Database forced access control method and system based on policy
A mandatory access control and database technology, applied in the field of data processing, can solve the problems of slow data access response and low access efficiency, and achieve the effect of simplifying management and configuration work
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
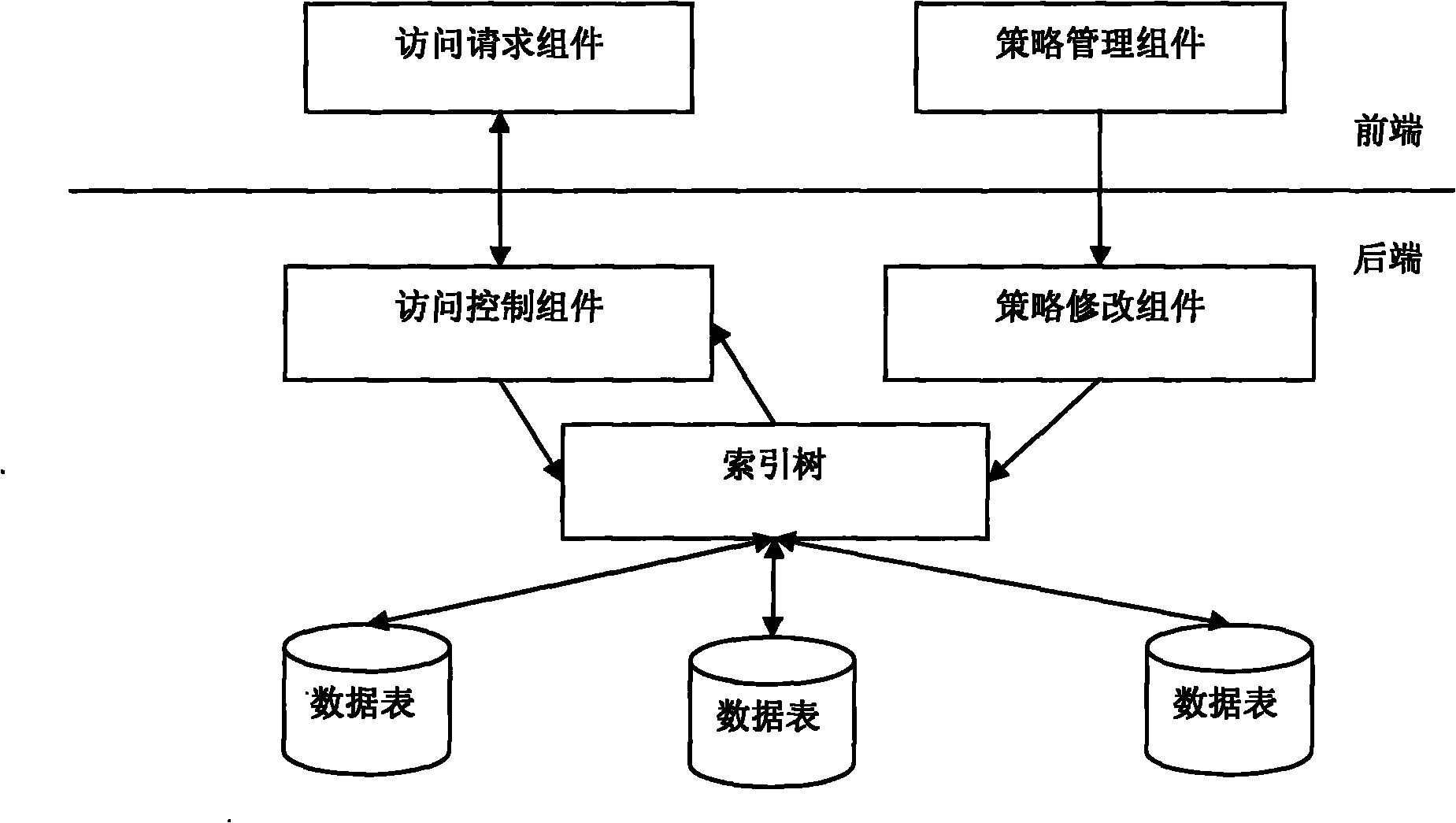
Method used
Image
Examples
Embodiment 1
