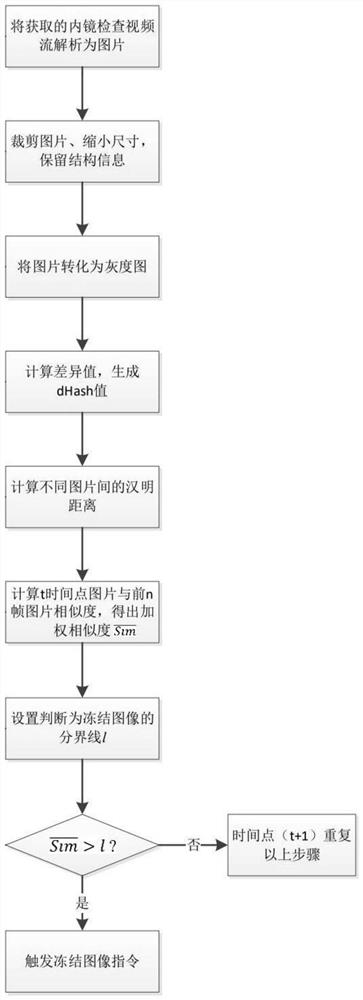
Method for automatic freezing of digestive endoscopy image based on perceptual hash algorithm
InactiveCN111784668AReduce workloadAvoid lossTelevision system detailsImage enhancementG i endoscopyAlgorithm
The invention relates to the technical field of medical image processing, in particular to a method for automatic freezing of a digestive endoscopy image based on a perceptual hash algorithm. The method comprises the following steps: S1, analyzing an endoscopy video stream acquired by endoscopy equipment into image data; S2, calculating the similarity between a picture at a time point t and previous n frames of pictures to obtain the weighted similarity k of the picture; and S3, comparing the picture weighting similarity k at the time point t with a freezing boundary l, and triggering an imagefreezing instruction when the value k reaches the value l. After the method is applied, when an endoscopic doctor needs to carefully check a view image, the endoscopic doctor only needs to stop moving an endoscope body to keep the view unchanged, a frozen image can be automatically judged, and the doctor does not need to manually operate a freezing button, so the workload of the doctor is reduced. A system automatically executes a freezing instruction, so offset of a frozen image view or loss of effective information caused by slow response or unskilled operation of people can be avoided, anda clear image of the optimal view can be effectively obtained.
Owner:WUHAN ENDOANGEL MEDICAL TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com