Method of identity identification, cross-network communication and service transplantation as well as information intercommunication network architecture
A technology for identifying information and identity. It is applied in the field of network architecture to realize information exchange and can solve problems such as lack of clarity.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
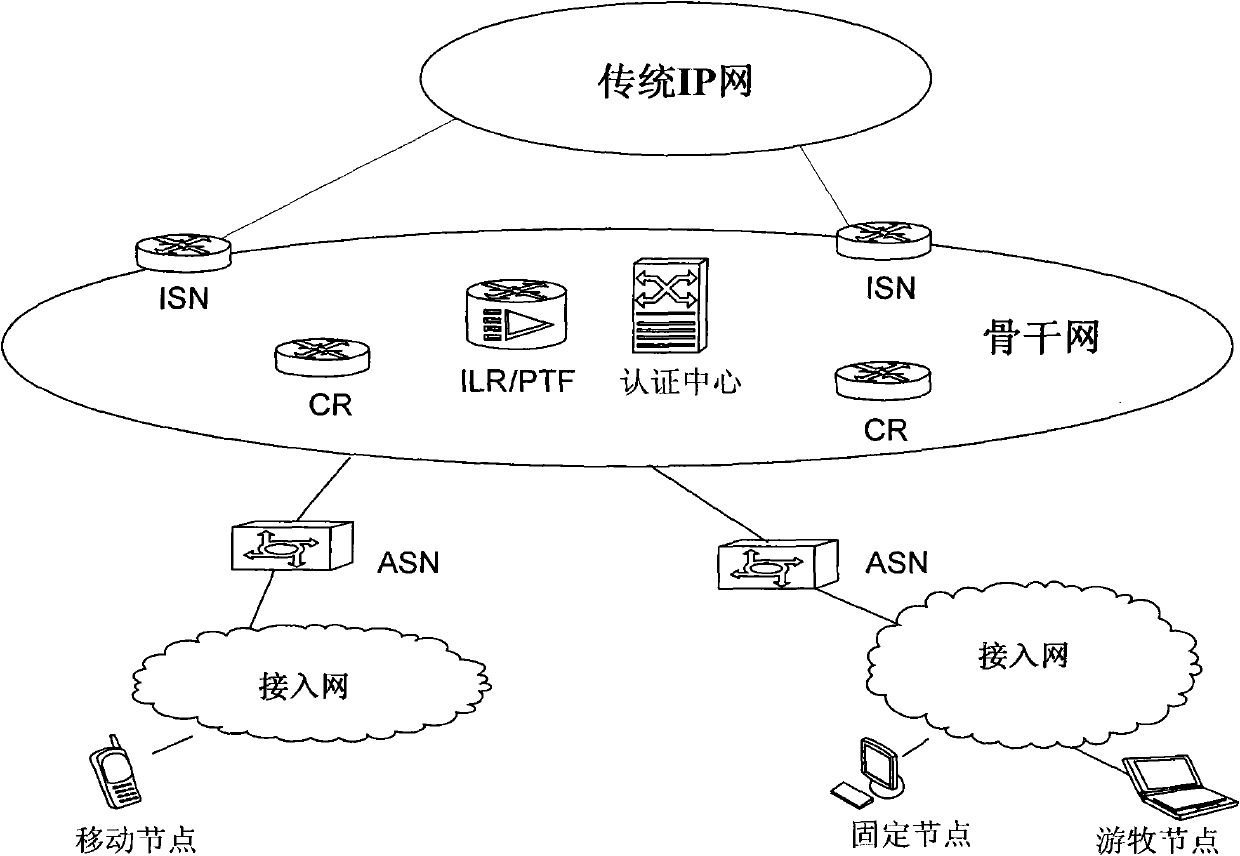
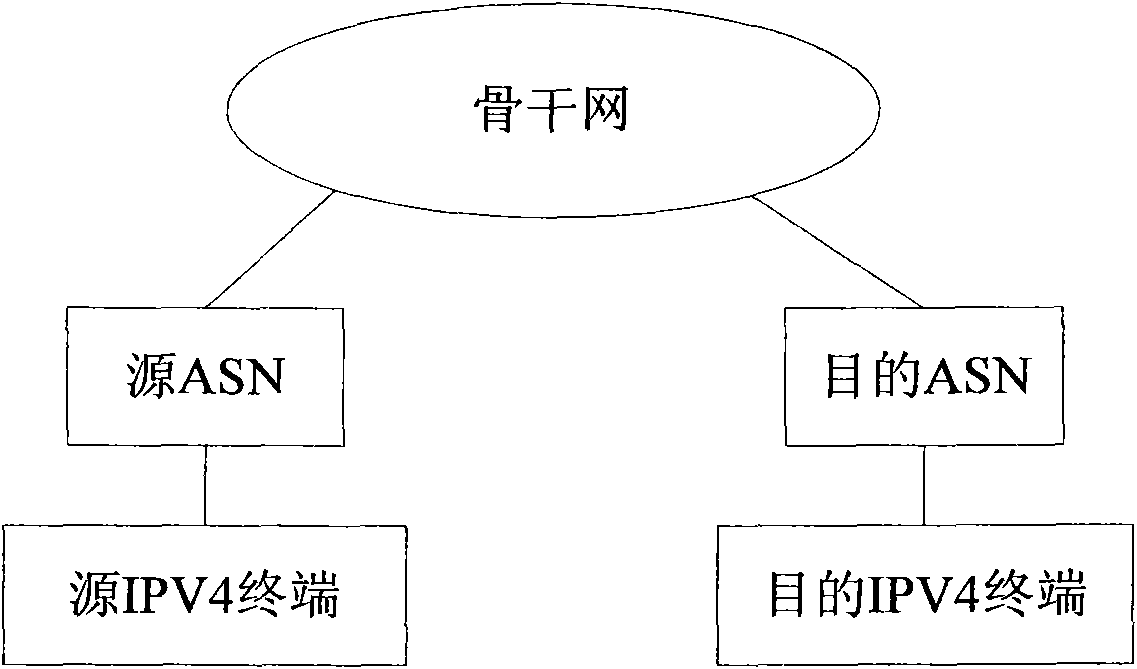
[0107] During the coexistence of the Legacy IP network and the network-based identity and location separation framework, the 32-bit suffix part adopts the IPV4 public network address. The interconnection and intercommunication of IP network; for the IPV4 terminal, it realizes the compatibility with the upper layer business.
