Symmetrical ternary string represented voice perception Hash sequence constructing and authenticating method
A technology of perceptual hashing and sequence construction, applied in voice analysis, instruments, etc., to achieve the effects of improving operating efficiency, reducing computational complexity, and reducing data volume
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0053] specific implementation plan
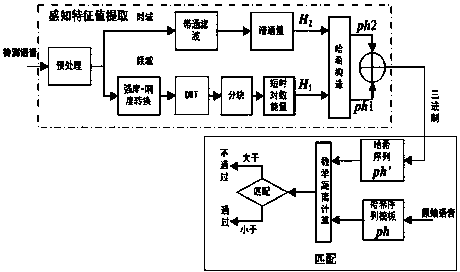
[0054] The present invention is a speech perception hash sequence construction and authentication method represented by a symmetrical ternary string, and its steps are:
[0055] (1) For audio signals S Perform pre-emphasis processing;
[0056] (2) Perform loudness-intensity transformation (ILT) on the pre-emphasized signal;
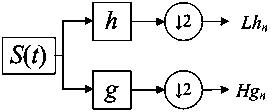
[0057] (3) Discrete wavelet transform is carried out to the signal transformed by ILT, and the low-frequency coefficients of wavelet decomposition are extracted;
[0058] (4) Carry out non-overlapping blocks on the low-frequency coefficients of wavelet decomposition, the block length is M, and the number of blocks is N 0 , get the matrix T;
[0059] (5) Calculate the logarithmic short-term energy of the matrix T row, and obtain the logarithmic short-term energy characteristic parameter vector H 1 ;
[0060] (6) Perform band-pass filtering on the pre-emphasized signal;
[0061] (7) Extract the time-domain spec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com