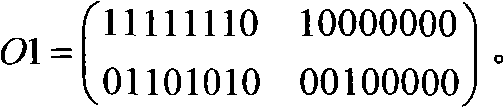Authenticity self-identifying and tampering self-positioning method for digital image
A digital image, self-identification technology, applied in the field of computer application, computer security, image processing, can solve problems such as simple methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
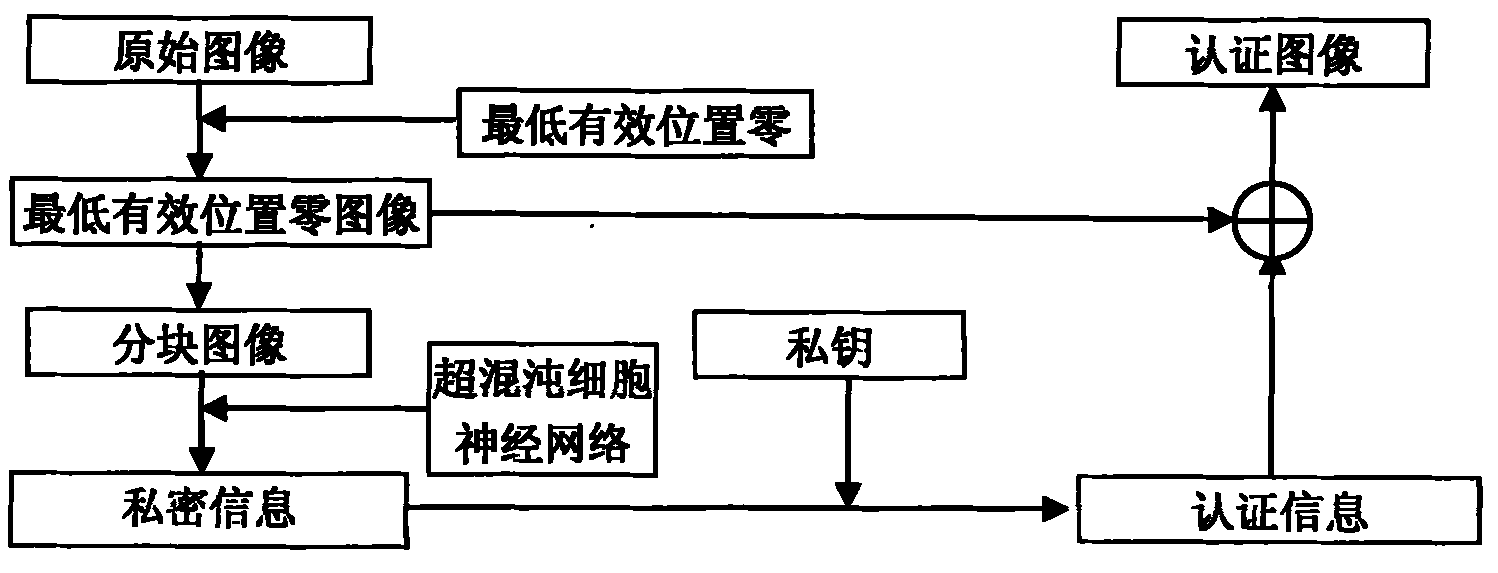
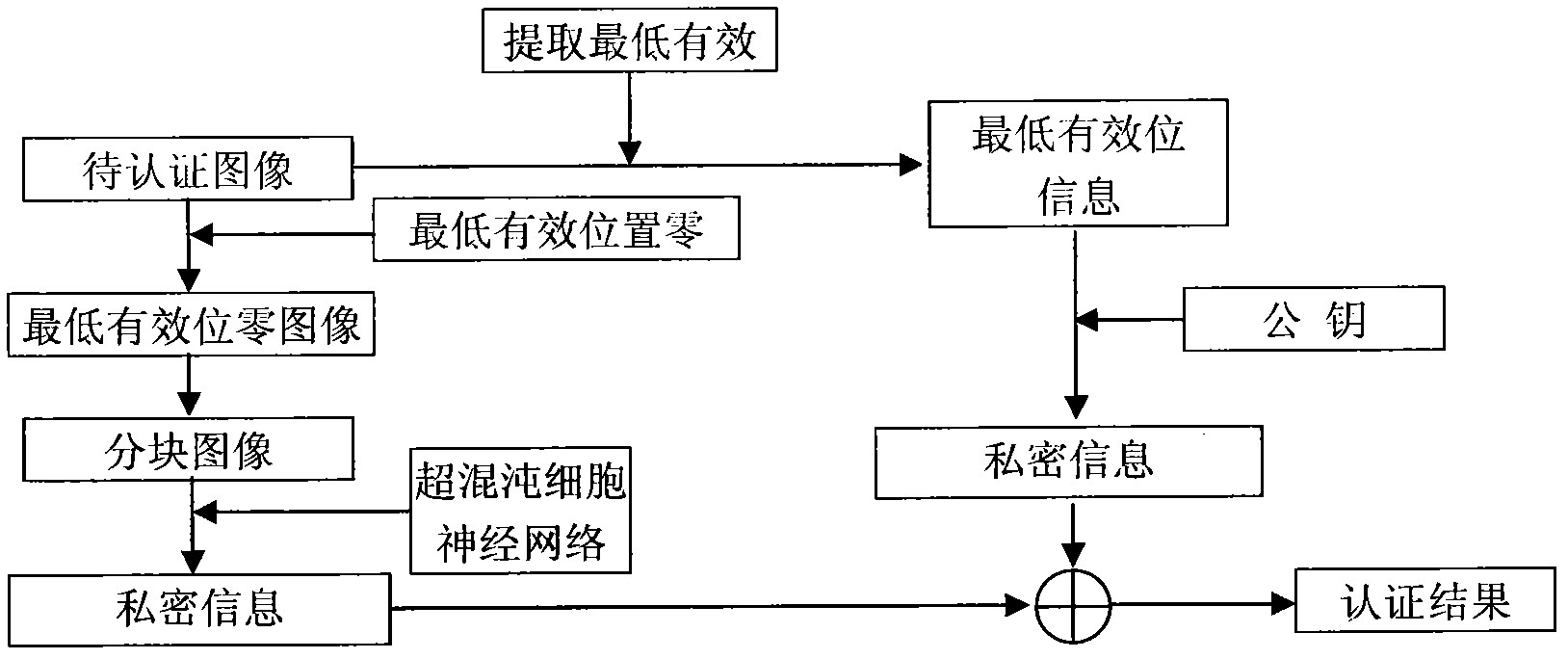
[0006] The specific implementation includes two processes. The first process is the information embedding process of embedding verification information into the image, and the second process is the verification process of realizing image authenticity identification and tampering self-location.
[0007] 1 Information embedding process
[0008] The specific steps of the information embedding process are as follows:
[0009] 1.1 Least Significant Position Zero
[0010] Suppose the original image O has a size of 256×256 pixels, and the least significant position of this image is zeroed to obtain image O1. For example, the pixel value of a block in the image O is which is Zero the least significant bits of all its bits, which is O 1 = 11111110 10000000 01101010 00100000 . ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com