[0108] The value of the extension header is a constant determined within the framework of identity identification and location separation. In this way, the extension header of the AID is removed and converted into the corresponding IP address, and the IP address is converted into the corresponding AID by adding the constant as the extension header.
[0109] In this embodiment, the setting rule of the extension header constant is a unique constant determined within the framework of separation of identity and location, so as to realize flexible conversion between the AID format and the IPV4 public network address. In a preferred embodiment of the present in...
Embodiment approach 2
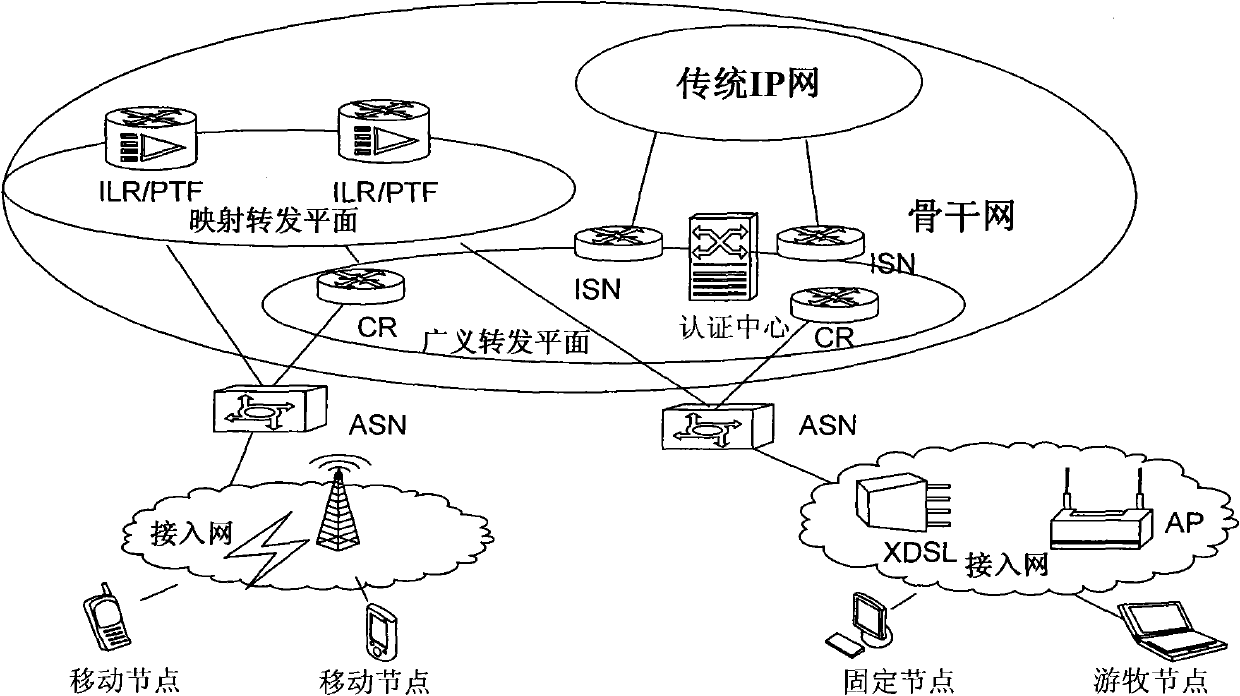
[0118] After the traditional Legacy IP network evolves to a network based on the network-based identity and location separation framework, the value of the extension header EH is assigned by the identity and location separation framework as needed. After completing the historical task of network evolution and transition, in order to realize the expansion of AID address scale and support more user scale.
[0119] After the evolution transition phase is over, since there is no need for interworking with the Legacy IP network, AID does not need to follow the address allocation and occupancy specifications of the Legacy IP network when using a public network address. In the network-based identity and location separation framework, the use of AID can uniquely identify the communication peer, and the value of the extension header EH can be expanded from a constant to a variable, which is allocated by the identity and location separation framework as needed, greatly expanding the avai...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com