[0062] This example enforces mandatory access control on the employee information table of a common database. The employee information table includes 5 fields, number, name, salary, department, and the information stored in the data table is as follows:
[0063]
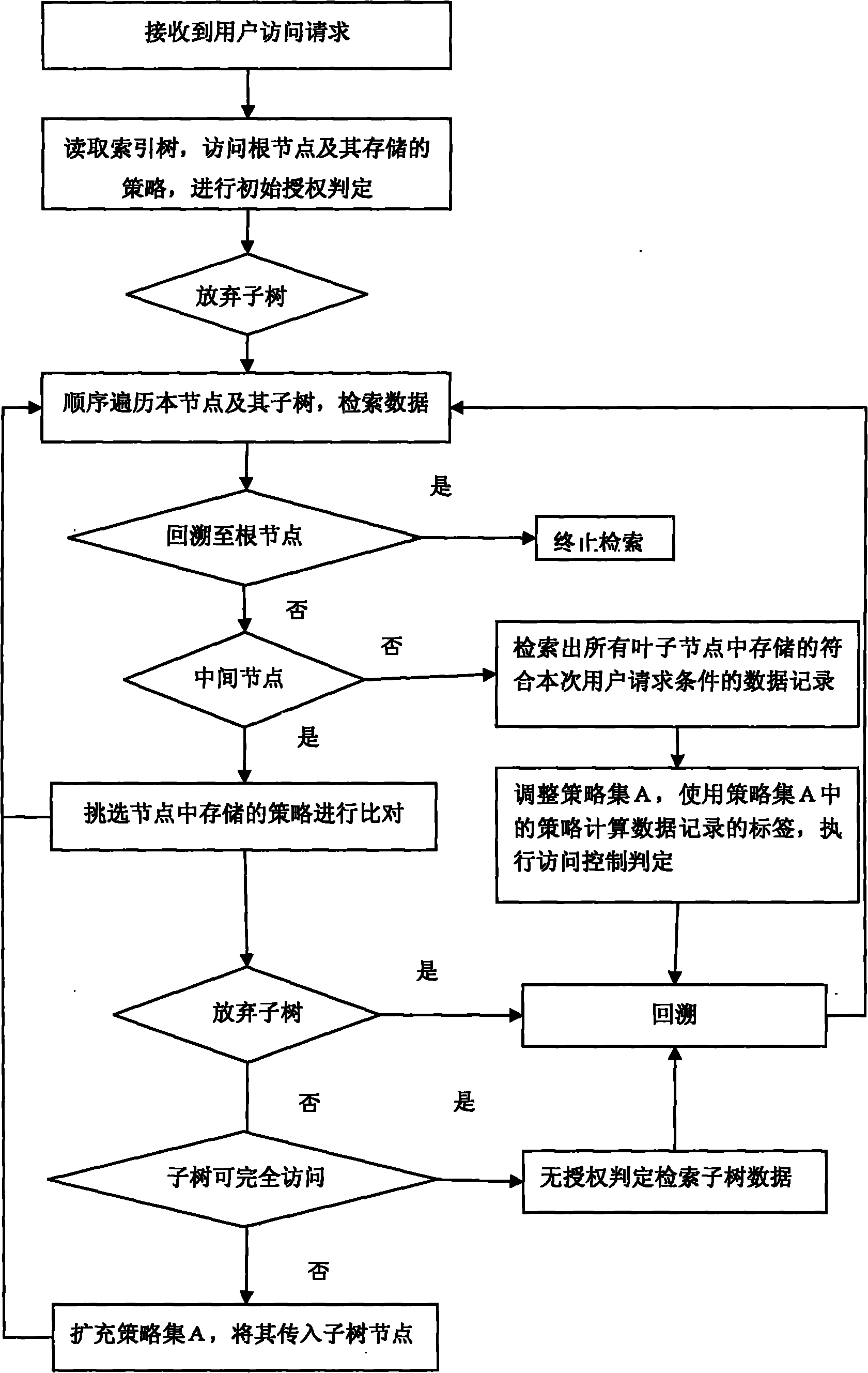
[0064] The process of using this method to perform spatial query access control on each data table in the database is as follows:
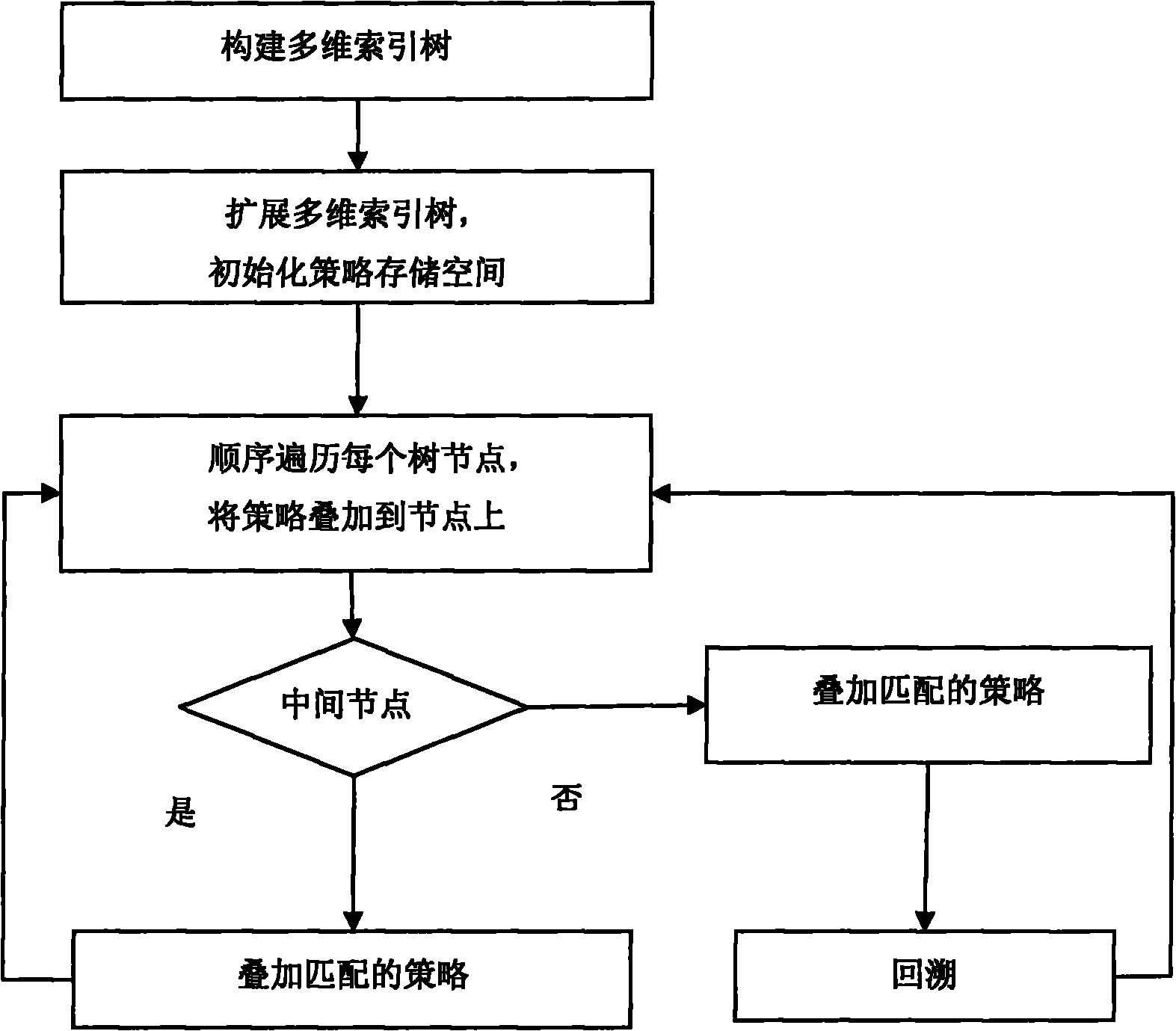
[0065] 1) Create an index tree for the spatial data table in the database. The index tree is an R+ index tree, and the index field is {salary, age}. The tree has three layers of nodes including the root node. The node space segmentation effect is as follows Figure 4 shown.
[0066] 2) superimposing and storing the mandatory access control security label setting policy layer by layer on the nodes of the index tree;
[0067] a. First set a set of security labels L, each element of which is composed of two components, the first is the category category, the value is any subset of {Dep...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com